SOX or The Sarbanes-Oxley Act (SOX) was passed in 2002 in the USA and requires that all publicly traded companies implement and affirm a framework of internal controls supporting accountability and integrity of the financial reporting process. In practice, this means that as an effort to “protect shareholders and the general public from accounting errors and fraudulent practices in enterprises, and to improve the accuracy of corporate disclosures.”(Source: Digital Guardian: What is SOX Compliance? 2019 SOX Requirements & More, Juliana De Groot).
Organizations must be able to present where sensitive data is stored, how it is stored, and who has access to it. As keeping track of your sensitive data and regulating access to your network and systems is the cornerstone of SOX compliance, having a SIEM to gather, analyze and visualize this information for you makes compliance more effortless and efficient than ever.

Table of Contents
Who must comply with SOX?
SOX compliance requirements extend primarily to publicly traded U.S. companies and foreign companies operating in the U.S., with eleven provisions governing their internal controls, auditing, and reporting practices. These measures aim to ensure reliability and transparency in financial statements, instilling trust in American markets and attracting investors while reducing financial fraud. However, SOX guidelines also encompass privately held companies, nonprofits, and accounting firms. Privately held companies and nonprofits must adhere to regulations prohibiting the destruction or falsification of financial documents and cooperate with federal investigations related to financial reporting. Audit firms, on the other hand, must maintain compliance with the Public Company Accounting Oversight Board (PCAOB), fulfilling requirements such as ongoing education on accounting ethics, standards, and the impact of SOX provisions.
The upsides of SOX Compliance:
SOX compliance offers multiple advantages for organizations:
-
- One of the key benefits is the ability to identify and strengthen internal controls. Similar to SOC 2 compliance, SOX provides a baseline understanding of the necessary standards to safeguard data and protect the business.
- Another advantage is the facilitation of reliable and efficient audits. With executive teams being held accountable and internal audit teams having specific responsibilities under SOX, audits become more streamlined, benefiting both internal and external audit processes.
- SOX compliance also primes processes for growth. By establishing early documentation processes for audits, companies can enhance efficiency not only in auditing but also in various other areas. This includes prioritizing high-risk aspects, implementing appropriate controls, integrating IT systems, and fostering collaboration across departments. Building secure and financially healthy processes from the outset allows organizations to minimize auditing costs while maximizing their financial growth potential.
The downsides of SOX Compliance:
SOX compliance comes with certain challenges and considerations:
-
- Establishing new internal controls can be a burdensome task. This involves constructing processes for financial information, ensuring the accuracy of reports, and implementing new controls to meet the criteria set by SOX.
- Compliance efforts may require hiring additional employees and contractors. Conducting compliance reviews of IT processes, introducing new procedures, and managing them, in the long run, may necessitate the recruitment of new personnel.
- Increased audits are a result of SOX compliance. While these audits enhance accounting objectivity, they also contribute to higher costs for organizations.
- The potential for more penalties is another aspect to consider. Failure to comply with the requirements of signing or publishing financial statements, along with the heightened penalties for fraudulent activities, can make executives and private organizations cautious about assuming accountability.
- Compliance with SOX introduces more regulations and requirements, leading to higher accounting costs. It also diverts resources from primary business functions to the demands of financial reporting.
SOX Compliance Requirements:
At a high level, SOX compliance requirements involve a four-step process:
- Providing audited financial statements to the SEC by a third party.
- Reporting material changes to the public.
- Designing, implementing, and testing internal controls.
- Composing an annual statement on internal controls, signed by management and audited by a third party.
Internal Controls Requirements:
Within the realm of IT, SOX compliance necessitates the management of internal controls in a digital environment, focusing on:
- Access control
- Security and cybersecurity
- Segregation of duties
- Change management
- Backup systems
To address these areas, various frameworks are available, including COSO, COBIT, NIST, and ISO 27001. These frameworks enable companies to link business and IT goals, establish controls, assign responsibilities, and measure performance, thereby facilitating SOX compliance.
