Updated April 2023
A Security Operations Center (SOC) is a command center for cybersecurity professionals responsible for monitoring, analyzing, and protecting an organization from cyber attacks. In the SOC, internet traffic, internal network infrastructure, desktops, servers, endpoint devices, databases, applications, IoT devices, and other systems are continuously monitored for security incidents. The SOC staff may work with other teams or departments but are typically self-contained with employees that have distinguished cybersecurity skills. Most SOCs operate 24-7 with employees working in shifts to monitor network activity continually and mitigate threats. A SOC can be built internally, alternatively entirely or partially outsourced to external providers.

Table of Contents
- 1 Cybersecurity is a must-have for all modern businesses
- 2 Understanding today’s cybersecurity threats
- 3 Beyond ROI: ensuring cybersecurity resilience
- 4 Leaders need to step up and pave the way
- 5 How does a SOC work?
- 6 What are the tools included in a Security Operations Center?
- 7 Benefits of a Security Operations Center
- 8 Challenges of a Security Operations Center
- 9 Security Operation Center Deployment Model
- 10 Building Security Operations Center Capabilities
- 11 Questions to consider when building a SOC
Cybersecurity is a must-have for all modern businesses
Right now, cyberattacks occur far too frequently for businesses to be complacent. There are new threats, new vectors, and new actors, these are being met by an ever developing cybersecurity solutions sector.
As cybersecurity technology evolves, these tools are becoming more accessible — and more successful — than ever before. Businesses now have a choice of different products, price points, and payment structures, so they do not need to make the call between investing in cyber protection or cutting back in other areas.
This is good news for modern organizations, especially those underpinned by a mostly digital foundation. As digital transformation continues, more doors open for digital threats — and this makes a business vulnerable to cyber attacks and breaches.
These vulnerabilities are likely to become more stressed the more your business scales; the larger you grow your team, the more devices and endpoints you include, and the more data you start processing.
Partnering with the right cybersecurity supplier is one way to modernize your approach and better protect your business.
Understanding today’s cybersecurity threats
The word ‘hacker’ used to conjure images of a lone wolf sitting in a dark basement — someone with a talent for coding but driven by a hunger for disruption.
Today’s cybercriminals are a different breed. It’s commonplace for hackers to form a group, bonded by a shared comradery and cause. Threat actors are more connected than ever, and this has given rise to a new criminal phenomenon.
‘CyberCrime as a Service’, or CCaaS, is an established form of revenue for those with the ‘skills’ for cybercrime. It’s no longer the case that those with bad intentions have to carry out the dirty work themselves — they can simply hire someone to act in their place. This creates a market for threat packages, which means they are available to anyone that wants to use them.
So, to withstand — and stay ahead of — this rapidly evolving threat landscape, smart business leaders must put cybersecurity at the heart of their operations, boosting their prognosis in a world filled with threat actors.
Beyond ROI: ensuring cybersecurity resilience
Cybersecurity resilience is an all-encompassing term for sustainable, water-tight digital infrastructure.
This resilience, means being able to detect, locate, and deal with attacks. The first step is to secure a form of surveillance to spot suspicious activity, followed by containment and then mitigating action.
Malicious actors do not adhere to regular working hours — your security operation needs to be razor sharp, twenty-four hours a day. Monitoring and detection operations should run constantly, to fend off any threats.
Consequently, threats are ever-evolving to try and get ahead of newly implemented defense strategies. This means that your cybersecurity solution needs to be dynamic and responsive to the fresh tactics and methods that hackers deploy.
If you can achieve that, then your cybersecurity spend shifts from being an insurance policy (bought ‘just in case’ of attack) to a proactive investment in the future of your business. What’s more, you will be better placed to protect your business as you scale.
At Logpoint, our SaaS protection is formulated from event information and threat detection from across the web. This means we’re able to provide the most up-to-date and relevant cybersecurity solutions for your enterprise.
Leaders need to step up and pave the way
As a C-Suite leader, you set the tone for others to follow.
- Create a culture at your organization that places cybersecurity at the forefront of your priorities. Doing so will inspire others to understand its importance.
- Educate your colleagues on intelligent cybersecurity practices, to promote better organizational health and resilience to threats. As with tactics such as phishing, it only takes one member of staff not to recognize a malicious email to create a route in for malware.
