Recently, CISA, along with the National Cyber Security Centre (NCSC) of the United Kingdom, the Polish Military Counterintelligence Service (SKW), CERT Polska (CERT.PL), and the Federal Bureau of Investigation (FBI) of the United States published a report regarding the Russian Foreign Intelligence Service (SVR)-affiliated cyber actors exploiting the CVE-2023-42793 that allow an unauthenticated malicious actor to execute arbitrary code on the TeamCity server remote code.

Since September 2023, Russian SVR cyber operatives going by the names APT 29, the Dukes, CozyBear, and NOBELIUM/Midnight Blizzard have been widely using CVE-2023-42793 to target JetBrains TeamCity software servers to advance its privileges, traverse sideways, install more backdoors, and undertake further actions to secure continuous and enduring access to the compromised network environments. Targeting public and private networks worldwide to collect a broad spectrum of foreign intelligence to encompass political, economic, military, scientific, and technological data. Over the years, SVR's activities have evolved, targeting entities ranging from government agencies to technology companies. They engage in reconnaissance, file exfiltration, privilege escalation, persistence techniques, sensitive data exfiltration, and lateral movement within compromised environments.
As per CISA, the SVR utilized various techniques to avoid detection, including turning off endpoint detection and response (EDR) and antivirus software, hiding backdoors in legitimate software, and using covert channels via Microsoft OneDrive and Dropbox for command and control. Throughout their operations, the SVR uses various tools, including custom backdoors like GraphicalProton, which utilizes cloud services for data exchange and employs multiple layers of obfuscation and encryption to evade detection. They state that SVR operation is directed at networks hosting TeamCity servers and continues its established pattern of targeting technology-oriented companies.
All TeamCity software versions before 2023.05.4 are affected by CVE-2023-42793 which has a CVSS score of 9.8 (Critical). It's an authentication bypass vulnerability in JetBrains TeamCity located within the "RequestInterceptors.java" file whereby attackers utilize this flaw to send an HTTP POST request to "/app/rest/users/id:1/tokens/RPC2" to retrieve an access token. If an incoming HTTP request corresponds to this wildcard path "/**/RPC2," the TeamCity server skips authentication checks, enabling unauthorized access to victims, specifically enabling threat actors to infiltrate the networks of numerous software developers. JetBrains responded to this CVE by issuing a patch in mid-September 2023, limiting the SVR's activities to exploiting TeamCity servers that remained unpatched and accessible via the Internet.
In this blog, we take references from the CISA report and analyze how Logpoint customers can detect, hunt, and respond to TTPs mentioned using Logpoint Converged SIEM. In addition, customers can leverage our previous Emerging Threats report on APT29 for an in-depth analysis corresponding to previous TTPs utilized by ATP29.
Log Source Needed
To detect, hunt, and respond to the tactics, techniques, and procedures of APT9, Logpoint customers users would need the following log sources:
-
Windows
-
Windows Sysmon
-
Firewall
-
IDS/IPS
-
Proxy
TTP Detection and Hunting Using Logpoint
In late September 2023, the SVR initiated the exploitation of Internet-connected JetBrains TeamCity servers using CVE-2023-42793, facilitating insecure handling of particular paths, which enabled the bypassing of authorization protocols and led to the execution of arbitrary code on the server.
Initial Access - Exploiting CVE-2023-42793
Based on the CISA's observations, the exploitation of TeamCity typically resulted in code execution [T1203] with elevated privileges, providing the SVR with a significant advantage in the network environment. The authoring agencies need to learn an alternative method the SVR employs to gain initial access to JetBrains TeamCity servers. According to CISA, the exploitation of the vulnerability necessitates the utilization of the following specific endpoints:
-
/app/rest/users/id:1/tokens/RPC2: This endpoint is essential for exploiting the vulnerability.
-
/app/rest/users: Only necessary if the attacker intends to generate an arbitrary user.
-
/app/rest/debug/processes: Only necessary if the attacker aims to create an arbitrary process
As a user of Logpoint Converged SIEM, you can use the following query for detection of exploited endpoint purposes:
Reconnaissance
Early observations indicate that the SVR employed fundamental, built-in commands for conducting host reconnaissance [T1592.002]. Once the SVR established a secure position and became familiar with a victim's TeamCity server, it directed its attention toward network reconnaissance [T1590.004]. The SVR conducted network reconnaissance using a blend of inherent commands and supplementary tools, including a port scanner and PowerSploit, activated in the system's memory [T1046]. Furthermore, the SVR executed specific commands from the PowerSploit toolkit.
For the detection of host reconnaissance, customers can utilize our vendor alerts "Possible Reconnaissance Activity," "System Service Discovery," and "Reconnaissance Activity with Net Command" from the Alert Rules Application or can utilize the following hunting query.
