Introduction
XZ Utils is a set of open-source compression utilities for compressing and decompressing files using the LZMA compression algorithm, known for its high lossless compression ratio. XZ Utils is famous for compressing release tarballs, software packages, kernel images, and initramfs (initial ram file system) images. It’s favored for significantly reducing file sizes while maintaining data integrity. This utility is so widely used that it’s typically pre-installed on most Linux and macOS systems, making it readily available for users without additional installation steps.
Go To Section
Background
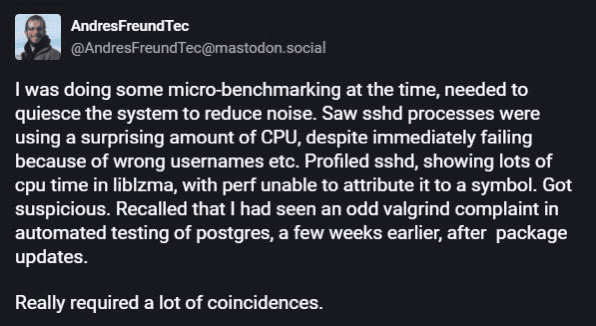
Microsoft engineer and PostgreSQL developer Andres Freund went about normal job activities when he noticed some lag in his SSH connection. Upon investigation, he observed that sshd processes consumed an unusually high amount of CPU. This prompted him to profile sshd, where he discovered excessive CPU time being consumed by liblzma. Further investigation led to the discovery of a backdoor in xz/liblzma, which he emailed his findings to oss-security on Friday, 29 March 2024.
The cybersecurity community quickly erupted over the weekend when they realized a backdoor in the most recent versions, 5.6.0 and 5.6.1, of XZ Utils. This incident was identified as a supply chain attack, where a GitHub account, handled by Jia Tan (also known as Jia Cheong Tan or JiaT75), had pushed malicious packages and successfully got it merged them into the open-source library xz/liblzma. Following this revelation, CVE-2024-3094 was assigned to this backdoor, with a CVSS Score of 10, indicating the severity of the vulnerability that could allow remote code execution.
The GitHub account handle was created in 2021 and contributed to the XZ project nearly two years ago. They gradually built credibility within the community until they were granted maintainer responsibilities. According to Hackernews, Through additional cunning social engineering, it is suspected that sockpuppet accounts such as Jigar Kumar and Dennis Ens were utilized to submit feature requests and report various issues in the software. This strategy aimed to compel the original maintainer, Lasse Collin of the Tukaani Project, to appoint a new co-maintainer to the repository. In 2023, Jia Tan implemented a series of modifications to XZ Utils, which ultimately became integrated into the release version 5.6.0 in February 2024. Unknown to the community, these modifications concealed a sophisticated backdoor. During the build process, the xz build system included the backdoor in the liblzma library. This backdoor was shipped as part of the binary within RPM or DEB packages for the x86-64 architecture. Essentially, the malicious code was embedded within the XZ compression library itself2.
Thomas Roccia has shared a chart about the XZ outbreak through the X platform, providing an introduction, a GitHub activity summary of JiaT75 user activity on xz repo, and backdoor details, illustrated below.