- Place digital upskilling on the agenda to minimize breach events. Achieving buy-in from staff means there are more vigilant eyes and ears available to safeguard your enterprise.
- Establish a long-term partnership with a world-class cybersecurity provider to cement a strong foundation and build resilience into your business.
Take a tour of Logpoint’s solutions and platform.
The SOC monitors security data generated throughout the organization’s IT infrastructure, from host systems and applications to network and security devices, such as firewalls and antivirus solutions.
Combining a range of advanced tools, and the skills of experienced cybersecurity professionals, the Security Operations Center performs the following vital functions:
- Security event monitoring, detection, investigation, and alert triage
- Security incident response management, including malware analysis and forensic investigations
- Threat intelligence management (ingestion, production, curation, and dissemination)
- Risk-based vulnerability management (notably, the prioritization of patching)
- Threat hunting
- Security device management and maintenance
- Development of data and metrics for compliance reporting/management
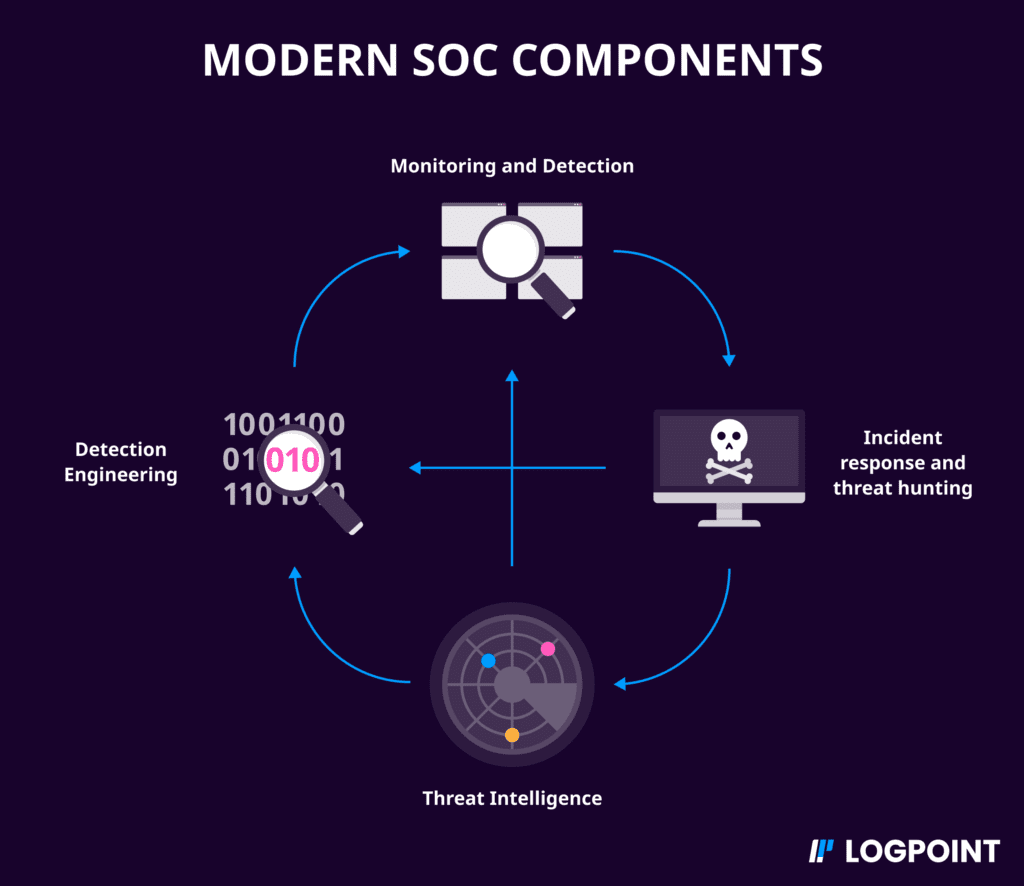
The SOC includes a set of tools in a diverse technology stack to help cybersecurity analysts continuously monitor security activities in the organization’s IT infrastructure. The members of the security team stationed in the Security Operations Center use these tools to identify, categorize, analyze incidents and events, and ultimately decide how to respond to these events.
Essential tools in the SOC technology stack are:
Security Information and Event Management Solution
Security Information and Event Management (SIEM) tools provide the SOC's foundation, given its ability to correlate rules against massive amounts of disparate data to find threats. Integrating threat intelligence adds value to the SIEM activity by providing context to the alerts and prioritizing them.
