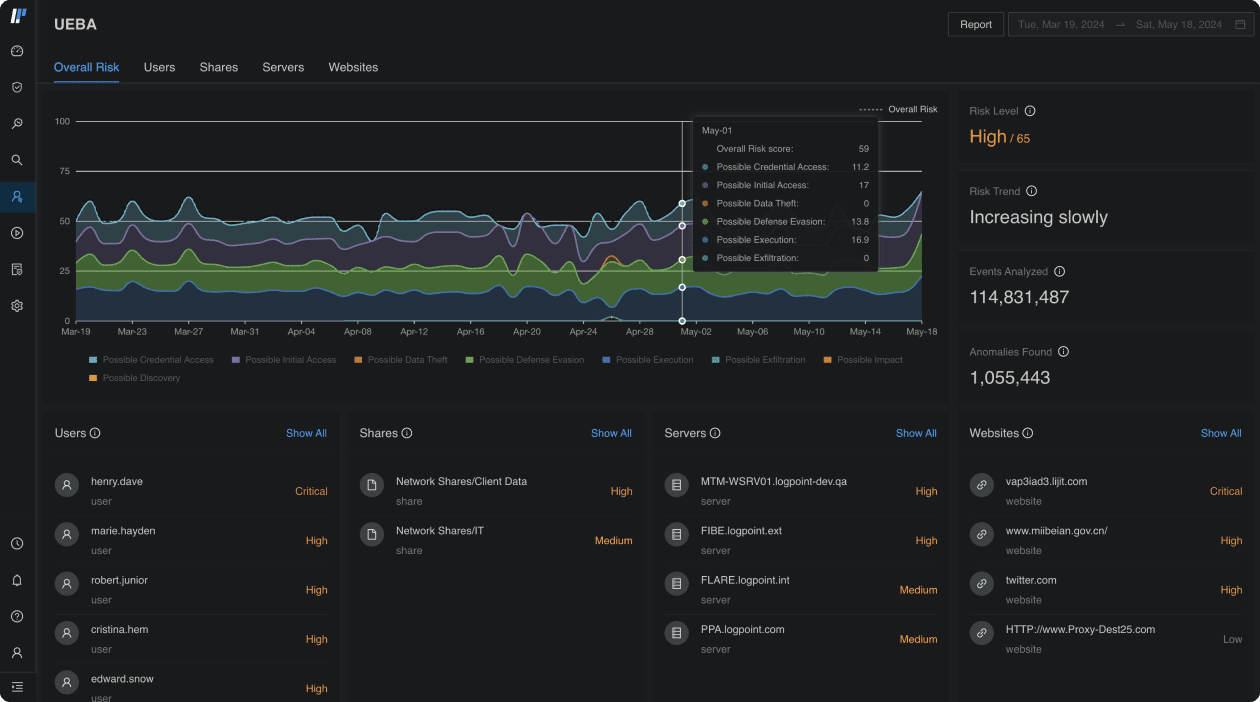
Anticipate identity, data and infrastructure risks
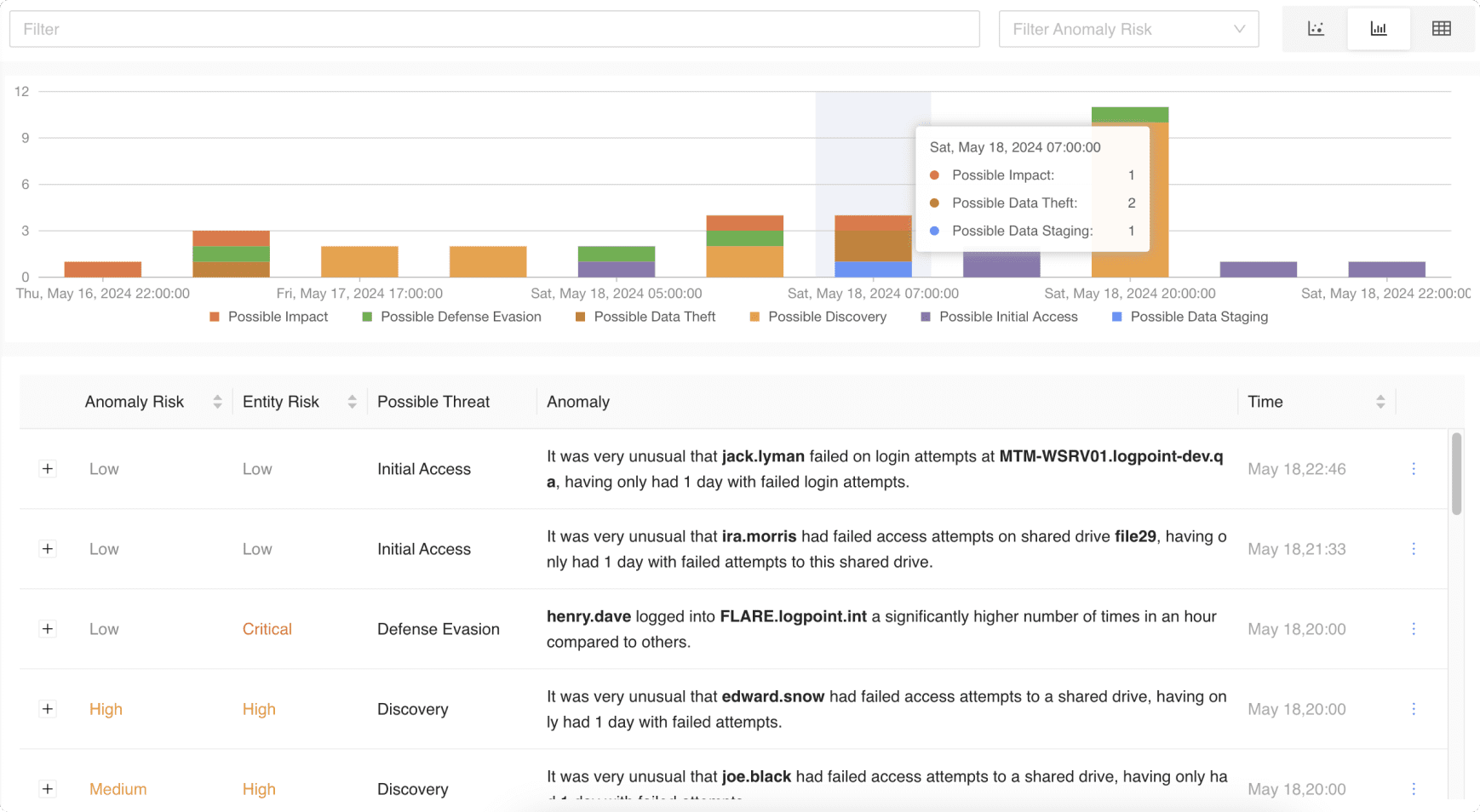