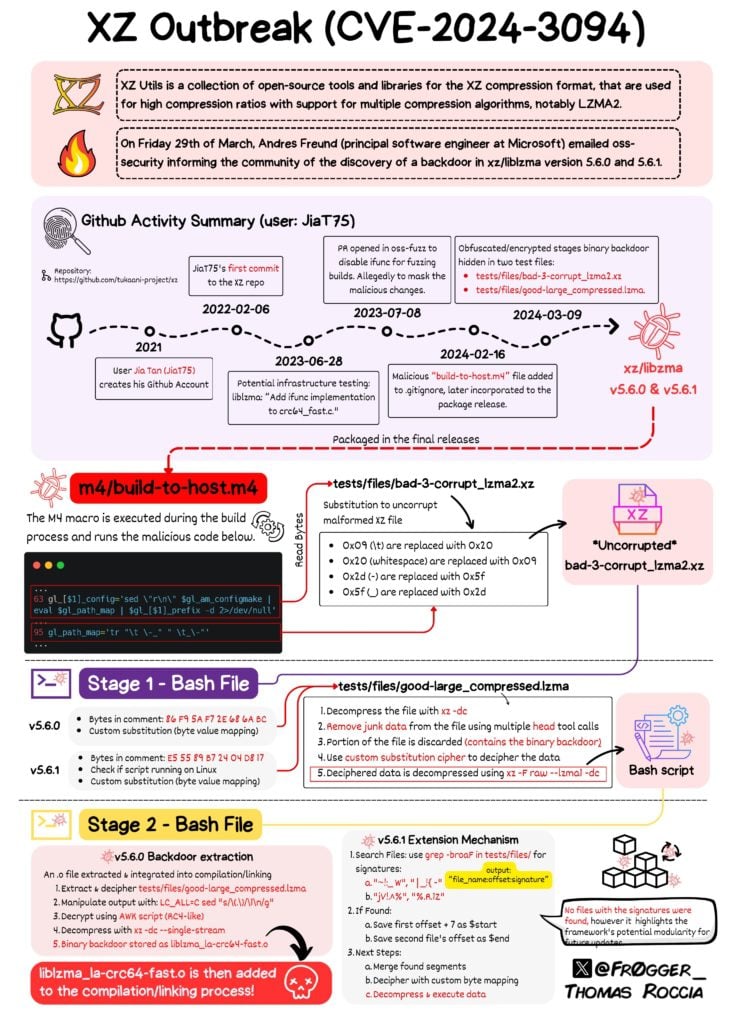
XZ Outbreak(Reference)
Who is affected?
Various Linux distributions and MacOS are susceptible to this vulnerability if the following conditions apply to your system:
-
You use a distribution that relies on glibc (for IFUNC).
-
You have versions 5.6.0 or 5.6.1 of xz or liblzma installed (xz-utils includes the library liblzma), which is typically the case for users who consistently update their rolling-release distributions.
The certainty regarding the vulnerability extended only to the combination of systemd and patched OpenSSH at present. The status remains undisclosed within the community, with uncertainty regarding the vulnerability's impact on other configurations.
According to Brjann Brekkan of Microsoft, multiple Linux distributions, including Fedora, Debian, openSUSE, and Kali Linux, have been impacted by a backdoor discovered in the XZ Utils library. Updates and advisories are being issued as the situation unfolds. As the situation evolves, we anticipate further clarity on additional impacted distributions, and updates will be provided.
Detection with Logpoint Converged SIEM
Logpoint Converged SIEM is a comprehensive security platform comprising SIEM, SOAR, and endpoint security. Logpoint's native, lightweight agent AgentX is designed to collect logs and telemetry from endpoints, transmitting them to the SIEM. Leveraging the capabilities of SOAR, AgentX conducts automated real-time investigations and remediation of threats.
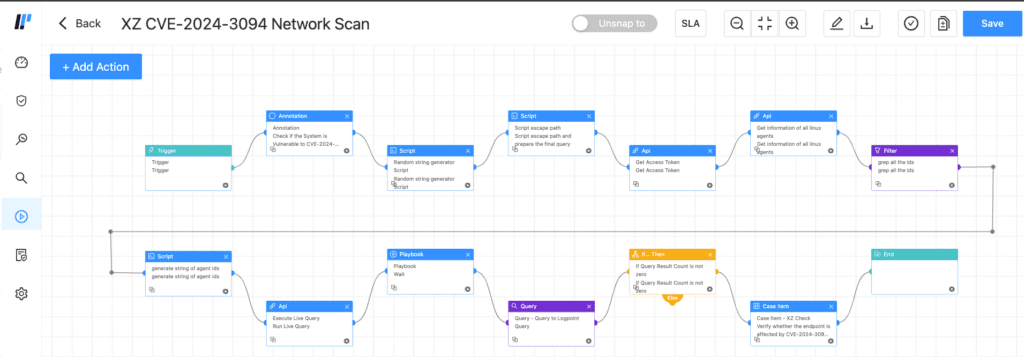
One of the standout features offered by AgentX is Osquery. If you're already utilizing AgentX, you're in luck, as you can leverage Logpoint Converged SIEM with AgentX and Osquery to identify potentially CVE-2024-3094 vulnerable systems on your network. We have generated a playbook tailored for this case. With the power of AgentX and Osquery in conjugation, this playbook will scan for the Linux endpoints that may be vulnerable to CVE-2024-3094.
