Public Administration
With the increasing digitalization of the public sector and its services, granting secure and seamless access to critical services is becoming a strategic priority. However, due to the intricate infrastructure covering regional, national, and even overseas levels, providing sufficient protection can be difficult. Logpoint delivers comprehensive threat detection, analysis, and response so you can effectively spot and counteract threats.
Ensure NIS2 compliance with Logpoint
NIS2 Directive is stepping into force, striving to enhance protection of critical infrastructure in EU from cyberthreats. It introduces stricter security demands, reporting obligations and enforcement requirements for a broader scope of sectors. Inability to comply can impose fines up to 2%* of the worldwide turnover.
WHY LOGPOINT:
Detecting Lateral Movement
Logpoint uses a mix of endpoint, Active Directory, and repository data to scan for suspicious behaviors deviating from the baseline. These include:
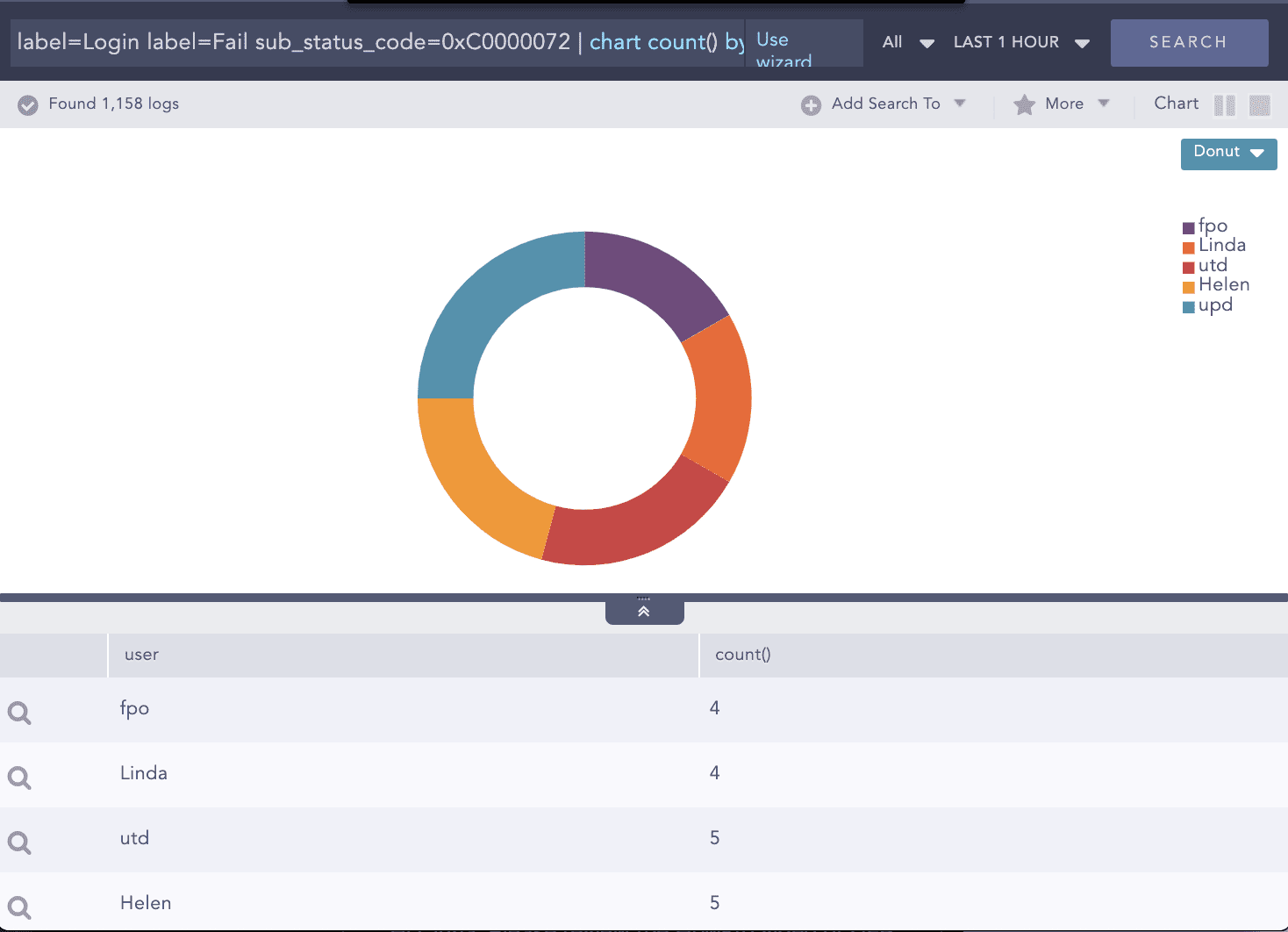
- Login failed attempts on disabled accounts
- Unusual activity by day of week or time of day
- Unusual access to servers, file shares, applications or other resources
- An unusually high amount of access to certain resources
