Logpoint vs. Splunk:
What are the Differences?
Our unique, out-of-the-box Converged SIEM platform is the best alternative to Splunk. It requires no integration or maintenance.
Compared to Splunk, we offer:
- Predictable licensing based on the number of nodes or employees.
- Local support in Europe.
- EAL3+ certification.

Trusted by Thousands, Guarding Millions
Logpoint has helped us become more efficient at a lower cost. The solution is easy to use. The new case management capabilities means we can manage all incidents more efficiently and save time in our daily work. The licensing model means we can easier control our budget.
Verified User in Events Services
Enterprise(>1000 emp.)
Why Choose Logpoint?
| Splunk | Logpoint | |
|---|---|---|
| Flexible deployment options | ||
| Classic SIEM data analytics and real-time monitoring | ||
| User and entity behavior analytics | ||
| Native security automation, orchestration and response | ||
| Out-of-the-box integrations | ||
| MITRE ATT&CK framework mapping and content | ||
| Data privacy and adherence to Schrems II | ||
| Native EDR capabilities | ||
| NATO EAL3+ Certification | ||
| Predictable pricing model |
6 Reasons To Choose Logpoint
Endpoint threat analysis and compliance –Logs and telemetry from your endpoints are normalized into a single taxonomy via SIEM. Get more in-depth analyses of security issues with operational context. It’s also a perfect ally for the compliance team as it helps identify PCI violations and runs policy checks to detect which devices enter a non-compliant state.
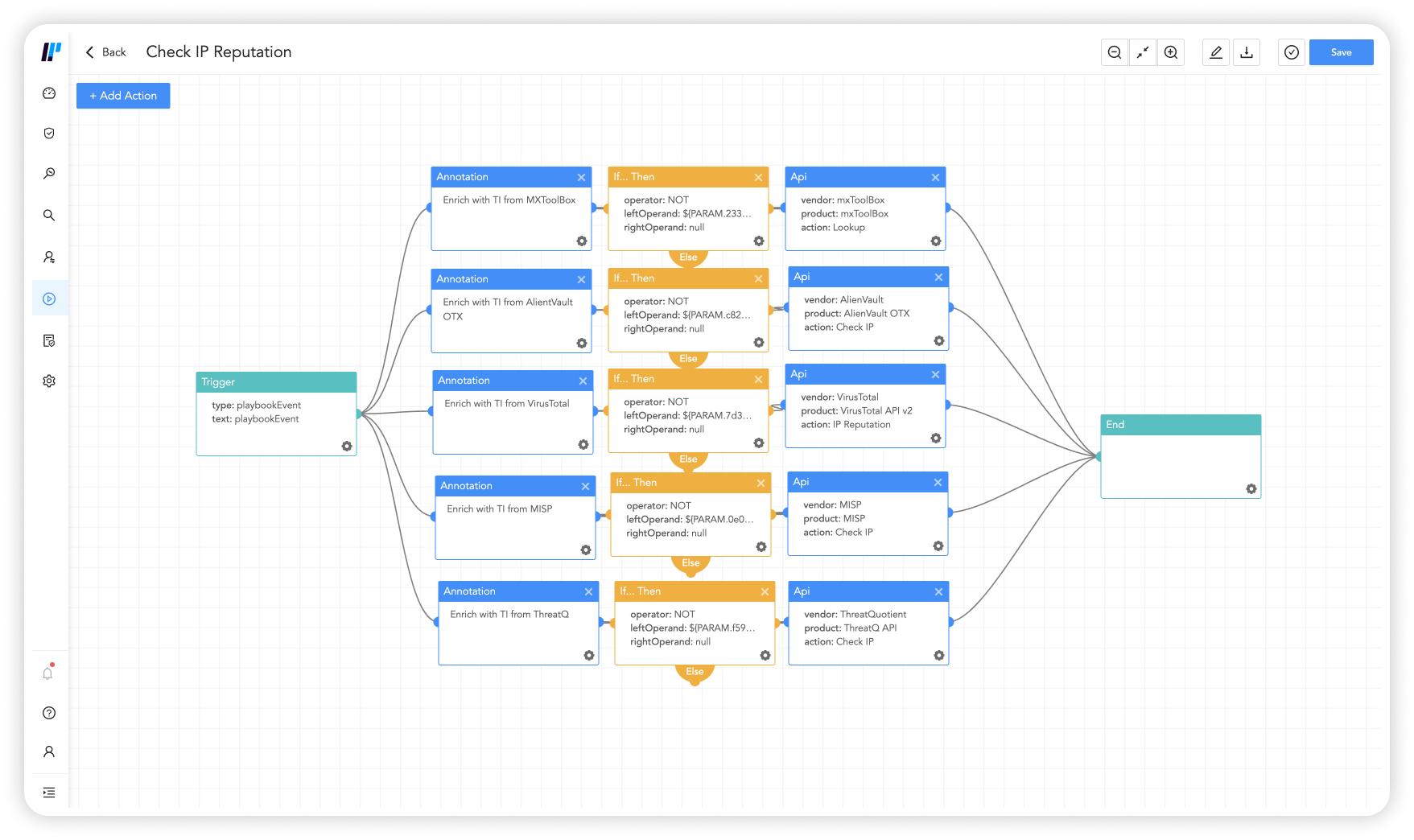
Security orchestration, automation and response –Rapidly contain and remove threats while minimizing the risk of human error. Analysts can group similar incidents into a case and run playbooks directly from it. SOAR prioritizes alerts and security data from different sources and brings order to chaos, pulling all cyber incidents and supporting data together in one place.
