Updated 16 May 2023
ERP (Enterprise Resource Planning) Security is the practice of taking effective security measures to prevent any infiltration inside of your ERP systems. While your ERP systems make life easier because they unify all your different platforms and departments, they’re also a weak point targeted by hackers
The purpose of an ERP System is to combine your administrative assets within one application, ranging from Human Resources to Supply Chain Management. They make our lives easier by centralizing data and enabling us to manage business processes better.
Unfortunately, by having all your eggs in one basket in terms of critical data and essential business information, there’s a higher risk of external threats. One recent study showed that cyberattackers are targeting ERP systems more often meaning you face more vulnerability as an organization. If even just one piece of the system is compromised by a hacker, they will then have access to the organization’s most valuable assets across departments.
And so, because of the amount of exposed and sensitive data, ERP Security is an essential countermeasure to ensure safety in your organization.

Table of Contents
- 1 What are the elements of ERP security?
- 2 Why are hackers targeting your ERP Security?
- 3 Why ERP systems are prone to attack:
- 4 ERP Security Best Practices to Secure Your Software
- 5 Benefits of Combining Your ERP Solution with SIEM
- 6 Logpoint Converged SIEM
- 7 BCS for SAP
- 8 The Takeaway
- 9 Test the benefits of Logpoint Converged SIEM
What are the elements of ERP security?
ERP Security helps you protect the assets and systems in a company, it covers areas such as:
- Infrastructure security
- Network security
- Operating system security
- Database security
A secure ERP system covers the secure configuration of servers, enablement of security logging, in-system communication security, and data security. Users and authorizations are no less critical.
As you can imagine, it’s essential to ensure system compliance with continuous monitoring, audits, and the establishment of emergency concepts.
Why are hackers targeting your ERP Security?
For many businesses, ERP security is a blind spot. While companies spend time and resources on upgrading their ERP systems and management, they often overlook or fail to invest in adequate cybersecurity to match it.
Because it’s connected to a range of daily operations, an attack on ERP systems can have a devastating impact on the business’s operations. And since cybersecurity threats are on the rise, the chances of facing financial losses and a damaged reputation are real. Organizations need to protect their systems against internal and external cyber threats to maintain confidentiality, availability, and integrity.
Despite this, many organizations keep them out of scope for security teams or rely on the ERP vendor tools alone—but that’s just not going to cut it anymore. This means that many ERP systems are outdated and remain unpatched for years, and the necessary security knowledge is often lacking.
As a result, these “gaps” in outdated ERP systems make it easier for cyber attackers to take advantage of organizations, as they did in the Colonial Pipeline attack last year. This led to a gas shortage in the Eastern U.S. and caused prices to jump to the highest they had been since 2014.
Of course, given the intricacies and complexities of ERP systems, ERP security is challenging to monitor and maintain.
Common Vulnerabilities of ERP Systems
The larger the company, the more users and—by extension—more vulnerabilities exist in your system. And so, this makes ERP security a uniquely complicated issue because of the increased difficulty in maintaining it.
Think of your ERP system like a house of cards. The smaller the system, the more stable and more difficult it is to blow over. However, the bigger it gets the more weak points there are in the structure—meaning it’s easier for it to fall apart. All this to say, your ERP system has a number of reasons it’s vulnerable and needs protection.
Why ERP systems are prone to attack:
ERP Systems Are Complex
First of all, ERP systems are substantial and complex applications. For users to perform actions in the application, there are hundreds of authorization objects in the systems. Authorizations, system settings, and customization parameters allow for a very flexible but complex system configuration.
ERP Systems Affect Your Whole Business
ERP systems are interconnected so that a single breach can compromise an entire business operation. Having a large attack area combined with lacking general ERP security and knowledge increases the risk of attacks and makes ERP systems, such as SAP, a prime target for adversaries.
Lack of Specialists on Your Staff
On top of that, there’s a shortage of ERP Security staff knowledgeable enough to run and practice safety within the organization’s systems. So, while the vendor provides an ERP security solution, it often does not integrate with its central cybersecurity monitoring due to a lack of resources. This creates a blind spot for the security team and increases the cyber threat from internal and external actors.
Users Not Updating Their Systems
Another problem is found in the behavior and attitude we have towards technology—basically, we think we’re safe when we’re not. When users fail to properly update systems, this can allow breaches. And when it comes to password security, only 56% of employees say they think their password habits are secure.
One-factor Authentication
Additionally, only 38% of large organizations use multi-factor authentication as a means to protect their accounts. Trust us when we say that being able to access critical business data with one-factor authentication is a no-go.
Authorization issues
Finally, a lack of stringency in setting up authorization is a common problem in ERP systems. When too many users have full access and privileges, that leaves your information far too exposed if a cyberattack happens.
ERP Security Best Practices to Secure Your Software
To keep your ERP protected and secure, it’s critical to establish appropriate controls by implementing ERP security solutions and integrating them with the rest of the security operations.
Keep yourself one step in front of potential threats by staying well informed and maintaining current community issues. Cybersecurity threats evolve and develop fast. As such, your organization needs to ensure everyone from the top-level executives to the daily users in your ERP Systems are educated on best practices to reduce the chances of threats.
Strong & Safe Password Hygiene
Practicing safe and adequate password hygiene and employees’ training is essential considering the internal security risk posed by insufficient security knowledge within an organization.
