In the last 18 months, a staggering 98% of businesses have reported cloud breaches, highlighting the critical need to safeguard your systems against attacks. To support you in taking command of your cloud security and proactively addressing threats, we are delighted to present one of the first security solutions for the SAP Business Technology Platform on the market.
Your responsibility in cloud security
The “Shared Responsibility Model” is a framework that aims to secure every aspect of the cloud environment including hardware, infrastructure, endpoints, data, configurations, settings, operating system (OS), network controls, and access rights. The model also clarifies the security and compliance responsibilities between the cloud provider and the customer, dictating that the provider is responsible for overseeing security threats related to the cloud infrastructure while users and businesses bear the responsibility of safeguarding the data and assets stored in the cloud environment. Unfortunately, the concept of 'shared responsibility' is often misunderstood, leaving users vulnerable to attacks targeting operating systems, data, or applications.
Fortify Your Cloud Security with BCS for SAP Business Technology Platform
The importance of securing SAP BTP
As SAP BTP serves as a central entry point to the entire Cloud infrastructure, securing it against breaches is of utmost importance. A compromise could potentially grant hackers easy access to the entire Cloud infrastructure, and all applications and enable them to disrupt the integrations between the applications and the SAP BTP itself. Securing the platform is crucial for strengthening your security posture in the cloud.
Why BCS for SAP BTP?
Say goodbye to operating in the dark when securing your SAP BTP against attacks. Sit back and let our powerful threat detection and monitoring solution provide you with complete threat visibility, so your teams efficiently can respond to threats and proactively mitigate risks.
Elevate the security of your SAP BTP - proactively
If SAP BTP gets compromised, your entire cloud infrastructure could be at risk. Keeping it safe should be your highest priority. By closely monitoring security-related events in real-time, such as logins, user geography, timeframes, and changes to roles and configurations, we provide you with full threat visibility, empowering you to proactively mitigate threats and keep attacks at bay.
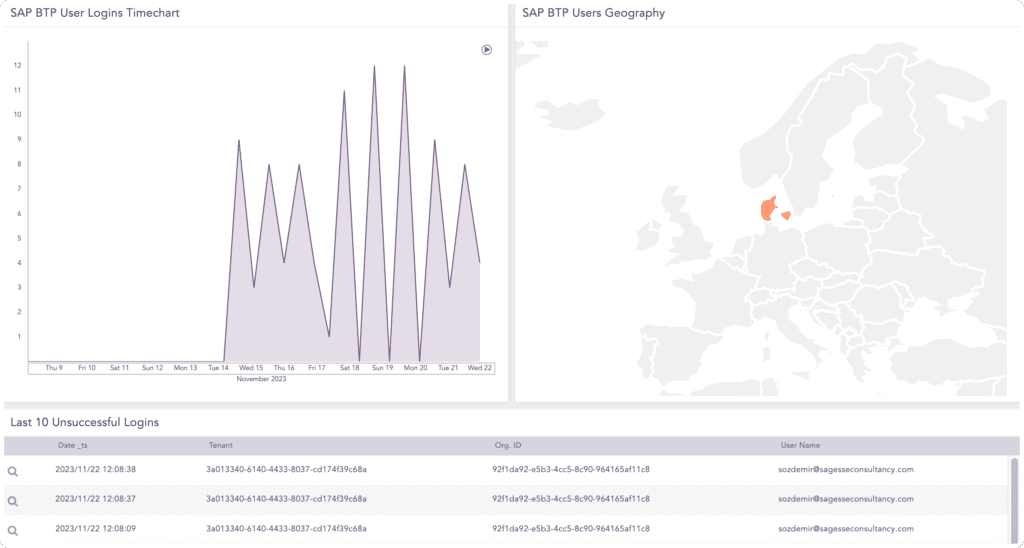
Boost your security posture - effectively
Automate the monitoring of security logs to maximize efficiency. Save time, and resources and alleviate alert fatigue by leveraging our intuitive dashboards, which offer a contextualized and prioritized overview of security incidents. This allows you to promptly take action and effectively mitigate threats putting your applications at risk.
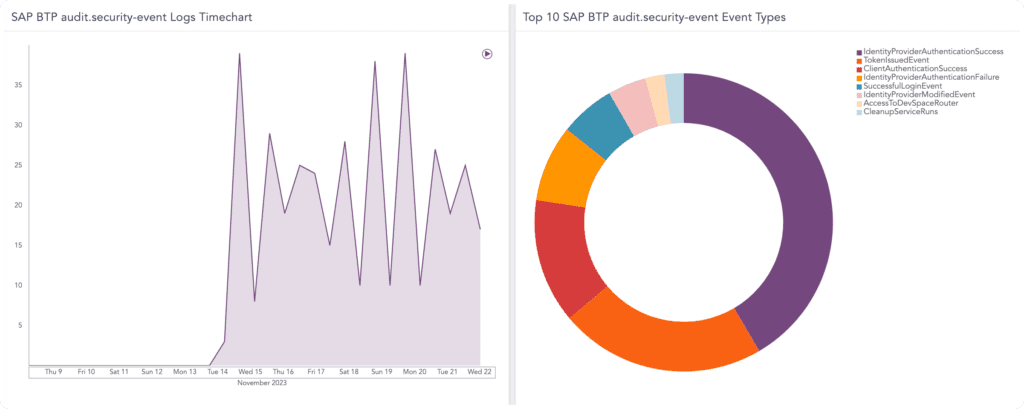
To see more info on how to protect your SAP Business Technology Platform click the button below.







