Goodbyes are hard for many people, but for a few those goodbyes are worth avenging. Welcoming new employees and bidding farewell is a regular process for the organization. People come and go; however, some who are unfortunately terminated or forced to resign can go rogue and join the dark forces. Generally, these ex-employees (we will call them “Lord Darth”) are technically well-versed with higher privileges and admin credentials. They are motivated to defame or gain monetary benefits.
History bears witness that insiders have a high chance of success. If you don’t believe it, please Google ‘insider threat cases’ and you will receive links to hundreds of unique and interesting cases. Managing the employee lifecycle (Onboarding, Retention, Development and Recognition, Exit) is critical in improving the security of an organization.
We discuss the onboarding and exit stages of the employee lifecycle in this blog, as well as Logpoint’s strategy for lowering insider threat events by leveraging automation. Although simple, these steps are critical in the HR process. Automating these processes would mitigate manual errors, thereby addressing the ever-growing list of cases involving malevolent employees. Below, we have delved into each phase with the workflow and playbook.

What is an insider threat?
CISA defines “insider threat” as
”the threat that an insider will use their authorized access, wittingly or unwittingly, to do harm to the department’s mission, resources, personnel, facilities, information, equipment, networks, or systems.”
They can be categorized into two categories: Intentional and non-intentional.
Intentional -These are the ones who previously worked, or are currently working, in the organization abusing their privileges and permissions to steal sensitive contents such as user data, product blueprints, and other confidential items.
Unintentional - Those who have been victimized by wrongfully leveraging their accounts, knowledge, and specialized processes to gain a competitive advantage or with malicious intent.
Detecting these insiders proves very difficult and generally takes time to triage. There are numerous ways to reduce and prevent these insiders from succeeding; however, proper off-boarding of the employee is simple yet effective. We have translated these simple steps into a playbook, and they can be customized in any form to meet the specific processes and policies of the organization.
Insights into Insider Threats
-
Staggeringly, 74% of respondents to a survey feel moderate to extremely vulnerable to insider threats.
-
The most critical impacts of insider attacks were loss of critical data (45%), brand damage (43%), and operational disruption or outage (41%)
-
Insider threats can be costly, 59% of the insider threat motivation was monetary gains while 50% was reputationdamage.
-
The time to contain an insider threat incident increased from 77 days to 85 days, leading organizations to spend the most on containment.
Notable Insider Threat Incidents
-
The FBI arrests 21-year-old Air Force guardsman in Pentagon leak case.
-
A Yahoo lawsuit alleged an employee stole trade secrets upon receiving a Trade Desk job offer.
-
Proofpoint alleged an ex-exec took trade secrets to abnormal security.
-
A fired healthcare exec stalls critical PPE shipment for months.
-
An Apple lawsuit says 'stealth' startup Rivos poached engineers to steal secrets.
Onboarding
The onboarding process is a formal procedure for welcoming new employees to an organization. It encompasses all the necessary paperwork, including the assignment of training (both HR and security awareness), the allocation of new devices, cubicles, and other relevant processes. Subsequently, an account will be created, and roles or function-based rights and permissions will be assigned. We are automating these crucial workflows as an onboarding playbook.
Workflow
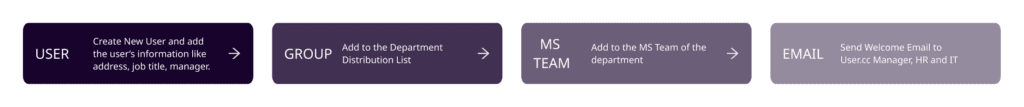
Playbook
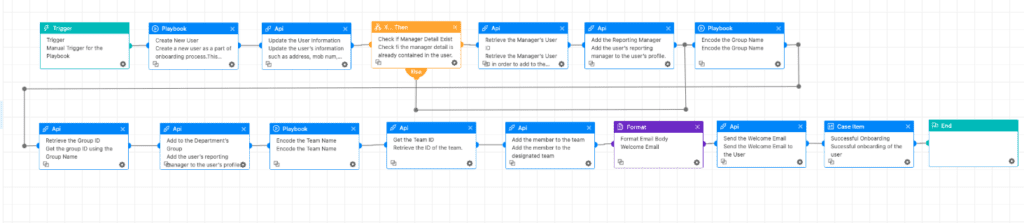
The playbook begins by creating a new user with the information provided in the trigger, which could be fed from the HR ticketing systems. Once the account is successfully created, we move towards adding the user to the distribution groups. We refrain from adding the user to department production groups at this stage. Typically, this task is handled by the reporting manager after completing other formalities such as training, and background checks.
