Cobalt Strike, first released in 2012, is a commercial adversary simulation tool and is popular among red teams, pen-testers, and threat actors alike. In essence, Cobalt Strike is a modularized post-exploitation framework that uses covert channels to simulate a threat actor in the organization’s network.
Cobalt Strike’s popularity is mainly due to its beacons being stealthy, stable, and highly customizable. The beacons are stealthy due to in-memory execution via reflection into the memory of a process without affecting the file system. Cobalt Strike’s post-exploitation suite includes support for keylogging, command execution, credential dumping, file transfer, port scanning, and more, making the adversary’s job easier. Malleable C2 is another beloved feature of Cobalt Strike that allows attackers to change how its beacons look and mimic other legitimate traffic to stay under the radar.
Though the vendor screens the distribution of licenses to security professionals, adversaries were able to crack and leak it frequently. In fact, two months before, Proofpoint had reported that adversarial use of Cobalt Strike increased 161 percent from 2019 to 2020 and still remains a high-volume threat in 2021. Proofpoint disclosed that they had attributed two-thirds of identified Cobalt Strike campaigns from 2016 through 2018 to well-resourced cybercrime organizations or APT groups. APT29, APT32, APT41, Cobalt, FIN6, TA505, TIN WOODLAWN and Mustang Panda are just some of the threat actors who have used Cobalt Strike for their operations.
Cobalt Strike was repeatedly used in the high-profile SolarWinds supply chain incident where the Raindrop loader dropped the Cobalt Strike payload. Several ransomware strains like Ryuk, Conti, Egregor and DoppelPaymer have started to use Cobalt Strike to speed up their ransomware deployment. In September 2020, Cisco Talos reported that 66 percent of ransomware attacks involved Cobalt Strike and ransomware actors heavily rely on the tool as they abandon commodity trojans.
Cobalt Strike’s post-exploitation features are exposed via beacons that are executed in the memory of the infected system. Security analysts can create detections from the beacon’s leftover artifacts while performing post-exploitation. Similarly, analysts can use default settings like beacon names and default certificates to help aid detection.
LogPoint has now released UseCases v5.0.4, which includes alerts and a dashboard for Cobalt Strike to help you identify threats within your environment, so you can take corrective actions against them.
Detecting Cobalt Strike activity in LogPoint
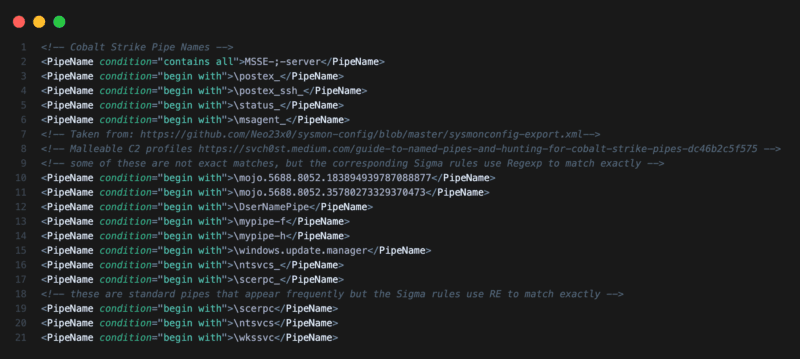
Named pipes are essential for the operation of Cobalt Strike beacons. Before version 4.2, Cobalt Strike did not allow the operators to change the default naming scheme of named pipes. If Sysmon is deployed in the environment and correctly configured, then it is an opportunity to detect Cobalt Strike’s default named pipes.
norm_id=WindowsSysmon label=Pipe
pipe IN ["\msagent_*", "\MSSE-*-server", "\postex_*", "\status_*", "\mypipe-f*", "\mypipe-h*",
"\ntsvcs_*", "\scerpc_*", "\mojo.5688.8052.183894939787088877*", "\mojo.5688.8052.35780273329370473*"]
Sysmon rules for Cobalt Strike Pipe Names
LogPoint customers can refer to our base sysmon configuration that covers various Cobalt Strike activities.
