Lack of visibility makes it difficult
to ensure the business is secure
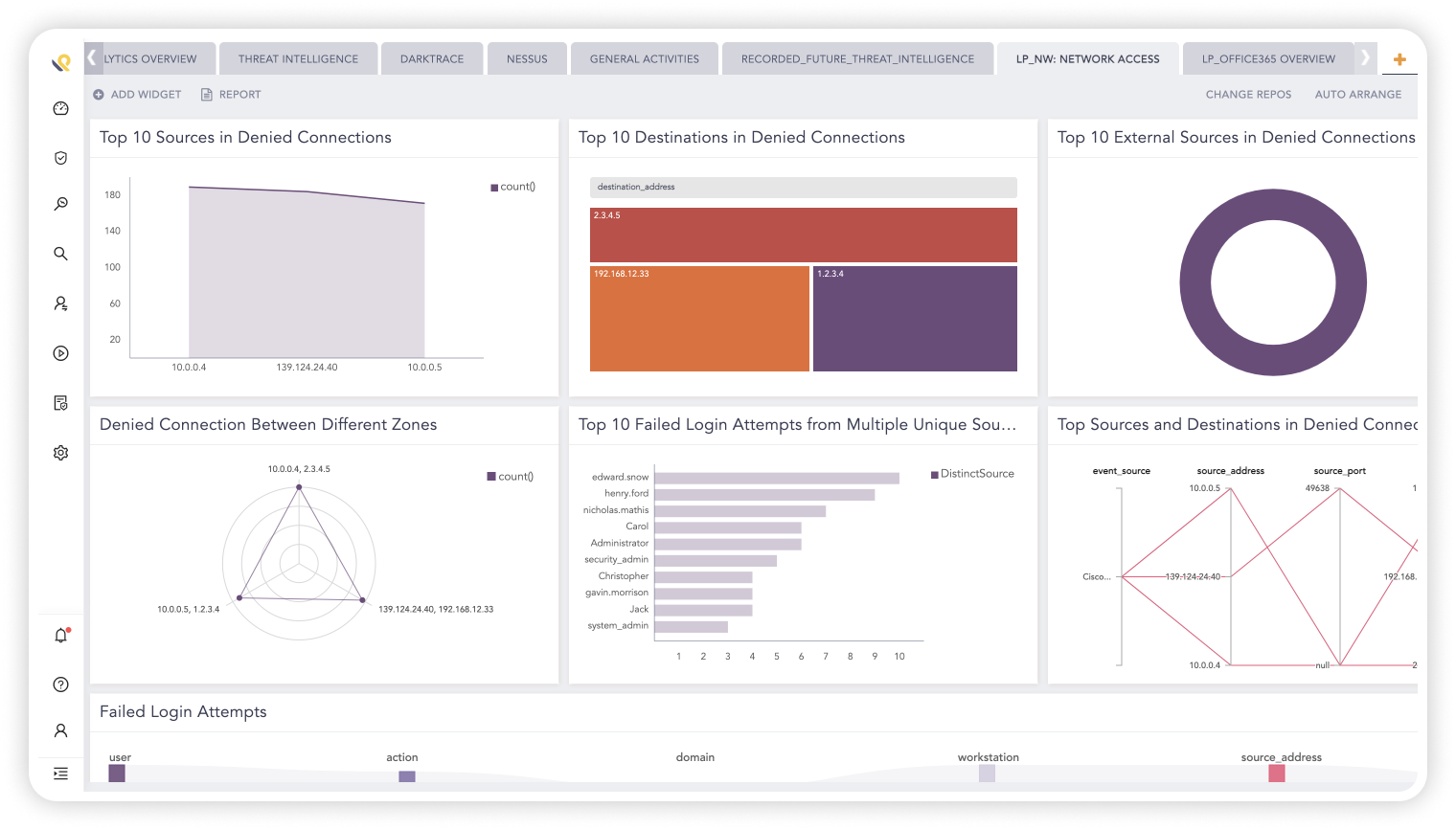
Without accurate and thorough visibility, it’s exceedingly difficult to make valid, meaningful security decisions and to ultimately know if the business is secure. Lack of visibility into network traffic and cloud environments is the number one cause for ineffective security operations.
A converged security operations
platform protects the entire business
Improve cyber efficiency
Easily integrate with network, servers and cloud apps to achieve visibility and efficiencies of scale
Reduce security complexity
Centralized monitoring combined with automation, workflows, and case management all in one tool

Get the latest security coverage
No need to implement or maintain solution so latest security coverage is always available
Gain visibility across tech stack to build defensive capabilities
With a converged security operations platform, you can fuse telemetry and automate response across the enterprise technology stack from clients, servers, network systems, cloud workloads and business-critical applications.
