Fast Facts
- Cactus ransomware has been active since March 2023 and has been targeting high-profile targets so far.
- It currently holds the seventh position in the Top Group VPM (Average Victims Per Month) ranking, maintained by Darkfeed.
- This ransomware has been observed to exploit known vulnerabilities in VPN appliances (Sangfor mentions Fortinet VPN devices) to get initial access to the system.
- The most peculiar aspect of Cactus ransomware is that it encrypts itself to evade detection.
- It has also been seen exploiting vulnerabilities in a data analytics platform called Qlik Sense to obtain initial access.
Table of Contents
Background
Ransomware is malicious software that encrypts the victim’s data and demands payment in return causing financial losses and operational disruptions. According to NCC Group's findings, the number of overall ransomware victims affiliated with different ransomware groups peaked in September 2023, with a total of 514 incidents. This surpasses the previous record set in July 2023, where there were 502 reported attacks.
The report also provided a graphical representation that illustrates an upward trajectory in the trend. While there was a minor decline in ransomware attacks during March-April and July-August, incidents have been on the rise throughout the other months of 2023. When compared to 2022, the data indicates a noteworthy surge in the frequency of ransomware attacks.
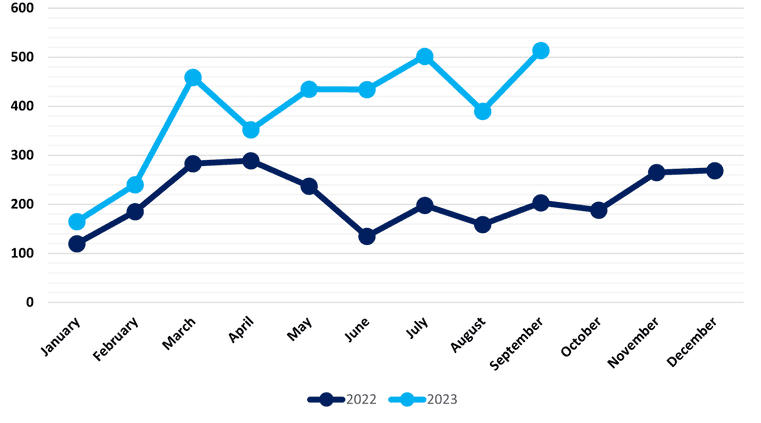
Fig: Global Ransomware Attacks by Month 2022 - 2023 (Source: NCC group)
The escalating trend in ransomware attacks underscores the severity of this growing threat. Ransomware, continues to become increasingly sophisticated with each passing day, emphasizing the need for individuals and organizations to remain vigilant. An illustrative example of a conversation between a victim and a ransomware group vividly portrays the merciless nature of these cyber criminals. This interaction reminds the urgency for robust cybersecurity measures and heightened awareness.
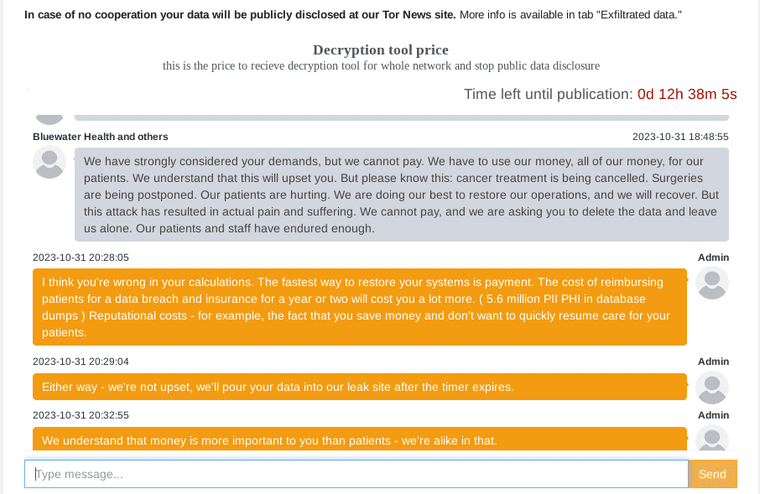
Fig: A chat between a victim and the ransomware group (source)
Among the many ransomware groups, Cactus is a newcomer yet it has quickly made a significant impact since its first emergence in March 2023. It has targeted many high-profile targets, with 58 victims as of November reported by Darkfeed. Cactus employs double extortion tactics, compromising sensitive data before encryption, leaving victims with limited choices. The most peculiar behavior of this ransomware is its evasion techniques including encrypting itself to avoid anti-malware detection and utilizing multiple batch scripts for various actions alongside acquiring the ransomware binary. The encrypted files have the .cts extension and the ransom note is named cAcTuS.readme.txt.