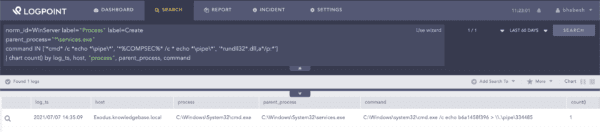
Adversaries commonly use Cobalt Strike’s named pipe impersonation feature to obtain SYSTEM privileges that can be detected via process creation events.
norm_id=WinServer label="Process" label=Create
parent_process="*\services.exe"
command IN ['*cmd* /c *echo *\pipe\*', '*%COMPSEC%* /c * echo *\pipe\*', '*rundll32*.dll,a*/p:*']
Search for Cobalt Strike Named Pipe Impersonation
You can also hunt for artifacts in services created by Cobalt Strike from the Service Control Manager (SCM) logs.
norm_id=WinServer event_id=7045 ((path="*ADMIN$*" service="*.exe") OR (path="%COMSPEC% /b /c start /b /min powershell -nop -w hidden -encodedcommand*"))
The creation of the Sysmon remote thread logs aids in detecting Cobalt Strike’s process injection activity.
norm_id=WindowsSysmon event_id=8 start_address IN ["*0B80", "*0C7C", "*0C88"]
Cobalt Strike spawns rundll32 without any command-line and regularly injects the necessary payload code into rundll32’s memory. Therefore, you must check for the creation of rundll32 without any command-line arguments unaffected by the noise.
label="Process" label=Create
"process"="*\rundll32.exe" command="*\rundll32.exe"
Next, you can decode PowerShell sessions with the default command-line prefix and watch for snippets of commands commonly used by Cobalt Strike.
norm_id=WinServer event_source=PowerShell event_id=400
application="powershell -nop -exec bypass -EncodedCommand*"
| norm on application -<:'EncodedCommand\s'>
| process codec(decode, encoded_command) as decoded_command
| search decoded_command IN ["*IEX*DownloadString*127.0.0.1:*",
"Invoke-WMIMethod win32_process*-argumentlist*", "Invoke-Command -ComputerName*-ScriptBlock*", "*=New-Object IO.MemoryStream [Convert]::FromBase64String*"]
| chart count() by host, device_ip, decoded_command, encoded_command
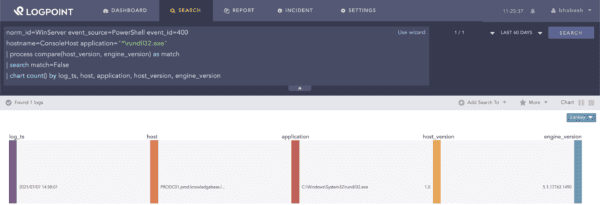
Cobalt Strike’s powerpick command enables the execution of unmanaged PowerShell. You can hunt for the activity via mismatch in the host version and engine version in PowerShell’s Engine Lifecycle events.
norm_id=WinServer event_source=PowerShell event_id=400
hostname=ConsoleHost application="*\rundll32.exe"
| process compare(host_version, engine_version) as match
| search match=False
Search for mismatch in host version and engine version in PowerShell’s Engine Lifecycle events
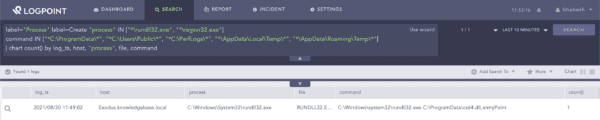
Proxy execution via RunDLL32 and Regsvr32 remains the most popular method for executing Cobalt Strike beacons. You can hunt for executions of the binaries from suspicious locations.
label="Process" label=Create "process" IN ["*\rundll32.exe", "*\regsvr32.exe"]
command IN ["*C:\ProgramData\*", "*C:\Users\Public\*", "*C:\PerfLogs\*", "*\AppData\Local\Temp\*", "*\AppData\Roaming\Temp\*"]
Search for loading of DLLs from suspicious paths
You can hunt for default certificates that appear with Cobalt Strike when adversaries forget or ignore to change the default certificates.
(certificate_serial="8BB00EE" OR certificate_serial_number="8BB00EE")
Search for default Cobalt Strike certificate
Finally, watch for IDS/IPS alerts related to Cobalt Strike. Cisco Talos provided a list of snort rules that can help you detect the Cobalt Strike infection.
norm_id IN [Snort, SuricataIDS]
(message IN ["*CobaltStrike*", "*Cobalt Strike*"]
OR signature IN ["*CobaltStrike*", "*Cobalt Strike*"])
Expect the use of Cobalt Strike to rise
Many threat actors use default settings in Cobalt Strike, making detections easier for defenders. On the other hand, sophisticated threat actors who care about OPSEC, change the defaults to evade detection. Enterprises can purchase threat intel feeds, such as DFIR Reports, to obtain a list of IP addresses of Cobalt Strike servers used as IoCs to sweep their network.
In the coming years, you can expect threat actors to continue and even increase their use of Cobalt Strike to help target all industries due to the stability, versatility, and difficult attribution of Cobalt Strike.