Ensure NIS2 Compliance with Logpoint
NIS2 Directive is stepping into force, striving to enhance protection of critical infrastructure in EU from cyberthreats. It introduces stricter security demands, reporting obligations and enforcement requirements for a broader scope of sectors. Inability to comply can impose fines up to 2% of the worldwide turnover.
Compliance is time consuming and expensive
Varying systems in your IT environment generate logs in different formats and locations making it costly and complicated to meet compliance requirements. Yet the cost of non-compliance is even higher. Fines, legal costs and reputational damage make non-compliance nearly 3x more expensive than the cost of compliance.
Simplify compliance with centralized
security platform and built-in reports

Demonstrate compliance
Support for all major regulatory domains makes it easy to document and prove compliance

Improve business security
Collect and analyze data in one central security platform to determine root cause of breaches

Predictable compliance cost
Out-of-the-box support for all major regulatory domains at a set cost that doesn’t increase with use
Automated detection and analysis to meet compliance
Logpoint provides compliance for all major regulatory domains, including Schrems II, HIPAA, GDPR, PCI-DSS and SOX. With centralized logging and reporting, Logpoint makes it easy to adhere to security guidelines including NIS2, CERT-In, SOC 2 Type II and ISO27001.
With Logpoint’s converged platform, you can also detect and manage access violations, data leakage and misuse of sensitive data in business-critical SAP systems.

