Over 1,000 Organizations Across 70 Countries Use Logpoint SIEM
Dealing with Complexity and Building a Better Service Model.
By utilizing cloud-based solutions MSSPs can focus purely on value for the customers.
Logpoint’s Matthew Rhodes, Regional Director for MSSP, is joined by IT Europa and discusses how an effective MSSP model can deliver not only better cyber security but streamline operational efficiency.
Shifting Priorities: Why MSSPs Need to Act Now to Innovate and Continue to Evolve Their Offerings
Our experienced research and security analyst teams specialize in SIEM and SOAR technologies, recommending, building, and helping implement playbooks, processes, and assisting organizations in automating workflows.
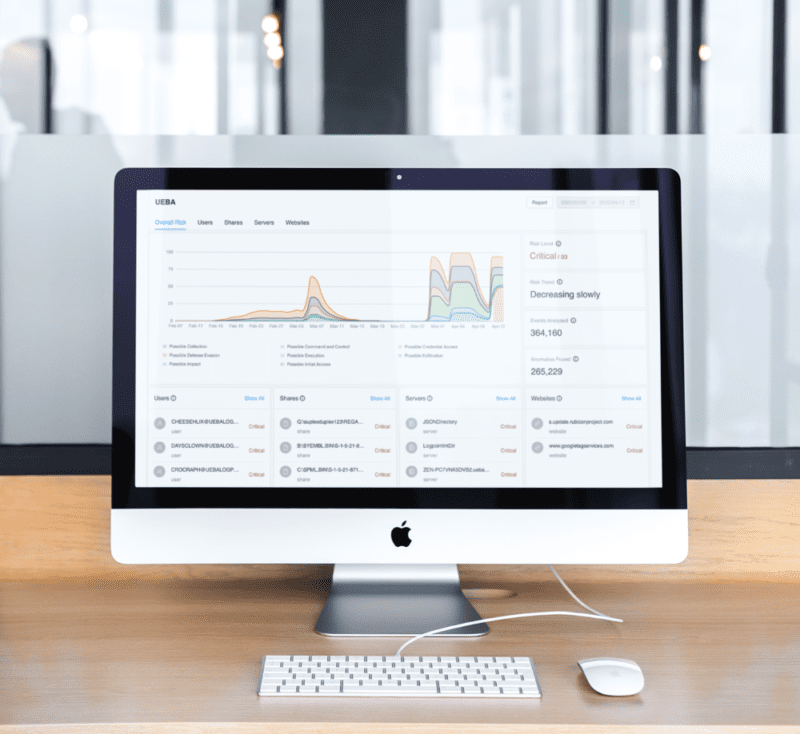

 Logpoint SIEM is the most flexible tool in our security solution stack. We build everything around it.
Logpoint SIEM is the most flexible tool in our security solution stack. We build everything around it.
GoSecure
North American MSSP

 Logpoint SIEM is the most flexible tool in our security solution stack. We build everything around it.
Logpoint SIEM is the most flexible tool in our security solution stack. We build everything around it.
GoSecure
North American MSSP









