By Rabindra Dev Bhatta, Security Research
Contents
TL;DR
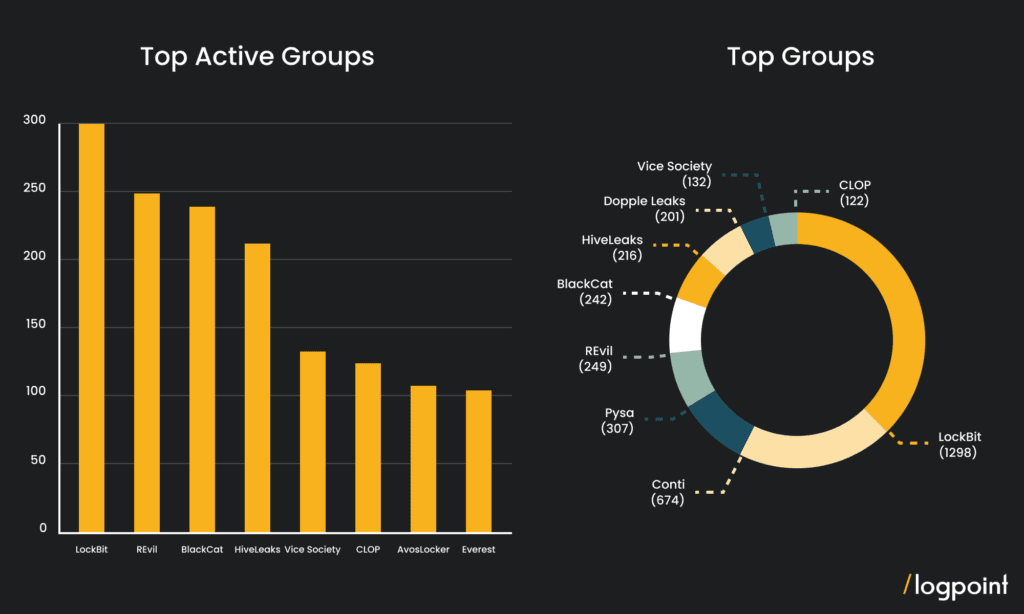
A comparatively new ransomware, Hive is around one-and-a-half years old in the wild, but it is already among the top ransomware threats in the industry. Threat actors have been using Hive to target a variety of companies and critical infrastructure sectors, particularly healthcare, government facilities, communications, critical manufacturing, and information technology.
According to the Joint Cybersecurity Advisory published by the FBI, CISA, and HHS as part of their #StopRansomware effort, as of November 2022, the Hive ransomware threat actors have targeted more than 1,300 businesses globally and have bagged almost US$100 million in ransom. Compared to other ransomware actors, the Hive syndicate functions in quite an organized manner with multiple portals and work distribution. Hive provides RaaS through its three primary API-based portals – affiliate, victims, and data leak site.
** Get research and analysis, insight, plus hints and tips, on how to detect, manage, and respond to Hive ransomware in the main blog.
Head to the contents and click each section for quick navigation.
Update 26 Jan 2023 – Hive Ransomware taken down.
An international operation led by the FBI and German law enforcement with support from the National Crime Agency (NCA) has taken down the HIVE strand of ransomware service used by cyber criminals to attack and extort businesses worldwide. The servers of the HIVE ransomware were taken offline, and anyone trying to access the HIVE infrastructure will now be met with a law enforcement splash page explaining that the network has been seized and is no longer available for use.
HIVE was available for purchase on the dark web and allowed criminals to launch ransomware attacks by sending it as an attachment to a phishing email, infecting the victim’s computer and encrypting their system until a ransom payment was made. The group has targeted over 1,300 victims worldwide since June 2021 and received over $100 million in ransom payments. The FBI developed the capability to circumvent HIVE encryption, and the NCA supported a number of victims in the UK to remove the impact of the ransomware.
The operation was a collaboration between multiple international law enforcement partners, including the US Secret Service, Canada, France, Germany, Ireland, Lithuania, Norway, Portugal, Romania, Spain, Sweden, and the UK. The NCA’s National Cyber Crime Unit continues to work closely with partners to tackle the national security threat of cybercrime and urges businesses to come forward and report any incidents to law enforcement.
