Disconnected from IT security,
SAP systems pose a security risk
Organizations have a lack of visibility into business-critical SAP systems. A lack of SAP security poses a huge risk to organizations with 64% saying they have been the victim of an ERP breach in the past two years, at an estimated cost of $5 million per breach. After an attack, organizations have no way of figuring out what happened and who accessed SAP data.
Combine security monitoring,
analytics and response with SAP

Protect business-critical data
Industry-leading analytics help solve the biggest challenges faced by today’s SAP teams
Reduce security complexity
Centralized monitoring combined with automation, workflows, and case management all in one tool

Achieve efficiencies of scale
Eliminate the gap between SAP and cyber teams to mitigate threats across the business
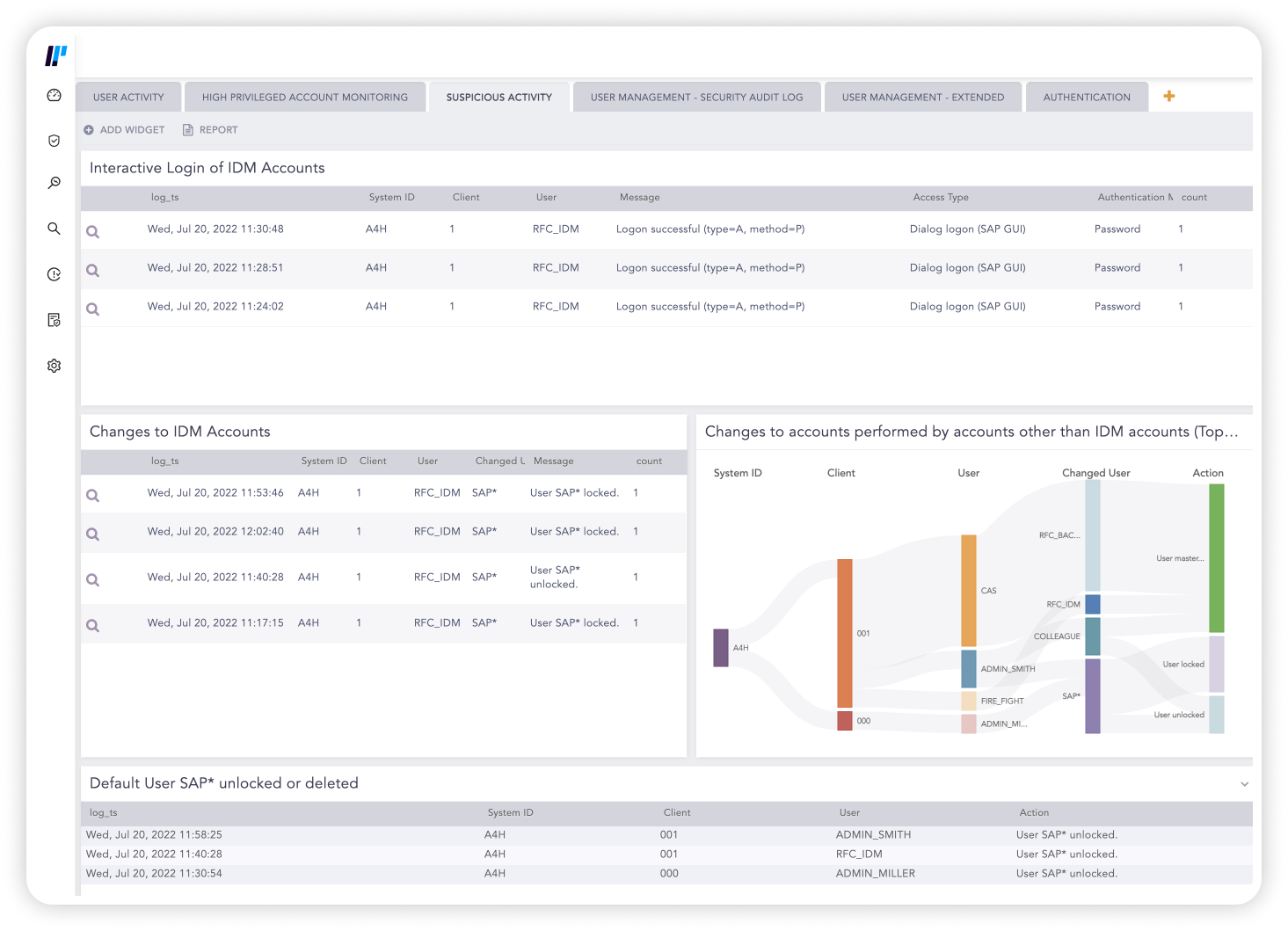
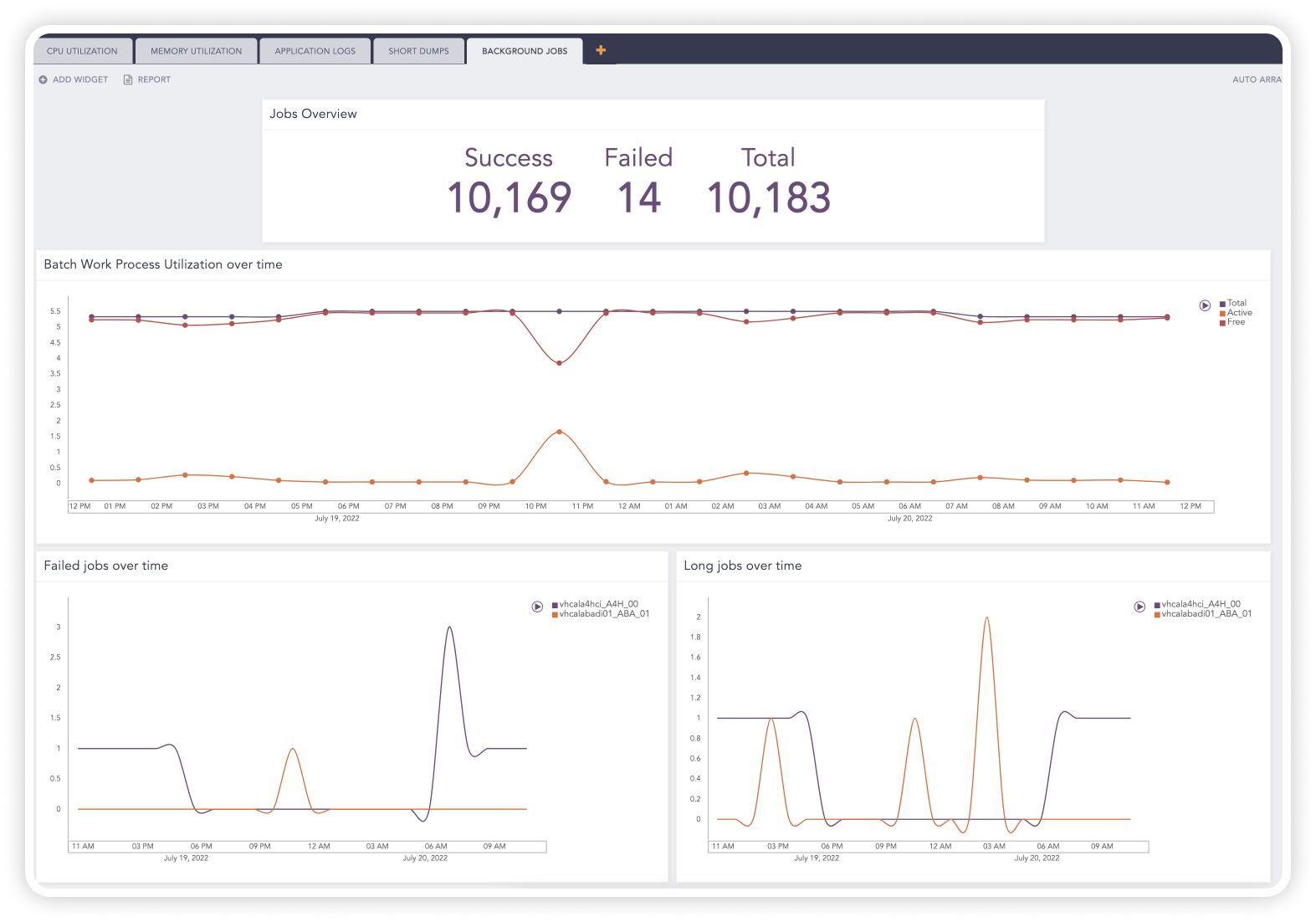
Get visibility across SAP and prevent costly downtime
Logpoint creates telemetry, gathers log events and monitors logs from SAP. By correlating and enriching data, translate logs into an industry standard, and create alerts for critical or suspicious activity.
