When it comes to cybersecurity, your organization is never too safe. However, adversaries will always look for the path of the least resistance and that’s why companies invest in security operations platforms and good practices, such as penetration testing through hackers as a service.
Unfortunately, not all businesses can afford all the tools at their disposal, especially small and mid-sized businesses (SMBs). According to McKinsey, there is an increasing number of attacks on smaller companies, and malware, including ransomware, can threaten small and midsize businesses (SMB) in a way it often doesn’t to large enterprises, as many times these smaller companies can’t afford paying the ransoms.
The truth is that economic means can be an obstacle for SMBs to reinforce their security, and in many cases, they end up cutting back on tools. But, with the proliferation of EDRs, many have seen the answers to their prayers in these solutions.
And now what happens with SIEM technology – is it time to retire it?
When to choose EDR or SIEM
Trying to compare an EDR solution with SIEM is like comparing apples and oranges. They both serve different purposes. From the security perspective, an EDR is designed to monitor and secure endpoints while SIEM focuses on collecting, storing, and analyzing data from many different log sources, including endpoint systems for threat detection, investigation, and response.
The second aspect to consider is the obligatory nature of log storage. Collecting and storing logs is not a choice but a requirement for compliance reasons, such as NIS2, GDPR, and HIPAA. So, whether a company chooses to have an EDR or not, it still needs some sort of log management tool.
Rather than focusing on the difference between SIEM and EDR, we need to look at how each of them performs against attacks.
How an EDR behaves against a threat
EDRs scan for various kinds of indicators of compromise and look for files that might potentially be viruses and malware. They can scrape a lot of data from the system and perform actions on the machine, such as running a script to remove a file or isolating the machine from the network.
The reason why an EDR is not enough and cannot be a direct substitute for the SIEM, especially against more sophisticated threats, such as APTs (Advanced Persistence Threats) is that like others they try to compromise somewhere in the system that has a connection to the internet – and those endpoints usually have a lower security.
But compromising the endpoint is not enough. APTs try to infiltrate deeper into the system, for example trying to get to the active Domain Controller, through lateral movement. This way they can create persistence in the network and approach other parts of it.
Hopefully, the EDR remediates the threat, but because the adversary focuses on creating all sorts of backdoors for its persistence, organizations sometimes can’t ever get rid of it. So eventually, analysts have no way of tracking its lateral movement through the network, only on the individual endpoints.
SIEM, as the only source of truth for remediation
Once compromised, all SOC teams start the incident response phase to remediate the cyberattack as well as reverse the damage that the APT might have inflicted. To do this, analysts try to track the digital footprint of what this threat has touched and might have persisted, or in other words, perform forensic analysis – and here is where a good log source comes in handy.
When it comes to APTs, it’s highly difficult to know if the threat has been remediated. Firstly, because attackers will always try to disable EDRs, so one can’t be really sure that the EDR records haven’t been manipulated.
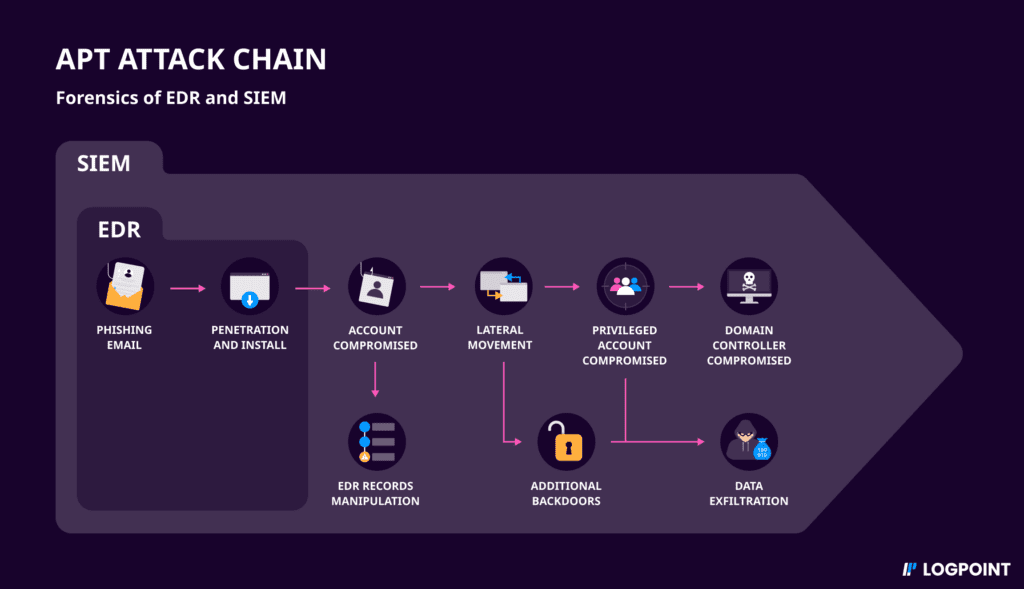
However, companies with a good logging system can use all data available in the SIEM for forensics to investigate what actually happened and then move forward with remediation. Whereas companies without a SIEM can’t be certain if the remediation is complete or be sure if they have removed the APT for good.
If the SIEM is well configured, it becomes a comprehensive log of what has happened in the system and includes traces of the threat’s lateral movement, which can be used for further remediation. Without those records, remediation becomes an infinite problem as analysts have to manually go through the whole network. At the same time, most SIEMs come with automated response features, facilitating the task at hand.
Normalization and orchestration: The Logpoint approach
For these reasons, many SMBs might consider that an open-source EDR and some sort of log management solution can be the answer to their problems, both in terms of security and budget, but nothing could be further from the truth.
To start with, they will have to spend a lot of time and resources to make it work and maintain the integration increasing the actual total cost of ownership. The reason is they will have to make the integration themselves between the EDR and their SIEM, as well as with other vendors if their main goal is to achieve full TDIR.
In addition, it’s useless to have a box with records for forensic analysis if analysts can’t get the data out of it or make sense of the raw database. This is not the case with Logpoint’s Converged SIEM, in which the data is normalized into a common taxonomy easing the creation of dashboards and alerts.
Eventually, any log management solution might not be enough when trying to improve the security posture because it lacks integrations with data sources on threat intelligence, compliance packages, and automated response that makes the SIEM easier to operate.
Cyber Defense: An end-to-end platform with SIEM and an endpoint sensor
At Logpoint we understand that EDR and SIEM are not mutually exclusive technologies. Our approach is to provide the midmarket with a platform that includes the best of both worlds.
With the Logpoint Cyber Defense platform, companies get a full SIEM solution that allows them to perform log collection, storage, and analysis for both compliance and forensics. And on top of that, the SIEM is built on an end-to-end security operations platform that comes with Logpoint Automation, to automate processes such as investigation and response, and a native endpoint sensor, called AgentX, which allows them to reach more endpoints and assess their vulnerabilities. On top of that, customers get access to Case Management, to handle all the security incidents and perform in-depth investigations, and Behavior Analytics, an ML-based solution to detect abnormal behavior in the network.
In combination with Logpoint SIEM and Automation, AgentX brings out-of-the-box endpoint observability and the ability to run playbooks for investigation and response over incidents on endpoints. Because the endpoint sensor is natively integrated, there is no need to extrapolate the threat information generated to understand what areas the threat has impacted.
AgentX come with the Logpoint SIEM license, which is based on the number of nodes or users. You can complement it with Logpoint Automation to get investigation and response, or get the full meal with all add-ons with Logpoint Cyber Defense Platform. For SMBs with a limited budget for portfolio products, this is the perfect option as they can maintain a strong security posture at a predictable cost.







