Cybersicherheit für Bildungseinrichtungen
Sicherheitsverstöße an Universitäten und Hochschulen haben in den letzten Jahren drastisch zugenommen. Die offene Struktur der Campus-IT-Systeme und das wertvolle geistige Eigentum in diesen Einrichtungen haben sie zu einem verlockenden Ziel für böswillige Angriffe gemacht. Universitäten und Hochschulen sind anfällig für Hacker-Attacken, Malware-Angriffe, Phishing-E-Mails, DDoS-Angriffe und absichtliches oder zufälliges Hacking durch Studierende.
Laden Sie unser Solution Brief herunter, um mehr über die Herausforderungen der Cybersicherheit im Bildungswesen zu erfahren und darüber, wie Logpoint SIEM- und UEBA-Lösungen zu deren Bekämpfung beitragen können:

Logpoint für die Universität von Bedfordshire
Mit Logpoint hat das IT-Team der University of Bedfordshire eine Lösung gefunden:
- die Verwaltung von Netzwerk-Alarmen zu vereinfachen
- besser Vorfälle zu identifizieren, die Maßnahmen erfordern
- Einsparungen bei den Betriebskosten zu erzielen
Durch die Umsetzung von Daten in verwertbare Informationen und die Verbesserung der Cybersicherheit hat Logpoint die zeitaufwändigen Analysen von Sicherheitsprotokollen verkürzt und gleichzeitig den Großteil der Fehlalarme eliminiert.

Sicherung sensibler personenbezogener Daten und moderner Forschung
Hochschulen und Universitäten speichern große Mengen personenbezogener Daten der aktuell Studierenden, der Fachbereiche, von Bewerbern, Verwaltungspersonal, Absolventen, Mitarbeitern, Forschungs- und Projektteilnehmern, Lieferanten und anderen Akteuren. Darüber hinaus speichern diese IT-Systeme modernste Forschungsdaten und wertvolles geistiges Eigentum. Leider fehlen den Bildungseinrichtungen, insbesondere den öffentlichen, oft die finanziellen und personellen Mittel, die für einen umfassenden Datensicherheitsplan erforderlich sind, was eine erhebliche Gefahr für die Geschäftsziele der Institutionen bedeutet.
Mit Logpoint können Hochschuleinrichtungen durch Machine Learning beschleunigte Advanced Analytics nutzen, um ihre Cybersicherheitslage zu verbessern und die entsprechenden Reaktionen auf interne wie externe Bedrohungen effizient zu automatisieren.
Bedrohungen
Wenn es um Verstöße in Bildungseinrichtungen geht, kommen viele potentielle Akteure in Frage. Gezielte Angriffe sind vielleicht keine Überraschung, sie sollten aber auch die Studierenden selbst nicht außer Acht lassen, die manchmal, aus Langeweile oder Neugierde, zum Auslöser eines Vorfalls oder Verstoßes werden. Doch egal, ob absichtlich oder unbeabsichtigt gehackt wird – Sie müssen Schutzmaßnahmen einführen, um Sicherheitsvorfälle generell zu verhindern.
Umgang mit besonderen Insider-Bedrohungen
Es gibt viele potentielle Bedrohungsakteure, wenn es um Verstöße im Bildungsbereich geht: Studenten, Dozenten, Bewerber, Verwaltungsangestellte, Alumni, Mitarbeiter, Forschungs- und Projektteilnehmer und Anbieter, die Zugang zum relativ offenen akademischen Arbeitsumfeld haben.
Eine Gruppe von besonderem Interesse sind jedoch die Studierenden. Jung, energisch und vielleicht tagsüber an einem Kurs über ethisches Hacking teilnehmend, könnten sie versucht sein, neu erworbene Fähigkeiten während der Nacht zu testen.
Es mag aus Langeweile oder Neugierde geschehen, dass die Studenten als Verursacher eines Bruchs enden. Ob absichtlich oder versehentlich, Universitäten brauchen Schutzmaßnahmen, um der Bedrohung durch Insider begegnen zu können.
Solution Brief herunterladen Laden Sie unser Solution Brief herunter, um mehr über die Herausforderungen der Cybersicherheit im Bildungswesen zu erfahren und darüber, wie Logpoint SIEM- und UEBA-Lösungen zu deren Bekämpfung beitragen können.
