Providing free and easy access to digital resources is a key issue for Universities across the world. New generations of students and researchers have high expectations for free and easy access, but there are growing concerns about safety and privacy.
At the same time, educational institutions keep large amounts of personal data from students, faculty, applicants, administrative staff and alumni while storing state-of-the-art research and valuable intellectual property. Sensitive data and a large attack surface make universities a vulnerable target.
Logpoint has worked with universities and colleges for years and have received great peer reviews. Based on this experience, we have developed cybersecurity use cases that help create a safer digital environment and support more efficient cybersecurity operations. Use cases include:
- Cybersecurity and Compliance
- Safeguarding Students using Big Data, not Big Brother
- Strengthening Security and Eliminating False Positives
- Preventing copyright Infringement
With Logpoint, colleges and universities can leverage advanced analytics, accelerated by Machine Learning, to improve their cybersecurity posture and efficiently automate relevant responses to both internal and external threats.
Download our solution brief to learn more about how to get going with SIEM and UEBA for educational institutions:
Logpoint for University of Bedfordshire
With Logpoint, the University of Bedfordshire’s IT team has:
- simplified management of network alerts
- improved their ability to identify incidents requiring action
- saved on operational costs
By converting data into actionable intelligence and improving their cybersecurity posture, Logpoint has reduced time-consuming analyses of security logs while eliminating the majority of false positives.

Safeguarding Students
In addition to the technical challenges in Cybersecurity, Educational institutions are facing a separate issue in Safeguarding students. Essentially it is preventing and protecting students from exposure to materials that may cause themselves or other individuals to come to harm.
The safeguarding approach many Universities take is to block specific websites entirely, limit internet usage on public networks, and closely monitor the activity taking place there. However, this approach contradicts the goal of providing free and easy access to digital resources.
What is needed is context, and that’s where the analytical power of the Logpoint SIEM and UEBA solutions, based on Machine Learning, can help. Universities can correlate behavior and metrics to make informed decisions – quickly and efficiently, to safeguard students.
Threats
There are many potential actors when it comes to breaches in the educational industry. While targeted attacks are perhaps not a surprise, you shouldn’t discard the students themselves, who sometimes, due to boredom or curiosity, may end up as the catalyst of a breach. Whether intentional or accidental, you need protective measures in place to prevent it from happening.
Facing a Special Insider Threat
There are many potential threat actors when it comes to breaches in Education: students, faculty, applicants, administrative staff, alumni, collaborators, research and project participants and vendors who access the relatively open academic environment.
However, students are a group of particular interest. Young, energetic and perhaps attending a course in ethical hacking during the day, they might be tempted to test newly acquired skills during the night.
It may be due to boredom or curiosity, that students end up as the catalyst of a breach. Whether intentional or accidental, universities need protective measures in place to face the insider threat.
Download our solution brief to learn about cybersecurity challenges in Education and how Logpoint SIEM and UEBA solutions can help solve them.
