FAST FACTS
-
Kapeka, also known as KnuckleTouch, originally appeared in mid-2022 but was formally tracked in 2024 due to limited-scope attacks, particularly in Eastern Europe.
-
The Kapeka backdoor is linked to the Sandstorm Group, which is run by Russia’s Military Unit 74455 and is notorious for disrupting cyber activity.
-
Sandstorm’s operations, including Kapeka’s deployment, are tied to geopolitical tensions, specifically targeting Ukraine’s critical infrastructure.
-
Kapeka exhibits advanced functionalities, including initialization, C2 communication, task execution, and persistence mechanisms, posing challenges to detection.

A bespoke backdoor has been observed in cyber attacks in Eastern Europe, including Ukraine and Estonia, since at least mid-2022. However, it wasn't until 2024 that it was formally tracked officially due to its involvement in limited-scope attacks, which limits public knowledge. In a Security Intelligence report published on February 14, 2024, Microsoft referred to this new backdoor as "KnuckleTouch" and attributed it to a threat actor group known as SeaShell Blizzard, which is also the name of the notorious Sandworm gang. In their most recent analysis, the Finnish firm WithSecure has tracked this same backdoor with the name “Kapeka“ (‘little stork’ in Russian) and has also attributed this backdoor to Russian APT Sandworm (recently tracked as APT-44 by Mandiant from April 2024).
The Sandstorm Group is a Russian Advanced Persistent Threat (APT) group operated by Military Unit 74455, a cyber warfare unit of Russia’s military intelligence service (GRU). Some of the names attributed to this group include Telebots, Voodoo Bear, IRIDIUM, Seashell Blizzard, and Iron Viking. Its activities came to prominence around 2014 when it exploited a zero-day vulnerability via weaponized Microsoft Office documents, affecting Windows versions from Vista to 8.1. Since then, Sandworm has been involved in various cyberattacks and cyber espionage activities, with Ukraine being its prime target. Notable incidents include repeated attacks on the Ukrainian power grid in 2015, 2016, and 2022, with the motive of causing a blackout in Ukraine. As there is still tension between Ukraine and Russia, it is a formidable threat to Ukraine with more reasons and motivation. But by no means does this only apply to Ukraine, but to the world cybersecurity landscape, which is why it was recently graduated into APT44 by Mandiant.
Despite the fact that Sandstorm's arsenal includes a variety of toolkits, our focus in this blog post will be on the Kapeka backdoor. Given its recent appearance, the gang may continue using it in cyberattack activities. Our investigation will include evaluating its sample, exploring its Tactics, Techniques, and Procedures (TTPs), and developing hunting queries for potential detection inside your systems using Logpoint Converged SIEM.
Infection Chain
The Kapeka backdoor was an early toolkit used by Sandstorm threat actors to create persistence. This backdoor includes an initial dropper malware, which is responsible for deploying the Kapeka backdoor. According to a cybersecurity firm WithSecure assessment, the backdoor has all of the essential features of backdoor malware, as well as a high level of obfuscation designed to impede examination.
