Phishing is a cyber-attack where an adversary sends fraudulent emails, text messages, or other electronic communication to deceive recipients into divulging sensitive information such as usernames, passwords, and credit card details.
Here we will show how using Logpoint has facilitated in drastically reducing time spent on phishing email investigations using Logpoint SOAR, the results include:
- Estimated time savings: 72 days or 30% of an FTE per year
- Estimated over $80,000 savings/year
- 33% of phishing verdicts can be automated
- Queue time shortened drastically, reducing business risk

Go To Section
Use Case
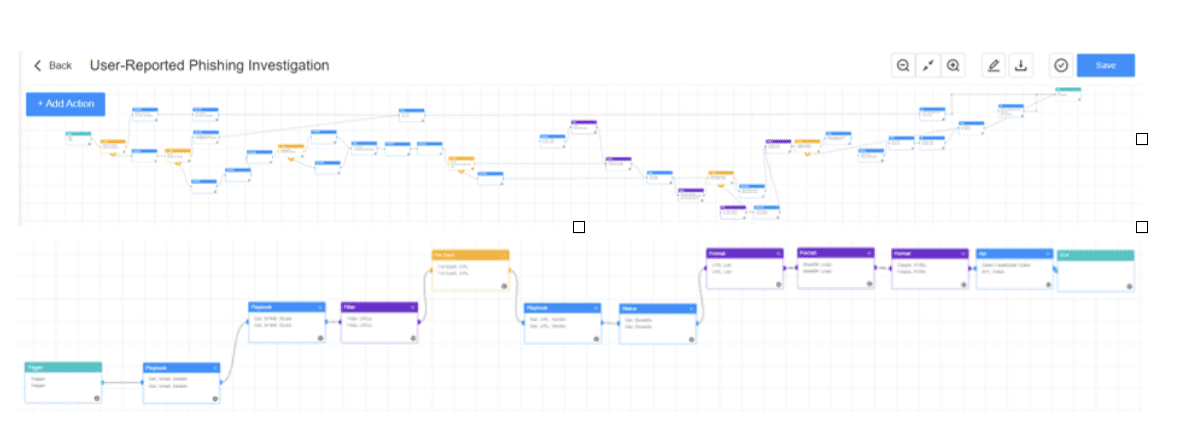
Background and SOAR automation steps
When an employee reports an email as suspicious, the suspected email is automatically forwarded to the company’s ticketing system, and an incident is created.
After this, the “Suspected Phishing Playbook” streamlines the review process for emails suspected of being potential phishing attacks, enabling the customer's environment to stay safe from any real malicious threats.
In this case, the customer expected a verdict match in excess of 75% between the automated process and the pre-SOAR manual investigation.
In contrast, for a fully automated response process, the customer expects a verdict match of over 90%. The customer decided to use Logpoint’s Playbook Design Service (PDS) to speed up the playbook development process, saving on in-house resources.
The PDS suggested the following steps:
- SOAR receives the email for investigation
- Dissects the email into body and headers for further evaluation
- Evaluates each individual characteristic of the email header and scores them accordingly towards a pre-determined risk scale
- All URLs are extracted from the email body, and their reputation is fetched using threat intelligence.
- SOAR Aggregates all risk scores into a combined severity level score for the entire email
- It updates the existing incident in a ticketing system with the analysis details and a conclusion based on the risk verdict.
