Incident investigation and
remediation take too long
Industry estimates suggest it takes skilled hackers less than 19 minutes to move laterally after compromising the first machine in an organization.
In contrast, MTTR can take months or even years and only 24% say their SOC can resolve security incidents within hours or days. The speed of attack shows a significant gap in the abilities of analysts to response.
Accelerate threat detection,
investigation and response

Protect your organization
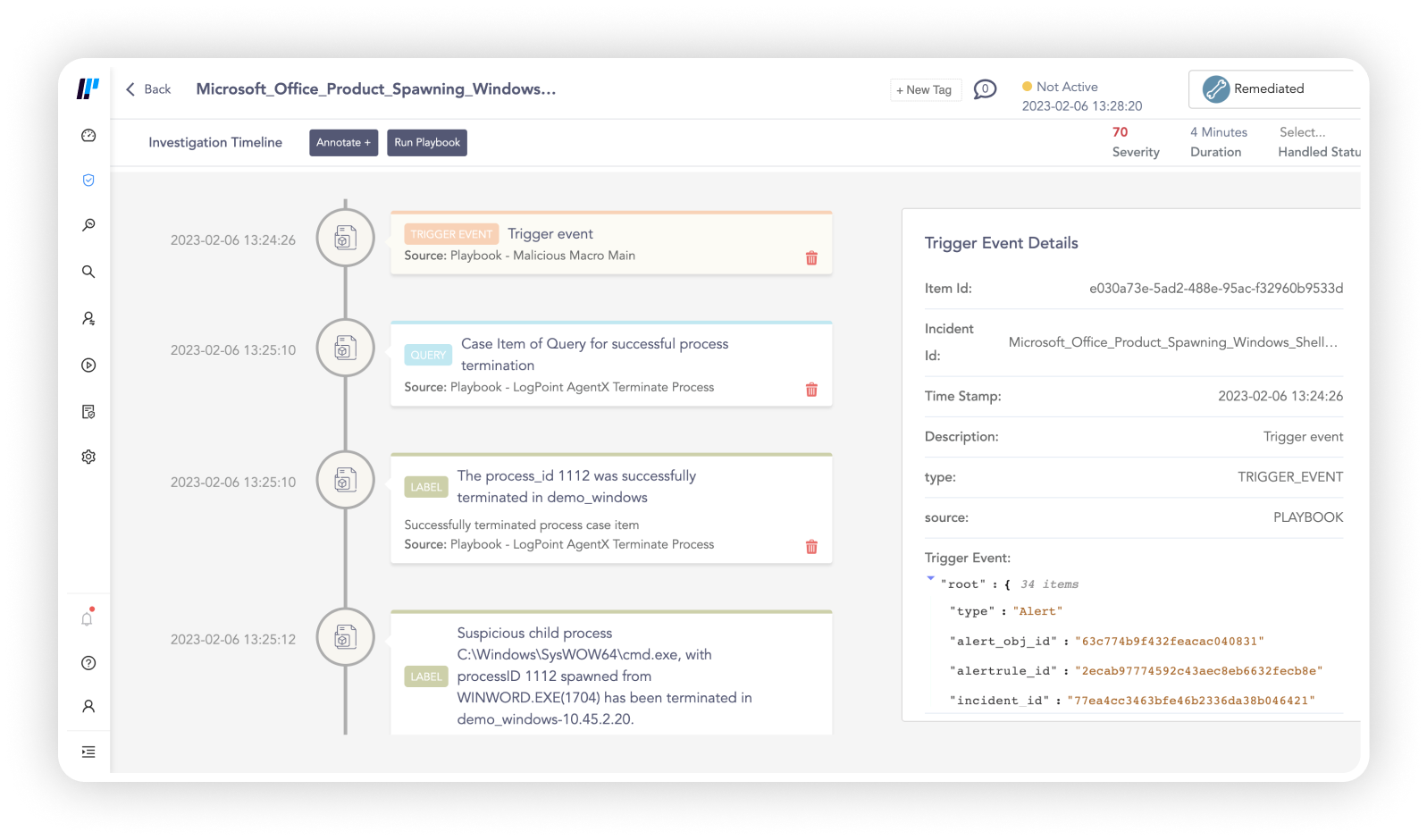
Empower security teams to detect and respond across the entire organization

Simplify the tech stack
Converged security operations platform gives security teams the full picture in one tool

Increase team efficiency
Automatic response actions help security teams respond quickly and consistently
Gain visibility across your environment
Logpoint collects event data from clients, servers, network systems, cloud workloads, and business-critical systems helping you visualize data.