Backdoor Dropper
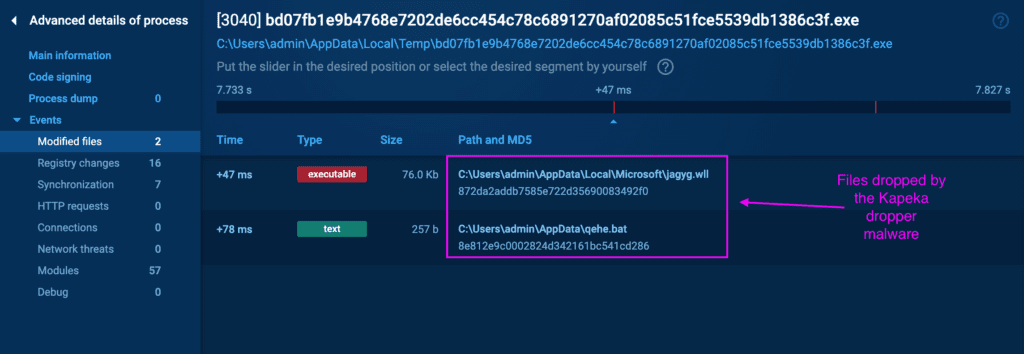
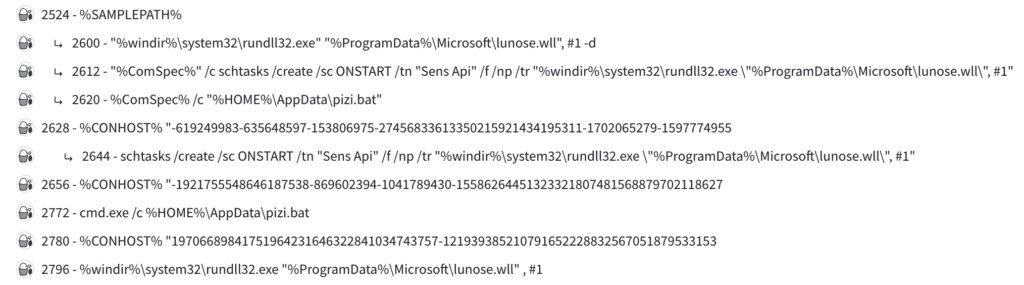
This executable file serves to initiate, execute, and oversee the actions of the backdoor. Upon execution, it drops the purportedly camouflaged Windows Add-in file with the extension '.wll', sourced directly from the dropper binary. The backdoor binary is placed either in the 'ProgramData' or 'AppData\Local' directory within the 'Microsoft' folder according to process privilege. Additionally, a batch file is dropped directly in the 'AppData' directory, intended to remove the dropper malware once the backdoor has been successfully established on the system.
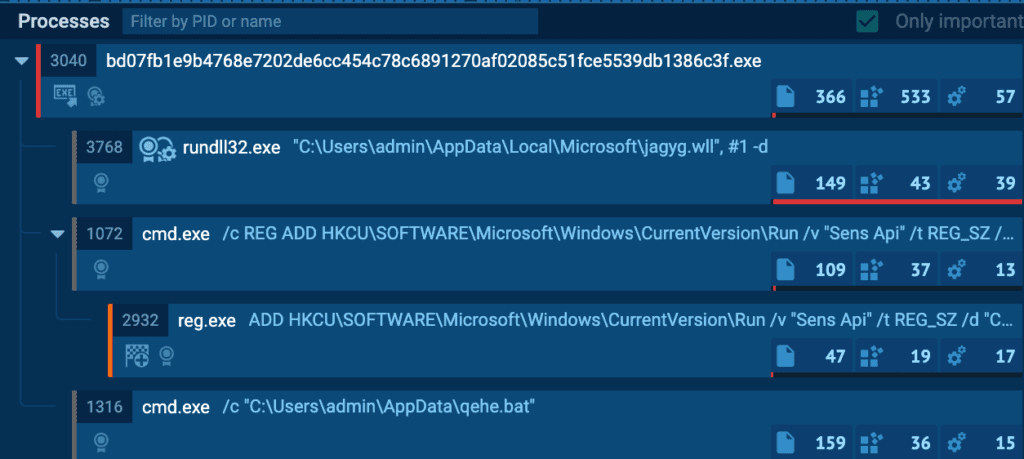
Immediately after execution, it initiates the rundll32.exe process to run the dropped .wll file’s first ordinal (#1) with the following command:
For persistence, it modifies an autorun registry to add an entry named “Sens Api“, which executes the same command as the one above.
For persistence, it modifies the autorun registry by adding an entry with the above command using the following command:
Additionally, in the same variant, the malware creates a scheduled task using schtasks.exe for persistence. The choice of persistence method depends on the privilege level of the executing process.
These actions establish mechanisms for the malware to persistently run on the system, ensuring that the backdoor file is automatically executed upon system startup. Finally, the batch file is dropped and executed to remove the original dropper malware.
Backdoor Malware
According to WithSecure, the kapeka backdoor is a Windows DLL containing one function and is exported by ordinal. This backdoor utilizes JSON to send and receive the data during its C2 communication. Its C2 configuration is encrypted via AES-256. The configuration is either decrypted during the backdoor’s initialization phase or reads the existing configuration that persisted in the registry. The backdoor persists its configuration via a registry value called “Seed” in “HKU\<SID>\Software\Microsoft\Cryptography\Providers\<GUID>\”.