- Anomalous application usage and anomalous access patterns to storage
Example – Login failed attempts on disabled accounts
WHY LOGPOINT:
Detecting Data staging and exfiltration
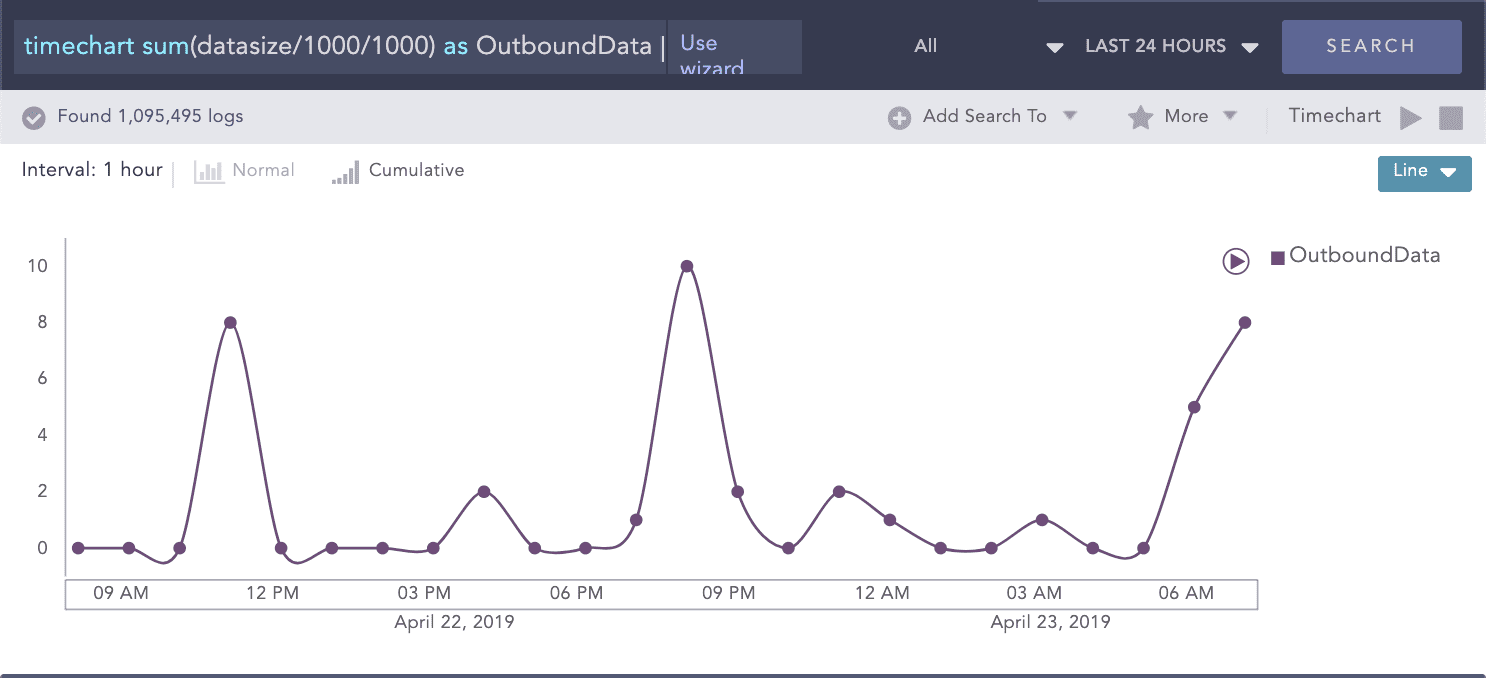
Compromised accounts or machines are usually trying to move data into staging areas where they can be easily withdrawn from the organization’s network. While preparing the data for removal, attackers will utilize tools such as PSExec or remote desktop tools. With Logpoint you can detect staging and lateral movement, including (the highly unusual) intra-workstation high-volume data transfers, unusual protocol/port combinations, and unusually high amounts of data access. Stay on top of high outbound data transfers.
Use Case:
Logpoint for Durham County Council
With Logpoint, the County Council instantly saved 50% cost compared to their previous vendor – and additionally improved their SIEM capabilities:
- Making compliance and accreditation requirements to be met comprehensively
- Due to the simple per node pricing structure it can be widely deployed, and more data can be fed into it
- Easy distribution of rights enabling e.g. the Service Desk to perform their own searches and solve cases more effectively
The outstanding offering – in terms of features, look and price – was Logpoint.