With single taxonomy, we guarantee that all of our security solutions work together and we can deliver third-party integration out of the box with limited customer effort.
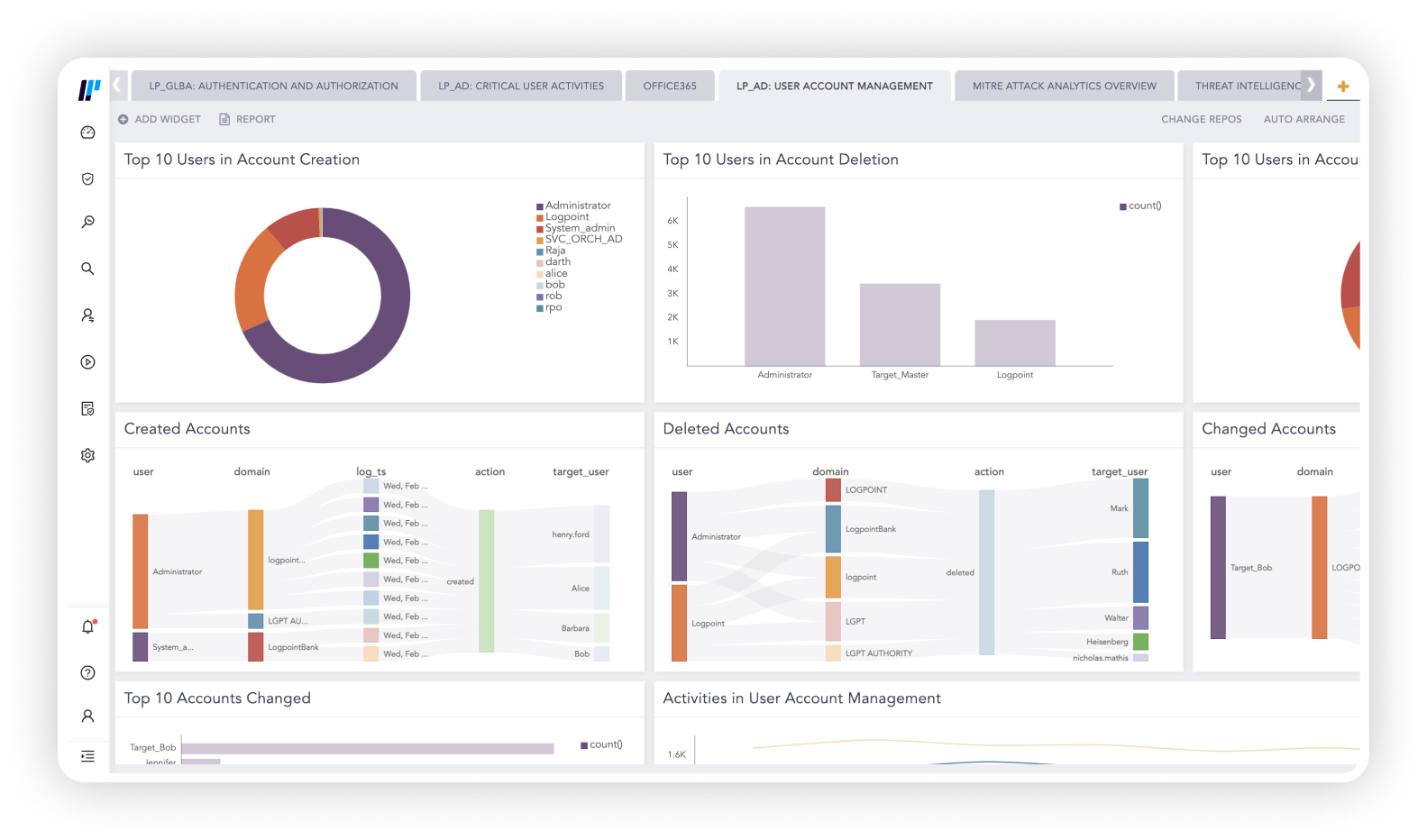
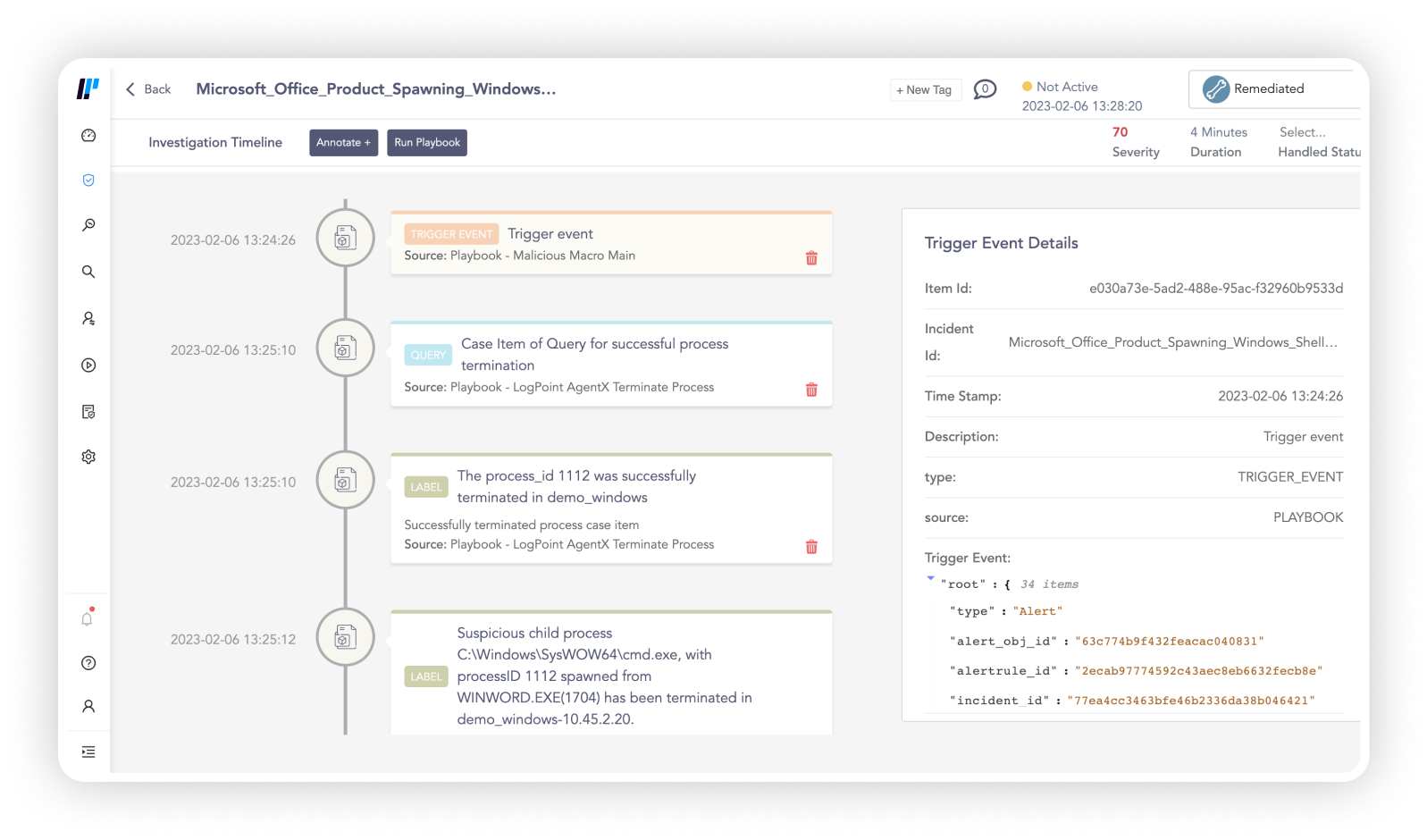
Manage cyber threats and reduce business risk
Our all-in-one converged platform provides all the necessary data to support security outcomes.
Logpoint surfaces high-value true positives that provide threat context to optimize the efficacy of the broader security infrastructure.
With sophisticated machine learning and detection logic, fuse weak signals and utilize automation to provide contextual information from threat and vulnerability sources to manage cyber risk across the IT environment.
Easy and cost-effective to maintain and manage
With often limited budgets for cybersecurity spending, we facilitate businesses in adopting a cloud-first strategy with our easy-to-manage SaaS platform.
Remove the headaches of implementing and maintaining an advanced security operations platform such as deployment, architecture, product updates and maintaining data center capabilities, including storage.
We are pulling logs from endpoint clients and cloud applications, in particular, Office365. It is incredibly easy to integrate Office365 logs in Logpoint, and it often provides an easier way to query non-standard data than in the native Office365 administrator portal.
Logpoint SIEM allows us to monitor the state of our infrastructure continuously and provides alerts if something out of the ordinary is occurring. In addition, it provides us with the necessary tools to drill down into an incident and to establish whether there is a technical problem, user error, or an actual breach of security.
Get up to date with the
Logpoint blog!