Monitoring der Benutzeraktivität
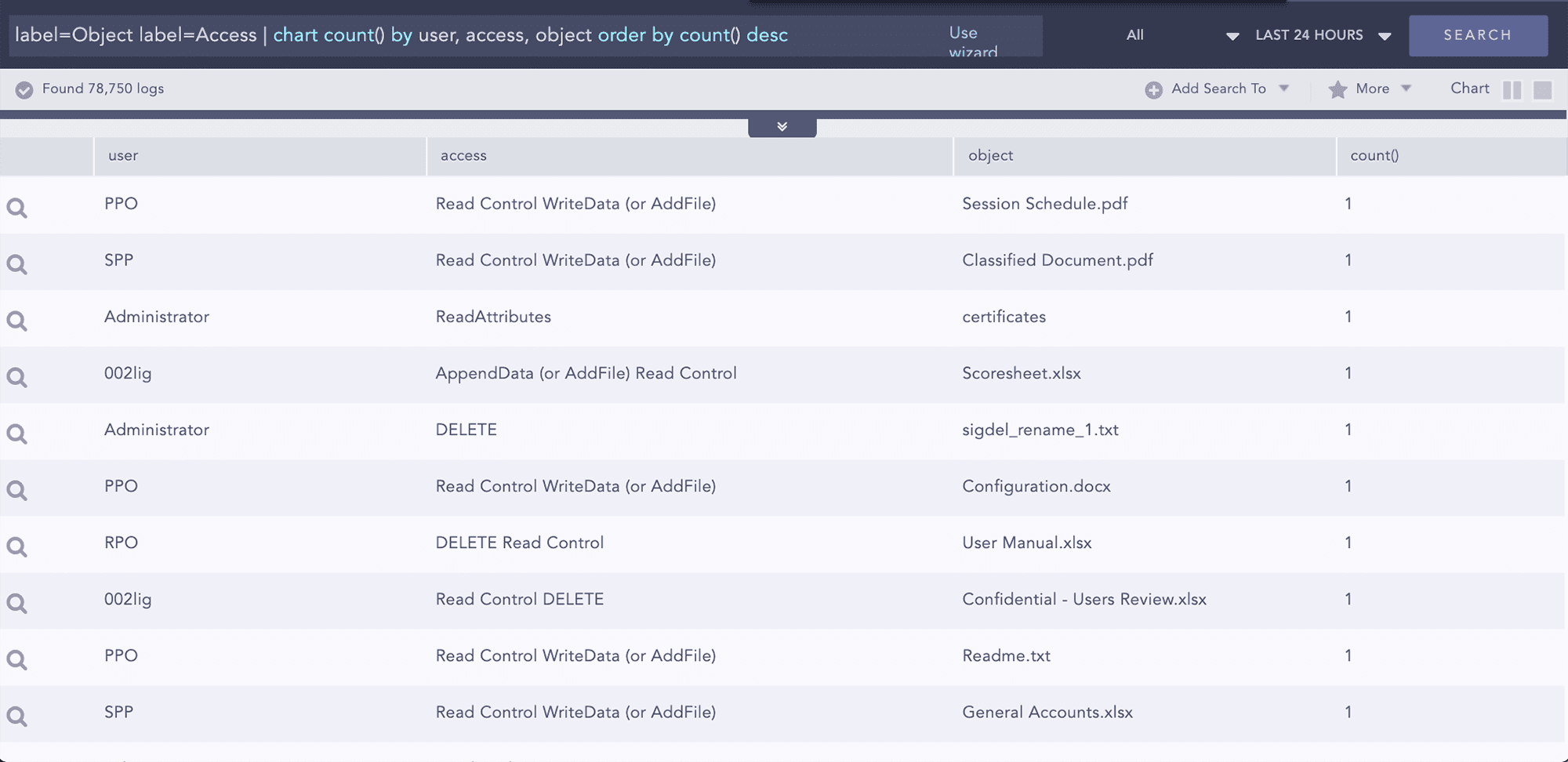
Die Überwachung der Benutzeraktivität ist seit langem der Eckpfeiler einer effizienten Verteidigungsstrategie. Logpoint ist darauf ausgelegt, Analysten ein intuitives und leistungsstarkes Tool bereitzustellen, mit dem sie böswillige Aktivitäten aufdecken und Warnungen, Dashboards und Berichte erstellen können – um sich so sofort einen Überblick verschaffen und Gegenmaßnahmen ergreifen zu können. In erster Linie aus Gründen des Datenschutzes und wegen den Vorschriften konzentriert sich das Monitoring der Benutzeraktivitäten auf Aktivitäten im Zusammenhang mit Zugriff auf Daten. Logpoint kann dies mithilfe nativer Auditaufzeichnungen über den Zugriff auf die Objektdaten überwachen. Darüber hinaus kontrolliert die FIM-Anwendung von Logpoint alle Zugriffsversuche auf privilegierte Dateifreigabesysteme und bietet Informationen zur Art des Zugriffs und zu den in der Datei ausgeführten Aktionen. Darüber hinaus können die ursprüngliche und die geänderte Prüfsumme verglichen werden, um das Zugriffsverhalten besser zu verstehen.