Then, Logpoint enriches data with information regarding users, assets, threats, and vulnerabilities making data actionable.
Putting the data into context provides insight that ensures decisions can be made quickly.
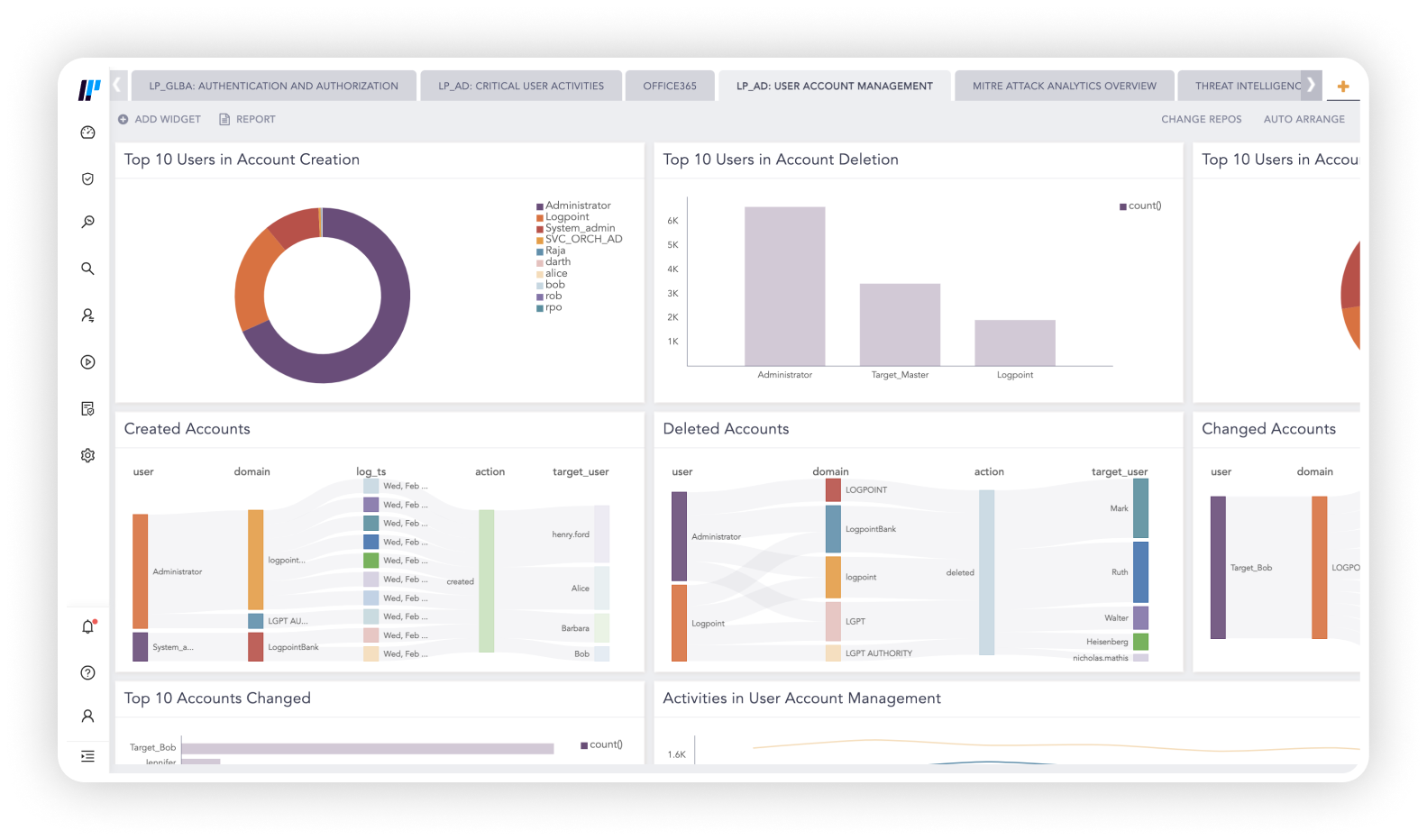
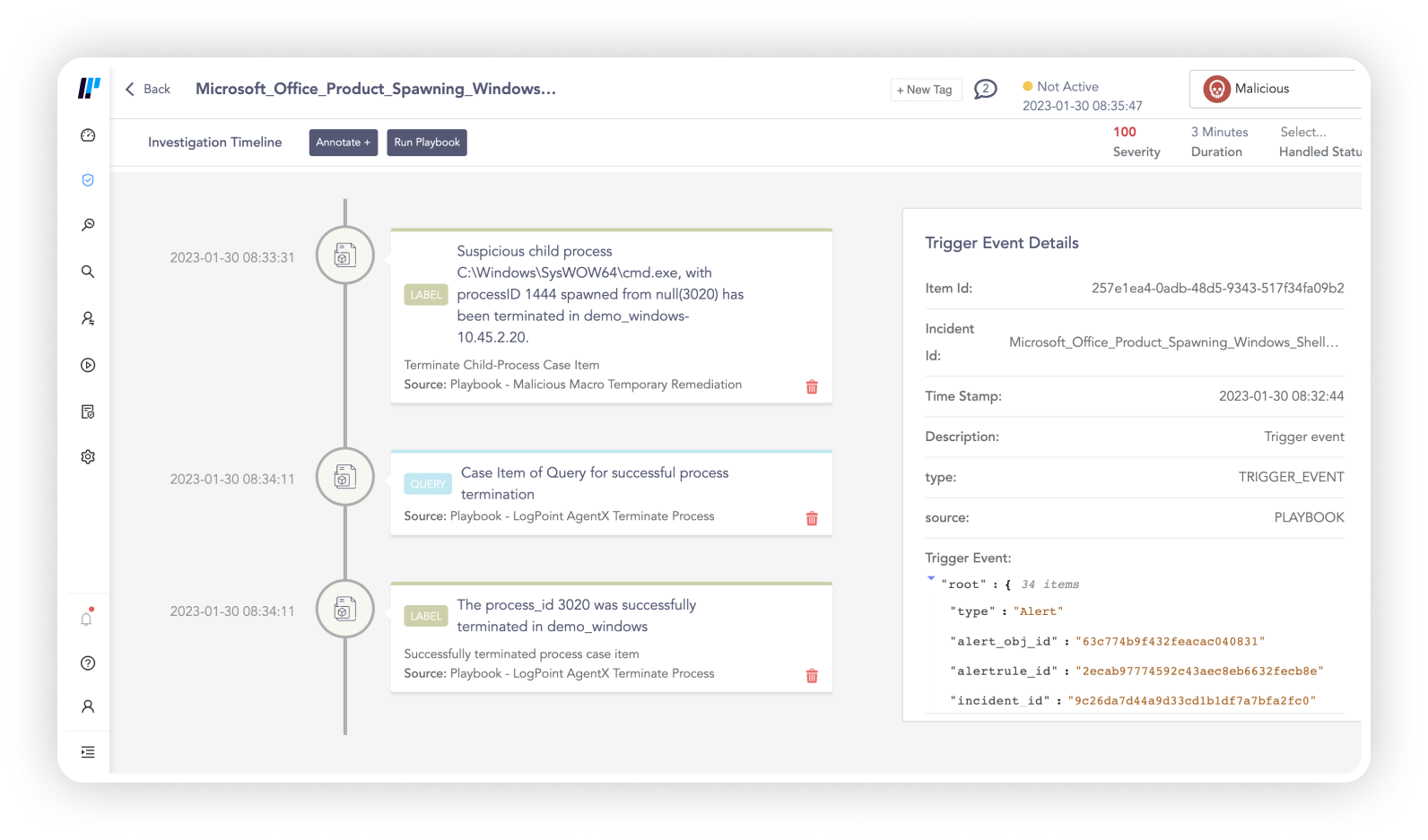
Focus on the alerts that matter most
Add context, threat intel and entity risk fusing weak signals and turning them into meaningful investigations. Built-in capabilities on endpoints allow analysts to run interrogations that can uncover threats accelerating investigation.
With regularly updated ready-to-use security content and playbooks, you can always detect, investigate and respond to the latest threats.