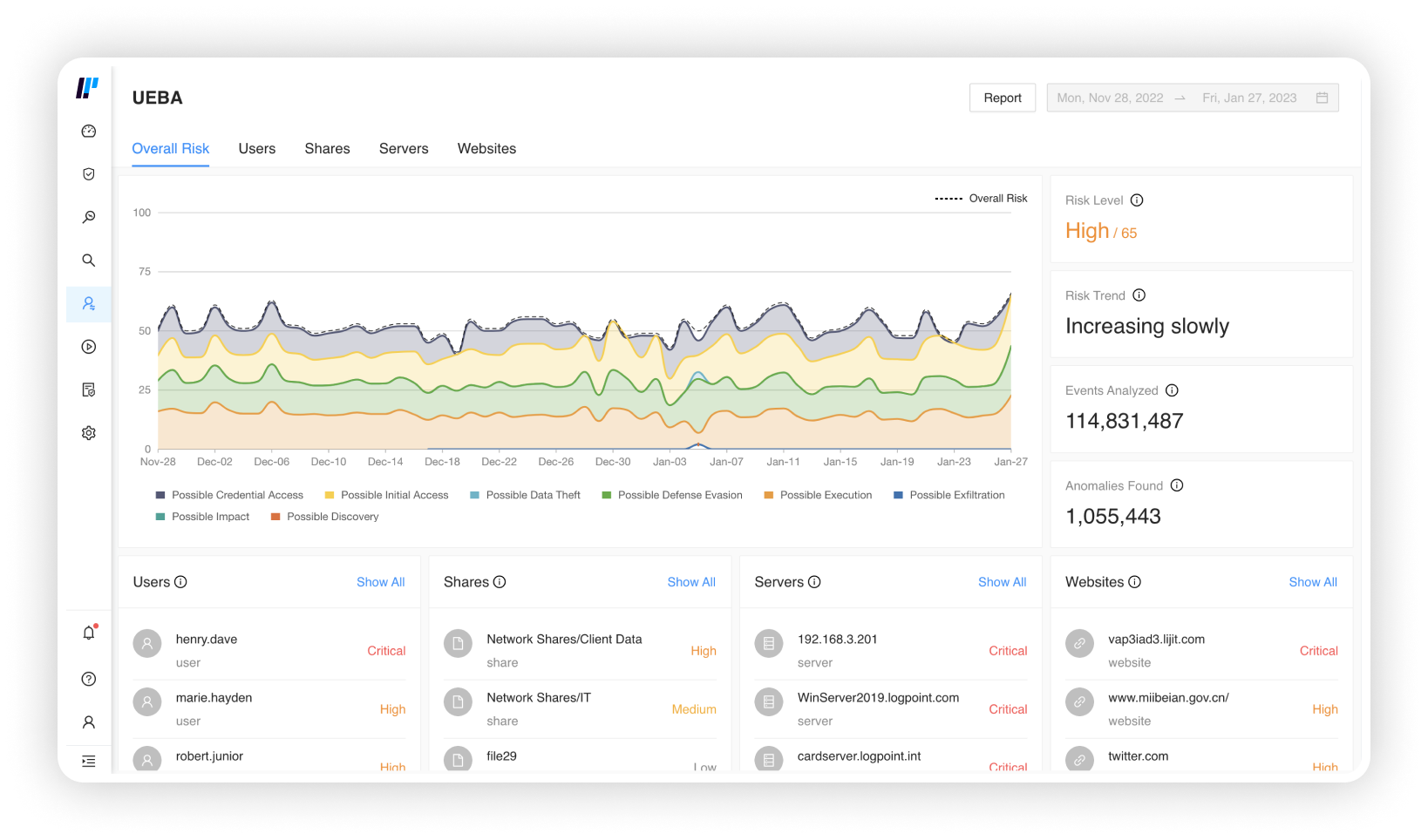
UEBA powered by machine-learning – Detect unknown threats by determining user and entity abnormal behavior from normal one, cutting detection and response time significantly. Combine UEBA with SIEM to make events more insightful and discover authentication abnormalities, data transfer activities or activity-based inconsistencies.