Converged SIEM
Converged SIEM helps SOC teams combine data sets from multiple sources. Instead of using multiple standalone products, they now have one single source of truth. Converged SIEM is the only unified platform that delivers SIEM+SOAR, UEBA, endpoint security, and BCS for SAP capabilities as a service directly to enterprises and MSSPs – all from a single plane of glass.
Behavioral monitoring
User and Entity Behavioral Analytics (UEBA), typically added on top of the SIEM platform, helps security teams create baselines by applying behavior modeling and machine learning to surface security risks.
Asset discovery
Asset discovery or an asset directory helps you better understand what systems and tools are running in your environment. It enables you to determine what the organization’s critical systems are, and how to prioritize security controls.
Vulnerability assessment
Detecting the gaps an attacker can use to infiltrate your systems is critical to protect your environment. Security teams must search the systems for vulnerabilities to spot these cracks and act accordingly. Some certifications and regulations also require periodic vulnerability assessments to prove compliance.
Intrusion detection
Intrusion detection systems (IDS) are fundamental tools for SOCs to detect attacks at the initial stages. They typically work by identifying known patterns of attack using intrusion signatures.
The primary benefit of having a SOC is the improvement of security incident detection through continuous monitoring and analysis of network activity and cyber intelligence findings. By analyzing activities across the organization's networks around the clock, SOC teams can detect and respond to security incidents early. This is crucial, as time is one of the most critical elements in an effective cybersecurity incident response.
The 24/7 SOC monitoring gives organizations a significant advantage in the struggle to defend themselves against incidents and intrusions regardless of source, time of day, or type of attack. The gap between the attacker’s time to compromise and the time to detect decreases, which helps organizations stay on top of threats facing their environments and limit their risk.
The key benefits of a SOC include:
- Uninterrupted monitoring and analysis for suspicious activity
- Improved incident response times and incident management practices
- Decreased gap between the time of compromise and the time to detect
- Software and hardware assets are centralized for a more holistic approach to security
- Effective communication and collaboration to detect and classify adversarial tactics and techniques, e.g., by utilizing the MITRE ATT&CK framework
- Reduction of costs associated with security incidents
- More transparency and control over security operations
- Established chain of custody for data used in cybersecurity forensics
The SOC has an increasingly complex role, managing all aspects of the organization’s digital security. For many organizations, creating and maintaining a capable SOC can be challenging.
Common challenges include:
Volume
The most common challenge facing organizations is the volume of security alerts, many of which require both advanced systems and human resources to categorize, prioritize, and respond to threats correctly. With a large number of alerts, some threats can be miscategorized or missed entirely. This emphasizes the need for advanced monitoring tools and automation capabilities and the need for a team of skilled cybersecurity professionals.
Complexity
The nature of the business, the flexibility of the workplace, an increased use of cloud technology, and other issues have increased the complexity of defending the organization and responding to threats. Today, relatively simple solutions like firewalls are insufficient as a stand-alone measure to protect the enterprise from digital adversaries. Sufficient security requires a solution that combines technology, people, and processes, which can be challenging to plan, build, and operate.
Cost
Building a SOC requires significant time and resources. Maintaining it can be even more demanding, as the threat landscape constantly changes and requires frequent updates and upgrades and continuous education of the cybersecurity staff. Also, few organizations have the internal talent needed to understand the current threat landscape sufficiently. Many organizations engage with third-party security service providers (such as MSSPs) to ensure reliable outcomes without significant internal technology or workforce investments.
Skills shortage
Building an in-house security solution is made even harder by the limited availability of skilled cybersecurity professionals. Cybersecurity professionals are in high demand worldwide, making it challenging to recruit and retain these individuals. This means that employee turnover within a cybersecurity organization can potentially affect security operations.
There are several different ways for an organization to acquire SOC capabilities. The most common deployment models include:
Internal SOC
Building a dedicated in-house Security Operations Center is recommended for mature cybersecurity enterprises. Organizations that tend to develop internal SOCs have the budget to support an investment that includes 24×7 around-the-clock efforts and deal with lots of moving parts in and around their infrastructure. One of the essential advantages of building an internal SOC is maximum visibility and responsiveness across the network. A dedicated internal team will have the capability to monitor the environment and its applications, providing a complete picture from a threat landscape perspective. Some disadvantages include the struggle to recruit and retain talent and high upfront investment costs. This model typically takes a considerable amount of time to build and maintain at an adequate level.