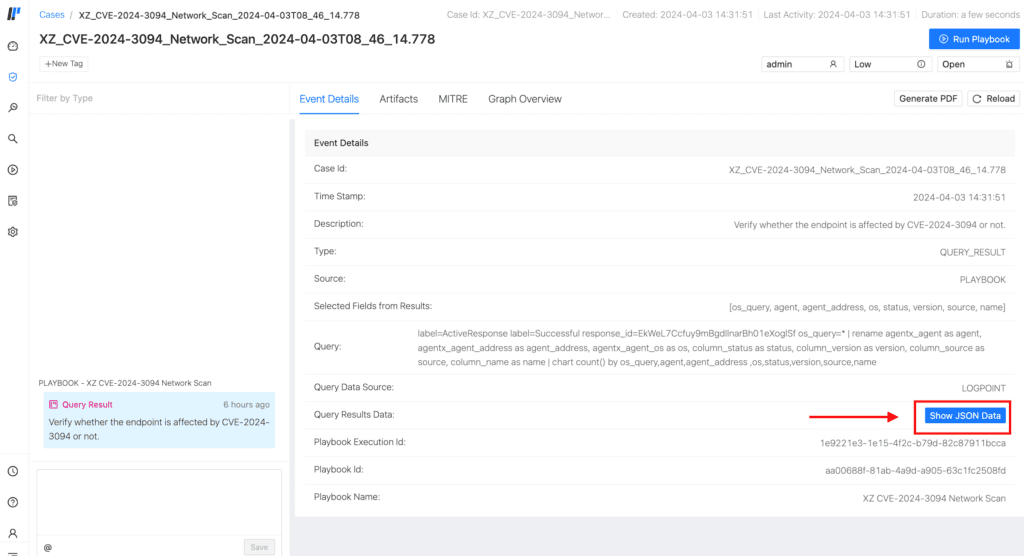
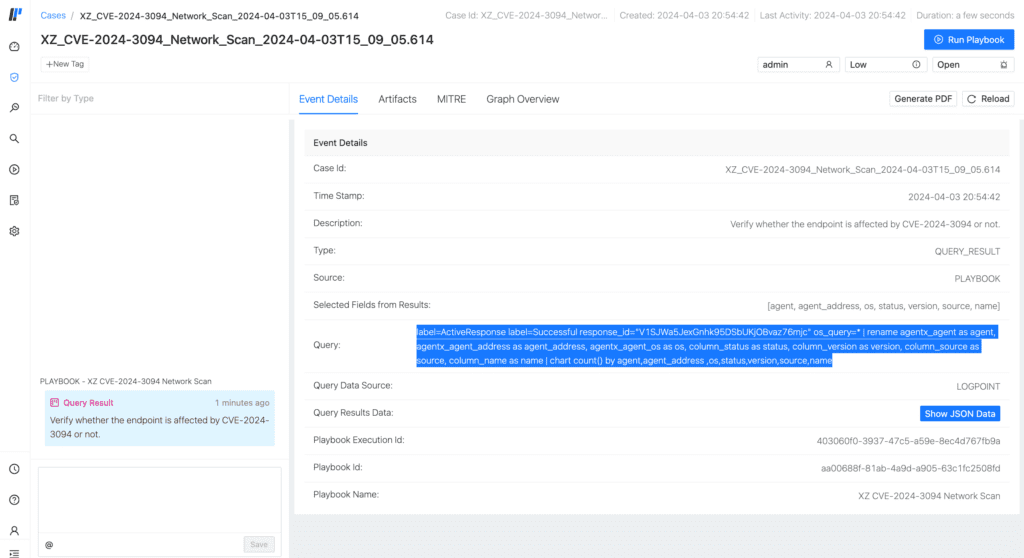
The execution flow of this playbook begins with obtaining a list of Linux agents enrolled in an AgentX Manager. Subsequently, it queries each Linux machine to determine each system's installed version of xz/liblzma through OSquery. The version is deemed potentially vulnerable if identified as either 5.6.0 or 5.6.1. Conversely, if the version differs, it is most likely not vulnerable. All this information is then collected in Logpoint, enabling visualization through Logpoint Case Management, as illustrated in this screenshot of the case generated after the successful execution of the playbook.