A comparatively new ransomware, Hive is around one-and-a-half-years-old in the wild, but it is already among the top ransomware threats in the industry. Threat actors have been using Hive ransomware to target a variety of companies and critical infrastructure sectors, particularly healthcare, government facilities, communications, critical manufacturing, and information technology.
Original article:
According to the Joint Cybersecurity Advisory published by the FBI, CISA, and HHS as part of their #StopRansomware effort, as of November 2022, the Hive ransomware threat actors have targeted more than 1,300 businesses globally and have bagged almost US$100 million in ransom.
Source: https://darkfeed.io/
Similar to BlackCat and LockBit, the Hive syndicate is a Ransomware-as-a-Service (RaaS) provider, that was first reported in June 2021 against a Canadian IT company. Hive made headlines in August 2021 for interrupting the clinical and financial activities of three hospitals in Ohio and West Virginia as a result of Hive’s ransomware assaults. On the ground level, this forced the emergency rooms to divert traffic, and cancel radiological tests and urgent surgery cases; while causing the FBI to issue alerts detailing the indications of compromise (IOCs) and tactics, techniques, and procedures (TTPs) used by Hive ransomware.
Compared to other ransomware actors, the Hive syndicate functions in quite an organized manner with multiple portals and work distribution. While the developers build, maintain, and upgrade the Hive infrastructures – malware variants, data leak website the “HiveLeaks” and the negotiation site; the affiliates are responsible to locate victims, infect them, steal their files, and spread Hive ransomware over the networks of victims. Hive provides RaaS through its three primary API-based portals – affiliate, victims, and data leak site.
We at Logpoint deployed multiple variations of the ransomware and have attempted to create a comprehensive detection and understanding of it in the following section.
Hive fast facts
-
First reported in June 2021 and has amassed almost $100 million in ransom from 1,300 global businesses.
-
Affiliates discovered to have used spam campaigns, leaked credentials, and vulnerable servers for initial access.
-
Targets healthcare, government facilities, communications, critical manufacturing, and information technology.
-
Known for strict negotiations and double or sometimes triple extortion methods for extorting the ransom.
-
Known to re-infect victim organizations that restore infrastructure without making a ransom payment.
-
Has multiple ransomware variants affecting Windows, Linux, FreeBSD, and VMware ESXi with the latest iteration written in Rust Programming Language, while the older ones developed in Go.
Technical analysis of Hive
For our research, the Hive ransomware variants in consideration were abstracted from vx-underground while samples from tria.ge sandbox were also referenced. The results are summarized below.
Intrusion
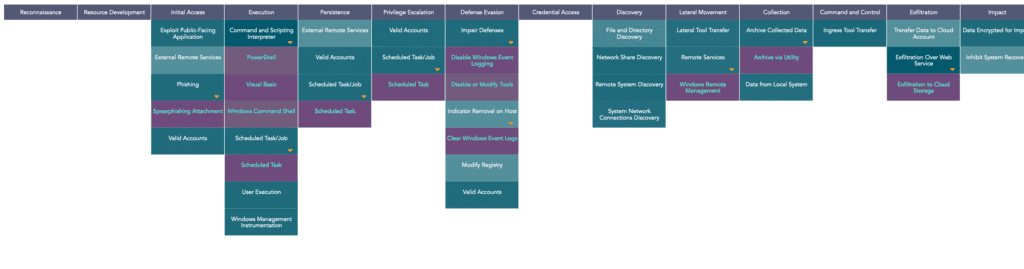
The common method of initial access, phishing with malicious attachments [T1566], and leaked/compromised credentials [T1078], remains a prominent approach for the Hive ransomware threat actors. Further, Hive actors have also been found to exploit vulnerabilities in public-facing applications [T1190]:
-
Microsoft Exchange server vulnerabilities: CVE-2021-31207, CVE-2021-34473, and CVE-2021-34523 to drop web-shells into the web server, and
-
FortiOS SSL-VPN MFA vulnerability: CVE-2020-12812, to gain access to FortiOS servers
Therefore, it can be stated that the method for initial access into the target system depends on the affiliates’ capabilities.