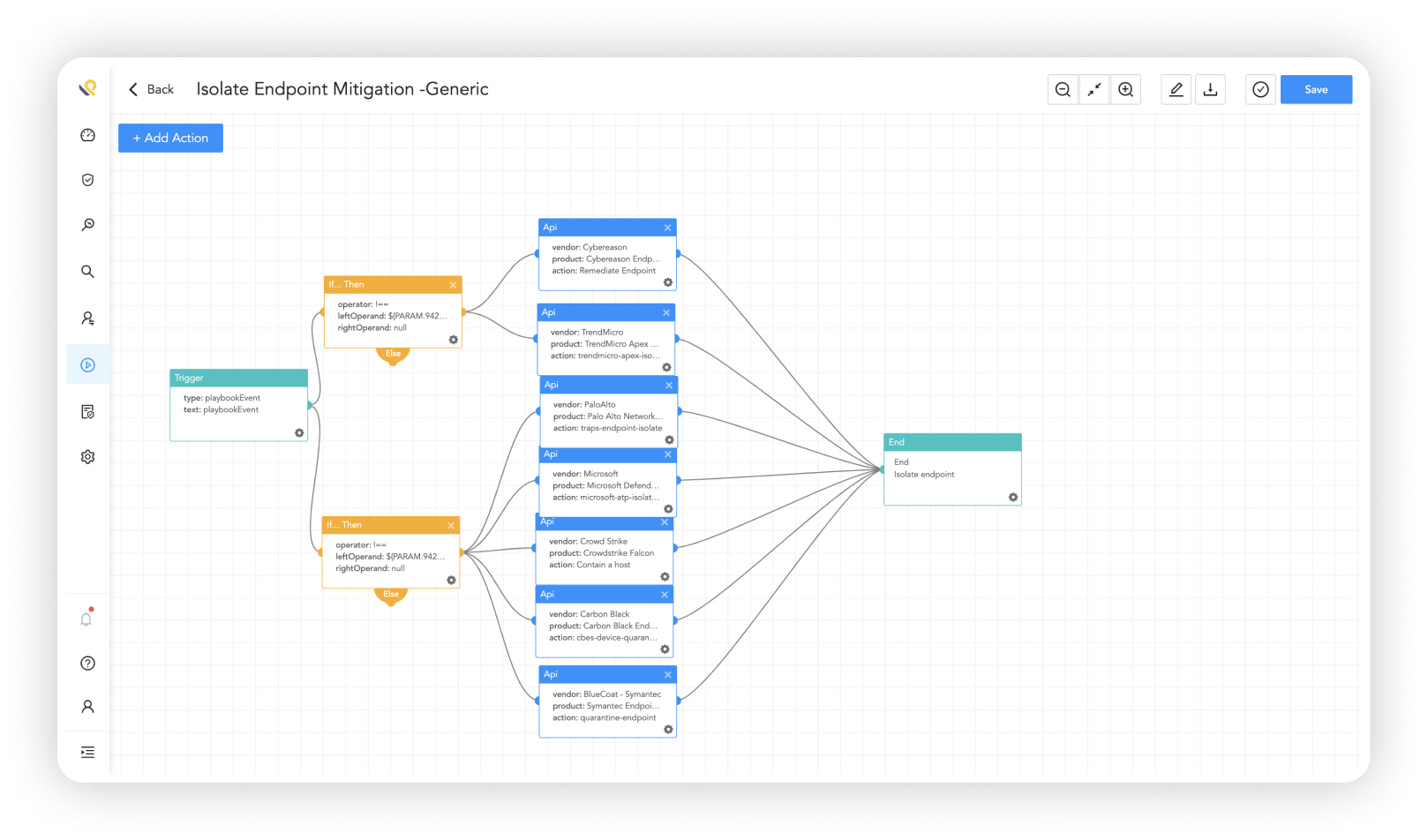
Automatically respond to reduce impact of incidents
Logpoint alerts and playbooks work seamlessly with the entire converged platform – SIEM, SOAR, UEBA and endpoint security.
Automate across tools and increase security posture with no additional cost or implementation required.
Built-in endpoint response capabilities reduces alert fatigue by isolating hosts, blocking incoming connections from malicious sources, and disabling users in case of a breach.
Logpoint allows Computerome administrators to quickly detect unusual behavior in the system and to prevent misuse and data breaches. It provides that extra layer of security on top of the established security controls, which is required when handling vast amounts
of data.
Implementing Logpoint has not only increased situational awareness and cybersecurity. It has allowed us to respond faster and use less human resources on the cumbersome, repetitive work of manually collecting and analyzing data from different log sources in case of incidents. Those resources can then be deployed to improve service and security elsewhere.
Get up to date with the
Logpoint blog!