By Ivan Vinogradov, Solution Architect, LogPoint
Risky insiders (also known as insider threats) are one of the main threats to organizations in the current security landscape. As the 2019 Fortinet Report on this topic has shown – almost 70% of organizations feel moderately to extremely vulnerable to this type of threat.
In this blog, we aim to address this topic and propose some basic ways to detect and counter this type of threat.
Insider Threat definition
An insider threat, in the context of an organization, is a threat that comes from an individual belonging to or closely associated with that organization. Contrary to a popular belief, this threat is not necessarily malicious or even intentional. Other factors, such as human negligence would also fall under this umbrella. It is also not exclusive to actual individuals – contractors, for example, are also included in this category.
Who are the insiders in your company? Different types of Insider threats
There are several ways one could classify insider threats. For example – by the type of relationship they have with the entity that is under said threat – from former employees to parts of its supply chain.
However, by convention there are three general types of insider threat:
- Malicious Insiders: probably the best known and most publicized category of insider threat. This is typically individuals who take advantage of their privileged access to the organization’s resources in order to inflict some form of harm on the organization.
- Negligent Insiders: individuals who fail to practice security, follow regulation and standards, etc. Often these are unknowing – especially if, for example, the company’s security policies have not been articulated.
- Infiltrators: actors that are in practice outsiders who intentionally gain insider access – often temporarily – in order to achieve their objectives.
The threat model for these varies widely. For example, the often-used example of disgruntled employee or former employee may in fact prove more of a threat than an infiltrator due to their experience and knowledge of the environment. Similarly, negligence can result in significant commercial losses. For example, exposed databases which have often resulted in simple but high-profile hacks.
How to detect an insider threat?
It is notoriously difficult to identify an insider threat in advance. And it’s also quite difficult to investigate it. There is a high variety of behaviors that can be associated with insider threats. Because their behavior is highly dependent on non-technical factors.
Potential insider threats are typically de-risked during the early stages of engaging with them. For example vetting a candidate, auditing for compliance in the case of vendors, signing contracts and similar solutions. In terms of technical controls, prevention is achieved through restrictions on the use of personal PCs, DLP solutions, various mobile device monitoring enrollments, etc.