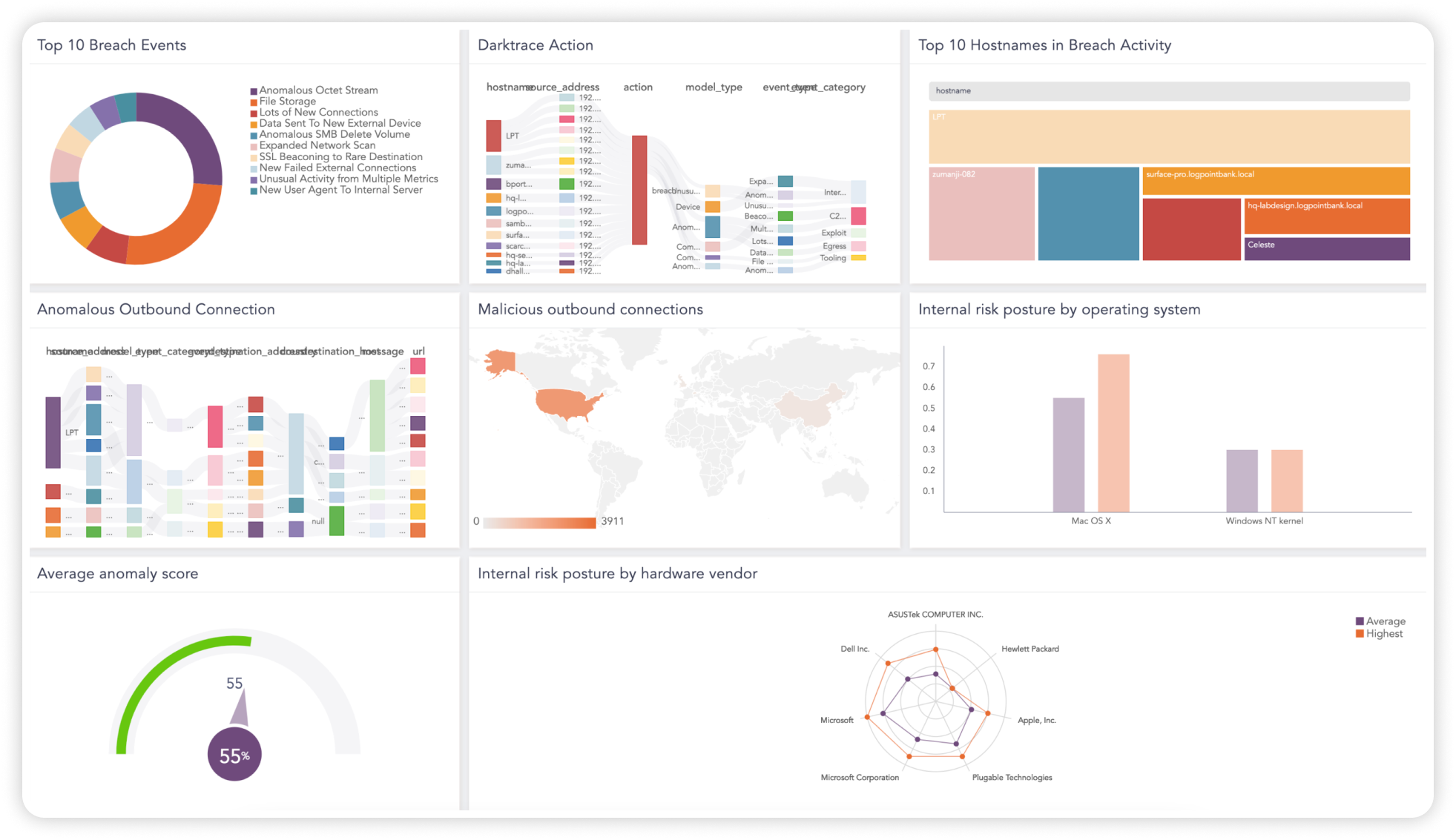
Centralized data monitoring for heightened visibility – Logpoint SIEM collects event data produced by any device, application or endpoint within your infrastructure. By centralizing the data monitoring you improve your visibility into your network and IT infrastructure.
Powerful security analytics – By translating complex log data into a single language, Logpoint maps the alerts to MITRE ATT&CK for better analysis of user activity and incidents. Get your data in context and visualize it with intuitive dashboard that allow you to quickly detect and investigate incidents.
Quick and flexible deployment – Whether you need full control of a SIEM solution in your own infrastructure or simply want a solution with zero infrastructure to manage, we got you covered. With easy onboarding and implementation, the platform is available with a minimal lead time.
Personalized Demo
Converged Platform: Combine SIEM, SOAR, UEBA, and EDR on one platform.
Our sales team will contact you shortly to discover your needs. Then our experts will run you through a customized demo and discuss how Logpoint can support you.