Erweiterte Analysekorrelation und Mustererkennung
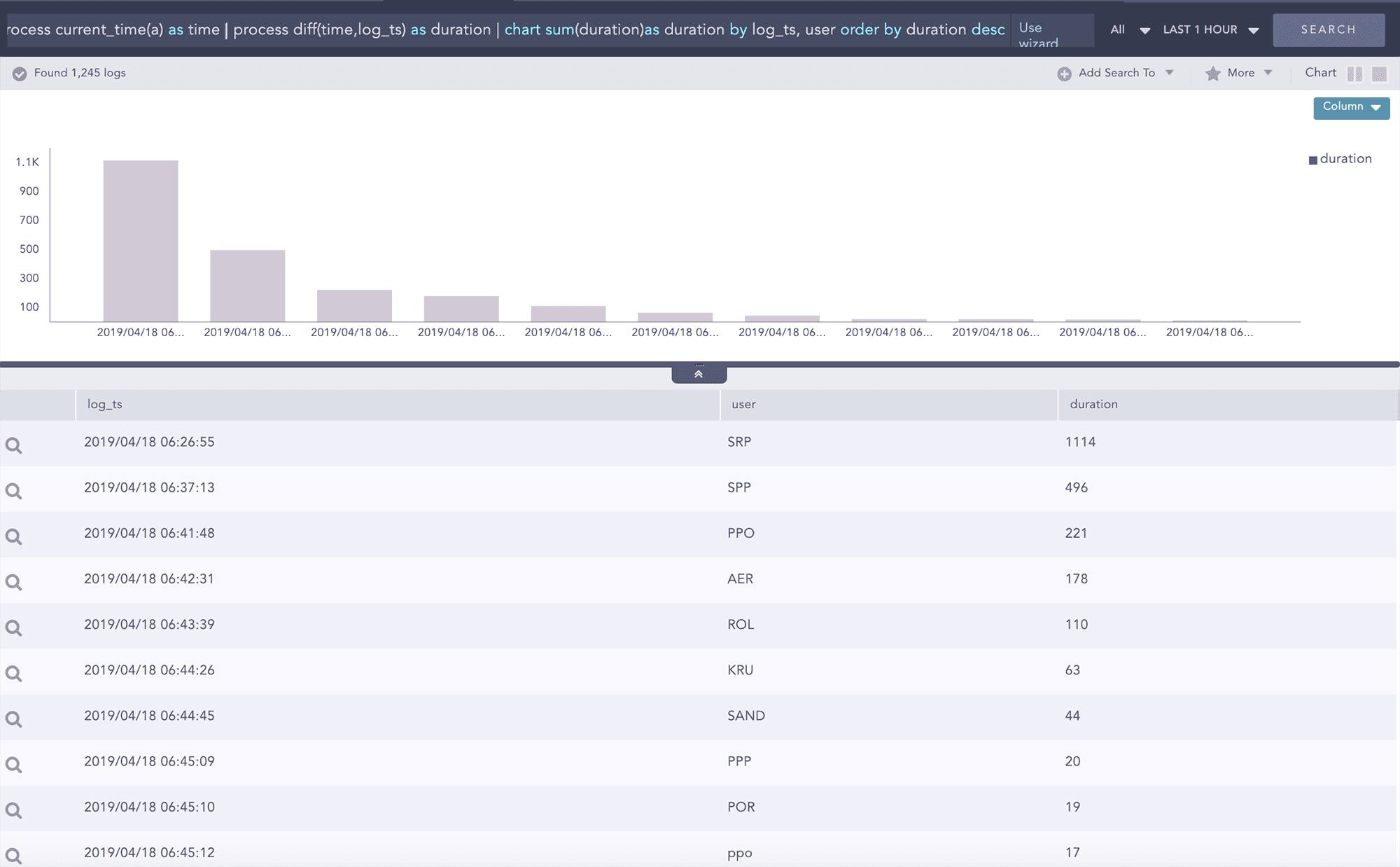
Standardmäßig kann Logpoint eine erweiterte Korrelation für eine beliebige Anzahl an Datenquellen durchführen – intern, extern oder strukturiert. Unabhängig davon, ob es sich um eine Anhäufung zwischen zwei oder mehr Gruppen von Entitäten, wie Benutzer- und Quelladresse für fehlgeschlagene Anmeldungen, handelt oder um das Kombinieren von Datensätzen in mehreren Protokollmeldungen über mehrere Datenquellen hinweg mithilfe von Join und anschließenden Abfragen, stellen wir Ihnen Warnungen zu riskantem Verhalten und abnormen Aktivitäten in Echtzeit bereit.
