Sometimes different tools can have overlapping functionalities/capabilities, which may prove to be confusing to decision-makers. In this short blog post, I try to shed some light on the differences between a Security Information and Event Management (SIEM) and Endpoint Detection and Response (EDR) tool.
Sometimes different cybersecurity tools have overlapping functionalities and capabilities, confusing decision-makers. In this blog post, we lay out the differences between a Security Information and Event Management (SIEM) and an Endpoint Detection and Response (EDR) tool.
What is an EDR solution?
Traditionally, foundational cybersecurity software offers protection through signature-based tools or a SIEM. An EDR (Endpoint Detection and Response) is a SIEM-complementary software used to expand detection and response capacity.
An ‘endpoint’ is any device that is physically an end point on a network. They could be on-premise or remote devices. As they provide entry to an organization’s assets or applications, ‘endpoint’ security is important.
In particular, an EDR determines if malware has been installed on an endpoint device and finds ways to respond to this kind of threat. Once installed, EDR solutions use agents installed on an endpoint to collect data from many different kinds of data sources directly on the endpoint and stores it in a central database.
This data typically comes from the following sources:
- ARP
- DNS
- Sockets
- Registry
- Memory dumps
- System calls
- IP addresses
- Hardware types
Once an EDR solution locates a hacking attempt or a malicious infiltration, it will immediately provide a list of recommended responses.
All EDR’s provide dashboards or reports, and data analysis is performed. EDR solutions currently support Windows OS and are beginning to support other platforms such as Linux, Unix, iOS, or Android.
What is a SIEM solution?
A SIEM (security information and event management solution) is a central risk management tool for threat detection, investigation and response.
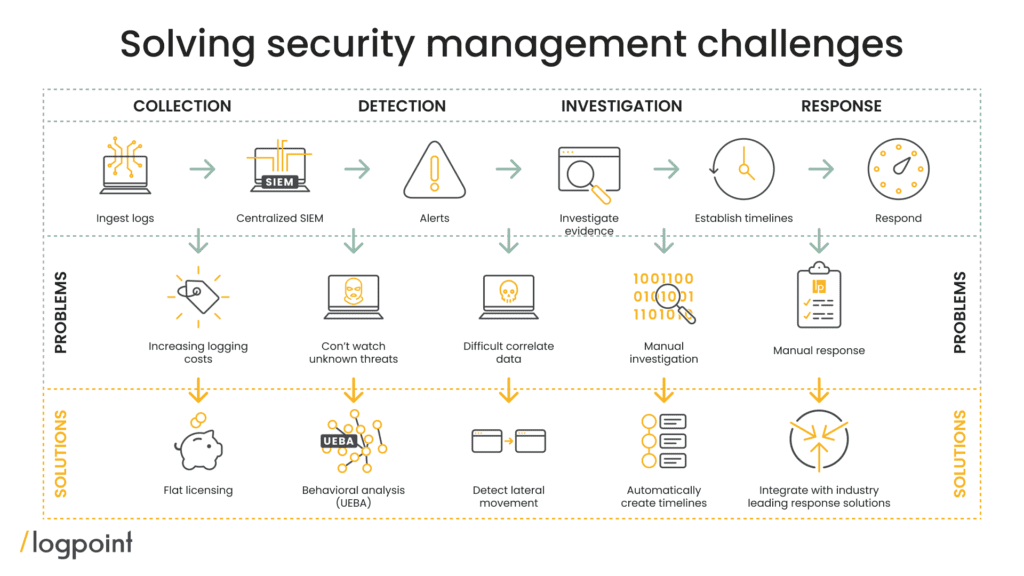
A SIEM is used to provide a single central location for storing and analyzing data, coming from many different log sources – and is not limited to endpoint systems. In this way, SIEM provide the means of connecting previously distinct information silos to collect data and analyze data in real-time, detect data breaches, store data and report – providing easy to understand, product-agnostic insight to enable appropriate actions and responses.
As all institutions complete their digitization journeys, data is now central to all business models. Data and the ability to visualize it, are inherently valuable. That value increases dramatically when put into context. When enriched with information about users, assets, threats and vulnerabilities, this data becomes actionable and the SIEM supporting this increases ROI.
With a SIEM it is possible to understand many different use-cases and connect to many types of systems accessing different log sources, such as: firewalls, servers, IPS, proxies, etc. As a SIEM supports a multitude of different platforms, it can be used for advanced correlation, log management, and forensics.
Additionally, with Logpoint SIEM, there is no limit when it comes to use cases. Logpoint is capable of managing different areas like IT-Operations, IT-Security, Compliance and Business Analytics.
