SIEM for Today’s SOC – Detect, Automate, Hunt, and Respond
- Unify SecOps: Consolidate your spend, simplify your tech, and accelerate threat detection and response with Converged SIEM.
- Operational Efficiency: Alleviate the pain of traditional SIEM maintenance with pre-built integrations, use cases, and playbooks.
- Do Security Your Way: Deploy Logpoint as SaaS, On-Prem, or Cloud to match your security requirements.
Over 1,000 Organizations Across 70 Countries Use Logpoint SIEM
What Sets Us Apart
Adaptable Security Content
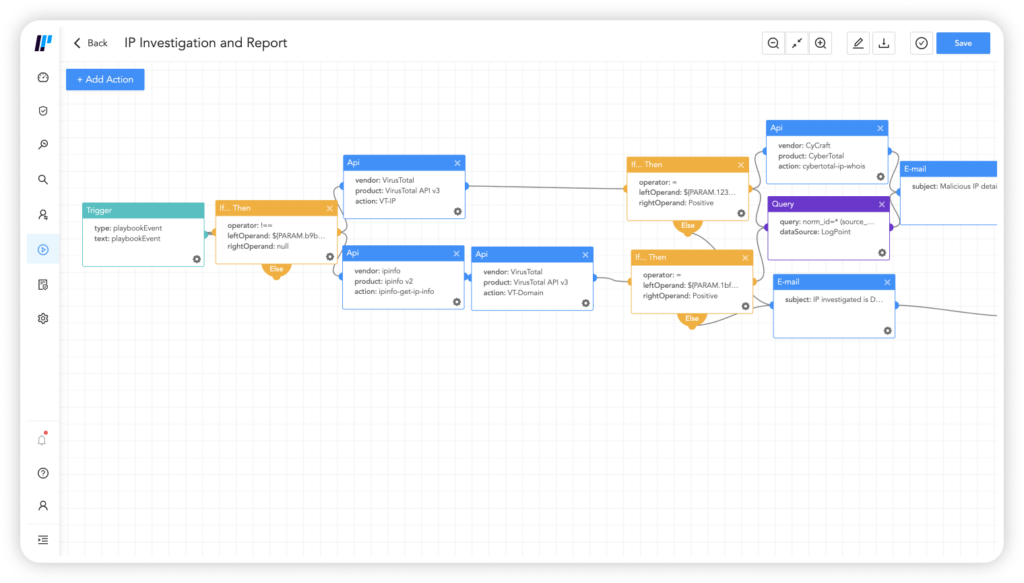
Logpoint provides pre-built use cases, correlation rules, alerts, and playbooks that can be easily tailored to your environment and business needs.
End-to-End Security
Prevent and identify vulnerabilities, detect and investigate threats, plus respond to and remediate the impact of attacks — all from one security operations platform.
Identify True Positives
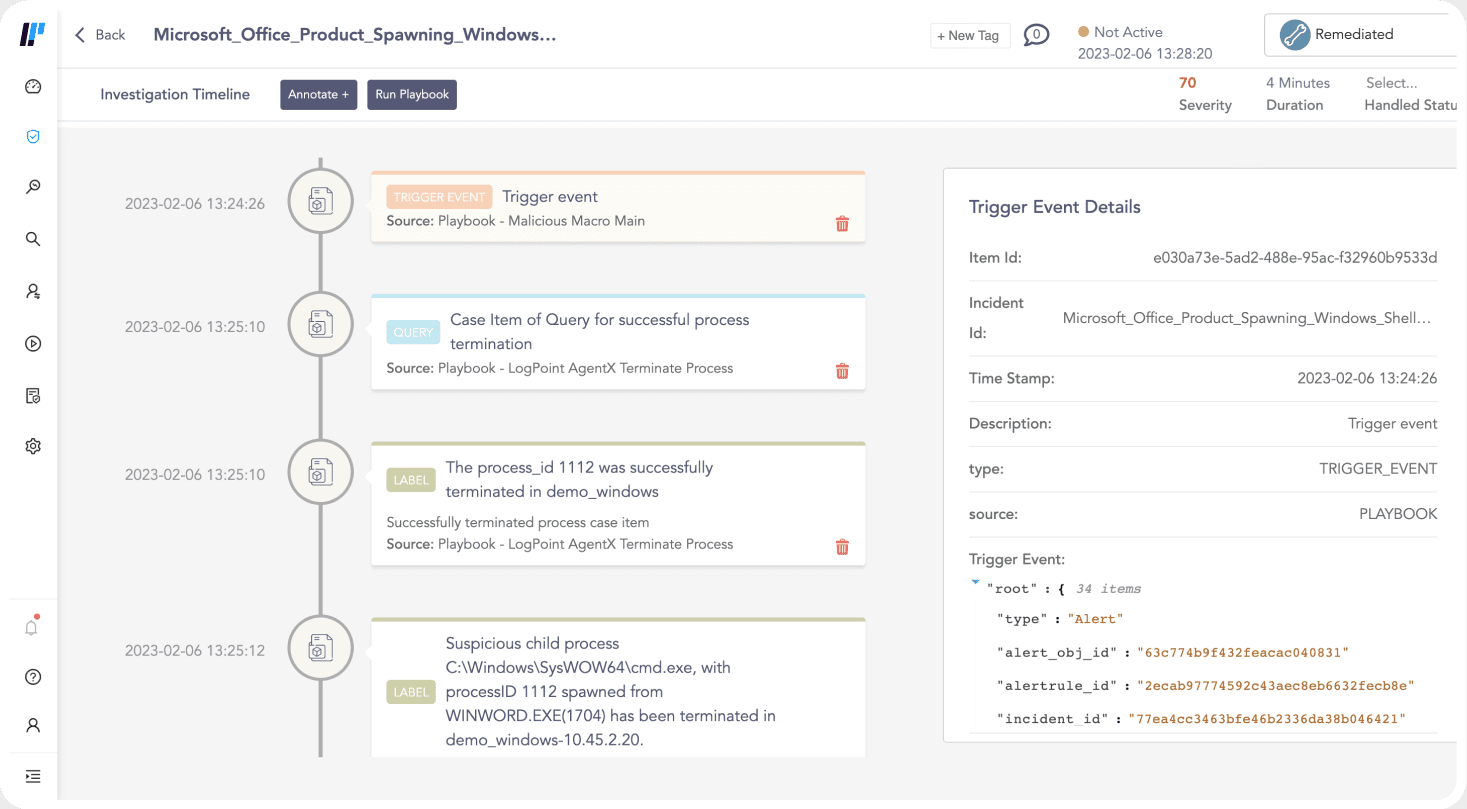
Pre-built SOAR playbooks reduce alert fatigue by accurately identifying the true positives and adding contextual threat intelligence for faster detection.
