Last updated 20/12/2021, 10 am CEST
Status of Log4j vulnerability in LogPoint
Recently, a critical remote code execution vulnerability (CVE-2021-44228), also known as Log4Shell, was discovered, which affects Apache Log4j versions 2.0-2.14.1. Log4j is a popular logging library in Java and is used in several enterprise applications, including LogPoint products.
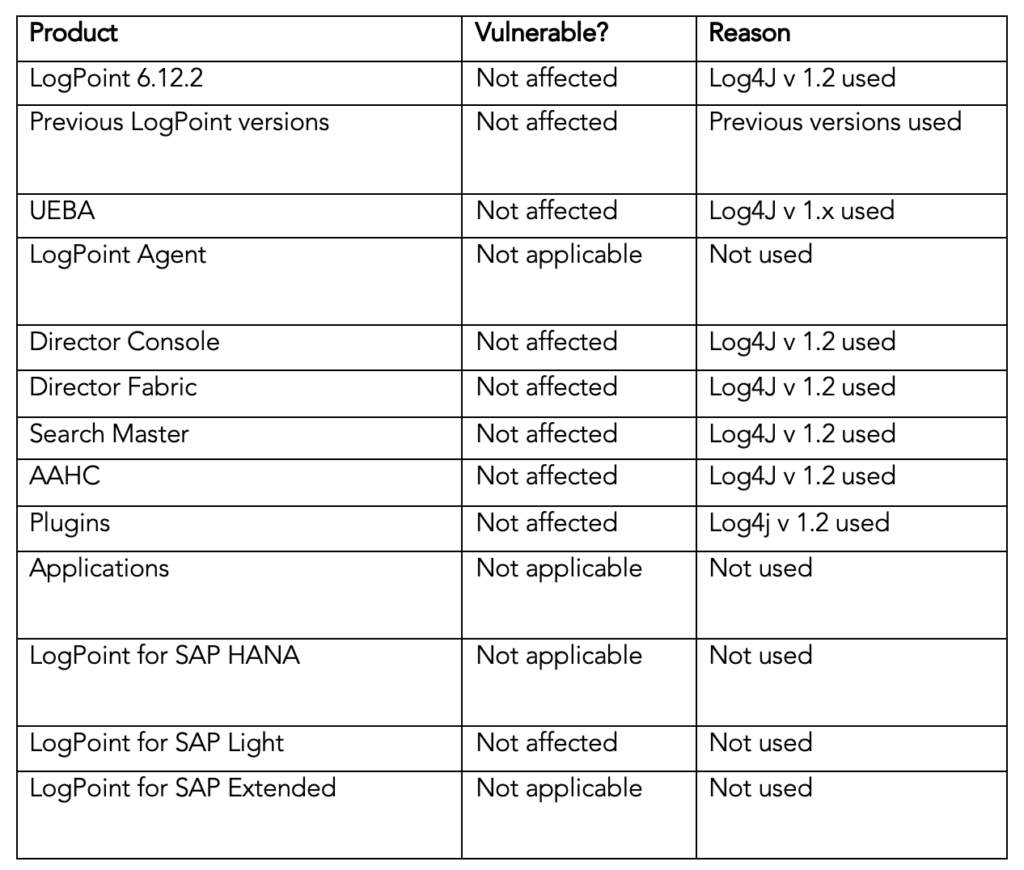
Vulnerability status of LogPoint products
At this time, we have determined that no LogPoint products are affected by the vulnerability, and we will update this page as we continue our investigations.
For detailed information about the vulnerability status of each LogPoint product, please consult the table below. If you have any questions about the vulnerability, please contact your LogPoint representative.
Details of vulnerability by LogPoint product
* Note: log4j v1.2.x is vulnerable to another vulnerability, that is only exploitable when using the class JMSAppender. While LogPoint uses log4j in version 1.2, JMSAppender is not used in LogPoint and we have actively attempted to exploit the vulnerability, confirming that in these cases log4j v1.2 is not vulnerable in the current deployment configuration.
Log4j 1.x vulnerability is not applicable & deprecating log4j soon
We are using log4j as the logging engine for our java based components but log4j is not our main logging engine and log4j only used for a few components. LogPoint uses logback as the main logging engine and LogPoint is in the process of deprecating log4j soon.
Log4j consumes log messages directly from the internal java components only and those java components are not exposed to the outside world.
Specifically, Log4j 1.x vulnerability is not applicable for LogPoint product because we are not using JMSappender feature.