Every year, 34% of organizations are hit by insider attacks. Because the insider uses valid credentials to access company networks, systems, and data, it is difficult for the security teams to distinguish between harmful and regular activity. In fact, on average, it takes 197 days to detect an attack and another 77 days to recover from it. In the high-stakes game of information security, these statistics are a glaring neon sign, signaling the critical need for comprehensive measures against insider threats.

Go To Section
Types of Insider Threats
Negligent insiders
Negligent insiders cause a security threat inadvertently because of human error, poor judgment, malware, or stolen credentials. According to Ponemon, negligent insiders account for 62% of data breaches.
Malicious insiders
Malicious insiders exploit their privileged access with the deliberate intent to engage in fraudulent activities, steal intellectual property, and disrupt systems. Leveraging their knowledge of enterprise systems, procedures, and policies, they hold a significant advantage. In addition to this, there’s a significant correlation between insider breaches and employees intending to cut ties with their organization, with 60% of insider threats emerging within 90 days of an employee's planned departure. This underscores the need to monitor employee behavior and data access patterns and tackle insider threats with at least as much rigor as external threats.
Compromised insiders
Compromised insiders are legitimate users whose credentials have been stolen by external threat actors. Threats launched through compromised insiders are the most expensive, costing victims an average of USD 805K to remediate. Phishing attacks are causing 67% of all accidental insider threats, with 94% of the malware coming from emails.
How can UEBA help detect suspicious activity?
As advanced attacks and pervasive threats often arise from compromised credentials or coercing users into performing actions that damage enterprise security, it is essential to monitor for suspicious behavior. User Entity Behavior Analytics, UEBA, is critical in identifying abnormal patterns and detecting early signs of potential threats.
How does it work?
Using machine learning techniques, UEBA constructs a foundational behavioral profile for users and entities, continually comparing each new activity against this baseline. It assigns a risk score based on any deviations detected. To maintain accuracy, UEBA relies on behavioral analysis rather than predefined rules to define what constitutes normal behavior. This approach ensures the system only identifies abnormal behaviors, minimizing false positives.
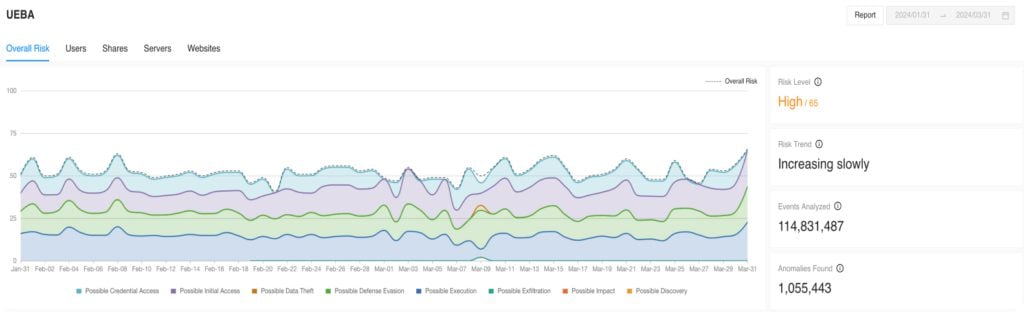
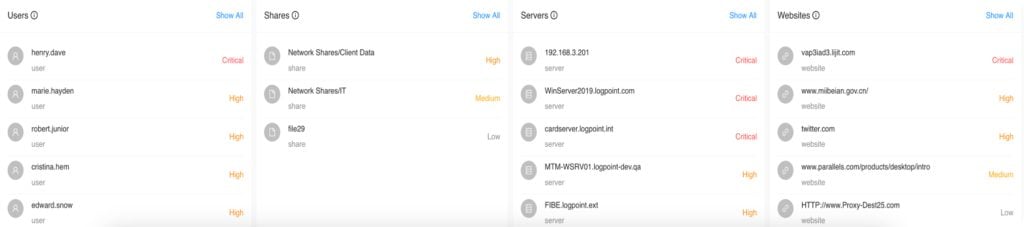
UEBA provides a complete risk overview and anomalies detected from various entity types, such as users, servers, shares, and websites. From here, you can drill down on the risky entities, search the information specific to each anomaly, and explore the raw log events for further threat analysis.
With UEBA, you get a complete overview of users worth investigating. As illustrated, examining Henry Dave's activities closely would be a good idea.
From here, you can get a detailed overview of what Henry Dave is monitored for, including the activity timeline and the risk levels. In this case, the following critical activities have been flagged:
- Use of a flagged external website many times.
- Failed access attempts on network shares.
- Strange working hours.
- Large amounts of data are being sent.
- Access to drive shares or projects to which he wouldn’t usually access.
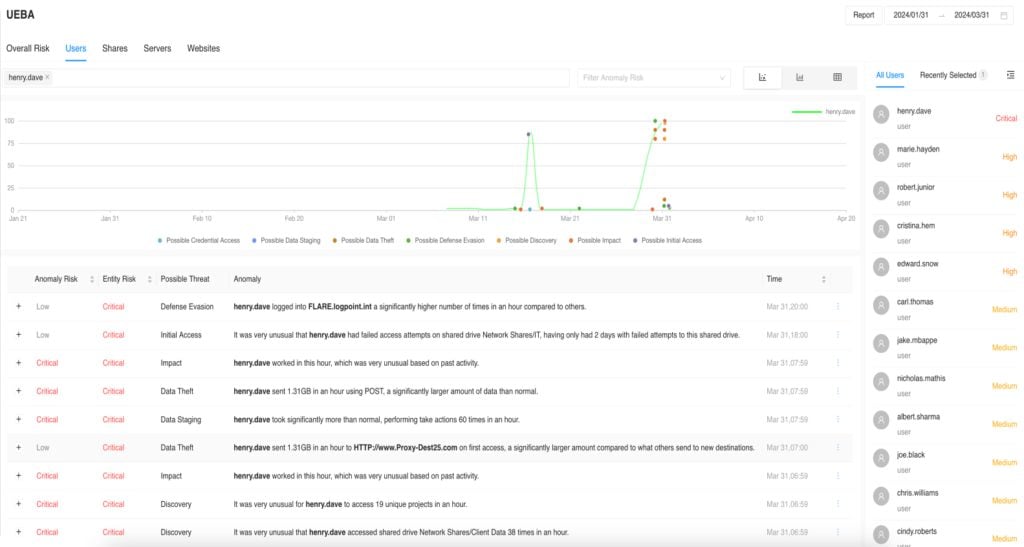
A complete overview of all critical activities conducted by Henry Dave, accompanied by a timeline and risk levels.