The backdoor exhibits several major functionalities, enabling it to operate as a flexible tool within the victim’s environment. Here are the high-level functionalities of this backdoor as described in the WithSecure Report.
-
Initialization and Fingerprinting: The backdoor gathers information about the victim's computer and user via WinAPI calls and registry searches. This data is saved internally and transformed to transmission-ready JSON format. This data collection gives insights into the victim's system, such as user permissions, operating system specifics, machine and domain names, and so on.
-
C2 Communication: The backdoor communicates with its command-and-control (C2) server using the WinHttp 5.1 COM interface. It communicates and receives information in JSON format.
-
Task Execution: The backdoor can carry out actions on the victim's PC depending on commands received from the C2 server. These tasks include:
-
Uninstalling the backdoor.
-
Reading files from disk and transmitting them back to the C2.
-
Writing data to disk allows you to create or modify files.
-
Launching processes or payloads, which allow arbitrary executables to be run.
-
Upgrading itself by replacing the current backdoor binary with a newer one.
-
Running shell commands
-
-
Persistence Mechanisms: The backdoor maintains persistence on the victim's system by altering autorun registry entries, establishing scheduled tasks, and configuring callbacks to monitor system events such as logout. This persistence ensures that the backdoor stays active even after the machine reboots or the user logs out.
-
Data Encryption and Security Measures: The backdoor uses encryption techniques like AES encryption to secure connection with the C2 server. It also employs security techniques such as RSA-2048 public key encryption to protect sensitive data.
Overall, these functionalities allow the backdoor to establish and maintain control over infected systems, execute commands remotely, gather sensitive information, and remain resilient to removal attempts.
Detection through Logpoint Converged SIEM
Required log sources
The following should be enabled:
-
Windows
-
Windows Sysmon
Detect dropping of the decrypted backdoor binary
From the above analysis, it is clear that the backdoor is downloaded by the dropper in a fixed location with a fixed file extension. Analysts can use the following query to detect the dropping of the decrypted backdoor binary.
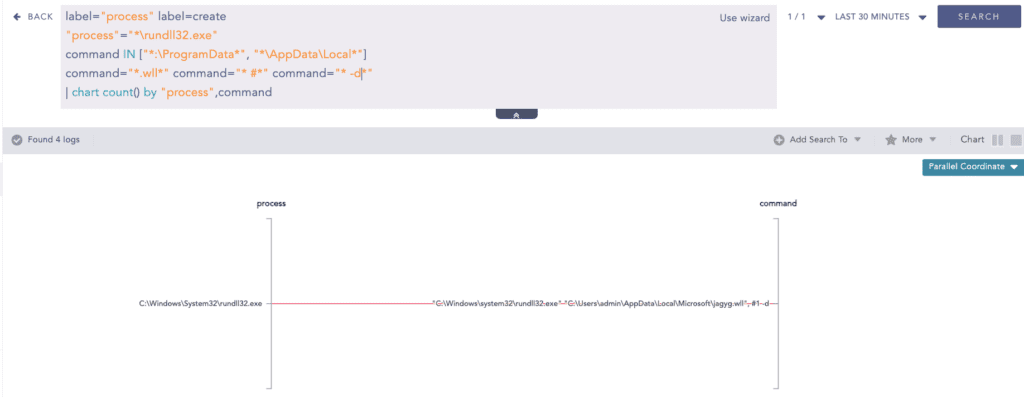
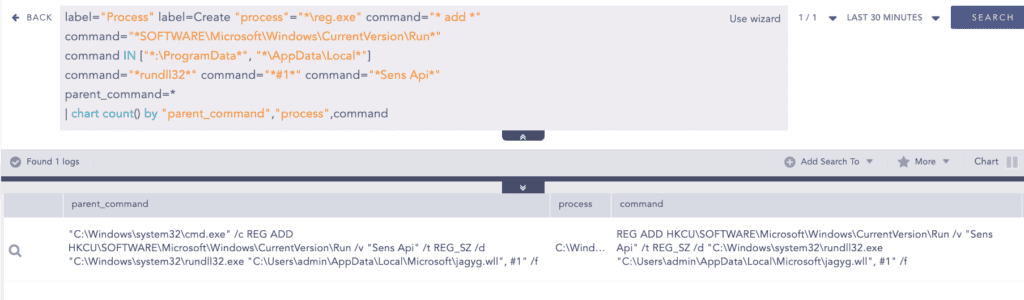
Backdoor execution via RunDLL32
Rundll32.exe is abused to proxy load the dropped backdoor binary (.wll) file. Analysts can use the given query to detect such process creation patterns.