User Activity Monitoring
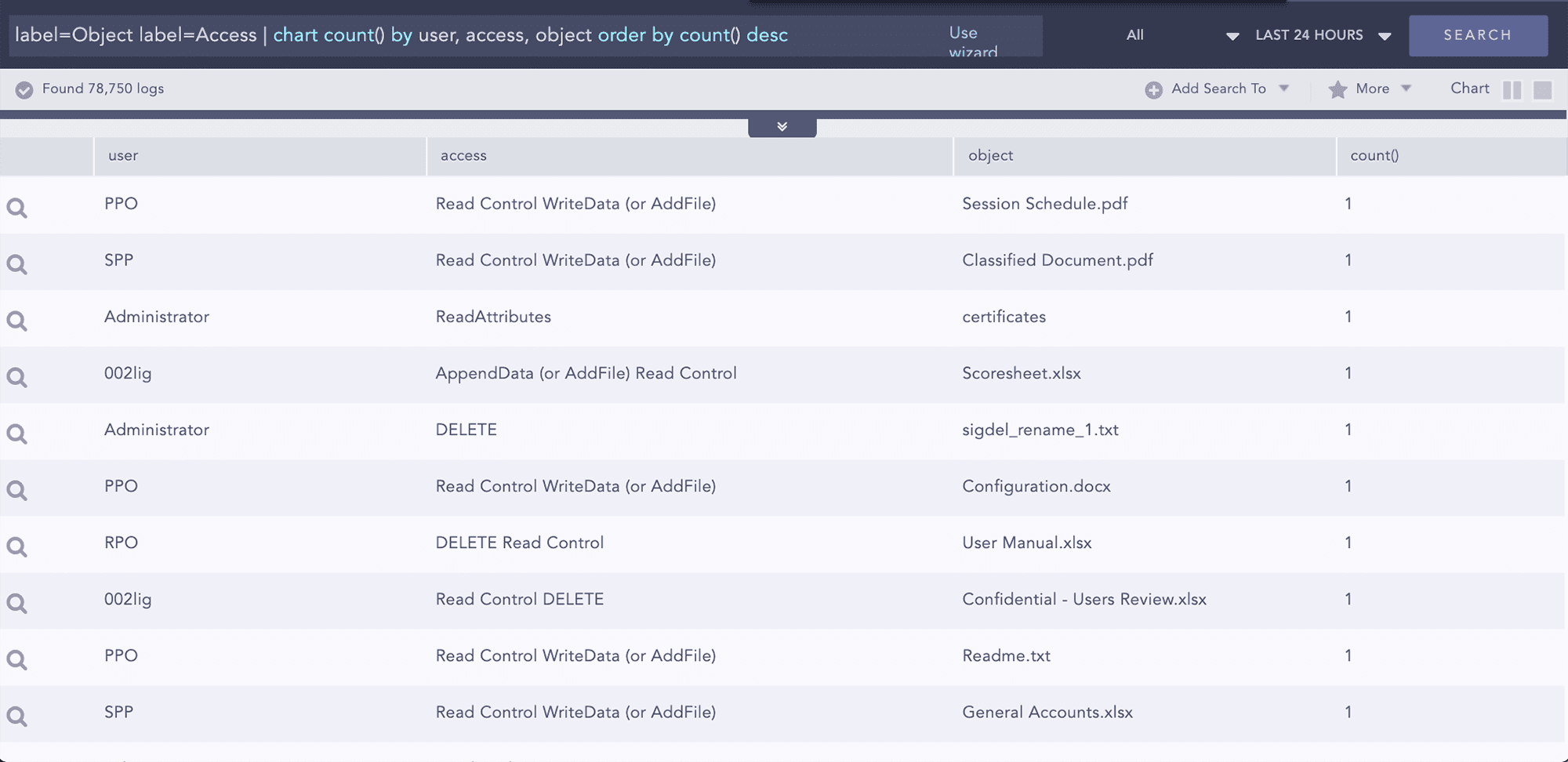
User Activity Monitoring has long been the cornerstone of any efficient defense strategy. By design, Logpoint provides analysts with an intuitive and powerful tool to identify malicious activities, create alerts, dashboards, and reports so they can get an overview and counteract immediately. Primarily for data privacy and regulations, user activity monitoring focuses on activities associated with file access. Logpoint can monitor this using native object access audit records. Additionally, Logpoint’s FIM application monitors any access attempts to privileged file share systems and provides information on the type of access and the actions performed in the file. Additionally, the original and the altered checksums can also be compared to better understand access behavior.