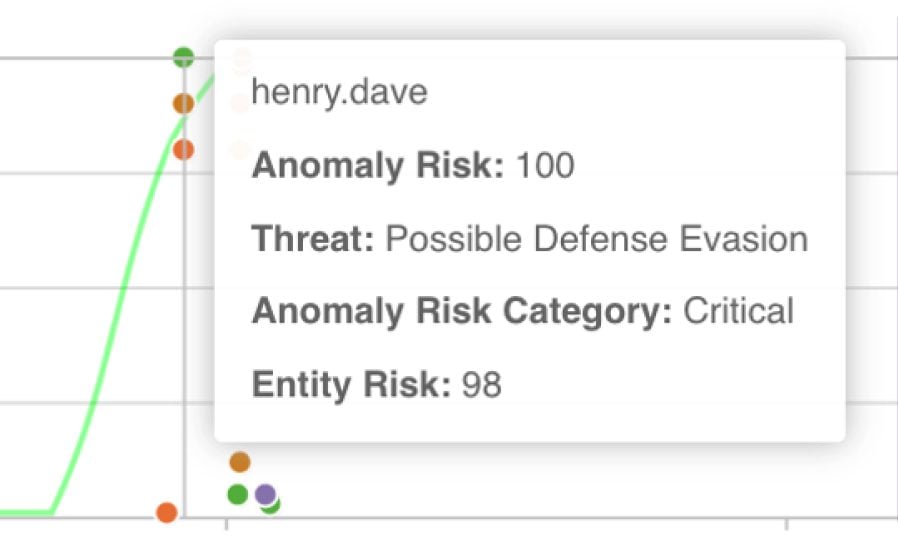
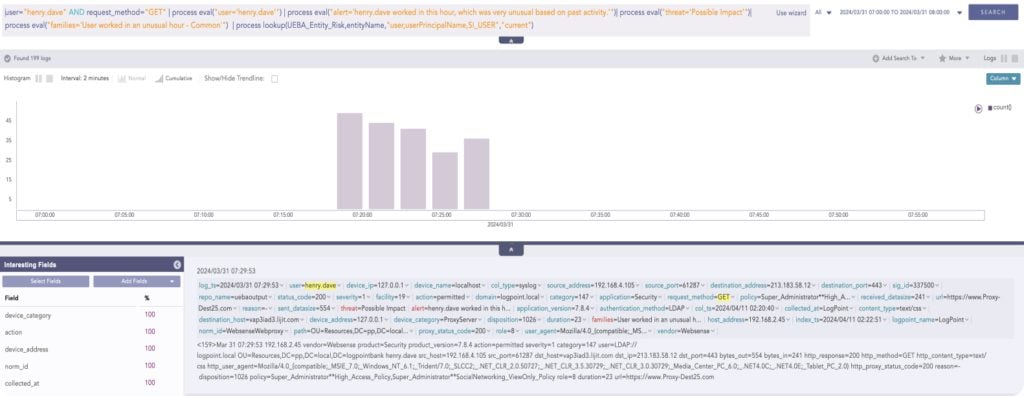
Hovering over the graph will show precisely what happened and help to piece together the complete picture of the activity.
Within UEBA, users can delve into raw events, offering a comprehensive view of all components contributing to a potential risk. Users can use this data to compile individual events into a cohesive "incident" for subsequent remedial actions.
Why UEBA?
In the ever-evolving cybersecurity landscape, UEBA offers organizations the opportunity to proactively strengthen their defenses, ensuring they remain one step ahead of cyber threats. Embracing UEBA is not just about securing the present but also safeguarding the future of your organization's digital assets through:
Proactive Threat Identification: UEBA conducts real-time analysis of user and entity behavior, enabling organizations to promptly identify potential threats as they emerge and effectively mitigate risks before they escalate.
Continuous Monitoring: With UEBA, there's no room for complacency. Its ongoing surveillance enables swift detection of suspicious activities, narrowing the vulnerability window.
Reduced False Alarms: The deluge of alerts in cybersecurity often includes false positives, creating noise. UEBA tackles this by employing advanced machine learning to differentiate genuine threats from benign anomalies. By focusing on behavior rather than rigid rules, UEBA significantly curtails false positives, empowering security teams to prioritize effectively.
Dynamic Learning: UEBA is not static; it evolves alongside the organization. UEBA continually hones its grasp of normal behavior through adaptive learning algorithms, ensuring efficacy in spotting emerging threats.
UEBA is a foundational element in cybersecurity, bolstering organizations’ defense mechanisms and empowering proactive risk mitigation. If you are looking to fortify your cybersecurity defenses, we invite you to read more about how Logpoint can help you detect, investigate, and response to incidents related to insider threats or contact our sales representative to get an in-depth demo of our solutions.