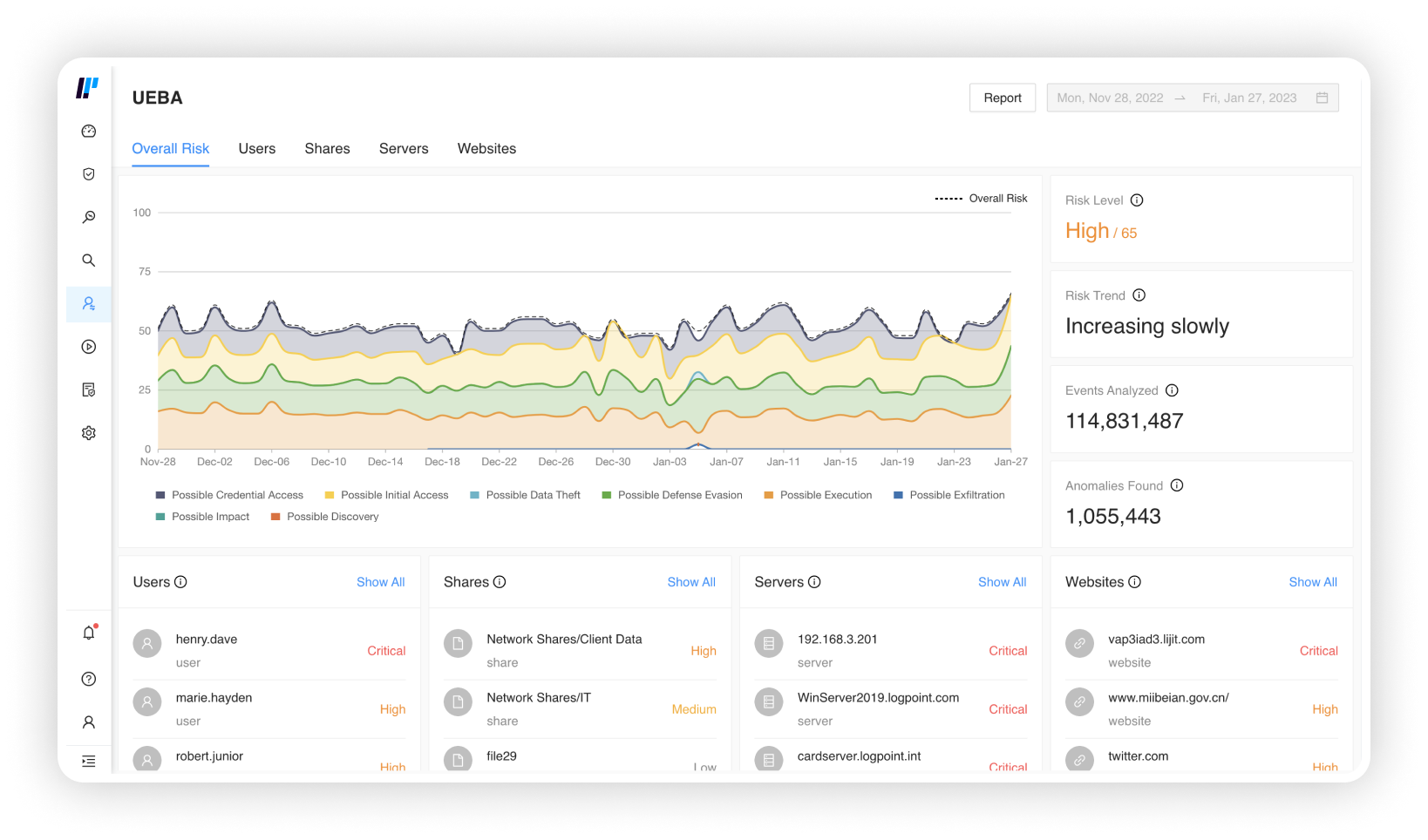
With inside access, internal
threats evade detection
Whether through stolen credentials, phishing or simple human error, 82% of breaches involve the human element. Insiders have the upper hand because they already have access to the system, making them difficult to investigate and 10x more effective at exfiltrating data than external actors.
Immediately detect anything
out of the ordinary
Reduce the impact of breaches
Machine learning helps security teams quickly detect and deal with suspicious behavior
Mitigate the full security risk
Alert context equips security teams to understand and address the full scope of insider threats

Justify cybersecurity investment
High-fidelity risk scoring ensures teams identify and respond to otherwise hard-to-detect threats
Save time and identify anomalous behaviour
Analyzing data across the organization and security infrastructure, Logpoint uses AI-driven profiling of behavior norms and patterns to build user and group baselines and peer groups.