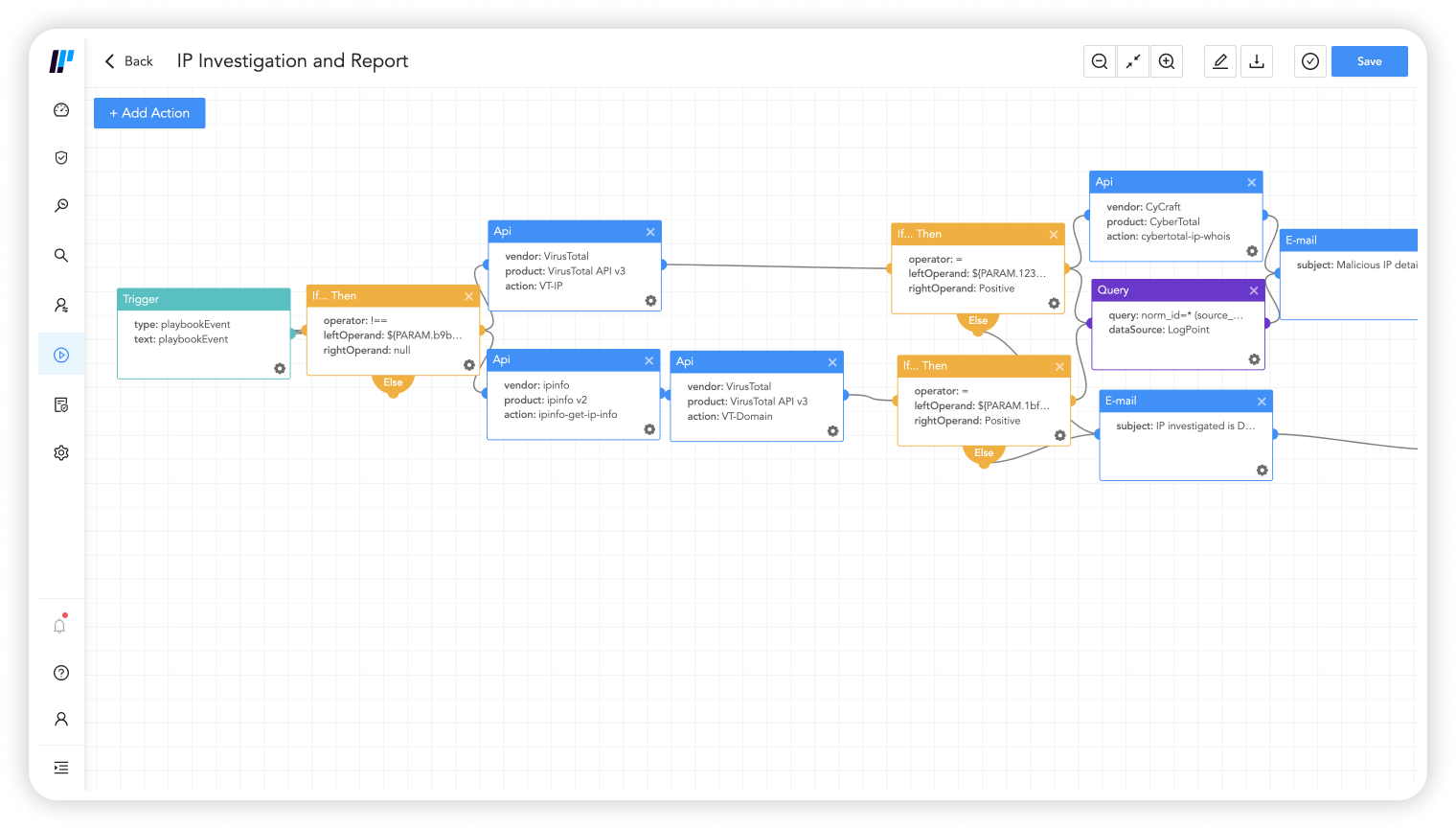
Improve security posture across infrastructure
Logpoint collects and analyzes event data produced by any device, application or endpoint within your infrastructure and flags potentially non-compliant actions immediately.
With playbooks and analytics in one central platform, problematic behavior is quickly identified and the appropriate response is driven.
It’s easy to perform forensic analysis and investigation so you can present compliance evidence and determine the root cause of breaches.
Reduce manual effort to satisfy compliance
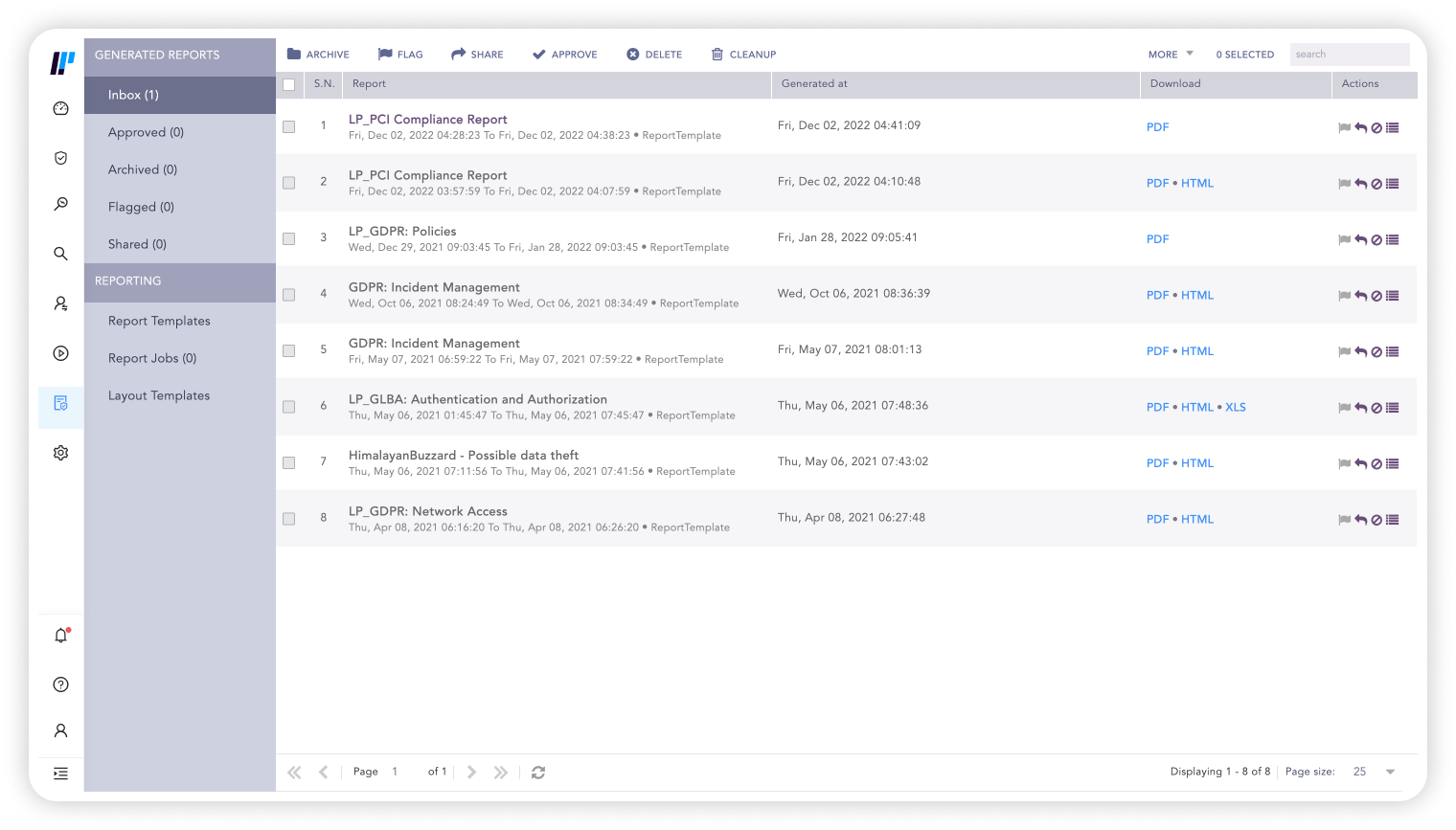
Automate compliance with out-of-the-box reports, audit records of all changes to the system and historical analysis. It’s easy to create and share full incident reports. Also build your own custom reports to meet any compliance regulation.
Our built-in case management system makes it easy to automate investigation and response of a compliance breach and create reports to document mitigation of any incidents.

Bottom line is that Logpoint enables us to document compliance with a wide variety of standards and boost security as well. The SIEM solution enables us to provide our customers with better services and support.
As a financial services company, it is imperative that we maintain a strong security posture at all times. We are also faced with a wide range of industry standards such as PCIDSS, GDPR, SOC 2, and Point-to-Point Encryption. By using Logpoint we can keep a very granular view of our logs and easily identify any out-of-the-ordinary activity.
Get up to date with the
Logpoint blog!