Efficient Threat Hunting
We continuously create security content and playbooks, allowing you to efficiently threat hunt by applying the latest IOCs, TTPs, and mapping incidents against MITRE ATT&CK directly in Logpoint.
Experience the Full Capability Range of
Logpoint Converged SIEM
1
Platform
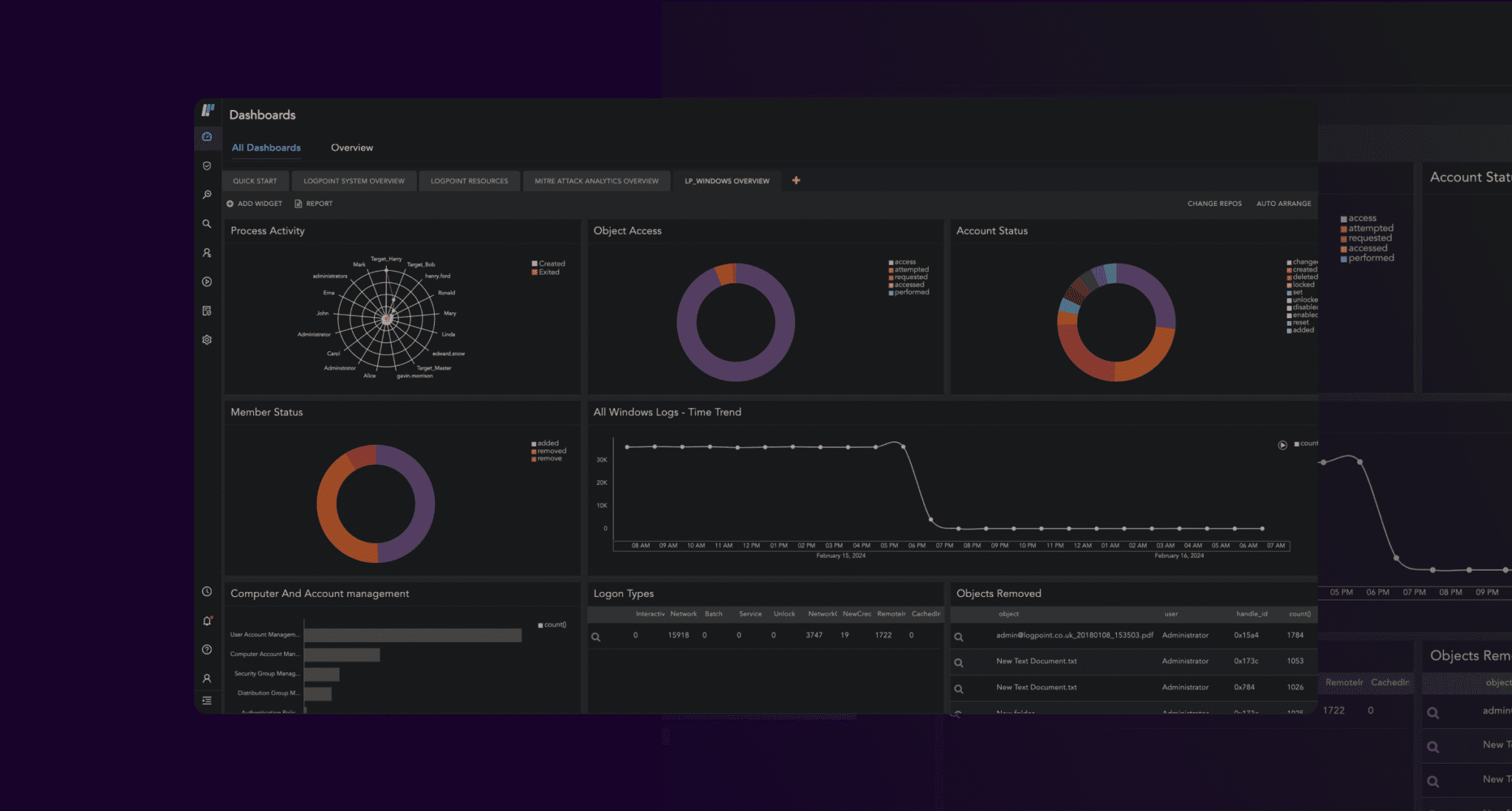
SIEM, SOAR, UEBA, and EDR technologies are unified into one platform, reducing the number of point solutions, vendors, and integrations security teams must maintain.
Faster Response
Automatically add threat intel, business context, and risk scores to observations, turning weak alerts into actionable investigations and faster incident response to threats such as phishing.
Average Cost Reduction
When switching from a SIEM licensed on data volume, Logpoint licensing enables better security coverage and cost predictability when scaling.
Level Up Your Security with Predefined Use Cases and Automation.
Phishing, malware, and ransomware attacks are a constant threat to many organizations. We provide security teams with the edge to respond efficiently to such attacks by providing automated investigation and intuitive threat hunting capabilities to keep the organizations infrastructure endpoints safe.
Insider threats often rely on compromised credentials or coercing users into performing actions that damage enterprise security. To identify such attacks, you need a robust solution that allows the security team to determine normal versus abnormal activity on your network quickly.
Organizations are moving more applications and workloads to the cloud every day. Confidence is building as efficiencies increase, but cloud security is still a blind spot.
Logpoint provides visibility to your cloud data, including infrastructure and applications.
Meeting compliance can be costly and complicated. But that investment is minimal compared to the costs of fines, legal costs and a damaged reputation. Automate and consolidate compliance reporting with reports that show auditors security controls are in place and work as designed.
With us you get compliance reporting for GDPR, NIS2, PCI DSS, NERC-CIP, SOX, and many others.