SOX Compliance and Logpoint
Monitoring of critical systems
Critical systems containing sensitive information should be constantly monitored to detect any suspicious activity. Logpoint supports dynamic lists and tables, ensuring constant risk assessment. In Logpoint, dynamic lists collect and store specific values from events and allow for dynamic updates using values from log messages, while dynamic tables store specified fields and field values during runtime to be used as enrichment sources. By enabling analysts to define dynamic lists and tables, organizations can reduce the time to detect and respond to incidents faster. By combining dynamic lists with static enrichment, we also empower our customers to build self-configuring analytics to automatically react to new observations on the data, thus accelerating response.
Example: Un-privileged connections to critical systems
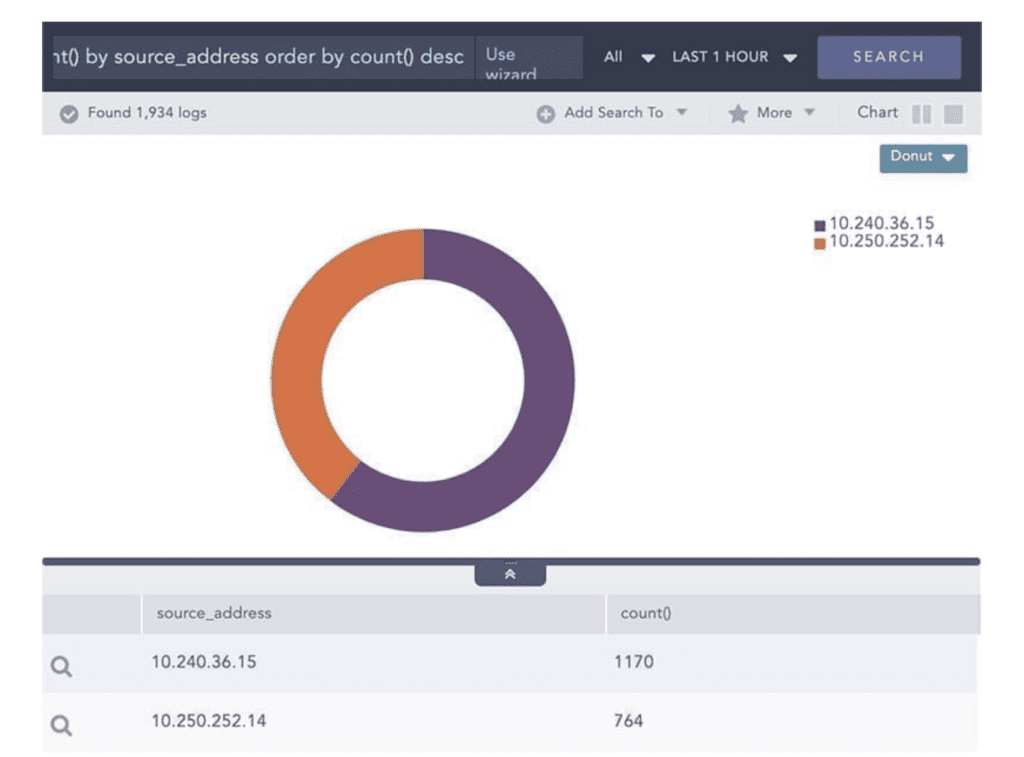
Ensuring network security
Network security ensures that the CIA triad for network infrastructure and related data is fulfilled. The three components of the triad are Confidentiality, Integrity, and Availability. Confidentiality ensures that your network is not being accessed by unauthorized users or from unauthorized networks. Integrity guarantees that files or data either in rest or motion are protected from unauthorized modification. Availability guarantees that the system and network are up and running whenever needed.