Execution and persistence
Right after the Hive actors find their way into the target system, they attempt to establish persistence by executing obfuscated Powershell script [T1059] that is a part of the Cobalt Strike beaconing technique for command and control and lateral movement in the target network.
Following that, they begin executing multiple Powershell commands to stop/disable important security services and processes like SamSs, SDRSVC, SstpSvc, vmicvss, VSS, wbengine, WebClient, and UnistoreSvc_196e4 using system executables – “net.exe”/”net1.exe” and “sc.exe” that might otherwise hinder its attack chain.
Defense evasion
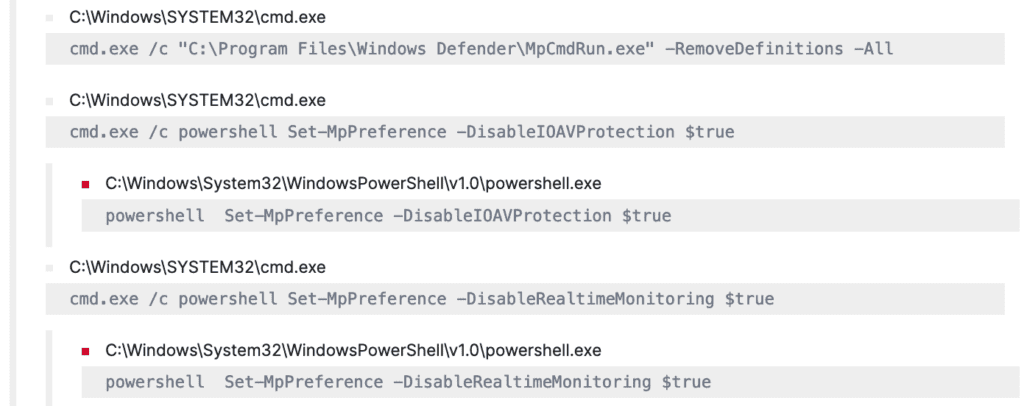
The malware notoriously inhibits detection by modifying registry entries [T1112] and scheduling tasks through “reg.exe” and “schtask.exe” respectively, to disable/stop security monitoring services and Windows Defender Real-Time Protection.
Hive makes use of “MpCmdRun.exe” to delete anti-virus definitions and disable the protection status [T1562].
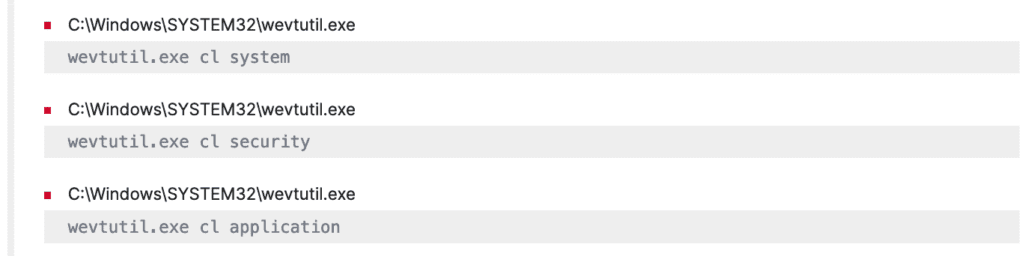
Further, Hive also removes its activity traces by clearing out system, security, and application logs [T1070] by exploiting the “wevtutil.exe“ binary.
Actions on objectives
Once the detections have been disabled, Hive quietly exfiltrates data archived through tools like “7-Zip” and “Rclone” to anonymous file sharing/cloud storage service [T1537] providers like “Mega“, “Anonfiles“, “Ufile“ and “Privatelab“, and then proceed to delete the shadow copies, using “vssadmin.exe” and “wmic.exe“ behind the user visibility zone to prevent any suspicion. Further, it also deletes the system state backups using “wbadmin.exe“ to make the system irrecoverable.