Logpoint performs behavioral analysis to alert when there are deviations from baselines to identify truly anomalous behavior.
Analysts can detect and track insider threats, while also eliminating time spent on false positives.
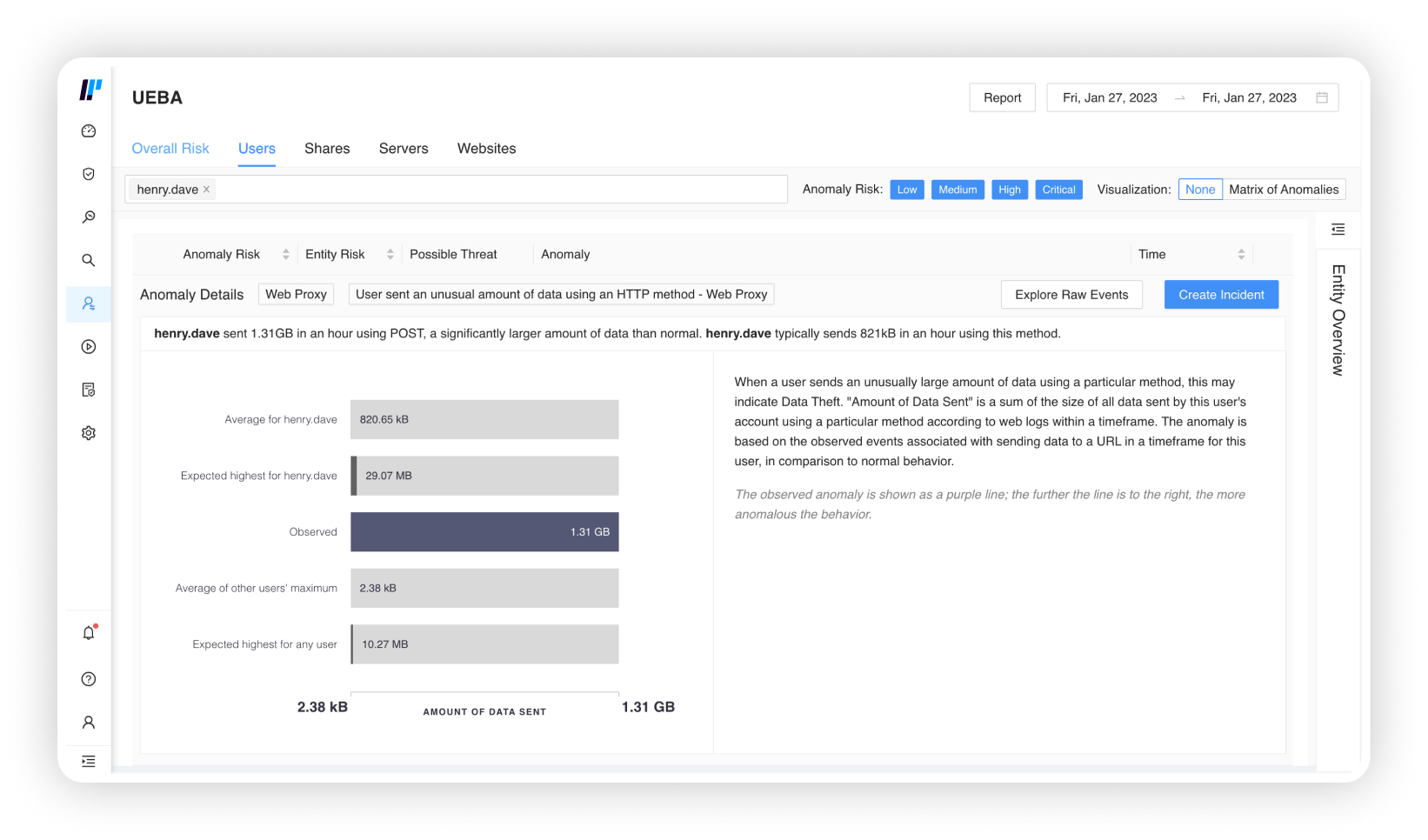
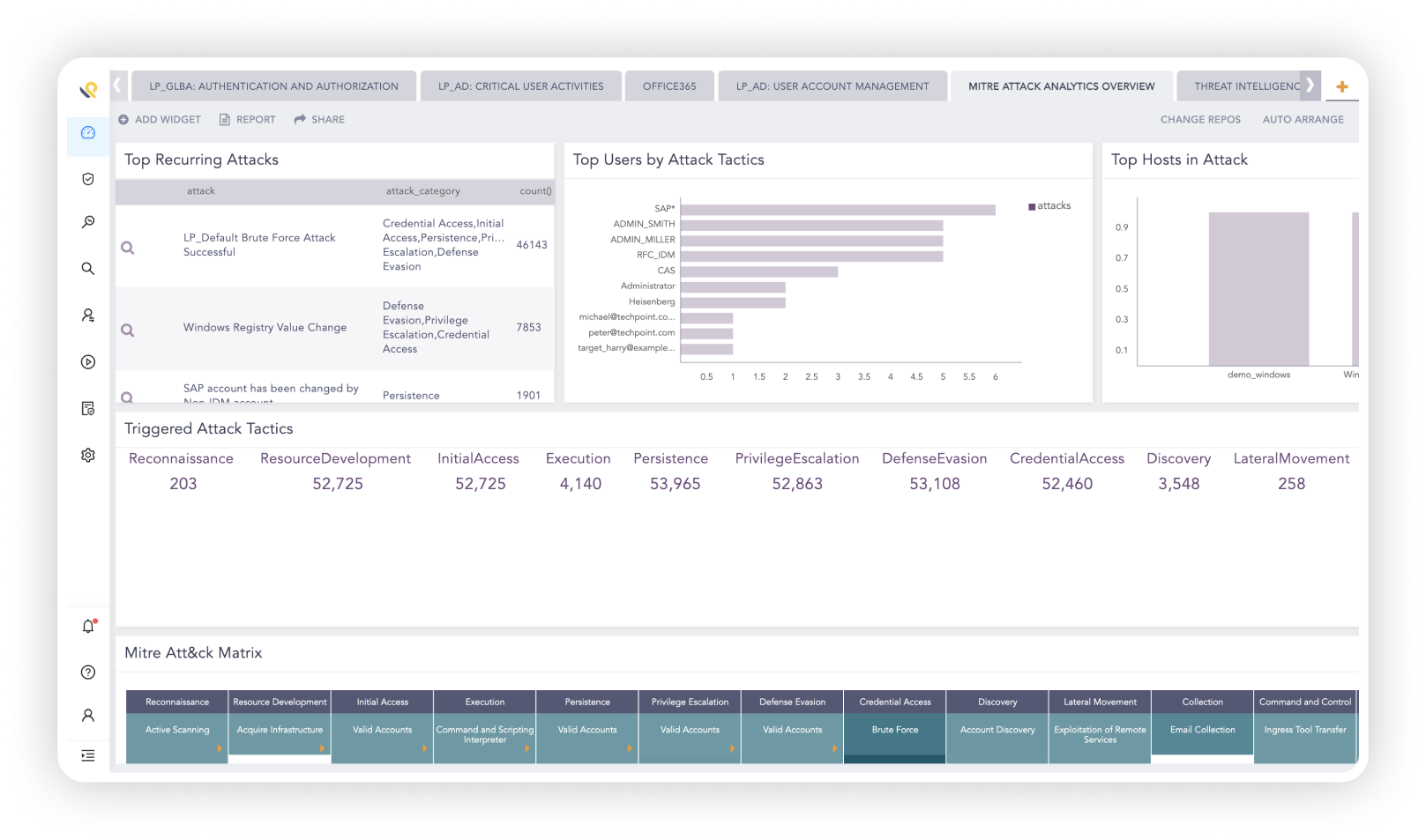
Easily track and investigate insider threats
Logpoint automatically adds threat intel, business context and entity risk to each alert to help analyst get a full picture of each incident.
Fuse weaker signals by applying sophisticated machine learning and detection logic and utilize automation providing contextual information from threat and vulnerability sources.
With all anomalies mapped to the MITRE ATT&CK framework, analysts can easily get an overview of the threat landscape and track the stages of an insider threat.
Reduce time to detect and respond
Logpoint uses high-fidelity risk scoring as an enrichment source for threat detection and incident response to reduce response time to attacks. The faster you’re aware of an intrusion, the greater your ability to control it.