Additionally, in the execution process, rundll32.exe loads the malicious DLL. So, we can leverage the Sysmon image load event to detect this activity through the following query.
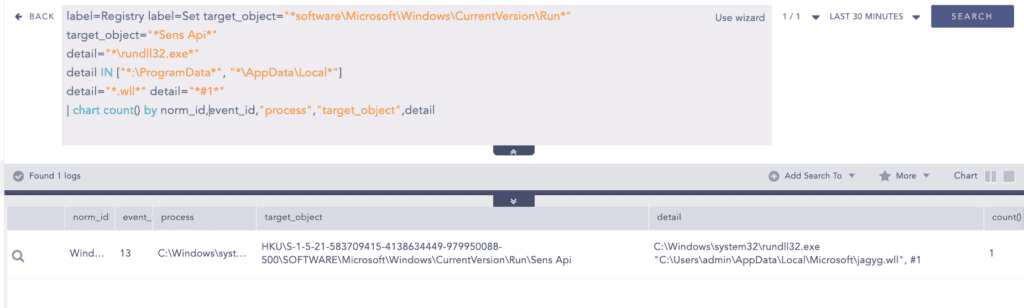
Autorun for persistence
For backdoor persistence, the dropper has been observed modifying the Autorun registry. The following query can be used to detect such process creation activity:
Schtasks for persistence
Schtask is a command-line tool in Windows that is used to schedule tasks. The dropper has used the schtask utility to persist its malicious execution on the system startup.
When a scheduled task is created, that activity is logged via Windows security event ID 4698. The Advanced Audit Policy setting Object Access > Audit Other Object Access Events has to be configured to allow this detection.
The queries provided above are specifically designed to identify the Kapeka backdoor variant. These queries are finely tuned to detect the unique characteristics and behaviors associated with this particular threat. The tactics, techniques, and procedures (TTPs) demonstrated by this particular dropper and backdoor are rather commonplace. Consequently, we have already disseminated similar alert rules through the 'Alert Rules' application. Activating these alerts on your system should ensure coverage for the aforementioned variant. Here is the list of such alerts.
-
Registry Run Key Pointing to a Suspicious Folder
Conclusion
The advent of the Kapeka backdoor, also known as KnuckleTouch, demonstrates the increasing complexity of cyber threats, particularly in Eastern Europe, where geopolitical tensions have driven targeted assaults. Kapeka, discovered in mid-2022 and formally tracked in 2024, poses a serious challenge to cybersecurity specialists because of its affiliation with the Sandstorm Group, which is run by Russia's Military Unit 74455.
The attribution of Kapeka to the Sandworm gang emphasizes the group's history of disruptive cyber actions, notably against Ukraine, where important infrastructure has been regularly targeted. As cyber warfare continues to expand, and with impending elections in the coming years, its activities will undoubtedly increase, its possible targets must prioritize comprehensive security measures to prevent the risks presented by sophisticated attacks like Kapeka.
Kapeka's complex functionality, ranging from initialization and C2 communication to task execution and persistence methods, necessitates a complete detection and reaction strategy. Organizations may strengthen their defenses against Kapeka and other malicious programs by utilizing sophisticated threat intelligence, installing effective logging and monitoring solutions such as the Logpoint Converged SIEM platform, and conducting regular security reviews.
In a constantly changing threat landscape, proactive awareness and coordination among cybersecurity specialists are critical. Organizations may successfully manage Kapeka threats by being informed, sharing intelligence, and taking a proactive security attitude.