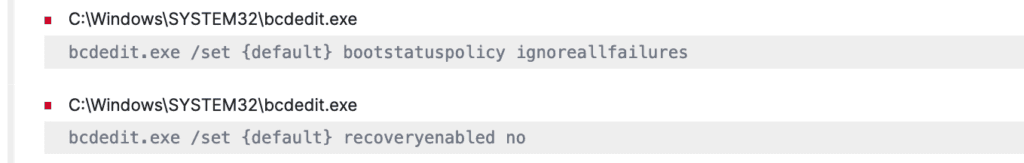
To leave no stone unturned, the malware performs one last thing before encrypting it all, that is, it modifies the boot configuration data of the system using “bcdedit.exe“ to restrict the system administrator’s access to the Windows Recovery Environment’s System Image Recovery capability and therefore inhibit system recovery [T1490].
The malware finally enacts its actual agenda – it executes the ransomware and encrypts all the files of the system [T1486]. The newer variants of the ransomware use Elliptic Curve Diffie-Hellmann (ECDH) with Curve25519 and XChaCha20-Poly1305 (authenticated encryption with ChaCha20 symmetric cipher) for the encryption. The ransomware iterates the action in all the systems it has access to.
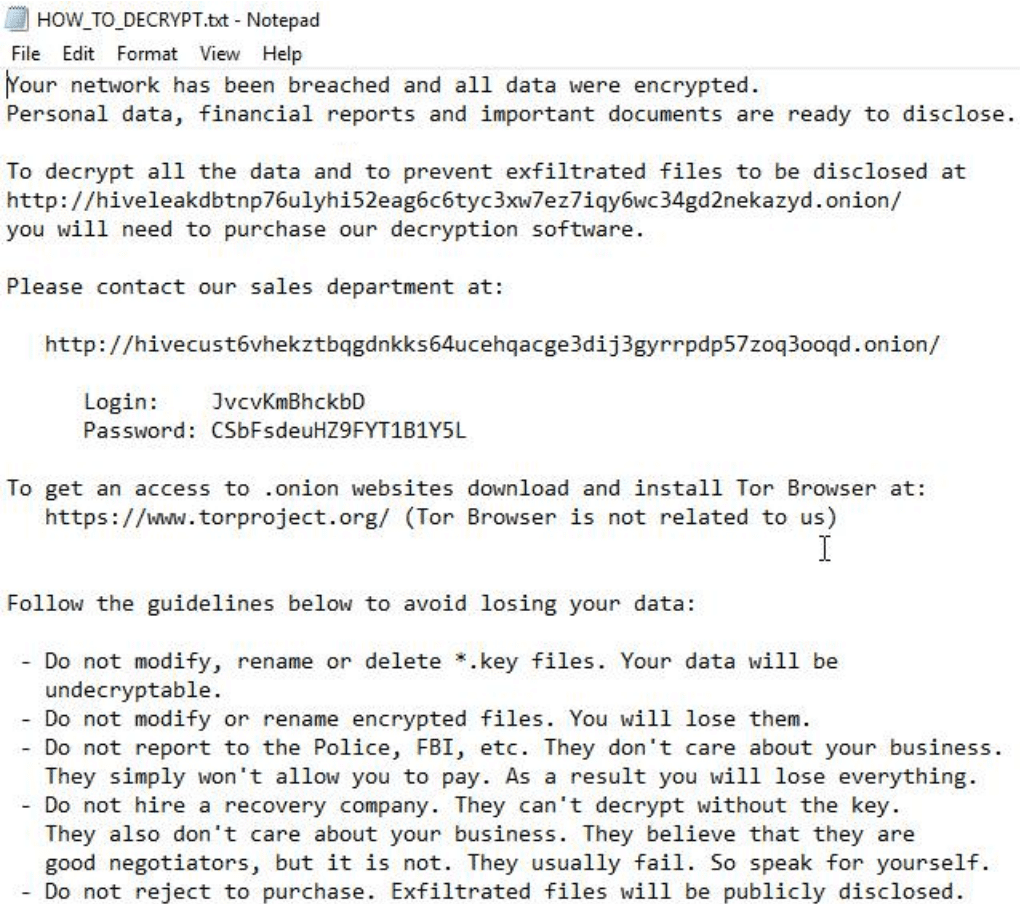
Once the entire disk files have been encrypted, a message pops up in a “HOW_TO_DECRYPT.txt” notepad file, notifying the users about the incident that happened in their system, URL link, and credentials to log in to the hive’s .onion/ portal for negotiations with the “Sales Department”, and guidelines as a warning.