In the displayed case, all results have been retrieved and can be accessed by selecting the "Show Json data" button. Upon doing so, a floating window containing the results is presented.
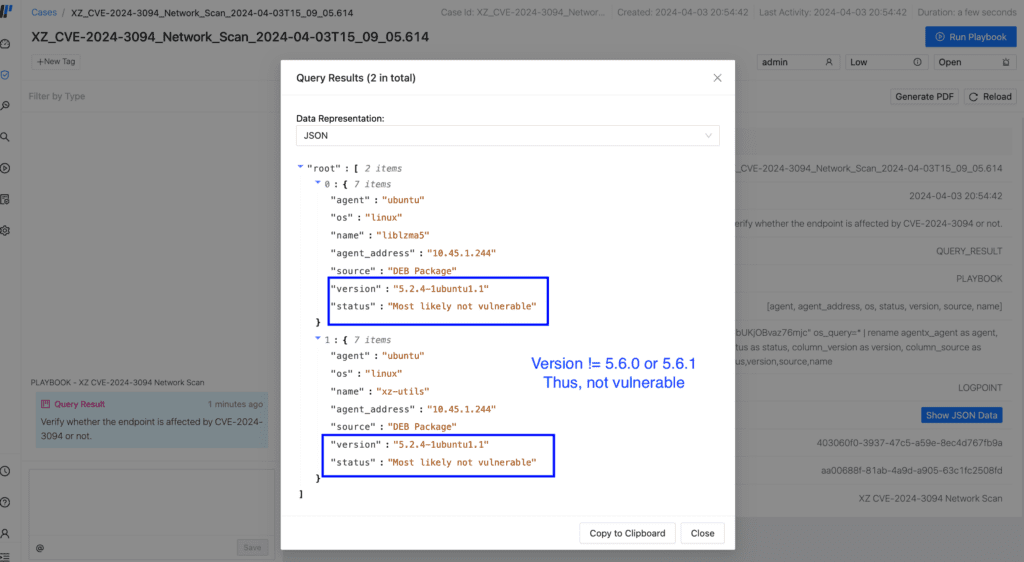
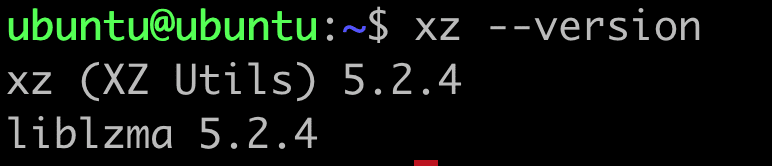
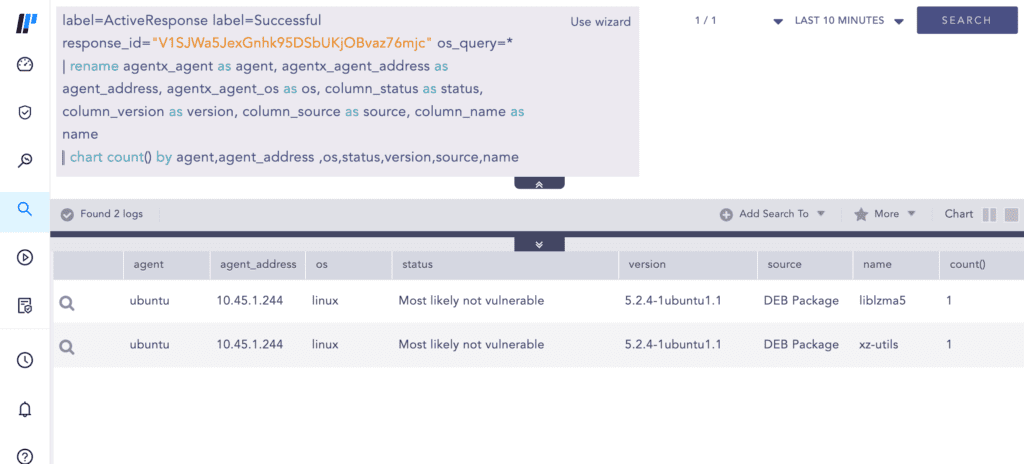
In this case, we had only one agent enrolled in AgentX. Thus, only two results for packages liblzma5 and xz-utils are displayed. Their version was also found to be 5.2.4 (less than 5.6.0), hence not vulnerable, denoted by the "status" key, as observed in the screenshot above. We double-check that in the Linux agent to double-check the version of the xz/liblzma library.
For enhanced visual experience, the "query" from Event Details can be copied from the Case to Logpoint Search UI.
The Search UI offers a more concise view and enhanced visibility, which is particularly beneficial in scenarios with numerous query results.
Furthermore, even without AgentX and Logpoint, detection of vulnerability to CVE-2024-3094 is feasible through Osquery. The SQL query provided by @jamesspi can be employed for this purpose. However, it necessitates local execution on each Linux machine.
Alternatively, you can also use this query shared by Bitdefender.
Possible Exploitation Detection
Suppose you have Sysmon for Linux installed on your machine, and you are collecting those logs in Logpoint. You can use this Sigma rule to detect possible indicators of exploitation of CVE-2024-3094.
Recommendations
-
Execute the 'XZ CVE-2024-3094 Network Scan' playbook on your enterprise to detect potentially vulnerable devices.