However, if an organization were to allow a potential threat to slip through its initial measures, there are few things that can be utilized. One technical solution is the use of baselining of user behavior.This is typically done through a wide-spanning integrated monitoring solution such as a SIEM.
Having a behavioral solution – such as UEBA – would help here as well. Typically, these solutions have standard ways of identifying abnormal behavior and assigning risk to individuals. A good starting point if one were to threat hunt for a potential insider threat. UEBA also tends to be non-intrusive and non-transparent when it comes to personal data. This is highly helpful if privacy is a concern.
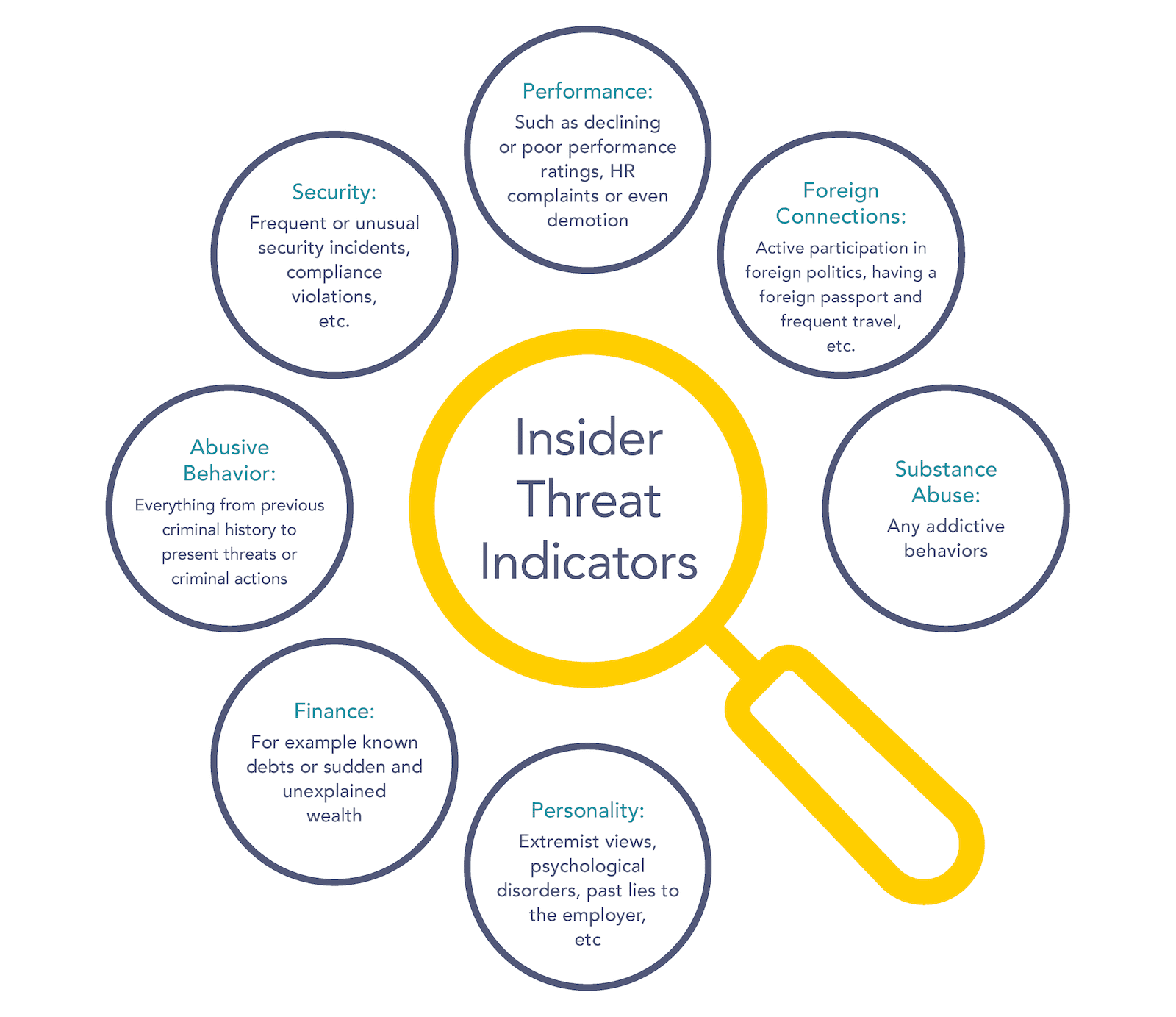
Common insider threat indicators
Overall, there are many, many potential indicators of an insider threat – which is what makes detecting one difficult.
However, if we look at the established best practices, on a higher level the indicators fall into the following categories:
- Performance: such as declining or poor performance ratings, HR complaints or even demotion
- Foreign Connections: active participation in foreign politics, having a foreign passport and frequent travel, etc.
- Security: frequent or unusual security incidents, compliance violations, etc.
- Abusive Behavior: everything from previous criminal history to present threats or criminal actions
- Finance: for example known debts or sudden and unexplained wealth
- Substance Abuse: any addictive behaviors
- Personality: extremist views, psychological disorders, past lies to the employer, etc.
Examples of Insider Threats
A common and deceptively simple example of an insider threat is an employee who is dodging security measures such as password renewal, enrollment in MDM solutions or simply does not follow policies.
If one were to consider a company spanning several continents that suddenly needs to enroll in a data protection solution, MDM or some other technical security control, but there are logistical impairments, you may end up with a small army of insider threats without even being aware of it. This underlies the virtue of security basics as a way to prevent insider threats.
Another example – perhaps more glamorous – is the presence of spies. This is now done far more rarely as technical methods are more reliable and have a higher reliability. In many cases where individuals were engaged in espionage, they were employees already planning to leave the company. Such behavior is detectable if one is willing to implement controls that are highly invasive of privacy. For example stripping HTTPs to examine what data the user is transferring.
How to detect and stop insider threats
Overall, same as with anything, defense-in-depth is a great heuristic to start with.
