Fast Facts
-
Over the last seven years, there has been a noticeable increase in the sale and use of stealers’ malware, sold on underground forums ranging from $50 to USD 350 for a monthly subscription.
-
According to a report from any. run, loaders, stealers, and RATs (Remote Access Trojans) comprised the majority of samples uploaded to the platform in 2023.
-
Redline Stealer emerged as the most common malware, with detections more than twice as high as Remcos, the second most common.
Go To Section
Background
The term stealer or info stealer is self-explanatory. Stealers are trojans that collect and retrieve data from infected systems. It's evident that, as the name implies, they steal information. If we reflect on the trend from the previous year, there has been a notable rise in the use of the Stealer malware variant. A report from any. run highlights that in 2023, loaders, stealers, and RATs (Remote Access Trojans) were the most common uploaded malware types, with counts of 24,136, 18,290, and 17,431, respectively.
The graph below depicts the top 5 malware types from 2023
While stealer malware variants may employ diverse tactics, their ultimate objective is clear: to exfiltrate sensitive data from the victim machine. At its core, most stealer malware aims to capture “System/Host Information,” “Cookies,” “Saved Credentials,” “Email Clients data,” “VPN Credentials,” “Browser Cache,” “Cryptocurrency Wallets,” “Browser History,” “Saved Credit Cards.”
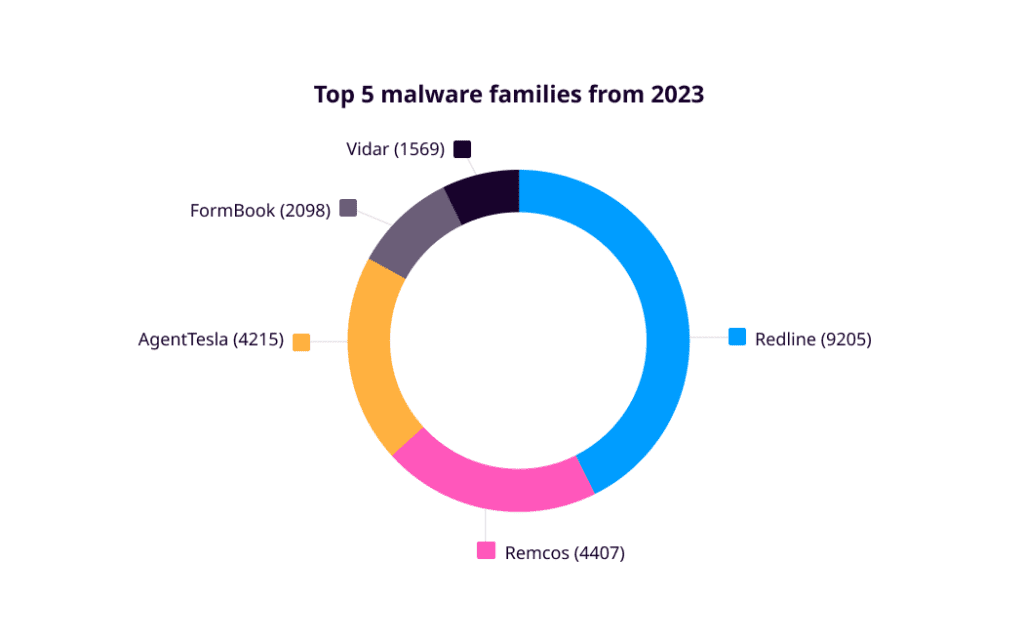
The graph below depicts the top 5 Stealer malware families from 2023 that operate as Malware as a Service.
We have created a comprehensive report covering an analysis of the top five stealer malware families observed in 2023: Redline, Remcos, AgentTesla, Formbook, and Vidar. These analyses serve as reference points for identifying patterns and understanding common behavior. Additionally, the report delves into the delivery mechanisms employed by threat actors to distribute this malware into victim environments.
Please check the report for more information regarding stealer malware behavioral patterns, detection, and remediation with Logpoint’s Converged SIEM platform.