-
Downgrade XZ Utils to an uncompromised version like 5.4.6 Stable after all vulnerable devices have been located.
-
If you're using an affected distribution, follow these steps:
-
Fedora 40: Update to the latest version (5.4.x).
-
Fedora 41 & Rawhide: Stop using immediately.
-
Debian: Update to the latest version (5.6.1+really5.4.5-1).
-
Alpine Edge: Update to the latest version (5.6.1-r2).
-
Kali: Update to the latest version (5.6.1+really5.4.5-1).
-
OpenSUSE Tumbleweed: Update to the latest version (5.6.1.revertto5.4).
-
Arch Linux: Update the latest version (5.6.1-2).
-
-
Suppose post-compromise activity is suspected, such as creating new users despite downgrading the XZ version. In that case, the compromise might be more extensive and sophisticated than initially thought. Taking comprehensive steps to remediate the situation effectively is crucial in such a scenario.
-
If a version that has been compromised was downloaded, it is essential to reset the passwords for all affected accounts.
-
It's essential to stay abreast of the ongoing developments related to the XZ supply chain vulnerability since new updates and information are surfacing regularly. Remaining up-to-date is vital to ensure that no significant news or advisories are overlooked.
-
Stay updated with our Emerging Threats Protection Reports, released by Logpoint every month. Reviewing these reports and applying the analytics provided in your Converged SIEM platform enables you to remain informed and enhance your security against emerging threats.