Advanced Analytics Correlation and Pattern Recognition
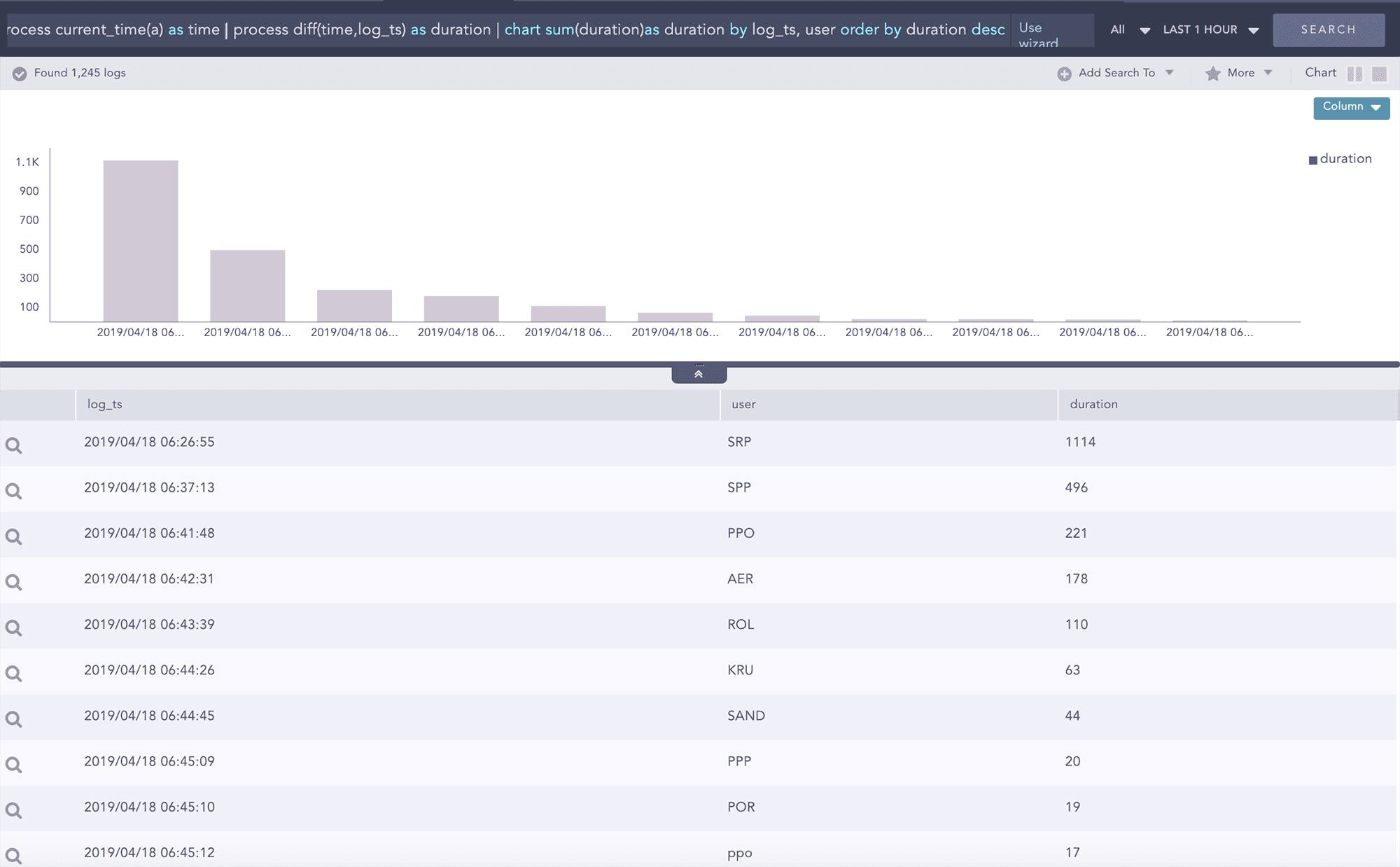
By default, Logpoint can perform advanced correlation of any number of data sources – internal, external, or structured. Whether it is something as simple as aggregation between two or more groups of entities such as user and source address for failed logins or combining records in multiple log messages across multiple data sources using join and followed by queries, we will provide you with real-time alerts on risky behavior, and anomalous activities. In Logpoint, Dynamic lists can also be used to perform advanced correlations in a number of ways such as creating a dynamic list with IP addresses or hostnames for vulnerable workstations to identify any potential exploitation of a vulnerability by a threat source.