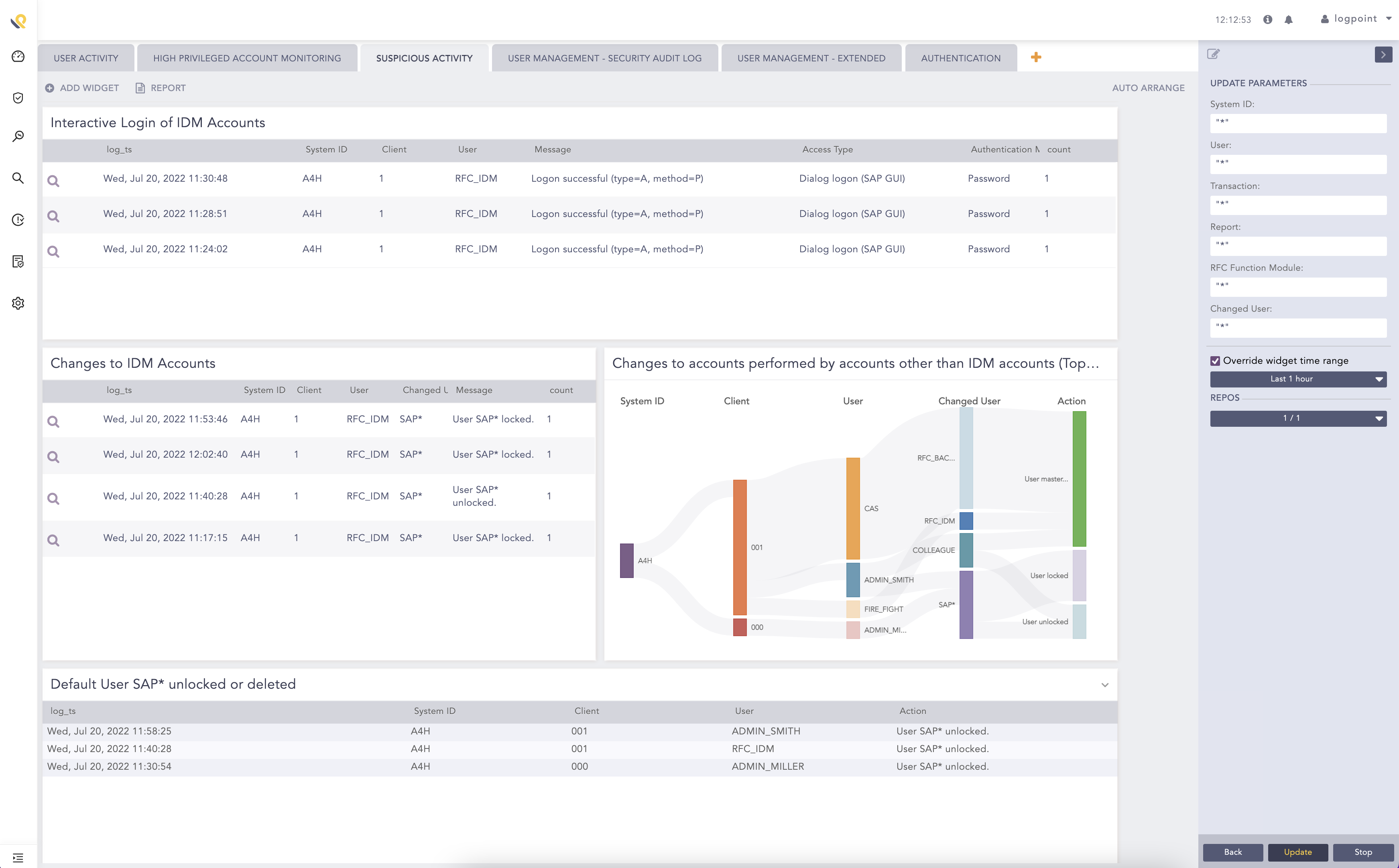
Advanced analytics and innovative orchestration capabilities are unified in a centralized security platform allowing you to effectively detect and manage incidents compromising the security of your SAP systems.
Detect, monitor, and respond to unauthorized access, violations, fraud attempts, IP theft, and operational degradations more effectively. These all threaten compliance, stability, and security of your SAP systems.
By improving event visibility across the entire IT architecture, Logpoint has enabled 80-90% time savings in incident diagnostics, faster problem resolution, and major improvements in the service quality for end-users.
Cédric Chevrel, CISO
Latest Research, Trends, and Insights
Stay updated with the latest research on the emerging threat landscape,
the hottest topics, and get insights from leaders in the world of cybersecurity.