Logpoint SIEM does much more than traditional SIEM software.
Our SIEM solution efficiently gathers, investigates and makes a record of event data produced by any device or application within your infrastructure, giving you the insight necessary to define the scope of the threat and make critical decisions.
The answer to the question about whether to choose a SIEM or an EDR is not an easy one. There are many factors that go beyond the cybersecurity budget, such as the analysts know-how to operate them properly and the use cases the security team wants to achieve. Eventually, the use cases should determine what tool is the best fit for a company.
What are the differences between SIEM and EDR?
A SIEM can be used to collect data from many different types of data sources and do advanced correlation, log management or forensics. This data may be generated by applications, databases, infrastructure, sensitive assets, manufacturing systems or security systems. There is no limit regarding supported platforms or the type of use case.
An EDR helps investigate, uncover, prioritize and remediate complex attacks, specifically and only, utilizing end-point data.
| Key features of SIEM | Key features of EDR |
|---|---|
| Focus on network-wide security monitoring, log management, and threat correlation | Focus on endpoint security, threat detection, and response |
| Various data sources, such as network devices, servers, applications, or security tools | Data sources from endpoints, such as laptops, desktops or servers |
| Broad visibility over networks and threat landscape | Visibility over endpoints |
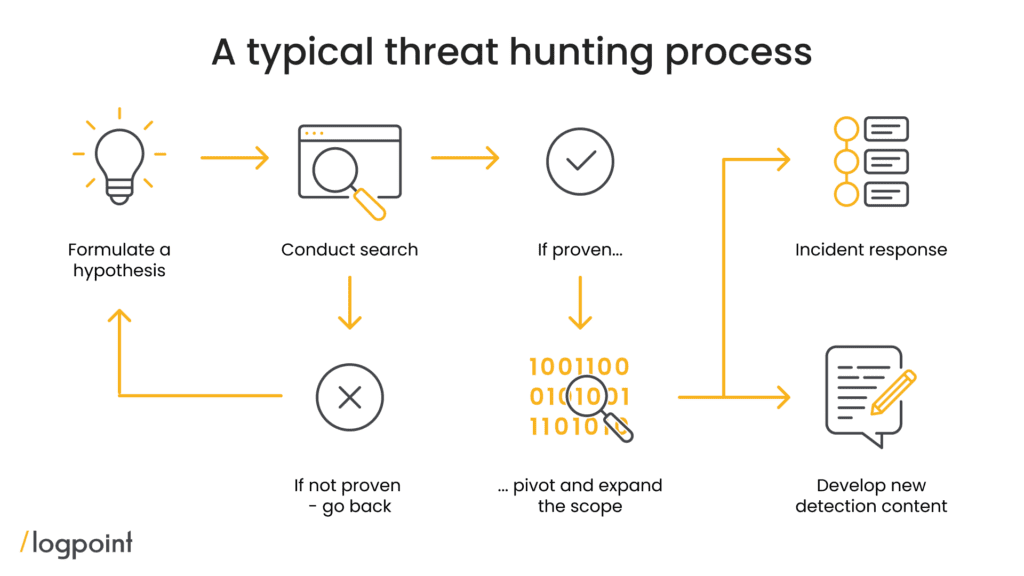
| It correlates events to identify potential threats | It performs threat hunting, behavioral analysis |
| High data volume | Lower data volume |
| It detects threats across the network by correlating events | It focuses on endpoint-based threats, e.g. malware and ransomware |
| Broad compliance capabilities due to log retention and reporting , and it can include pre-configured compliance packages, | Limited compliance capabilities |
| Detection of threats through correlation of events and it provides context for incident investigation | Proactive detection of endpoint-based threats and rapid investigation and response of incidents on endpoints |
The Logpoint approach to SIEM vs. EDR
Both SIEM and EDR are complementary and comparing them is like comparing apples and oranges. To make it easier for analyst and security teams, Logpoint SIEM comes with AgentX, an endpoint sensor that ships logs and telemetry data from various endpoints, including servers, workstations and applications, to the SIEM. Analysts can interrogate endpoints and perform automated investigation and response actions to incidents in them.
Recommendations
To achieve a multilayer and more effective defense system, it is advantageous to combine these two tools: utilizing the power of Logpoint’s SIEM collecting data from many different types of log sources and adding an EDR for individual network focus.
As an EDR works only with end-point data, it is essential to consider SIEM as foundational and an EDR as a complimentary addition. Structurally, a SIEM then utilizes an EDR as another log source providing valuable information.