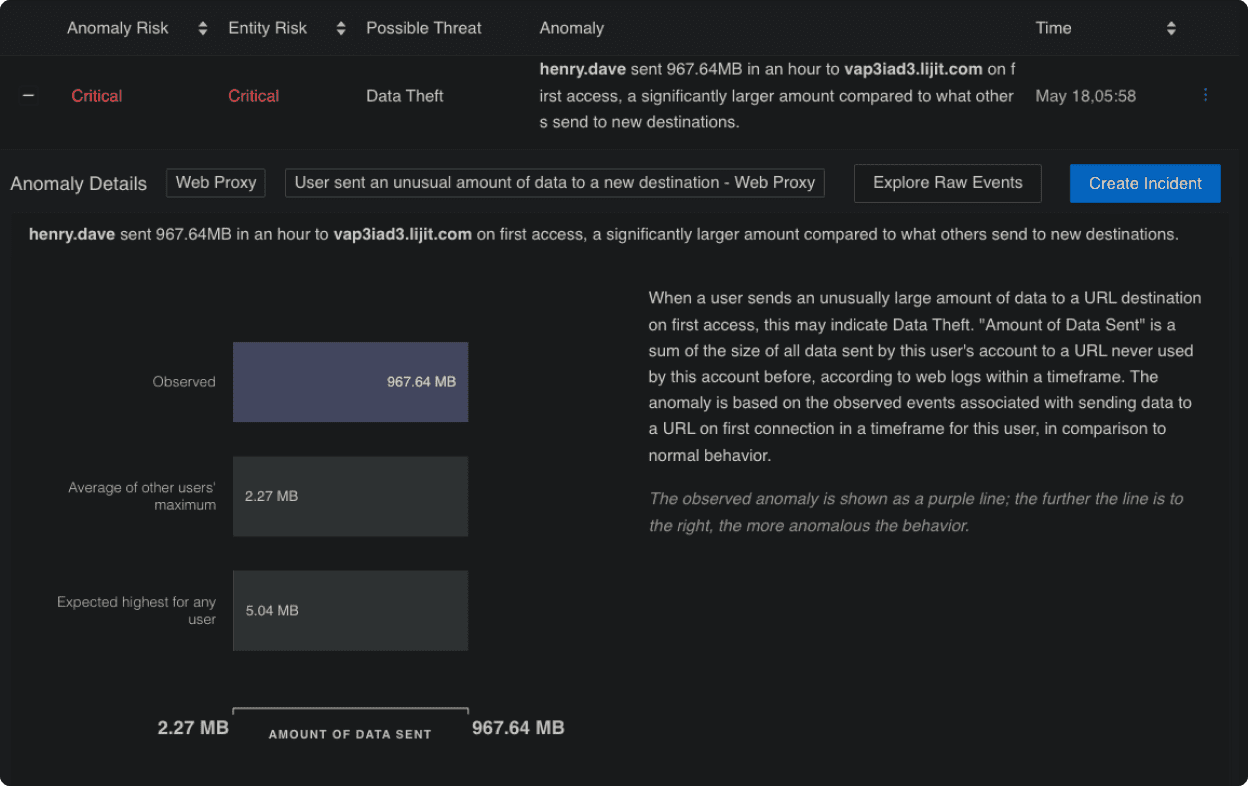
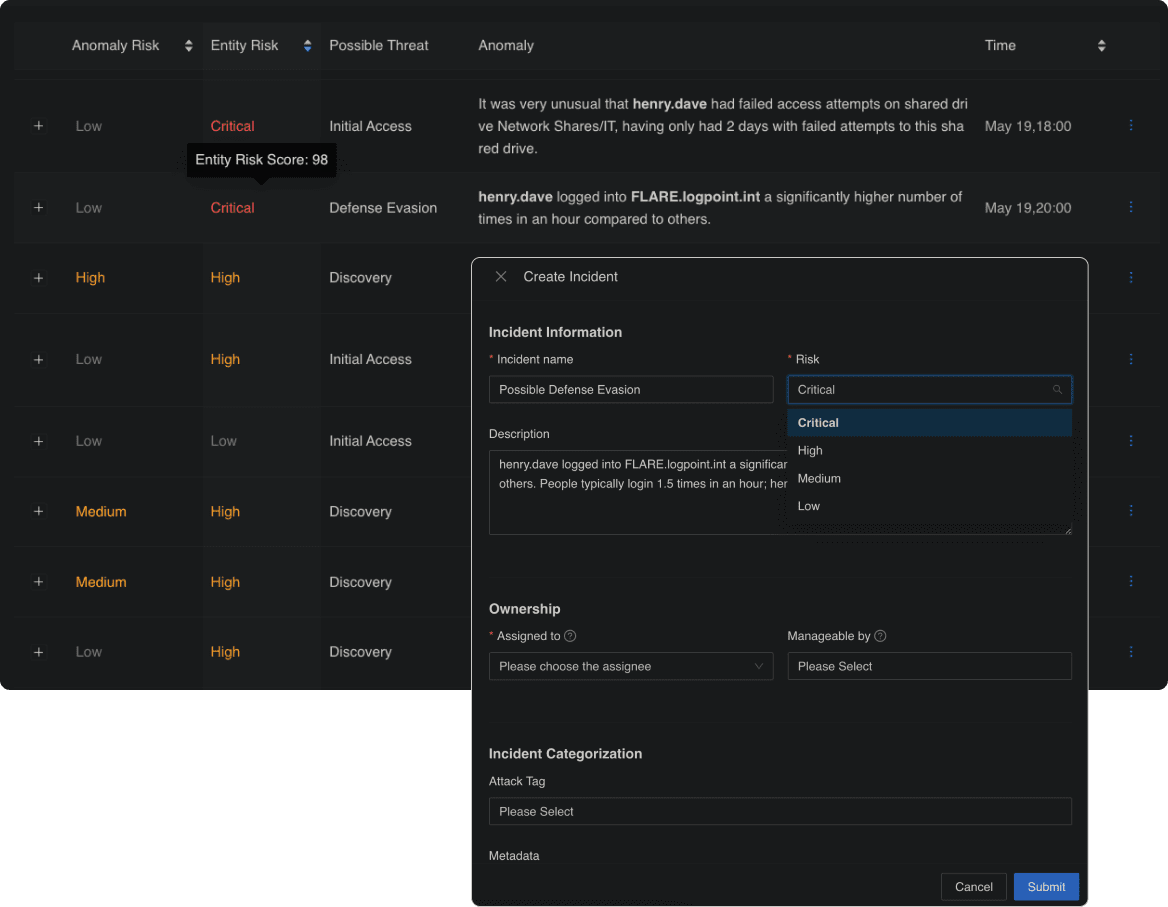
- Detect insider threats: Whether they are malicious insiders or the result of unintentional actions, automatically detect deviations from behavior baselines.
