Nowadays not a day goes by without a cyberattack. In 2022, organizations worldwide detected nearly 500 million ransomware attacks. Security vendors are aware of the ever-increasing number of threats, and with more investments in cybersecurity, their solutions to this problem shouldn’t be limited to just automation to deal with alert fatigue.
Instead, they should focus on enabling SOC teams through the implementation of practical features that can help them, regardless of whether they have plenty of resources or are a team of one’s own.
This has been the focus throughout the last quarter, where we put out efforts in releasing updates to our Converged SIEM platform that are both practical and SOC-centered.
We achieved this by connecting detection with the investigation, automation, response, and orchestration, continuing to break down silos.
The goal is to map our development with some of Converged SIEM’s best qualities: Ease of use and end-to-end functionality. And we did exactly that this quarter, so when analysts come back from their well-deserved vacations, they have the updated tools to increase the organization’s security posture.
More contextual data for better investigation with Cases
Investigation is a cornerstone of the incident response process, and perhaps equally – if not more – important than detection and response. And for us, facilitating context during incident investigations has been a priority during the latest release of SOAR.
To ensure that security analysts can put all the pieces together, we included two upgrades to our case manager that will provide them with all the information they need at their fingertips. Incidents are now mapped to the MITRE ATT&CK framework, and users can see a graphical overview of the connection between all the artifacts.
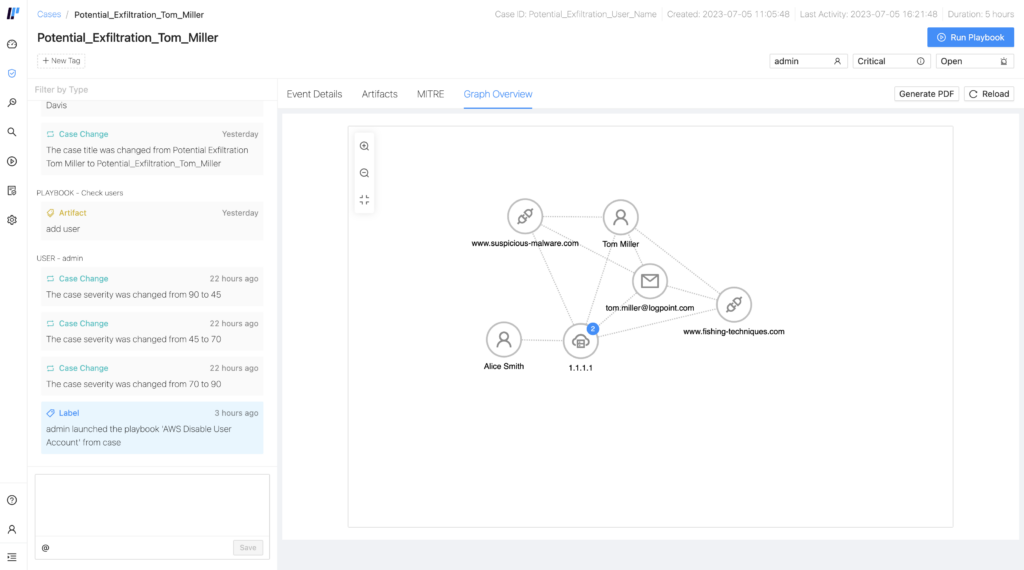
Sometimes, investigating a case can be complex as it requires an understanding of how all the artifacts, meaning all the external references or resources a playbook uses or accesses, connect to each other. Analysts will now find a tab called “Graph Overview” that aims to help them make sense of the case and reduce complexity, which in turn translates into more efficiency and less time spent on investigation.
In addition, analysts can see all the incidents inside of the case mapped against the MITRE Tactics, Techniques, and Procedures (TTPs) and kill chain. This way, they can easily identify behaviors, methods, or patterns of activity that are normally used by malicious actors directly from the case.
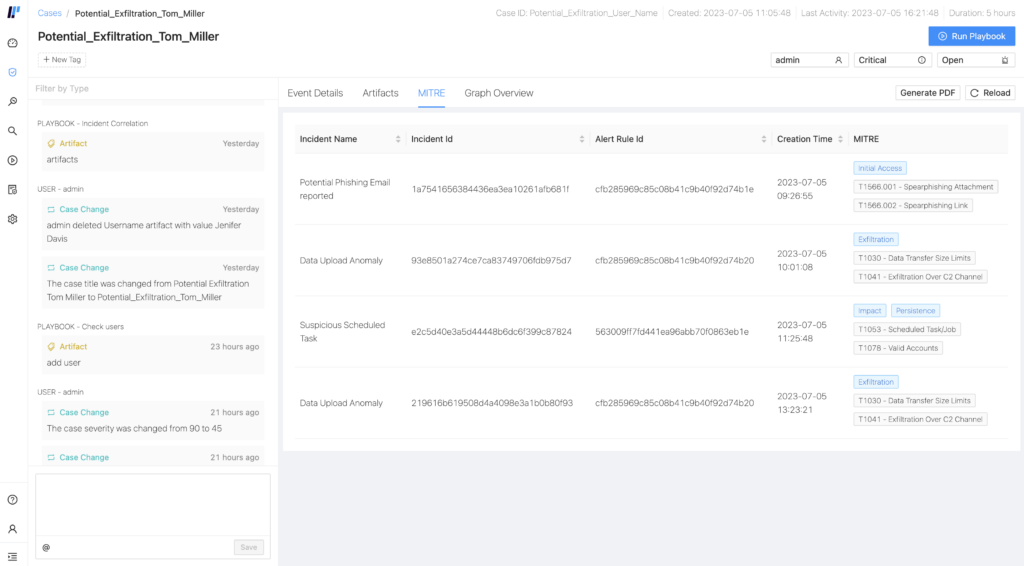
With this extra contextual data (previously only available in the SIEM), we close the loop between the alerts thrown by SIEM, the investigation in Cases, and the automated response in SOAR. This way, analysts can respond to threats faster and more adequately by running playbooks directly from the artifacts.