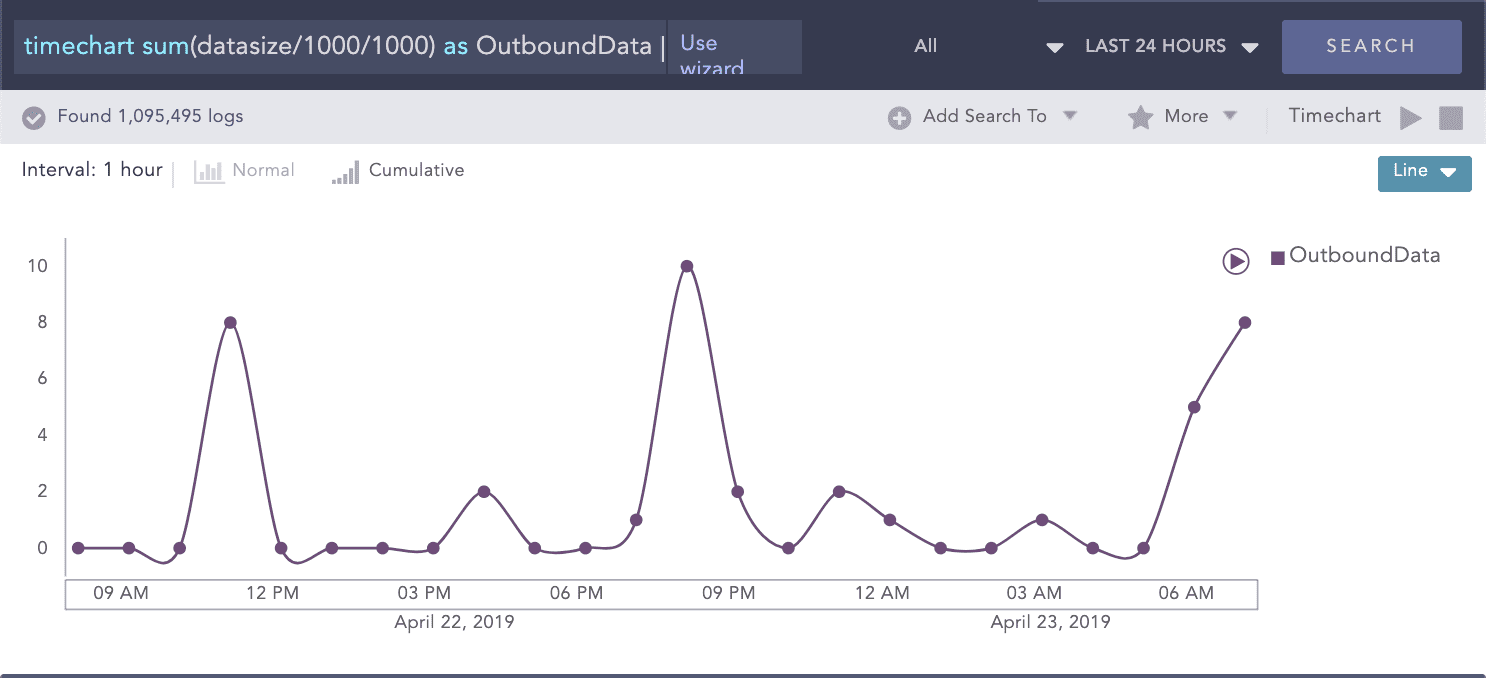
Detecting Data Staging and Exfiltration
Compromised accounts or machines are usually trying to move data into staging areas where they can be easily withdrawn from the organization’s network. While preparing the data for removal, attackers will utilize tools such as PSExec or remote desktop tools. In this case, Logpoint UEBA will detect and highlight anomalous staging and lateral movement including (the highly unusual) intra-workstation high volume data transfers, unusual protocol/port combinations and unusually high amounts of data access.