Staffing shortages, budgeting
issues and inadequate analytics
Recruiting and keeping skilled cybersecurity staff is difficult because of the skill gap. It’s estimated that there is a 3.4 million global cybersecurity talent shortage. More than 74% of cyber professionals say the gap puts their organization at extreme-to-moderate risk of cyber attack. To help address the shortage, organizations are investing in technology, but it’s difficult to determine what tech and how to prove the value of it.
Converged security platform that
automates across the technology stack

Reduce staffing shortage
Automate processes to increase efficiency without requiring additional security staff

Predictable TCO
Platform licensing is not based changing factors, like data, making it easy to manage cyber budgets
Improve security efficacy
End-to-end platform detects high-value incidents and adds threat context to accelerate response
Improve operational efficiency and increase productivity
Automation makes security teams more efficient providing structured workflows for many day-to-day security analyst tasks.
Logpoint gathers and prioritizes security data and alerts to help analysts identify and resolve incidents fast.
Investigate alerts and recommends a response so analysts can simply approve or execute a decision.
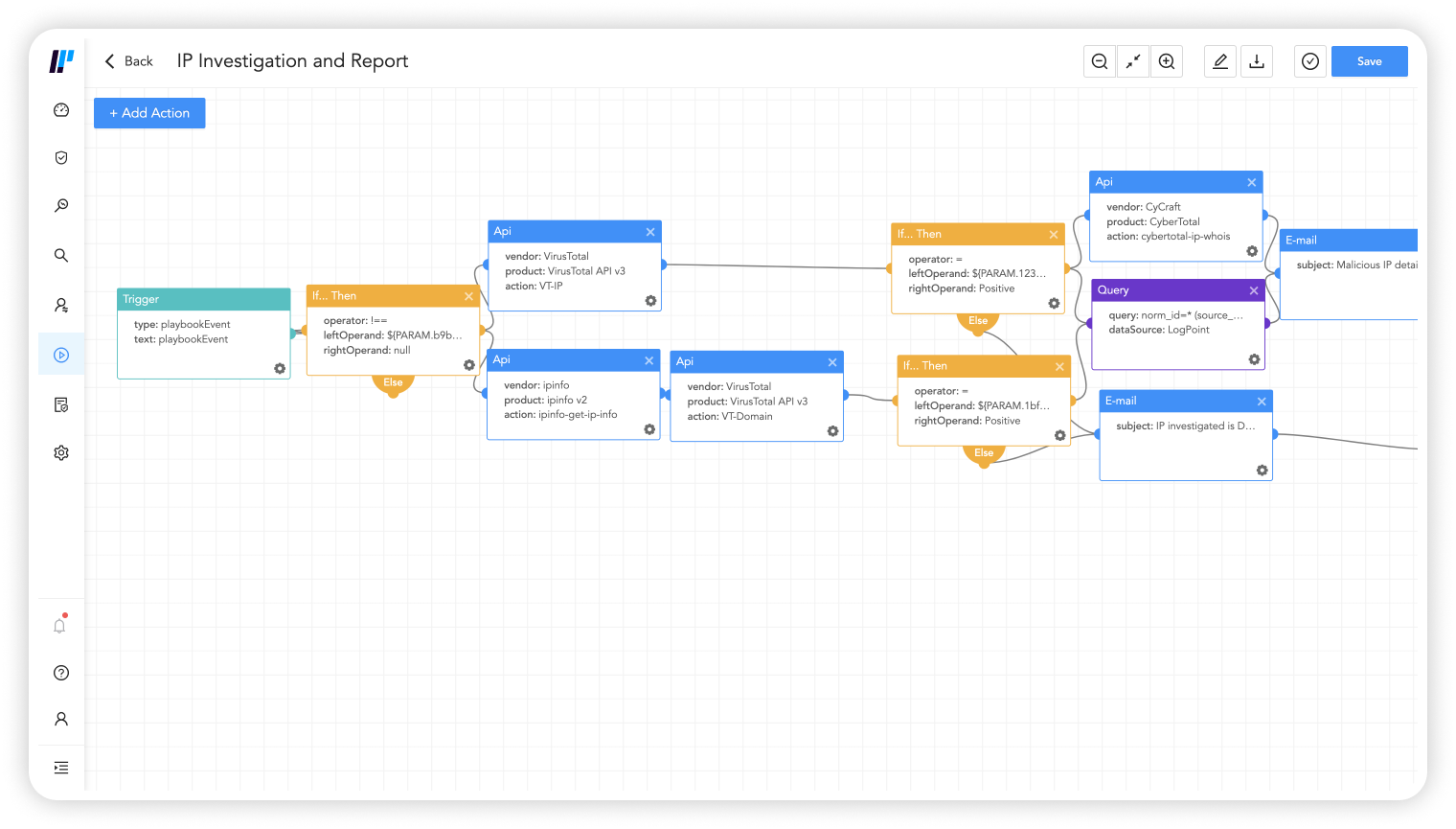
Reduce time needed to maintain security tools