Likewise, Logpoint customers can use the following hunting query for network reconnaissance:
Execution and Persistence
SVR cyber operatives utilize a modified version of GraphicalProton, which employs DLL hijacking within Zabbix to commence execution [T1574.002]. Meanwhile, SVR cyber actors seem to exploit the Windows Task Scheduler to schedule tasks, enabling the initial or repetitive execution of malicious code [T1053.005]. Similarly, for persistent access to the compromised environment, the SVR employed the Rubeus toolkit to create Ticket Granting Tickets (TGTs).
Hunting the scheduled task used by SVR for the GraphichalProton backdoor below mentioned query can be used.
Privilege Escalation and Credential Access
The SVR employed various tools to elevate privileges [T1098], including WinPEAS, NoLMHash registry essential modification, and the Mimikatz tool. SVR cyber operatives utilized Mimikatz commands in the system's memory to acquire access to credentials stored in that memory. In specific instances, the SVR employed the SharpChromium tool to receive sensitive browser information like session cookies, browsing history, or saved logins.
The "Mimikatz Command Line Detected" alert rule with the following query can help Converged SIEM users detect the Mimikatz commands.
Similarly, The SVR modified the NoLMHash registry by running the following command.
To detect the NoLMHash registry key modification, users can query the following:
For the detection of Windows registry exfiltrated by SVR, users can enter the query below:
Defense Evasion
The SVR employed diverse backdoor installation tactics to evade detection, from hijacking legitimate software with GraphicalProton to modifying open-source tools and exploiting antivirus vulnerabilities. SVR cyber actors used a tactic [T1068] known as "Bring Your Own Vulnerable Driver," which aimed to deactivate EDR and AV defense mechanisms. Additionally, these actors injected code into AV and EDR processes to bypass these defensive measures. The mentioned query can detect known malicious drivers via their names or hash using EDRS and Blast.
Also, the query mentioned below can be utilized to detect the DLL names used by SVR for the GraphicalProton backdoor.
Lateral Movement
SVR cyber operatives might use remote services to illegally enter internal systems after gaining entry into a network. These actors executed Rsockstun in the system's memory or employed Windows Management Instrumentation (WMI) to initiate harmful commands and payloads.
Utilizing the following alert query, customers can easily detect when WMIC executes a Process Call Create suspicious calls to processes such as rundll32 and regsrv32.
Command and Control
To facilitate command and control operations, SVR might create connections dynamically with command-and-control infrastructure to circumvent typical detection and countermeasures. In specific scenarios, the SVR deployed an additional tool called "rr.exe," a customized open-source reverse socks tunneler named Rsockstunm, to establish a tunnel towards the C2 infrastructure. SVR cyber actors may utilize tunneling techniques to manage network communications to and from a victim's system through an alternate protocol, aiming to evade detection or network filtering and potentially enabling access to systems that would otherwise be inaccessible.
Exfiltration
SVR cyber actors employ OneDrive and Dropbox to transfer information to their command-and-control (C2) centers. They may exfiltrate sensitive documents utilizing automated procedures after gathering them during collection or by transmitting data through an established C2 channel. Stolen data undergoes encoding to assimilate into regular communications, using the identical protocol as the C2 communications.
Customers can utilize the following alert query to detect the network communication between domains in a query with a compromised host/server, which is also considered a false positive aspect.
Response with Logpoint SOAR and AgentX
Logpoint Converged SIEM platform includes AgentX, a native endpoint gent designed to detect, examine, and address endpoint security issues
Through automation, it accelerates threat detection in endpoints. AgentX enhances the scope of threat hunting and forensic inquiries by employing Osquery to offer comprehensive insight into endpoint operations. It swiftly identifies and confines compromised systems by persistently overseeing endpoints for indications of compromise and potentially hazardous activities orchestrated by SVR. Through inherent log and telemetry enrichment of SIEM and SOAR events, AgentX gathers endpoint logs and telemetry and supplements further context based on MITRE TTP, thereby diminishing the Mean Time to Respond (MTTR) to SVR.
Customers can always use the AgentX playbook for automated investigation and response as well as generic playbooks that can significantly affect the incident response process. Playbooks like "Isolate Host - Generic Playbook" can help isolate if the host is concerned.
Customers with Endpoint Detection and Response (EDR) from vendors like Microsoft, TrendMicro, Sophos, and Crowdstrike can also take benefit of this generic playbook to isolate affected servers for further investigation and remediation and to minimize further damage in the network.
