Secure your Manufacturing Against Cyber Threats
Interconnectivity has been one of the key pillars behind modern manufacturing, driving massive transformations and creating incredible opportunities. But with those advances came new challenges.
Interconnectivity gives malicious actors a wider area to attack and broader access to mine your infrastructure for valuable information. With the Internet of Things (IoT) connecting devices not only to each other but also to the internet, keeping these threats at bay becomes an even more urgent priority.
Ensure NIS2 compliance with Logpoint
NIS2 Directive is stepping into force, striving to enhance protection of critical infrastructure in EU from cyberthreats. It introduces stricter security demands, reporting obligations and enforcement requirements for a broader scope of sectors. Inability to comply can impose fines up to 2%* of the worldwide turnover.
Threats
Most attacks on manufacturing organizations are targeted and rarely random acts of cyber vandalism. The intention is most often to steal your intellectual property.
While threats certainly loom outside your infrastructure, it’s just as important to identify privilege misuse in which your employees attempt to exfiltrate your secret data. In 61% of all security breaches, valid credentials were involved. Insider attacks can be difficult to identify as established security controls do not apply or easily can be circumvented.


WHY LOGPOINT:
Let No Breaches Slip Through the Cracks
Logpoint provides end-to-end monitoring of your entire infrastructure and seamlessly alerts of suspicious patterns, in real time. Our intuitive dashboards deliver a holistic overview – no matter how vast your IT landscape or dense your data is.
Unwinding cyber infiltrations and exfiltrations can be time-consuming and labour-intensive. Save time with automation and ensure that no breaches slip through the cracks.
WHY LOGPOINT:
Efficiently Detect and Respond to Issues Compromising the Safety of your Systems
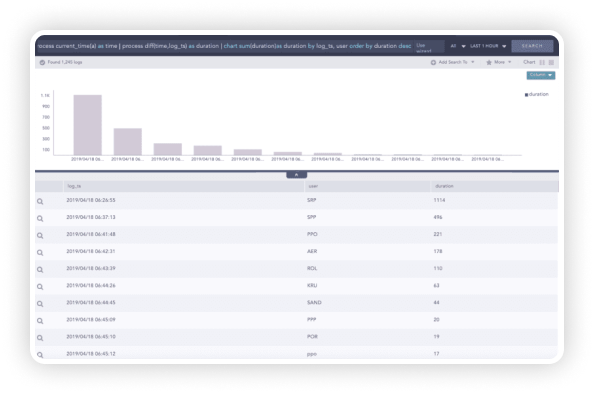
Dynamic lists collect and store specific values from events, allowing dynamic updates through log messages. By enabling analysts to define dynamic lists and tables, organizations can reduce the MTTD and react to threats more efficiently.
WHY LOGPOINT:
Detect Early Signs of a Breach with Advanced Analytics
Logpoint helps security analysts discover suspicious behavior in real-time with powerful analytics. Through advanced correlation of various data sources, we can detect anomalous behavior that usually goes unnoticed.
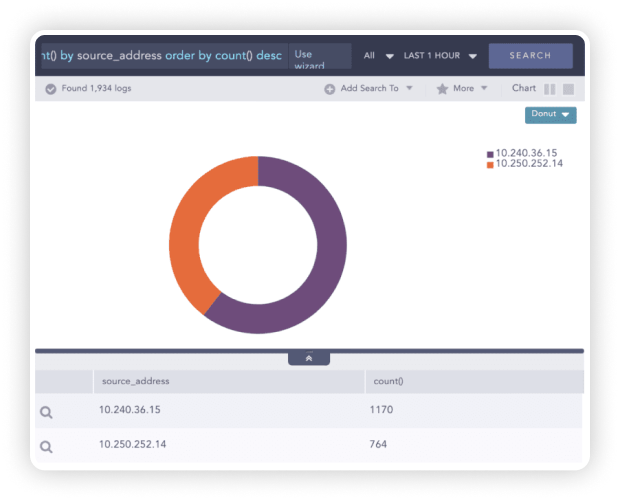
Dynamic Lists can be used to perform advanced correlations to identify potential exploitations of a vulnerability by a threat source.
WHY LOGPOINT:
Identifying Threat Indicators Associated with an Executed Malware Payload
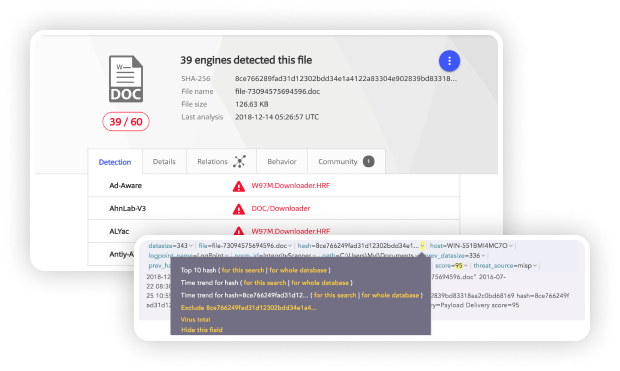
Logpoint’s FIM (File Integrity Monitoring) is an effective tool to monitor the creation of new files or changes in file extensions, indicating malware payload execution. The hash value given by the Integrity Monitor can be compared to the virus total database, identifying the associated threat.
Use Case:
How Logpoint helps Engelbert Strauss stay ahead on the Cybersecurity curve and keep an eye out for anomalies in the IT infrastructure
German workwear company Engelbert Strauss is using Logpoint to collect and analyze logs from a diverse IT infrastructure. The Logpoint SIEM solution provides the IT department with a centralized overview, helps them stay in control and respond in real-time to potential cyberthreats.

Using Logpoint fundamentally changes the way you work with log data in your infrastructure. With Logpoint log data becomes a useful tool. It allows us to take control and get a meaningful, constant output that enables us to spot potential problems and react promptly. Before things turn into a real threat.
Get up to date with the
Logpoint blog!