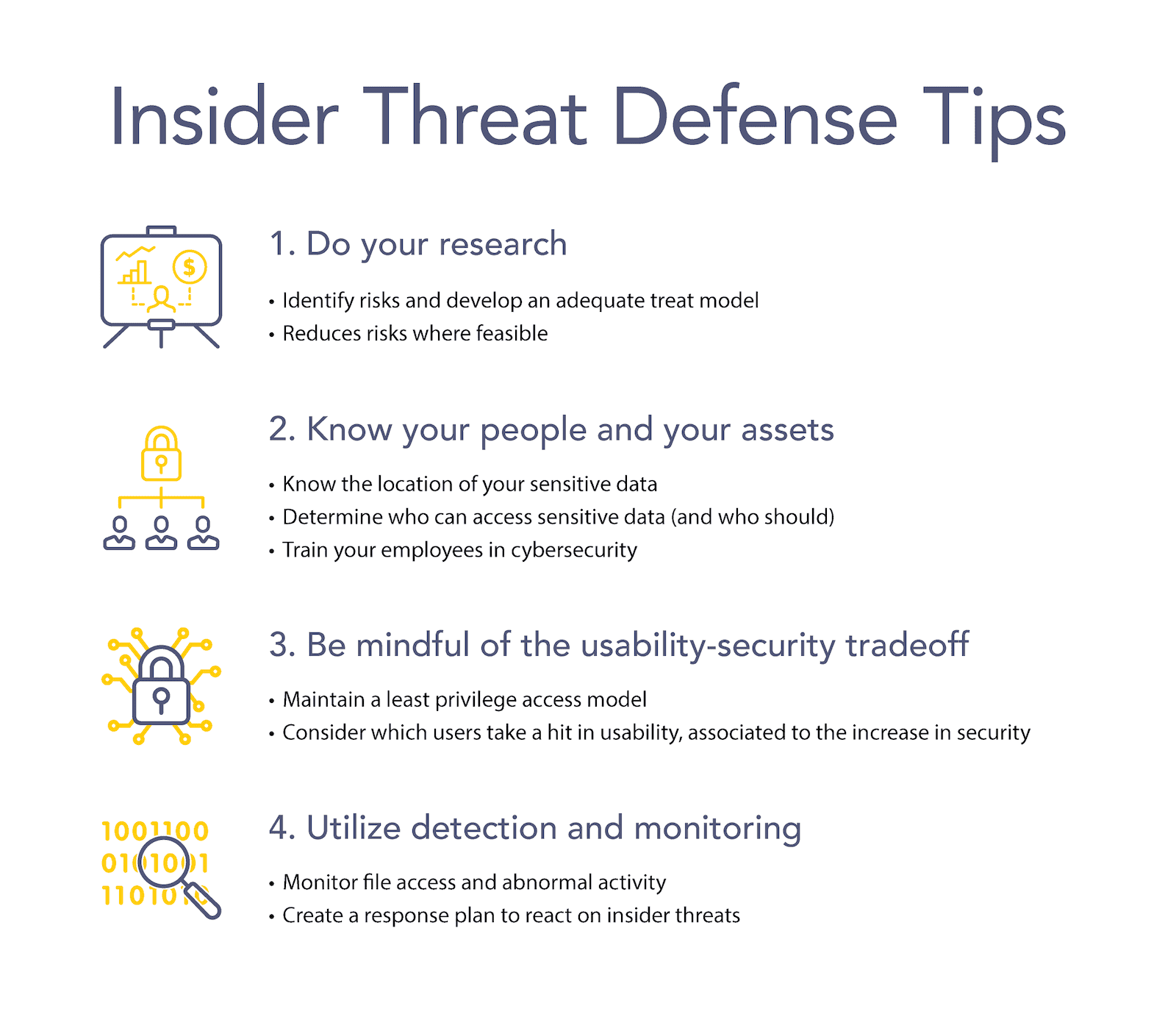
Step 1: Do your research
First, consider the pool of individuals you are recruiting from or otherwise conducting business with. Consider the associated risks and develop an adequate threat model. Following that, utilize available vetting methods to achieve a risk reduction that you believe to be cost-effective at this stage. The intensity of this may vary – from social media research to contacting previous employers to many things that go even more intense due to the highly sensitive nature of the business.
Step 2: Know your people and your assets
Within your environment, have an understanding as to who needs to know and operate which resources and restrict their access to the maximum possible degree otherwise. Utilize hardware and software that have already been configured or are configured automatically. Do not rely on users to get there themselves.
Step 3: Be mindful of the usability-security tradeoff
Be mindful of the usability-security tradeoff and consider which users will bear the brunt of the usability hit that is inevitably associated with an increase in security. Pay extra attention to these individuals.
Step 4: Utilize detection and monitoring, the final step
Finally, utilize detection and monitoring to the fullest extent allowed by the scope of your security program and the legal status of such activities in your locale. There are typically high-risk users that you can point out as more likely to be engaged in these activities. Based on, for example, their previous failures to comply with company security policies. Run threat hunts periodically and utilize tools like UEBA to automate detection as much as possible, or at least assist with it.
When it comes to external partners – compliance, contracts and audits are your main tools. While research that comes with almost all commercial relationships will tend to cover security aspects, make sure that your partners don’t accidentally become an entry point into your environment due to their negligence. And if they do, be sure that your organization’s liability for such incidents is limited.