A comprehensive malware analysis by Swascan shows that Cactus ransomware has several unique features like auto-encryption and a consecutive change of file extensions post-encryption, making the identification of affected files more challenging. It utilizes the C:\ProgramData\ntuser.dat file to store the public key for encrypting the malware sample itself to create confusion and evade detection. According to Swascan, two key aspects of Cactus ransomware that stand out are:
-
It employs the well-known and easily "unpackable" UPX packer.
-
It divides encrypted files into micro-buffers, possibly to speed up the management of encrypted data streams.
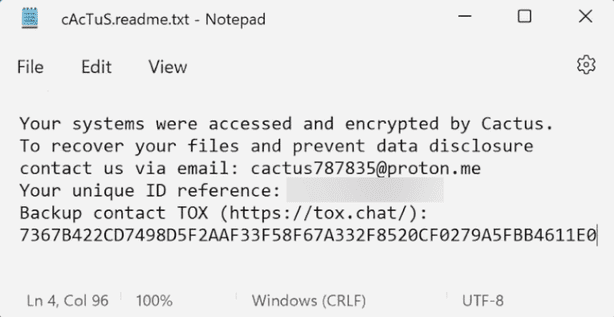
Fig: Cactus Ransom Note (Source: SalvageData)
Fig: Encrypted Files (Source: pcrisk)
Cactus ransomware's impact is undeniably severe, causing a lot of damage. However, it's crucial to recognize that Cactus is not alone with such a devastating impact; numerous ransomware families can do the same. These threats can disrupt business operations, tarnish reputations, and result in substantial financial losses through ransom payments, diminished revenue, and regulatory fines. In extreme cases, the cumulative impact may even lead a company into bankruptcy.
Prevention
However, these sorts of cybersecurity incidents can be prevented to some extent with good security practices. Proactive cybersecurity practices are essential, and established organizations such as NIST, CISA, and SANS provide valuable guidelines for good security practices.
In light of Cactus ransomware, patching the VPN flaw can be a major preventive measure. However, organizations can fortify their defenses with the following proactive steps:
- Enforce multi-factor authentication (MFA) for all services, particularly to email, VPNs, and accounts responsible for accessing critical systems.
- Periodic risk assessments should be done to identify, prioritize, and address risks stemming from various threats and vulnerabilities.
- Avoid exposing critical services like remote desktop protocol to the internet. If needed apply appropriate compensating measures to prevent its abuse and exploitation. It is better to limit the usage of remote desktop services if possible.
- Regularly scan and assess systems for vulnerabilities and misconfiguration. Also, keep operating systems, software, and firmware up-to-date. Limit unnecessary network exposure and enforce strict access control policy to reduce the attack surface in an organization. Also, enable the available security features.
- Monitor and control privileged accounts and apply the principle of least privilege. If possible implement time-based access for accounts set at the admin level and higher so that the users get access to the specified system for a set timeframe so that they can complete their task and then the access is revoked when not in need.
- Password policies should be strong and should require passwords to be unique, complex, and long. Avoid usage of default admin usernames and passwords to prevent unauthorized access. Storing sensitive credentials in notes or text files poses a significant risk. Additionally, saving passwords in browsers exposes them to potential dumping by adversaries. So, to enhance security, use password managers as a safer alternative.
- Employ Identity and Access Management (IAM) systems to oversee access control and also use credential monitoring services to keep a vigilant eye out for any exposed or compromised credentials.
- Use organizational detection or prevention systems like antivirus, EDR, Firewall, IDS/IPS, etc, and ensure that they are installed, configured properly, up-to-date, and trigger alerts if they are accidentally turned off. Also, establish a security baseline of normal network traffic and tune network appliances to detect anomalous behavior.
- Constantly review the security postures of third-party vendors or partners interconnected to your organization and monitor their connections for suspicious activity.
- Constantly monitor domain controllers, servers, workstations, and active directories for new and/or unrecognized accounts.
- Privilege escalation and lateral movement generally depend on software utilities running from the command line. So, disable command-line and scripting activities where possible.
- Use phishing prevention methods like user awareness training, email, and attachment filtering, adding flags for external emails, and disabling the macros.
- Security awareness training for employees with incident response simulations.
- Use segmentation or other methods to design the network in such a way as to maximize the reduction of impact.
- Encrypting the feasible portion of data at rest can render it useless to the threat actors even if they are successful in exfiltrating them and hence minimize the impact.
- Implement strict role-based access controls, credential rotation, and regular employee training to secure critical GitHub keys and Jenkins credentials to prevent unauthorized access which can safeguard the software supply chain.
The attached report contains an in-depth analysis of cactus ransomware along with proactive security, threat-hunting, and incident response guidelines necessary to fortify your organization against ransomware attacks. Access the complete report for a comprehensive overview and actionable insights on safeguarding your systems and data from such attacks.