Hunting Hive with Logpoint
Let’s begin our hunt all the way from the start of the incident. A very common method among both threat actors and defenders, spearphishing is still the most adopted technique to exploit the human element and infiltrate the target system. Therefore, we can be on the lookout for suspicious processes spawned by Microsoft Office utilities:
We have also observed Hive exploiting the Microsoft Exchange server’s ProxyShell vulnerability. Therefore, suspicious activities can be monitored through, “Exchange ProxyShell Pattern Detected”
and “Successful Exchange ProxyShell Attack“
Next, another widely used hacking tool is the Cobalt Strike beaconing. This is used for execution and maintaining persistence in the system. At Logpoint, we have been continuously offering our customers detection and understanding of various hacking tools, techniques, and methods that are prominently used by threat actors for different purposes in most of their attack campaigns. As such, detection for tools like Cobalt Strike and Mimikatz, also leveraged by the Hive actors, have been published and reviewed time and again.
To take it a step further, it has also been found that Hive actors execute base64 encoded commands to bypass detection during the beaconing phase. Detection of commands executed for encoded keywords can be of huge interest to us and therefore can be viewed through “Malicious Base64 Encoded PowerShell Keywords in Command Lines Detected“
Hive actors then proceed with terminating/disabling multiple processes and system services. We can look into those with the desired level of consolidated visibility through “High Number of Service Stop or Task Kill in Short Span“
Here, we have considered the occurrence of the event – process stop or service disable, to be greater than ten times. You can modify it based on your environment and requirements.
In an attempt to evade native defenses and maintain stealth for its future activities, Hive begins to modify the registry values of Microsoft Windows Defender with “reg.exe“, which could otherwise possibly detect its activities and trigger alerts. Hence, making the detection of such nasty acts our top priority with “Windows Defender Antivirus Disabled via Registry Modification”.
“Windows Security Health Disabled via Registry Modification”
Hive exploits the Malware Protection Command Line Utility – “MpCmdRun.exe“, to remove any or all antivirus signature definitions present in the system. The detection can be achieved with “Microsoft Defender Antivirus Definitions Removal Detected“
“Microsoft Defender Disabling Attempt via PowerShell”
To leave no traces of its activities, Hive also clears all the system, security, and application logs mostly using the “wevtutil.exe“ system binary which can be detected by “Suspicious Eventlog Clear or Configuration Using Wevtutil Detected“
Once the actors are sure of having no obstruction, they begin exfiltrating important organizational data. We found the hive actors to use “7z.exe“ to exfiltrate compressed or encrypted data to cloud storage services like Mega, Anonfiles, and more. This can be easily detected.
Along with exfiltrating data, they begin to delete/destroy shadow copies and system state backups leaving the organization with no back-ups or recovery points, “Shadow Copy Deletion Using OS Utilities Detected“
Further, threat actors make sure to deactivate and completely turn off the system administrators’ access to Windows Recovery Environment abusing “bcdedit.exe“ to modify the boot policy, which can be detected as, “Possible Modification of Boot Configuration“
The final act of the show – ransomware – begins its encryption after all this and drops a message through a notepad text file. Early detection is important.
MITRE tactics and techniques
Investigation and response with Logpoint
Logpoint SOAR can be the weapon in your arsenal to respond against a Hive ransomware attack and disrupt its cyber-kill chain.
1. Phishing investigation and response
Ensuring that all suspected phishing occurrences are properly investigated and responded to, the playbook drastically cuts down on response times and human error.
2. Ransomware investigation
This playbook extensively evaluates the IoCs and detonates the suspect files leveraging a sandbox environment. Additionally, it searches for typical TTPs that ransomware employs, increasing the likelihood that ransomware will be found before it is too late. If ransomware is detected, the playbook will alert administrators and begin upfront tasks to isolate the host and contain the threat.