- Uncover compromised entities: Anomalies in your IT systems don’t go unnoticed to prevent operational disruptions, DDoS attacks or major outage.
- Prevent data staging and exfiltration: Spot breaches and track what data is accessed and by whom to stay compliant and avoid costly fines.

Over 1,000 Organizations Across 70 Countries Trust Logpoint
From SIEM to Cyber Defense
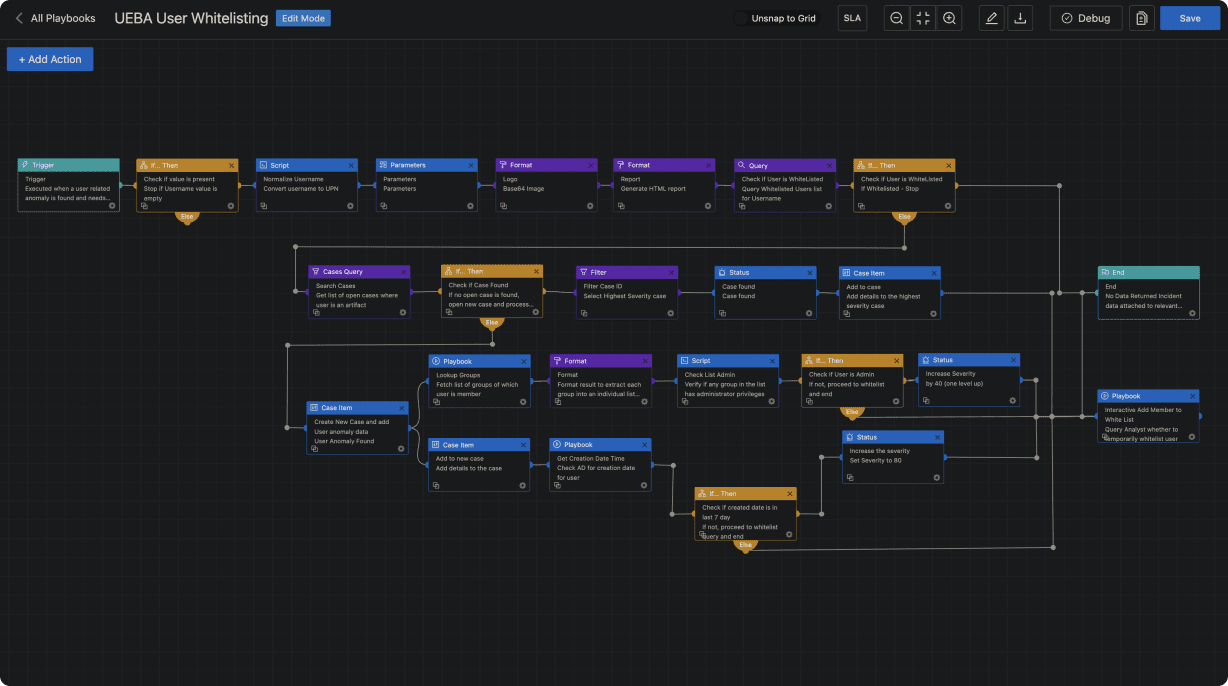
Looking to consolidate your tech stack? See how Logpoint SIEM fits with Automation, Case Management, and Behavior Analytics in one platform that combines data sets from multiple sources. Instead of using multiple standalone products, you can unify your security needs under one single source of truth.
- Full data integration for automated TDIR
- No integration or maintenance required
- Out-of-the-box compliance support
- Flexible deployment based on your needs