By extracting SAP logs and monitoring core SAP behavior, you can detect and respond to threats that would otherwise be missed. Eliminate unwanted SAP downtime with full-stack monitoring of your system’s operational capabilities, early warning system and trend analysis.
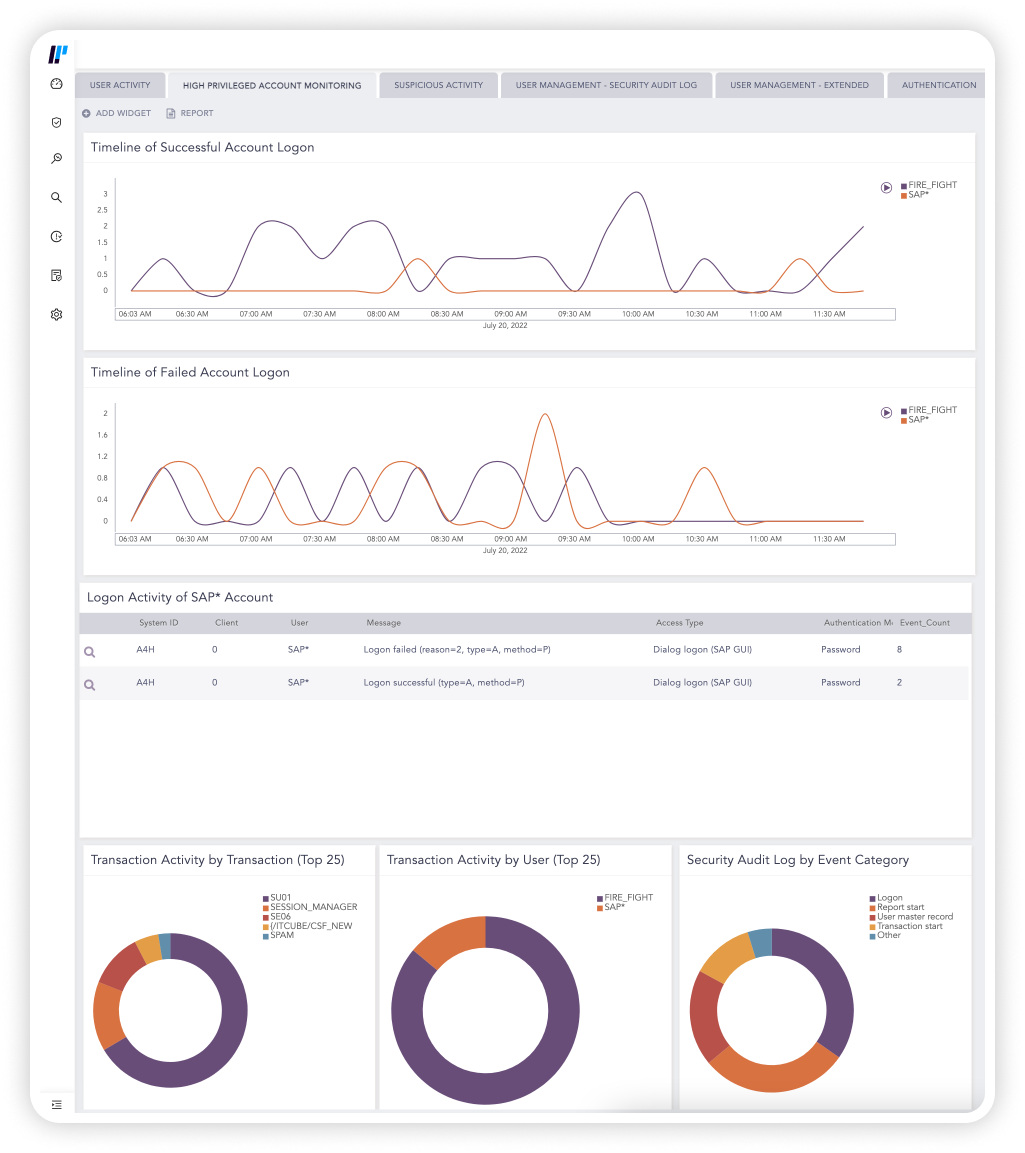
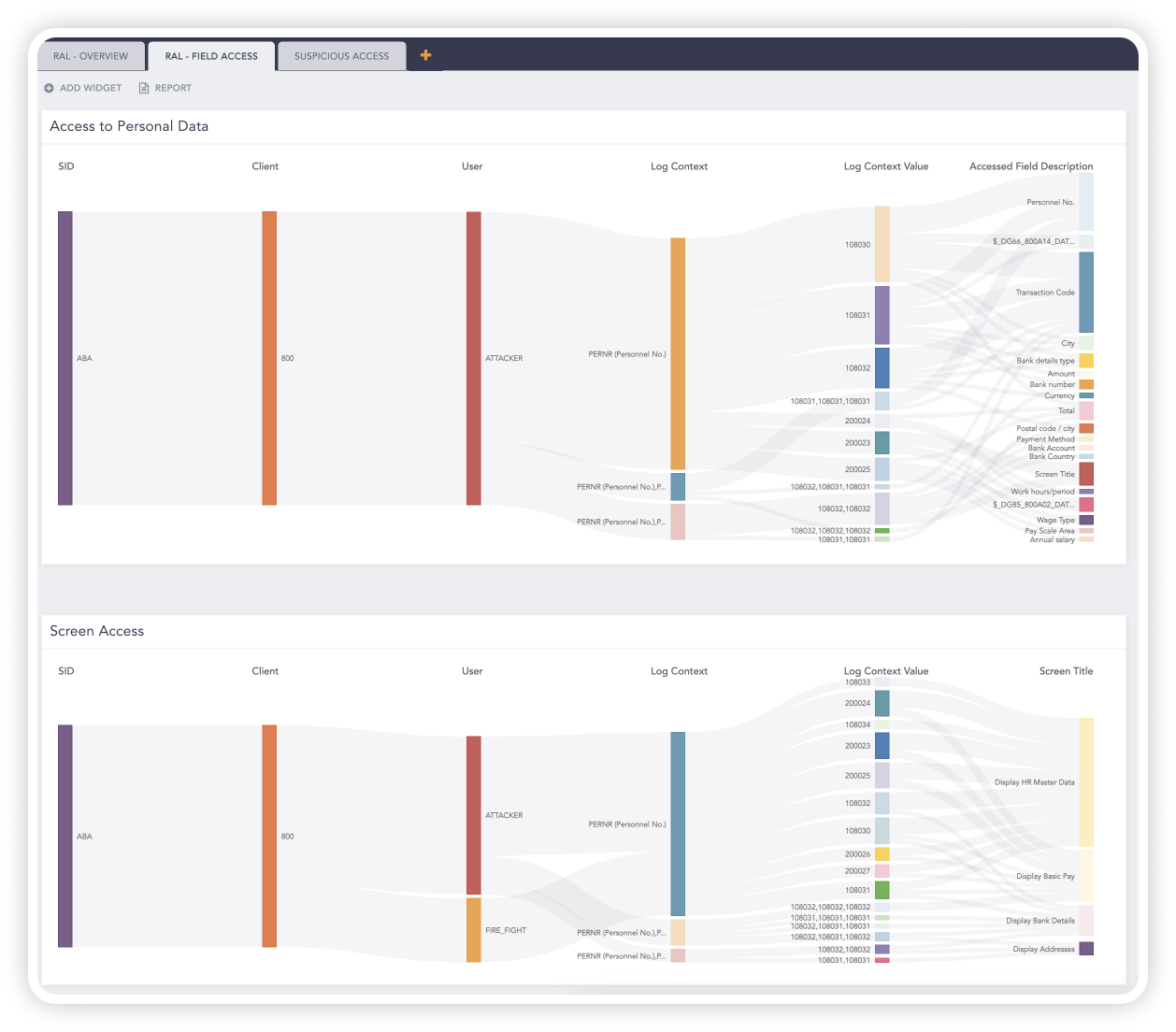
Accelerate threat detection and compliance in SAP
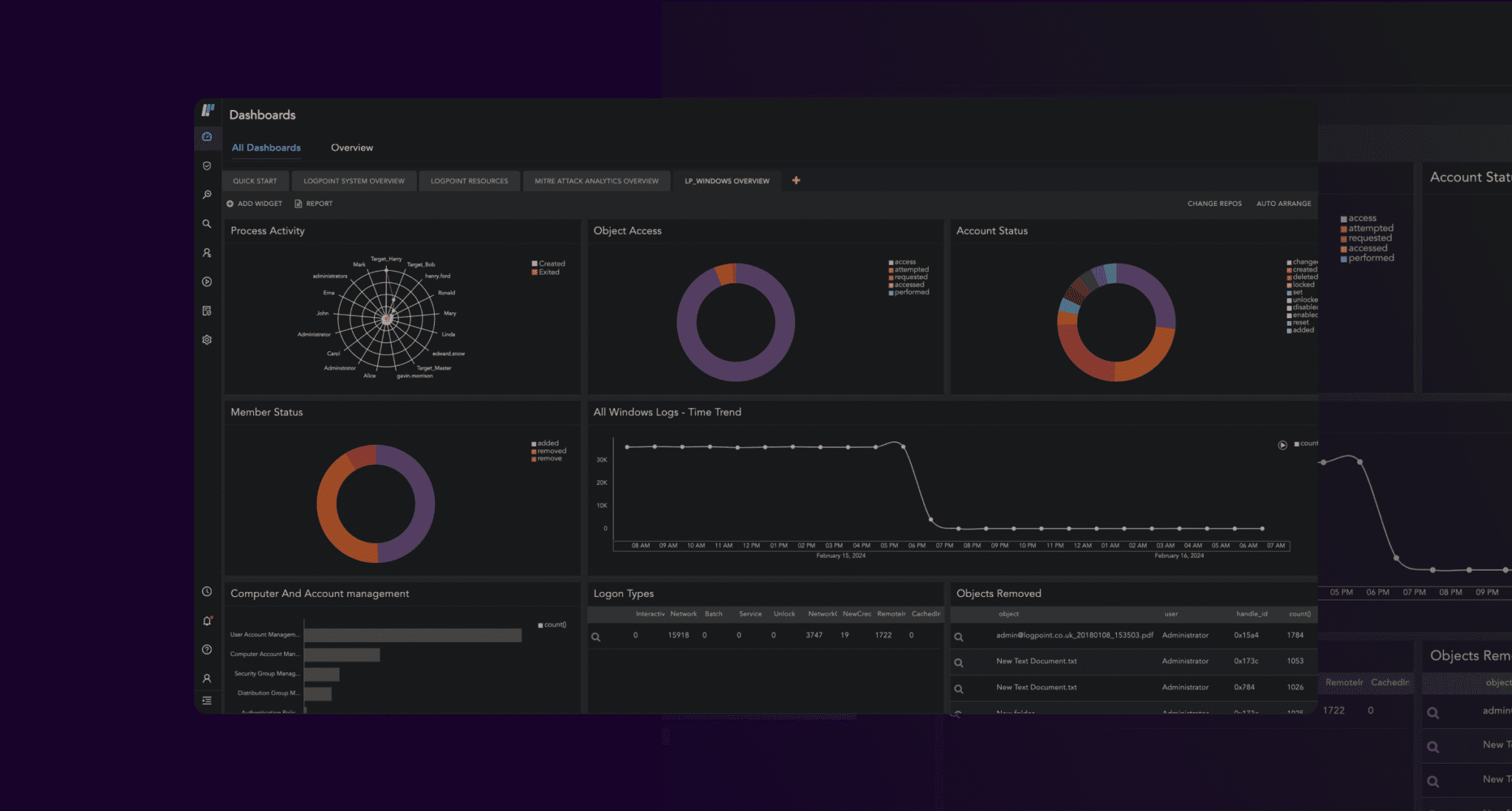
Logpoint continually monitors SAP systems for IP theft, fraud, access violations, and compliance to enable efficient threat detection and response.
With out-of-the-box analytics, you can detect suspicious transactions and SAP user behavior in near real-time and tracks the activity with user and entity behavior analytics – even when the attacker removes all traces. Logpoint automatically correlates and analyzes SAP and security data so you can respond quickly.
Consolidate tools and help mature security operations
Logpoint provides central monitoring and management of SAP logs, access, fraud attempts, compliance, and violations that can easily integrate with your existing security stack.
With native integration to Logpoint’s converged platform, you can thoroughly mitigate threats by translating observations from SAP into a cybersecurity context.
We now think of Logpoint as a member of the IT security team. It provides immediate answers to a lot of questions that we would have struggled to answer under a more manual system. We can take logs from everywhere that they need to be gathered and collate and analyze as much as we need and the process of ingesting data is very open.
The strength of the Logpoint solution is that we don’t have to spend unnecessary time on investigating false positives and that we check all logs. Not only logs chosen at random. This way, we comply to the legal requirements of effective log auditing.
Get up to date with the
Logpoint blog!