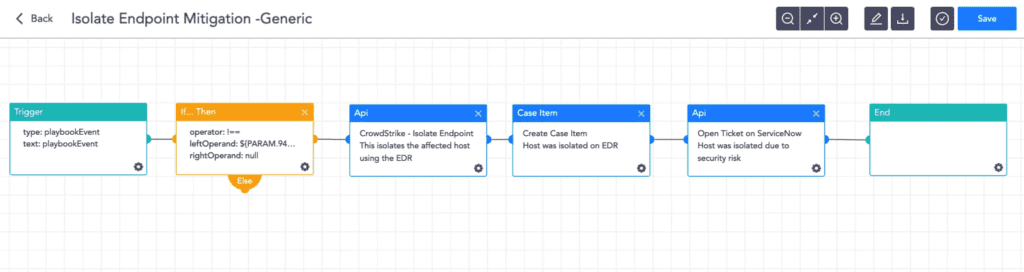
3. Isolate endpoint
Before the infection spreads to other machines, this playbook discovers and isolates the infected host using the brand-new Logpoint AgentX.
Logpoint AgentX is a lightweight application that transports logs and telemetry from endpoints (all servers, workstations, and applications) to the SIEM, and performs automated real-time investigation and remediation of threats with SOAR. With AgentX, security analysts get precise detection of malicious malware and the ability to respond to threats in endpoints.
Logpoint AgentX is available now: Contact your representative.
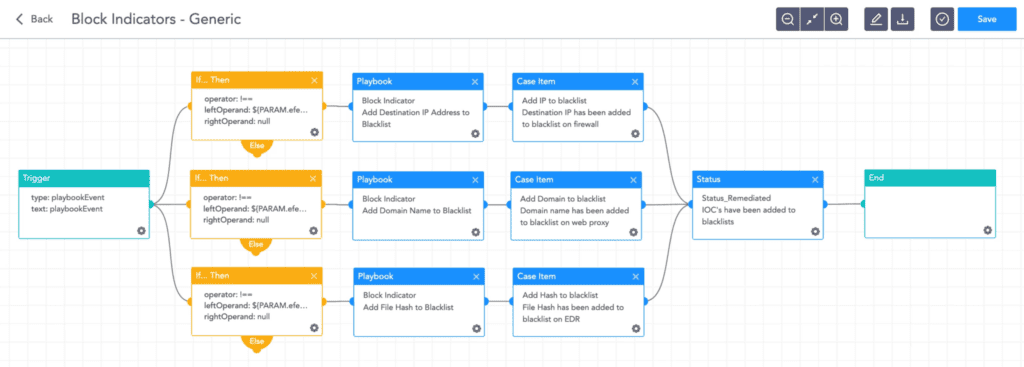
4. Block indicators
This playbook checks if any IP, domain, URL, or host exists in a list of IoCs, blocks them, and adds them to the blocked list.
Remediation and mitigation best practices
-
Regularly scan and assess organizational assets for vulnerabilities and misconfigurations to patch them, and maintain updated Operating Systems, firmware, and applications.
-
Strongly enforce MFA and phishing protection for both user and administrative accounts. Adopt the practice of least privilege and time-based access, where possible.
-
Conduct simulated attack scenarios to make sure that the employees are well aware of phishing and other risks, and also to make sure that they report the incident to the internal cybersecurity team.
-
Extensively implement network segmentation to prevent the spread and limit the impact.
-
Deploy Logpoint AgentX or other endpoint protection platforms (EPPs) to secure endpoint devices and ensure they are up-to-date, properly configured, and trigger alerts when disabled.
-
Develop the practice of regularly creating and maintaining offline encrypted backups that encompass the entire organizational data infrastructure, and assure their availability through periodic restoration attempts.
-
Regualrly review the security posture of third-party vendors interconnected with the organization.
-
Actively be on the lookout for leaked credentials on malware data leak sites, and make changes accordingly.
-
Continuously monitor critical organizational assets with a combination of tools such as Sysmon and the Logpoint Converged SIEM platform.
Final thoughts
Despite being new in the industry, Hive ransomware has an alluring rate of successful attacks, amassing additional affiliates to the gang. Therefore, a proactive detection approach is of utmost priority for security analysts of any organization wishing to stay away from harm’s way.
With the Logpoint Converged SIEM platform combining SIEM, SOAR and endpoint response, analysts can investigate Hive and initiate a proper response. With the resources in this report, we hope to enable our readers with the capabilities to actively hunt Hive ransomware and disrupt it’s chain of attack.
** We can help you! For help with the suggested playbooks – design, development, and implementation – contact Global services here.