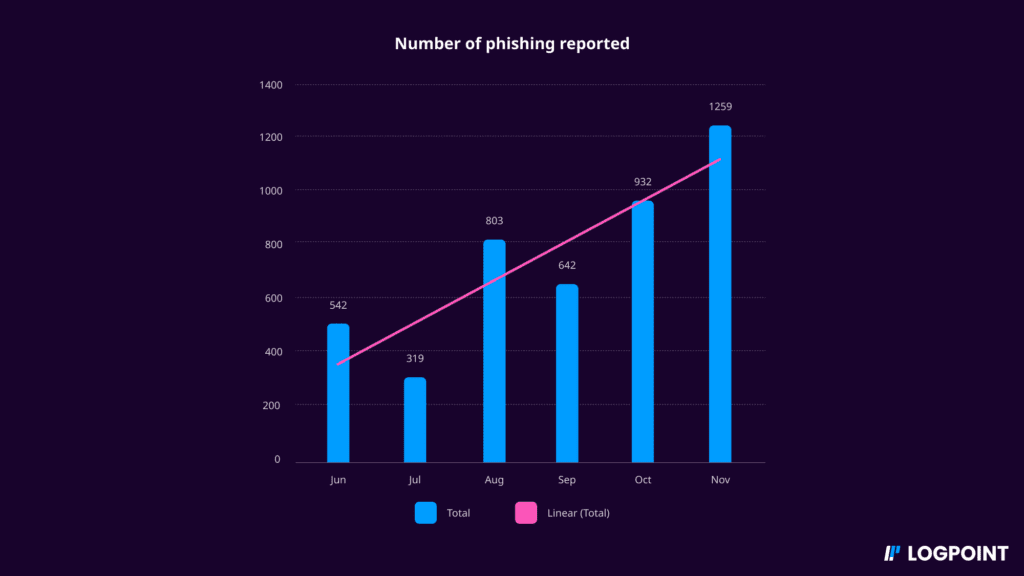
Data before implementing SOAR
The data shows that the company’s number of reported phishing emails is increasing steadily, with 1259 emails reported in November. The customer then splits this into subcategories and tracks the count and time spent on those investigations:
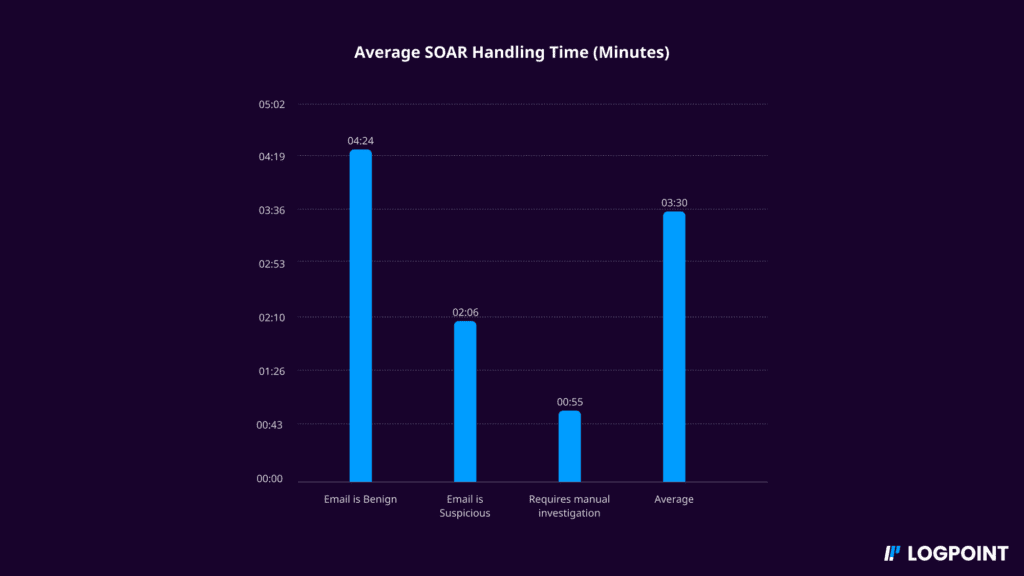
The result
| Resolution of reported phishing | Count of Incidents | Average Resolve Time Per Incident (Minutes) |
|---|---|---|
| Spam | 2176 | 213 |
| Phishing | 1461 | 155 |
| Legitimate | 694 | 207 |
| Phishing Campaign | 67 | 68 |
| Newsletter | 42 | 306 |
| Resolved by Caller | 28 | 117 |
| Possible Phishing | 25 | 222 |
| Other | 12 | 399 |
| Grand Total | 4505 | 192 |
In conclusion, without SOAR, the customer spends an average time to resolution of 192 minutes. With an estimated analyst time to resolution of 15 minutes: The average queue time without SOAR is 177 minutes.
Following Logpoint SOAR implementation
After three rounds of iteration on the playbooks, the customer was able to:
- Achieve over 90% verdict match - Goal achieved!
- Estimated time savings: 72 days or 30% FTE per year for a single use case:
| Average Working Time | Min. / Incident | Incidents per 6 months | Total time Spent |
|---|---|---|---|
| Without SOAR | 15 | 4505 | 67,575 |
| With SOAR | 3.5 | 4505 | 15,768 |
3. Estimated $80,000 in savings per year
4. 33% of cases (phishing verdicts) can be fully automated
5. Queue time shortened drastically, reducing risk to the business
6. A fully automated playbook can potentially reduce queue time by 3 hours
Conclusion
Security teams face immense pressure, and automating tasks to save their time not only helps them but also makes the business more secure and efficient with its resources. Phishing is just one example of how Logpoint SOAR can help. With its exceptional flexibility, Logpoint SOAR can support countless use cases, enabling the automation of investigation and response to various cyber threats.
Want to learn how SOAR can help your organization? Need support in designing efficient Playbooks that fit your organization? Get in touch, and we will guide you through it.