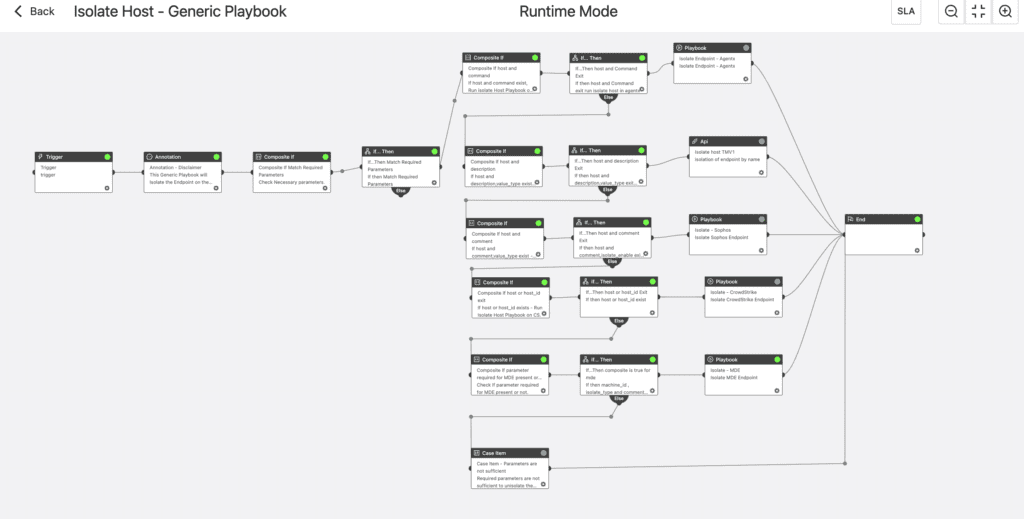
Isolate Host - Generic Playbook (support Agentx, Visionone, Sophos, Crowdstrike, Defender for Endpoint)
Once the affected servers are patched, "Unisolate Host - Generic Playbook" can remove isolation and revive servers to their original condition.
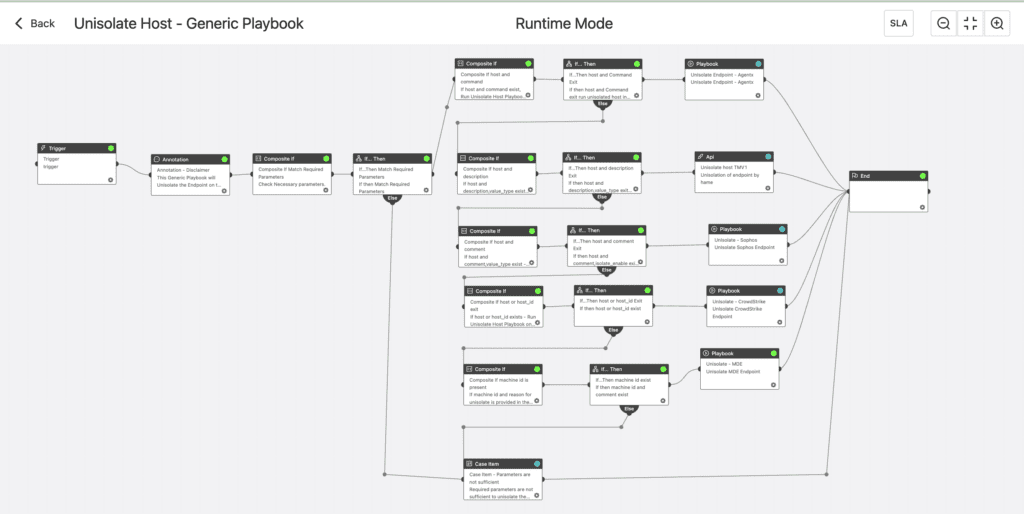
Unisolate Host - Generic Playbook (support Agentx, Visionone, Sophos, Crowdstrike, Defender for Endpoint)
Mitigation
Since the patch and plugin for the CVE are already available, install them for mitigation of this threat.
Conclusion
The ever-evolving threat landscape demands a multi-layered defense against cyberattacks. Recent exploits like CVE-2023-42793 by SVR actors and their sophisticated techniques like DLL hijacking and Rsockstunm underscore the need for vigilance. Organizations must prioritize prompt patching, advanced endpoint monitoring with tools like Logpoint's AgentX, multi-factor authentication, and robust endpoint protection to counter these threats. Continuous attention, system evaluations, and proactive adoption of emerging security measures are essential. By combining these tactics, organizations can build resilience and ensure their infrastructure is a fortress against even the most advanced cyber threats. Remember, references like CVE-2023-42793 and SVR's tactics are a roadmap for fortifying defenses and securing critical infrastructure.