In Logpoint können dynamische Listen darüber hinaus verwendet werden, um erweiterte Korrelationen auf verschiedene Arten durchzuführen, z. B. um eine dynamische Liste mit IP-Adressen oder Hostnamen für anfällige Arbeitsstationen zu erstellen, um so jede mögliche Ausnutzung der Sicherheitsanfälligkeit durch die Bedrohungsquelle zu identifizieren.
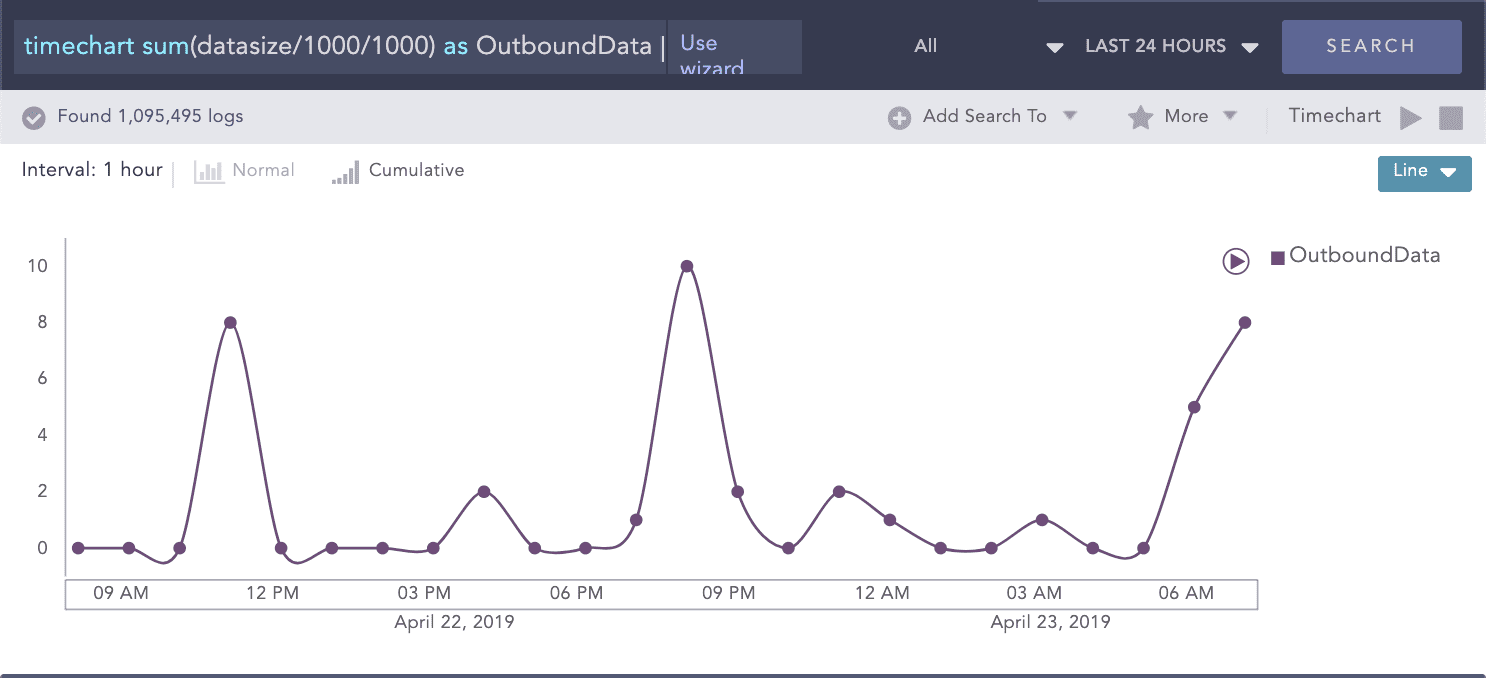
Erkennen von Datenbereitstellung und Exfiltration
Kompromittierte Konten oder Computer versuchen im Normalfall, Daten in Bereitstellungsbereiche zu verschieben, von denen aus sie leicht aus dem Netzwerk des Unternehmens entfernt werden können. Während der Vorbereitung der Daten zum Entfernen verwenden Angreifer Tools wie PSExec, oder Remote-Desktop-Tools. In diesem Fall erkennt und hebt Logpoint UEBA eine anomale Bereitstellung sowie laterale Bewegungen hervor, einschließlich (der äußerst ungewöhnlichen) Datenübertragungen innerhalb der Workstation mit hohem Datenvolumen, außerordentliche Protokoll-/Portkombinationen und unüblich hohen Datenzugriffsmengen.