Cybersecurity for Healthcare and Pharmaceutical Organizations
Protecting Patient Data
Healthcare and pharmaceutical organizations are particularly vulnerable and targeted by cyberattacks because they possess a wealth of information and intelligence of high monetary value. The targeted data related to patients includes health information (PHI), financial information like credit card and bank account numbers, personally identifiable information (PII) such as Social Security numbers, and intellectual property related to medical research and innovation.
Safeguarding sensitive data against misuse is key to meeting the GDPR regulations and ensuring compliance.

Ensure NIS2 Compliance with Logpoint
NIS2 Directive is stepping into force, striving to enhance protection of critical infrastructure in EU from cyberthreats. It introduces stricter security demands, reporting obligations and enforcement requirements for a broader scope of sectors. Inability to comply can impose fines up to 2% of the worldwide turnover.
Why Logpoint
Healthcare and pharmaceutical industry is highly digitalized, using a broad array of proprietary applications and systems to manage the daily operations. For example, specialized hospital information systems such as EHR systems, practice management support systems, computerized order entry systems, file storage system, and in addition to this, thousands of devices that comprise Internet of Things that also must be protected.*
Getting a complete threat visibility and contextual understanding in a complex landscape is difficult. Converged SIEM is a unified threat management platform that helps you collect, analyze and effectively respond to cyberthreats across all your systems, all in one place.

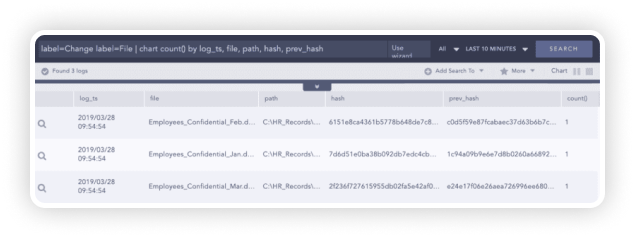
File Integrity Monitoring
Achieving HIPAA compliance is a complex task but maintaining it can often be even more cumbersome. Logpoint’s native FIM calculates the hash value of files, before and after changes could have been made, so you will always be in control of your sensitive assets and get alerted whenever a new directory or file is created, deleted, renamed or altered in its content. Additionally, FIM also monitors any creation or deletion of the files and directories.
Detecting Access to Systems
With Logpoint, you can easily detect users and systems accessing other systems along with other important contextual information such as the actions performed, the final status, or other entities used, like IP addresses. Monitoring access control helps verify users viewing systems and resources. Logpoint can detect activities such as failed and successful logins, various login attempts, users locked or unlocked. See more use cases here.*
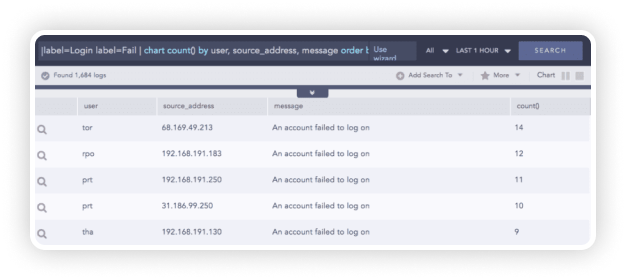
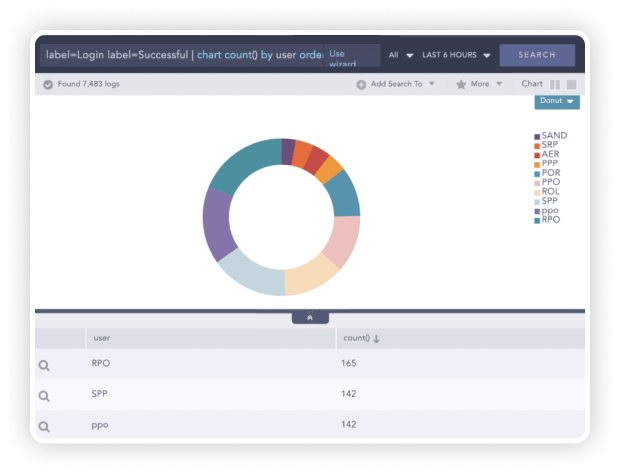
Authentication and Transmission Control
Logpoint automatically detects activities such as email, https and VPN communications to make audits of transmission controls easier. By design, Logpoint enforces authentication and transmission control for data security, maintained locally inside Logpoint or through a remote authentication server such as LDAP and Radius. Similarly, for transmission controls, Logpoint uses secure communication channels for interaction between an external object and a Logpoint instance or between multiple Logpoint instances.
Use Case:
Logpoint for Region Värmland
With Logpoint, Region Värmland has:
- ensured protection of patient integrity
- reduced false positives
- achieved compliance with the Swedish Patient Data Act
By logging medical record views, Logpoint has helped Region Värmland ensure patient data confidentiality and provide a detailed report containing views with missing care relations.

The strength of the Logpoint solution is that we don’t have to spend unnecessary time on investigating false positives and that we check all logs. Not only logs chosen at random. This way, we comply to the legal requirements of effective log auditing.
Get up to date with the
Logpoint blog!