Managed SOC, MSSP, and MDR
Selecting a managed SOC is recommended for organizations that seek assistance from an outside firm to perform highly skilled monitoring and detection tasks. Some organizations may be mature from an IT and cybersecurity perspective. However, budget constraints and limited expertise may hinder the ability to build a fully functional, internal 24x7 SOC. Conversely, some organizations may be in the immature stages of protecting the organization and require better expertise to handle Monitoring, Detection, and Response (MDR) efforts quickly.
The advantages of this model include: quickest, simplest, most scalable, and cost-effective to implement. Since there are a wide variety of clients and industries that MSSPs (Managed Security Services Providers) typically support, the expertise and wealth of additional intelligence can be invaluable.
The biggest difference between a traditional SOC and one including MDR services is that these providers will not only detect and analyze threats but also respond to them. When a threat is detected, they will verify the criticality while responding and informing you about the incident.
Hybrid – Small Internal & Managed SOC
A hybrid model brings out the best of both worlds; in-house staff complemented with third-party experts, offering a secure approach to detection and response. Most organizations at this level are large enough to build a small team of their own. However, they cannot build a fully functional internal 24x7 SOC. This solution is efficient because of its quick detection and response time. Also, there is a lower backlog due to the additional analysts (internally and externally) who work through high priority findings. Additionally, this model offers the best learning combination for an organization and cybersecurity team. It can also provide knowledge transfer from the experts of an MSSP.
Significant disadvantages include the fact that some data will be handled through a third party and that this model can be costly to sustain long-term.
To plan, build, and operate a Security Operations Center takes time and resources. It’s an essential task for cybersecurity effectiveness in the enterprise. Still, depending on the organization's size and the availability of expert resources, it’s worth considering assistance from external advisors. You’ll need to think through how to plan, build, and operate the SOC. Moving forward, the first step will be to make a business case that allows you to seek executive leadership support for the project and the required funding.
Keep in mind that an effective SOC business case focuses on the investment's outcome rather than the specific technical capabilities or tools a SOC adds. Senior leadership appreciates business cases providing tangible, metric improvements, or benefits.
| Plan | Build | Operate | ||||
|---|---|---|---|---|---|---|
| Justification | Level | Resources | Sourcing | Capabilities | Workflows | Metrics |
| Do I need a SOC? | What capabilities should the SOC have? | How much should/can I spend on the SOC? | Should I build the SOC myself or outsource it? | What capabilities do I need now and which can I add later? | What SOC functions can be automated? | What SOC metrics should I track? |
| What are the tangible metric advantages of SOC? | Who is managing the SOC and what is the organizational structure? | How much staff is required to run the SOC? | What SOC services are my peers using? | How do I add incident response capabilities? | Whom does the SOC work with internally/externally? | How should I manage the SOC? |
| Making the SOC business case to leadership | What service level do I require from my SOC? | What are the staff roles and responsibilities in the SOC? | Could/should I be able to change SOC sourcing decisions over time? | How do I improve threat detection capabilities? | How do I add or improve SOC capabilities over time? | What reports should I create for senior leadership on SOC performance? |
Do I need a SOC?
Plan
Level: What capabilities should the SOC have?
Resources: How much should/can I spend on the SOC?
Build
Sourcing: Should I build the SOC myself or outsource it?
Capabilities: What capabilities do I need now and which can I add later?
Operate
Workflows: What SOC functions can be automated?
Metrics: What SOC metrics should I track?
What are the tangible metric advantages of a SOC?
Plan
Level: Who is managing the SOC and what is the organizational structure?
Resources: How much staff is required to run the SOC?
Build
Sourcing: What SOC services are my peers using?
Capabilities: How do I add incident response capabilities?
Operate
Workflows: Whom does the SOC work with internally/externally?
Metrics: How should I manage the SOC?
Making the SOC business case to leadership
Plan
Level: What service level do I require from my SOC?
Resources: What are the staff roles and responsibilities in the SOC?
Build
Sourcing: Could/should I be able to change SOC sourcing decisions over time?
Capabilities: How do I improve threat detection capabilities?
Operate
Workflows: How do I add or improve SOC capabilities over time?
Metrics: Which reports should I create for senior leadership on SOC performance?







