Application and Network Traffic Monitoring for Financial Services
Protect valuable assets with SIEM
Keeping personal information of customers secure is vital. Data breaches in the financial services industry can erode a customer’s trust, lead to loss of business, and can result in regulatory fines and sanctions.
Ensure NIS2 compliance with Logpoint
NIS2 Directive is stepping into force, striving to enhance protection of critical infrastructure in EU from cyberthreats. It introduces stricter security demands, reporting obligations and enforcement requirements for a broader scope of sectors. Inability to comply can impose fines up to 2%* of the worldwide turnover.
Let No Breaches Slip Through the Cracks
To protect your customer’s personal data and to ensure compliance, you need a solution that spots attacks, keeps track of insider and outsider activity and offers clear visibility into every corner of your network.
Identifying Threat Indicators Associated with an Executed Malware Payload
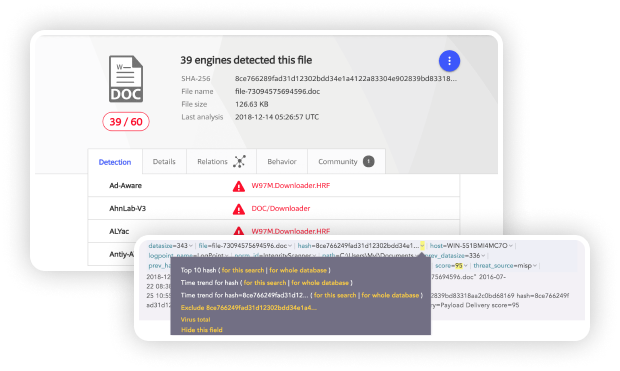
Logpoint’s FIM is an effective tool to monitor the creation of new files or change in file’s extension indicating malware payload execution. The hash value given by the Integrity Monitor can be compared to the Virus total database, identifying the associated threat.

User Activity Monitoring
Logpoint provides analysts with a powerful tool to identify malicious activities. Create alerts, dashboards, and reports so they can get an overview and counteract immediately.
Get a full overview of all accesses to critical transactions, disclosed corporate information, and personal data with a centralized logging solution covering your entire IT infrastructure.
Detect and effectively manage access violations, data leakage and misuse of personal sensitive data with a comprehensive, all-in-one overview.
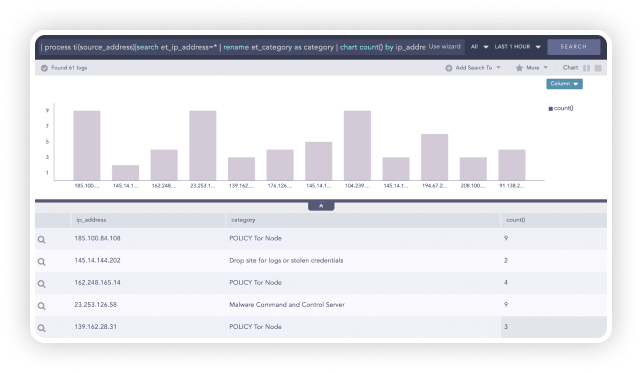
Spotting and Tracking Unauthorized Network or Systems Access
Logpoint enables you to detect any suspicious and/or unauthorized network behavior such as connection attempts on closed ports, blocked internal connections, connections made to known-bad destinations, requests initiated from untrusted zones, suspicious system access and many more.
Use Case:
Logpoint for Matmut
With Logpoint, Matmut has:
- improved event visibility across the entire IT architecture
- educed incident response time
By improving event visibility across the entire IT architecture, Logpoint has enabled 80-90% time savings in incident diagnostics, faster problem resolution and major improvements in the service quality for end-users.

A Highly responsive support in deploying the solution plus total control over costs were decisive criteria in validating the Logpoint solution. The savings generated by the Logpoint solution allowed us to upgrade the quality of service offered to our organization, which is an unexpected but much-welcomed benefit.
Get up to date with the
Logpoint blog!