Personal Identifiable Information Access Monitoring
Strengthen your compliance with full control of your sensitive data.
SAP stores a wealth of sensitive and Personally Identifiable Information (PII), dispersed throughout a multitude of different applications, integrations and databases. Knowing where your sensitive data resides, who has access to it and how to monitor it is almost an impossible task.
With centralized monitoring, we provide you with holistic insight, so you can manage violations more effectively and you no longer operate in the dark to meet the compliance regulations.

Effectively Detect and Manage Access Violations
Read Access Log (RAL) is automatically configured and extracted into SIEM, delivering comprehensive security monitoring of your sensitive data. Detect and manage access violations, data leakage, and misuse of personal sensitive data with a comprehensive, all-in-one overview.
Meet Compliance Regulations
Monitor user authorizations in your SAP systems to detect access to critical transactions, disclosed corporate information, and personal data. Secure your sensitive data with a powerful and centralized logging solution.
Holistic Overview at a Glance
Execute faster. No need to waste time monitoring system by system. To help you manage violations more effectively, we have centralized monitoring and provide you with all the insights you need in one view.
Use Case: Safeguard your Sensitive Data Against Theft

GDPR aims to protect personally identifiable and sensitive data from misuse. To operate within the EU and sell goods to EU citizens, ensure you comply with GDPR standards for collecting, storing, and managing personal data. Non-compliance can result in severe fines, penalties, and undermine the legitimacy of your business.

Sensitive data is compromised by an employee
Through the transaction code PA20, an insider within a supply industry gained access to salary and pension payment information. This data was downloaded, sent to a private email, and subsequently distributed via mail to employees in the organization. Disclosing such sensitive data is an abuse and a clear violation of the GDPR regulations. Figuring out who had access, which accounts were accessed, and who distributed the data can be difficult.
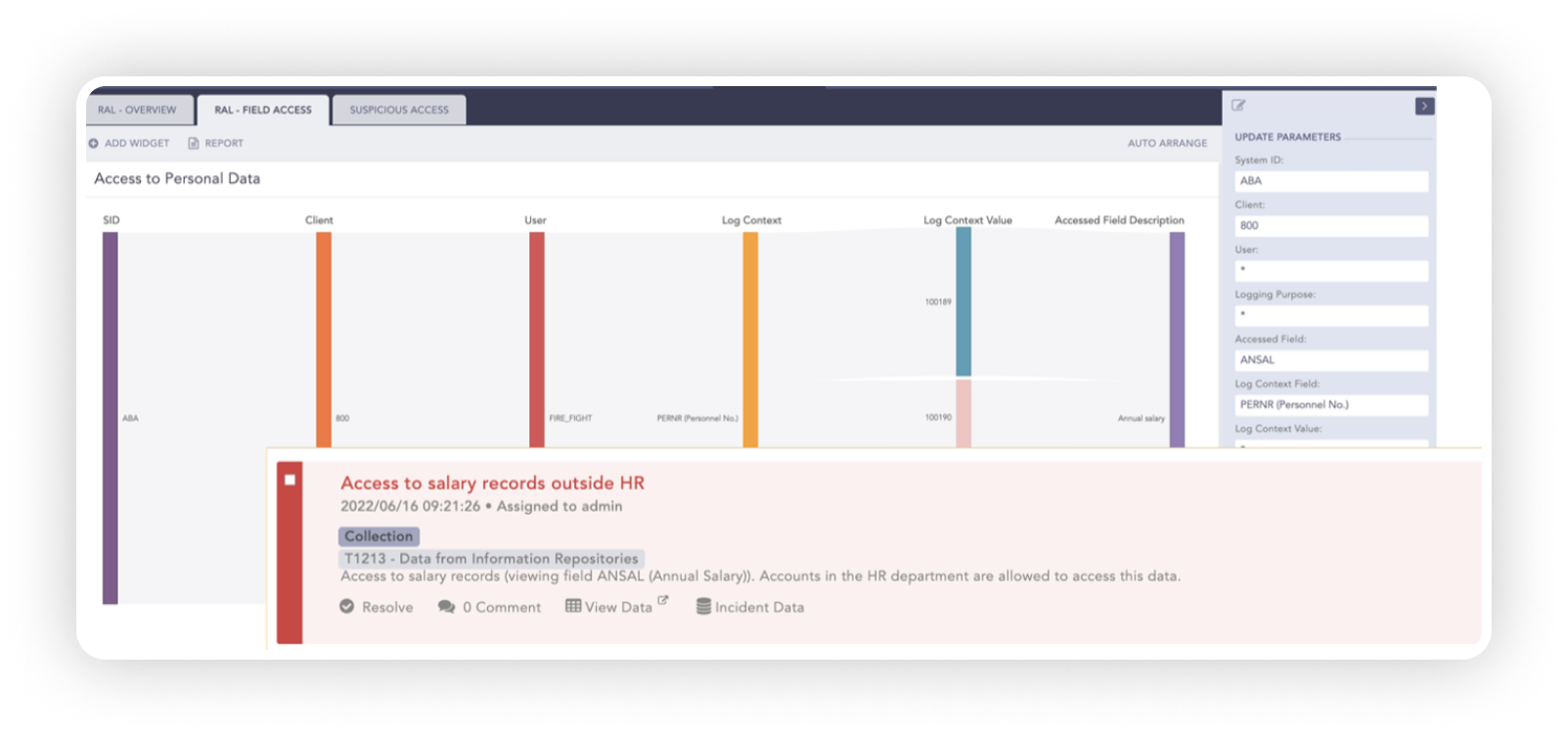
Downloading SAP information is a normal activity within the system. However, whenever sensitive data leaves the organization, it is essential this gets detected and flagged. Discovering such breaches is only possible if you monitor your SAP data holistically and in combination with the organization’s wider security operation.
With the PII Access Monitoring solution, your SAP logs are continually cross -correlated with logs from the e-mail, VPN access, etc. so you quickly can detect if your sensitive data has been displayed, downloaded, or sent to a private email. With our comprehensive out-of-the-box logging solution, you can effortlessly access, extract, centrally collect and automatically monitor RAL with appropriate rules.