Protecting your customer data against attacks
In order to succeed, retailers must excel at continuously collecting data and closely monitoring customer behavior. To deliver seamless user experiences, customer data is often stored in the systems, increasing the risk of exposure. A breach can have unprecedented impact on your customers, undermine your brand legitimacy, damage your revenue and even lead to regulatory non-compliance.
Ensure NIS2 compliance with Logpoint
NIS2 Directive is stepping into force, striving to enhance protection of critical infrastructure in EU from cyberthreats. It introduces stricter security demands, reporting obligations and enforcement requirements for a broader scope of sectors. Inability to comply can impose fines up to 2%* of the worldwide turnover.

WHY LOGPOINT:
Complete threat visibility – ensuring that no breaches fall through the cracks with Logpoint
With automation, we continuously monitor, analyze and help detect incidents that can compromise the security of retail customer data. Logpoint monitors key system objects and components found in any enterprise, including networking equipment, servers, applications and databases. When it comes to e-commerce sites, the most common breaches involve hacking the web application, whether through denial of service (DoS) attacks or stolen credentials from customers as part of phishing attacks.
With Logpoint’s native FIM features, you will always be in control of your sensitive assets and get alert.
WHY LOGPOINT:
User activity monitoring
User Activity Monitoring is a powerful tool that automatically delivers a comprehensive overview of malicious activities, allowing analysts to effectively counteract malicious activities.
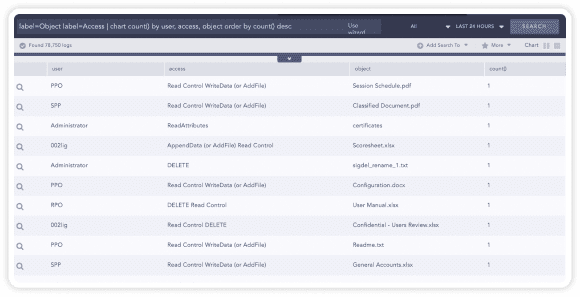
With out of the box use-cases and alert rules, you can easily monitor access to files, privileged file sharing systems and get additional information on actions performed in the file. To better understand access behaviors, original and altered checksums can be compared.
Example – Object access attempts
WHY LOGPOINT:
Identify threat indicators associated with an executed malware payload
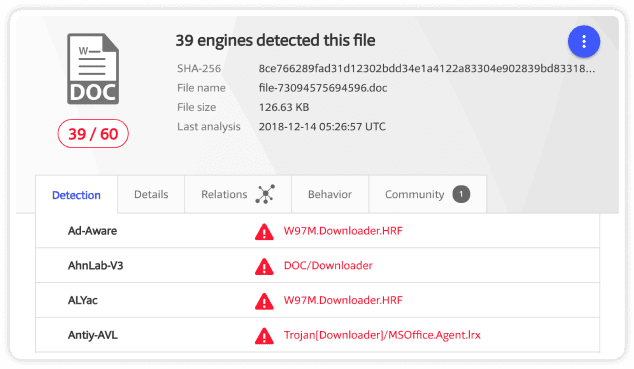
Logpoint’s FIM is an effective tool to monitor creation of new files or changes in file’s extension that could indicate malware payload execution. The hash value given by the Integrity Monitor can be compared to the Virus total database, identifying the associated threat.
WHY LOGPOINT:
Spotting and tracking unauthorized network or systems access
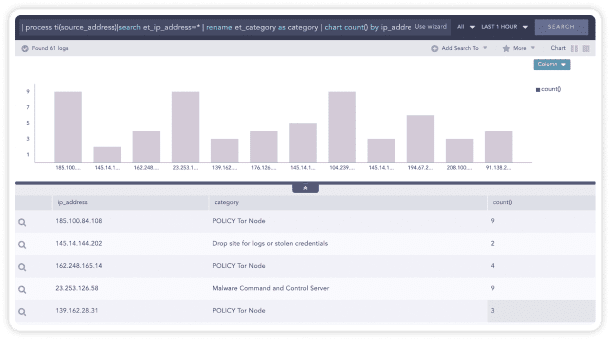
Logpoint enables you to detect any suspicious and/or unauthorized network behavior such as connection attempts on closed ports, blocked internal connections, connections made to known-bad destinations, requests initiated from untrusted zones, suspicious system access and many more.
Example – Threats in higher privilege systems
Use Case:
Logpoint for PXP Solutions
With Logpoint, PXP Solutions has a powerful tool in place to ensure alignment with:
- governance
- risk
- compliance standards
Logpoint allows PXP Solutions to keep a granular view of logs and quickly identify any out-of-the-ordinary activity to maintain its security posture at any time.
As a financial services company in a highly regulated industry, it is imperative that we maintain a strong security posture at all times.
While the investment in a SIEM solution was always driven by our need for a robust security infrastructure, we are also faced with a wide range of industry standards such as the PCIDSS, GDPR, SOC 2, and the Point-to-Point Encryption standard, where non-compliance can mean the loss of customers.
By using Logpoint, we can keep a very granular view of our logs and easily identify any out-of-the-ordinary activity.
Latest Research, Trends, and Insights




