By Martha Chrisander, Head of Product Marketing, LogPoint
Data breaches are expensive. IBM estimates that the average total cost of a data breach is $3.86 million, including expenses related to detecting the breach, business disruption, communication about the attack and post-breach response. Not to forget the costs associated with the amount of time the attackers breached the system and the amount of data leaked. On average, security teams take 280 days to identify and contain a breach. With 52% of breaches caused by malicious attacks, you could have a malicious actor with access to your sensitive data for almost a year.
Organizations that have nascent security automation and incident response processes often have much higher costs from security breaches. To help mitigate costs and exfiltration of your data, you need to speed up threat detection and response through automation. LogPoint is a security information and event management (SIEM) solution that detects, analyzes and responds to threats within your data for faster security investigations. LogPoint helps you prioritize incidents so you can focus on what’s important and get situational awareness.
Automate response to solve incidents quickly
LogPoint’s integration with Cortex XSOAR combines security monitoring and automated incident response so analysts can solve incidents fast. The out-of-box solution automates coordinated actions and responses to help analysts save time resolving incidents.
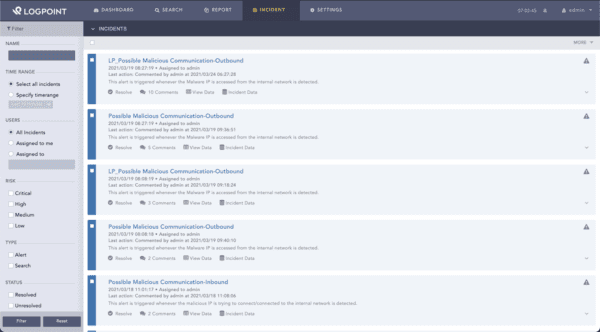
Analysts can explore incidents and see alerts based on risk level, helping them focus on the most critical incidents.
The LogPoint integration, available in the Cortex XSOAR Marketplace, helps analysts know which alerts to focus on by fetching incidents and information from LogPoint. Analysts can take the next step and respond to incidents using data from the XSOAR playbook. The integration includes sample playbooks, which analysts can customize to meet their specific needs. Analysts get complete control over incidents with the ability to update, resolve, close, and delete incidents.
Benefits of the LogPoint Cortex XSOAR integration:
- Real-time threat indications ensure that your SOC will find breaches before the 280-day average.
- Comprehensive understanding of the threat landscape with built-in incident prioritization.
- Reduce mean time to respond with incident mapping.
- Easily create unique playbooks for specific needs with a sample playbook.
Use case: Investigating failed login attempts
More than 80% of data breaches within hacking involve brute force or the use of lost or stolen credentials. One way to detect credential misuse is by investigating failed login attempts. In the case of a brute force attack, hackers trying to get access to your system will check all possible passwords until they find the correct one, resulting in an abnormally high number of failed logins.
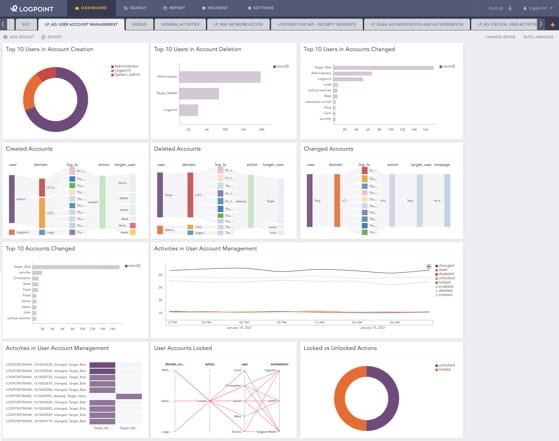
In LogPoint, analysts can get an overview of all user account activity, including failed login attempts.
It’s easy to quickly detect and respond using the LogPoint integration with Cortex XSOAR. LogPoint regularly checks for failed login attempts by Active Directory (AD) users. When there is a failed login attempt, LogPoint triggers an alert. When someone reaches a pre-defined threshold of failed attempts, let’s say 10 failed login attempts, LogPoint creates an incident.
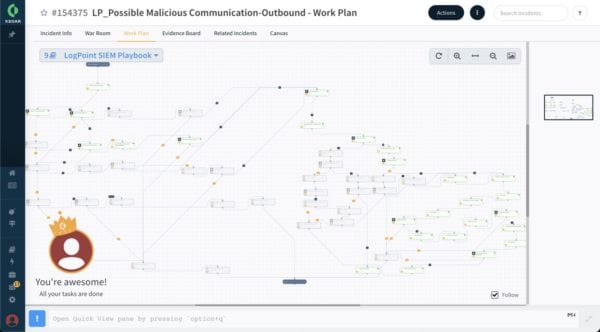
Cortex XSOAR playbooks trigger based on alerts from LogPoint, automating incident response.
Cortex XSOAR pulls incidents from LogPoint every minute, and the associated playbook triggers automatically. The playbook automatically resets the user’s password and notifies the user via email. The automatic response quickly thwarts the attacker’s attempt to gain access to your system.