For example, breaches can often be traced back to an internal compromise, such as phishing attacks. An organization can easily prevent a superuser’s compromise by educating employees, having two-step verification, or more frequent software and security updates.
Keep Everyone in the Loop
It’s essential to keep everyone in the loop to run an appropriately informed and well-updated organization. Being strict and precise is precisely what can keep intruders out of sensitive data.
Stay Secure from External Risks
Beyond internal risks, it’s important to keep your systems secure from external adversaries, and the best way to do so is by using an ERP Security solution that can:
- Detect exploitation and fraud
- Ensure data integrity
- Identify unauthorized access
- Provide continuous and automated audits
- Detect data leaks
- Centralize security monitoring
ERP security solutions can monitor system settings, patch/authorization management, or RFC communication.
Using an ERP Security solution will reduce an organization’s attack surface and strengthen your company’s security all over. That is why integrating your ERP security monitoring to a centralized SIEM, like Logpoint, can significantly add value in the areas of cybersecurity, IT operations, and system compliance. Ideally, these platforms use UEBA (User Entity and Behavior Analytics) – to get behavioral insights in addition to rule-based monitoring.
Organizations must monitor ERP security continuously and automatically in SIEM solutions. Including ERP security in the organization’s central security operations, such as a Security Operations Center (SOC), to identify threats and respond immediately is necessary to ensure a sound security posture.
Benefits of Combining Your ERP Solution with SIEM
Combining your ERP solution with SIEM gives near real-time monitoring of ERP events and information. Doing this allows organizations to know what’s happening with their ERP data. Beyond that, ERP operation teams also save time and money with ready-to-use controls, reports, and more to automate ERP compliance and maintenance monitoring.
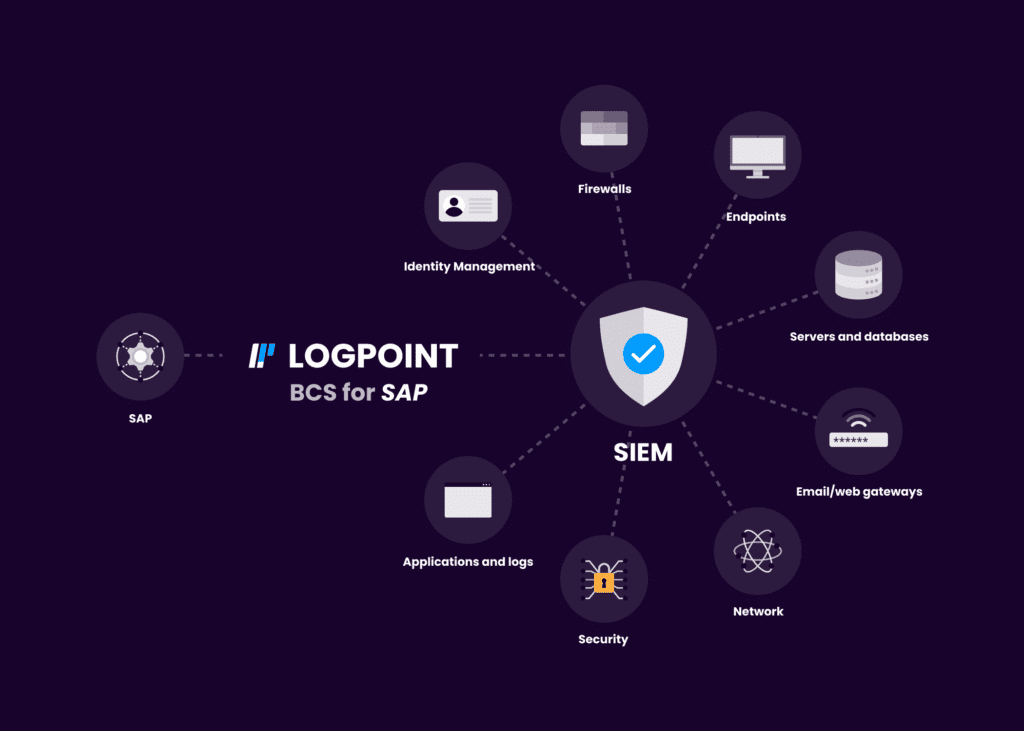
Logpoint Converged SIEM
Combine SIEM, SOAR, UEBA, Endpoint Security (AgentX) plus BCS for SAP. Converged SIEM helps SOC teams combine data sets from multiple sources. Instead of using multiple standalone products, they now have one single source of truth. It is the only unified platform that delivers SIEM+SOAR, UEBA, EDR capabilities and security monitoring of SAP for both enterprises and MSSPs. Get:
- Full data integration for automated TDIR
- No integration or maintenance required
- Out-of-the-box compliance support
- Flexible deployment based on your needs
BCS for SAP
The Takeaway
By integrating an ERP system like SAP into SIEM, you bolster your security, centralize monitoring, and have automated audits so that organizations can track entire IT environments from Cloud applications to IT infrastructure. Our customizable SAP security monitoring tools support special requirements and security policies.
Check out our Security for Business-Critical Systems information and our SAP security solution BCS for SAP and see how Logpoint can help keep your systems and data safe.
Test the benefits of Logpoint Converged SIEM
Discover more about Converged SIEM.