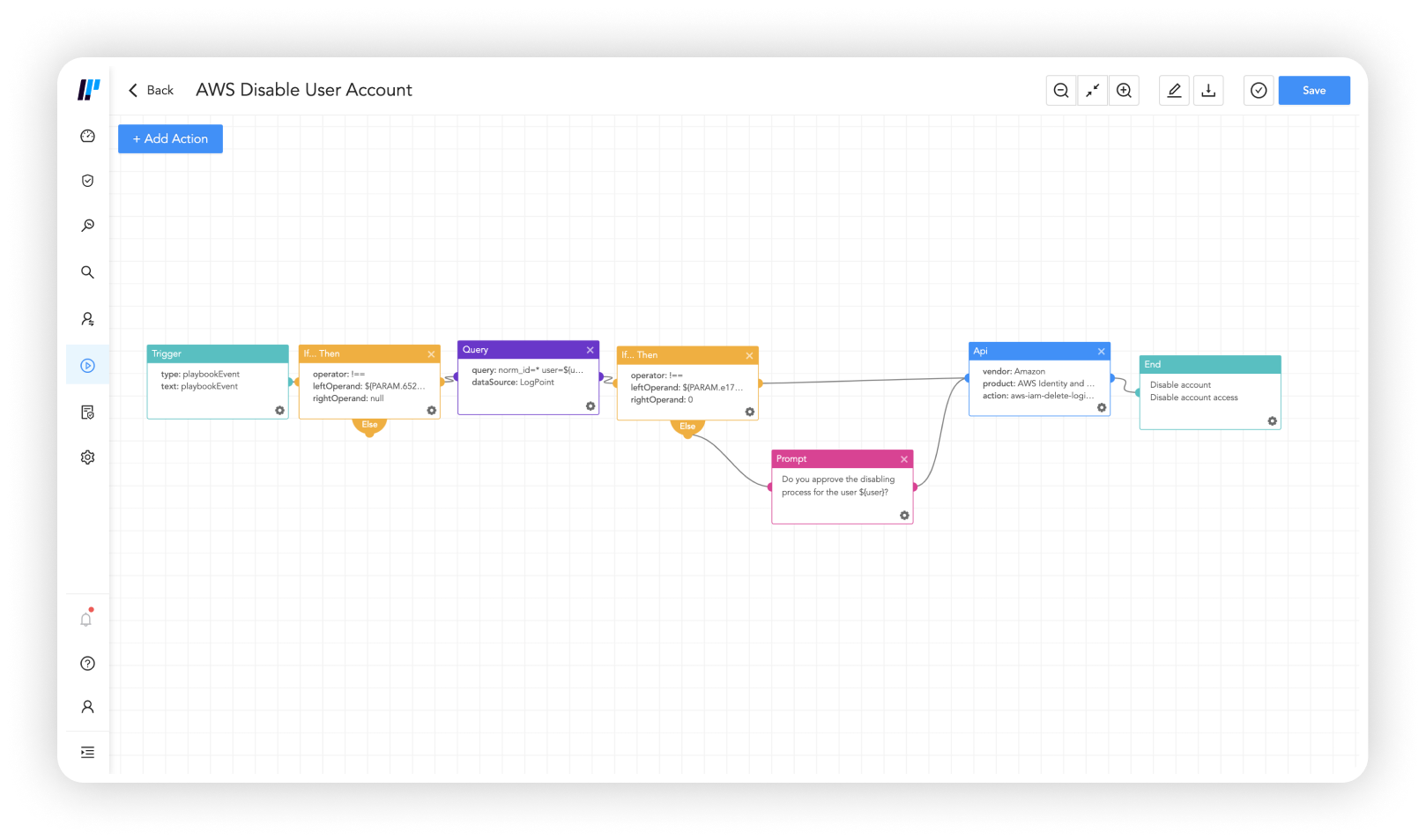
Response playbooks combined with response capabilities on endpoints help automate orchestration and remediation to put a stop to insider attacks, such as disabling user accounts or removing access from laptops.
With Logpoint we were instantly alerted and were able to track down what that IP did on our network, quickly identify
the compromised alumni account alumni and lock the account. With Logpoint, we had the tool to make that determination quickly and efficiently.
We experienced a lot of unsuccessful – and automated login attempts in Active Directory and in the infrastructure. It was clear to us that pressure was mounting and we needed [Logpoint] to give us a full overview, help us keep a close eye on things, and alert us in case of potential breaches.
Get up to date with the
Logpoint blog!