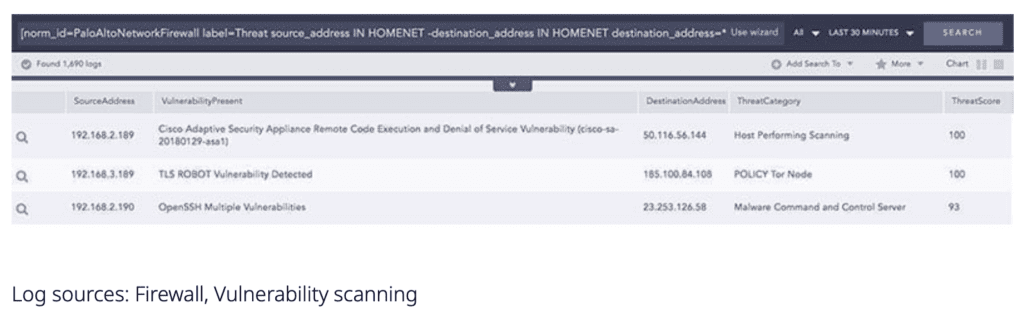
Logpoint integrates with a wide range of network and firewall devices. The data from these devices can be normalized, aggregated, enriched, and correlated to ensure security inside the network. Furthermore, Threat Intelligence feeds can be used to enrich the log data to understand if the network is being targeted by an external attacker. Logpoint can check various activities such as allowed and denied connections, usage of data and applications, connection to threat sources, or any other suspicious activities. Any asset, system, or device in a network activity when associated with multiple high-risk indicators, suggests that the network’s security posture is at risk. Logpoint can identify such threats through the use of join queries between the firewall and vulnerability scanning records. Also, the results matching this condition can be checked for association with an indicator of compromise. This activity can be simplified through the use of dynamic lists, where a list of vulnerable systems is constantly maintained, and an alert is fired every time a connection from an IOC is made to the values in the list.
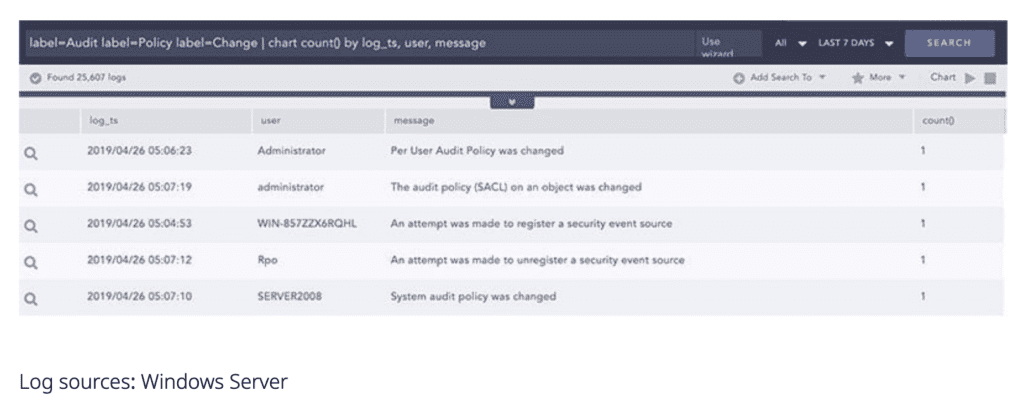
Policy monitoring
IT policies define what security-related guidelines employees should comply with in order to maintain the highest level of security. Any change to an organization’s IT policies is critical and therefore should be closely monitored. Logpoint can easily detect policy changes such as audit, authentication, authorization, filtering, and many more.
Role-based access control
Logpoint provides you with flexible yet powerful User and Account Management driven by a role-based access control mechanism where user access can be tied to AD via LDAP for a simplified user account creation. These users can then be assigned to Logpoint-specific groups. Group permissions to the system are aligned with a role-based approach to administrative rights, giving full control over access to the log repositories and the dashboard usage, operator rights for data and analytical purposes, and user account administration for managing users, groups, and permissions.
SOX compliance is crucial for publicly traded companies to ensure accountability and integrity in their financial reporting processes. Implementing a robust framework of internal controls is necessary, including the management of sensitive data, access regulation, network security, policy monitoring, and role-based access control. Logpoint offers a comprehensive solution for organizations, simplifying compliance efforts by providing monitoring capabilities for critical systems, ensuring network security through integration with network and firewall devices, detecting policy changes, and offering flexible user and account management based on role-based access control. By leveraging Logpoint's features, organizations can streamline their SOX compliance efforts and enhance their overall security posture, safeguarding their financial integrity and protecting shareholder interests.