Moreover, all investigations can be easily summarized with one just click directly.
With the latest release of SOAR, we introduced case summaries that allow the analyst to get a comprehensive PDF report of the ongoing, or finalized, case and share it with the team or other stakeholders in the company that might require this information. As they don't have to go through all the information, but everything is gathered automatically in a timeline, SOC teams save time and gain efficiency.
Playbooks: Simpler and easier automation
In our efforts to facilitate the job of the SOC team, we also brought enhancements to playbooks. So, to start with, we improved the documentation of 20 existing pre-configured playbooks and added icons to the action building blocks to illustrate each action's function. It can be difficult to understand how a playbook does what it says it does if it’s not clear – not a problem anymore.
Flexibility is key when defining complex workflows with playbooks, and workarounds do not always give the results needed. Now, users can add operators 'OR' and 'AND' to conditional cases by editing configuration rules in playbooks. By doing this, analysts can create more precise automation and less time-consuming workflows.
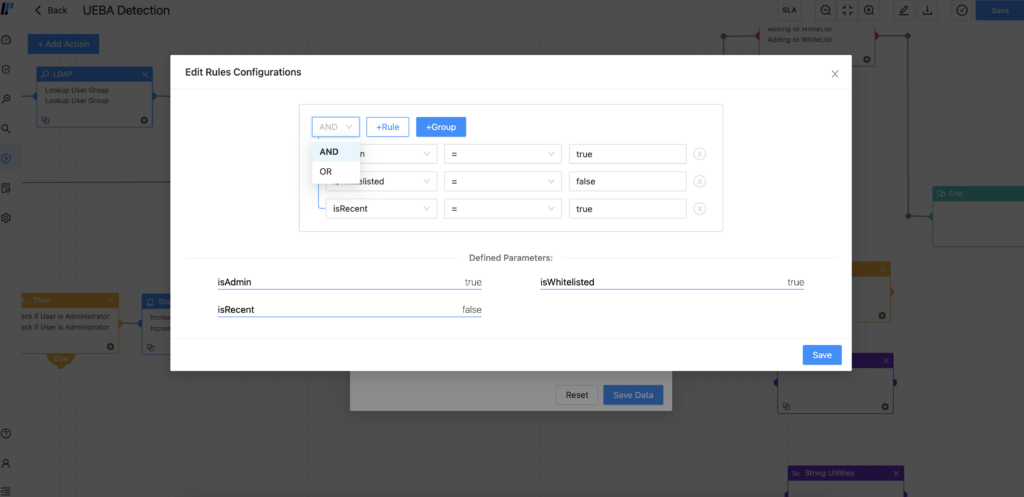
Finally, and for those situations in which playbooks depend on the output of async actions, such as an approval through email or ticketing systems, we have released the possibility of resuming execution until confirmation. By allowing playbooks to perform async API actions, we give back automation in circumstances that otherwise will stop the workflow.
And speaking of things getting stuck. If a playbook gets stuck in the runtime view, SOAR administrators can now terminate them. They can do it individually or select several by using the checkboxes in the list and terminate them all at once. Lastly, it’s important to highlight that SOAR is now available to SaaS tenants, too.
Facilitating the job for the SOC team in MSSPs too
And for SOC teams working in a multitenant environment, we expanded and improved generic playbooks. This allows analysts to update them once and distribute them saving time and reducing errors.
This is perfect for MSSPs, who also experienced the update of Director, our MSSP platform, to the latest version of Ubuntu during this last quarter. With this upgrade of the operating system, we ensure a good customer experience by delivering compliant, up-to-date, and stable software.
AgentX: Enhancements for endpoint response capabilities
Converged SIEM is an end-to-end security platform because it covers the whole TDIR process. With the inclusion of AgentX, our native endpoint agent, at the beginning of this year, Converged SIEM also provides EDR capabilities.
This quarter, we decided to improve AgentX even further, releasing updates to allow customers to select the installation directory and manage the TLS authentication directly from the UI. Finally, with this release AgentX is automatically authenticated in SOAR, saving our users time and preventing them from mistakes in manual authentications.
All these updates aim to ease the deployment and operation of AgentX and improve the analyst experience. But one can see this is an overall theme in Logpoint’s approach of creating an end-to-end security platform that is not only easy to operate with but useful to SOC teams, regardless of their experience, size, and seniority.
Do you want to know more about Converged SIEM or any of the products and services that Logpoint provides? Contact your local representative and get a demo.