Logpoint is a converged security operations platform that combines data analysis, incident automation, behavior analytics, business-critical security and endpoint security.
Without any additional integration needed, Logpoint offers a broad set of features to help limit the complexity, cost and friction of IT and security teams.
Accelerate detection, investigation and response
Logpoint uses machine learning and detection logic to fuse weaker alerts into high-value cases. Logpoint automatically adds contextual information from threat and vulnerability sources to prioritize investigation and response.
Weaker signals serve as indicators as part of larger cases, eliminating time spent on false positives.
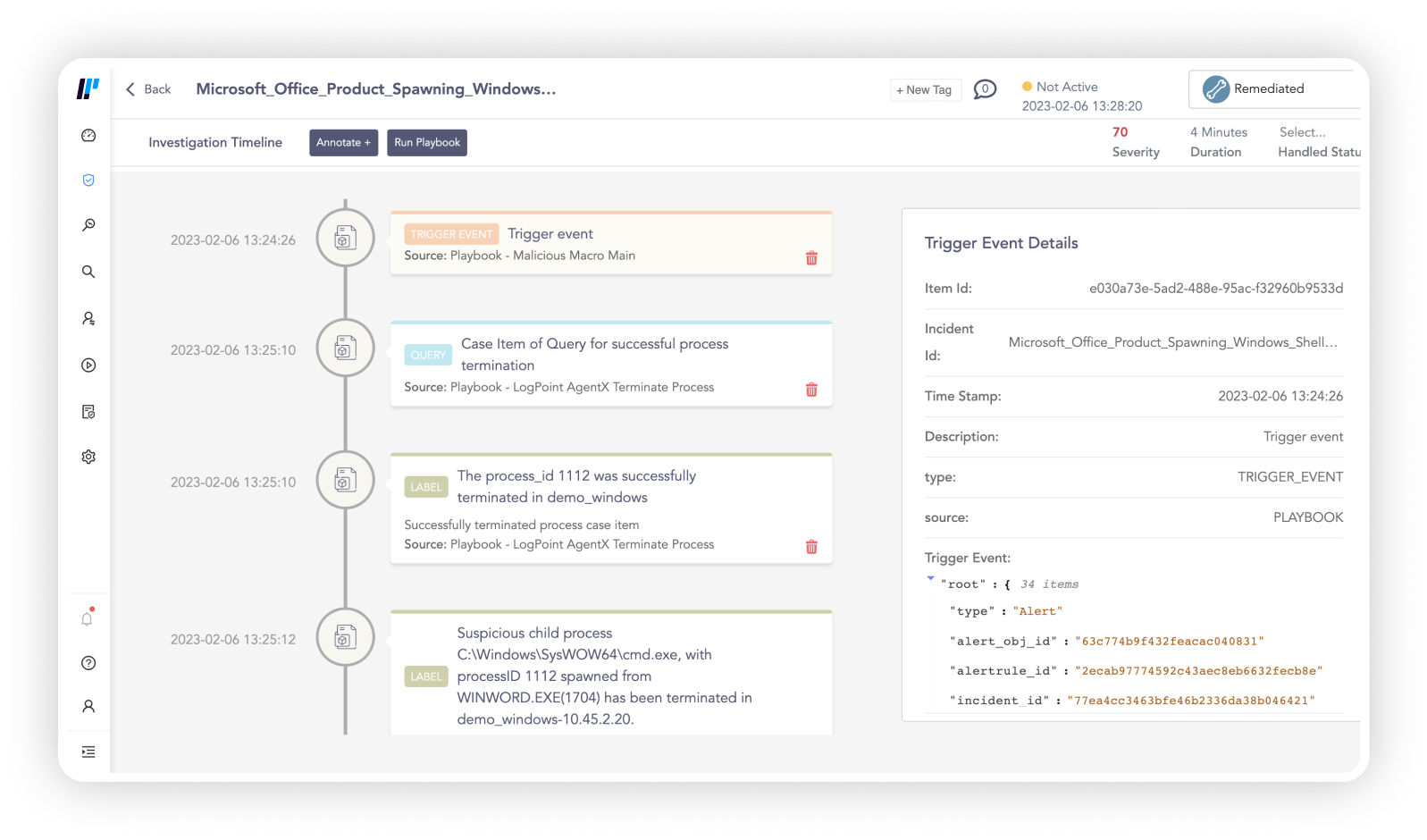
Over the last 3.5 years, our use of Logpoint has grown considerably. We do not see it as a point product, but a solution that has grown with our business. And the fact that it is not only deployed for security makes it all the more valuable. Logpoint is with us for the long run.
Previously we would take turns spending hours analyzing the logs of the previous day. It was a dreadful and time consuming task. Today everything is nicely served up, and if anything is missing, I’ll just take 15 minutes to create a dashboard that will tell me what I need. A 50% reduction was the target, but in reality, it’s more like 75%.
Get up to date with the
Logpoint blog!