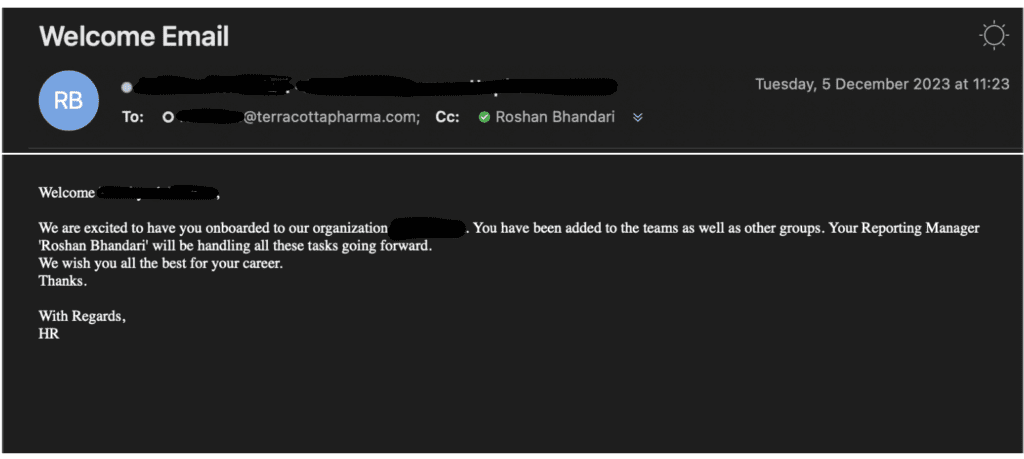
Microsoft Teams is gaining traction, and it's free to use; hence, most organizations are using it for their official messaging application. The user is added to the Teams channel and with the welcome email, the onboarding process is completed.
Off-boarding
Off-boarding is the formal exit process for employees. This includes deallocating the roles and responsibilities of the employees, returning owned devices, and disabling the account. This proper flow structure makes it a perfect automation case.
Workflow
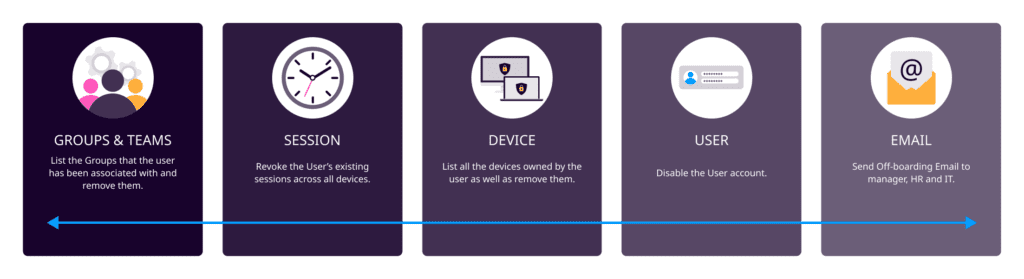
Playbook
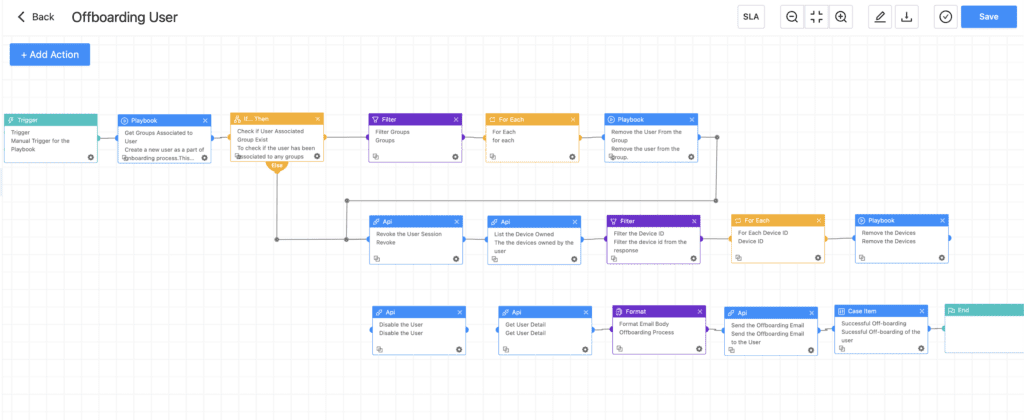
The playbook starts with retrieving all the groups that the user has been associated with. The user is removed from the groups, including the teams. The user's existing logged-in sessions across all devices and browsers are revoked.
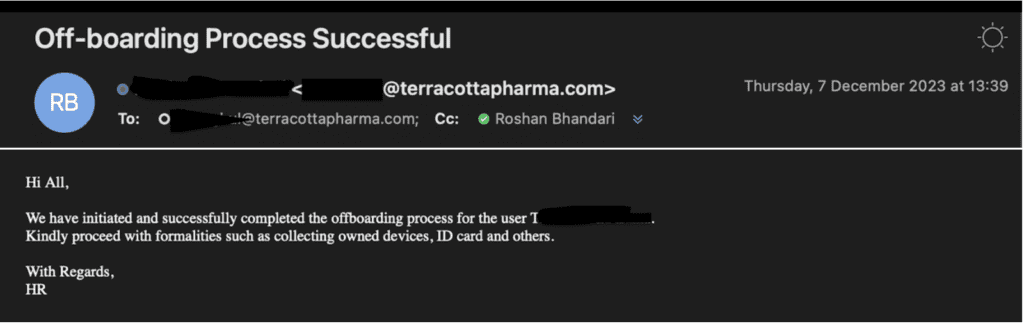
All the devices owned by the user would be listed and removed, and a successful offboarding email would be sent to HR, the manager, and IT with the owned devices. This eases HR's task of knowing the devices that need to be collected from the user before they are finally signed off or escorted.
What's Next?
Although these playbooks are an important first step in countering insider threats, we have only just begun to explore all of the possibilities. We are continuously working to automate the employee lifecycle in a number of areas, including transfers, entitlement management, notice period employee monitoring, and more. Through the integration of these extensive procedures into the playbook, our goals are to minimize mistakes, shorten reaction times, and lower the possibility of collusion.
These workflows and their associated playbooks will be featured in our upcoming blogs. Stay connected for more information.
Conclusion
Insider threat incidents are on the rise, and with organizations laying off workforces, the situation has been exacerbated. Our playbook demonstrated above, facilitates the seamless management of tasks such as role de-allocation, account disabling (including remote access, VPN, and local accounts), and handling security clearances, if applicable. By implementing our playbook, customers can achieve these processes flawlessly, minimizing the risk of human errors.
Security devices or technologies like DLP, UEBA, and EDR would actively monitor the employee's activity and thwart any unauthorized data transfer or access to confidential items. It is a complicated and mammoth task to monitor every employee; however, it is essential to monitor employees on notice periods as well as consistently low performers. Admin and Privileged employees' activity must be logged and closely monitored while investigating any anomalies promptly. Further, it is the organizational responsibility to inform the departing employee of the non-disclosure agreement (NDA) or non-compete agreement (NCA) during the exit interview.







