Fast Facts about Rhysida
-
Rhysida emerged as one of the most active ransomware groups in November 2023.
-
Targets medium to large-scale industries with a significant impact on the education sector.
-
Victims of the Rhysida group are spread across 25 countries, with a majority of victims in the United States.
-
Utilizes the malware families PortStarter and SystemBC.
-
Rhysida employs a double extortion technique, stealing data from victim networks before encrypting it and threatening to publish it on the dark web unless a ransom is paid
Table of Contents
All about Rhysida
Rhysida ransomware group, which first appeared in May 2023 and operates as a ransomware-as-a-service, showed an unpredictable pattern of activity. Notably, the group's activities surged again in November, following its prominence by securing a position in the Top 10 ransomware groups by victims in the months of June and July. Rhysida's attacks are becoming more widespread, with sectors such as healthcare, education, government, and manufacturing industries being targeted. Rhysida's activity has resembled a roller coaster ride since its emergence in May, with fluctuating monthly victim counts. The graph below illustrates the statistics of Rhysida's activities.
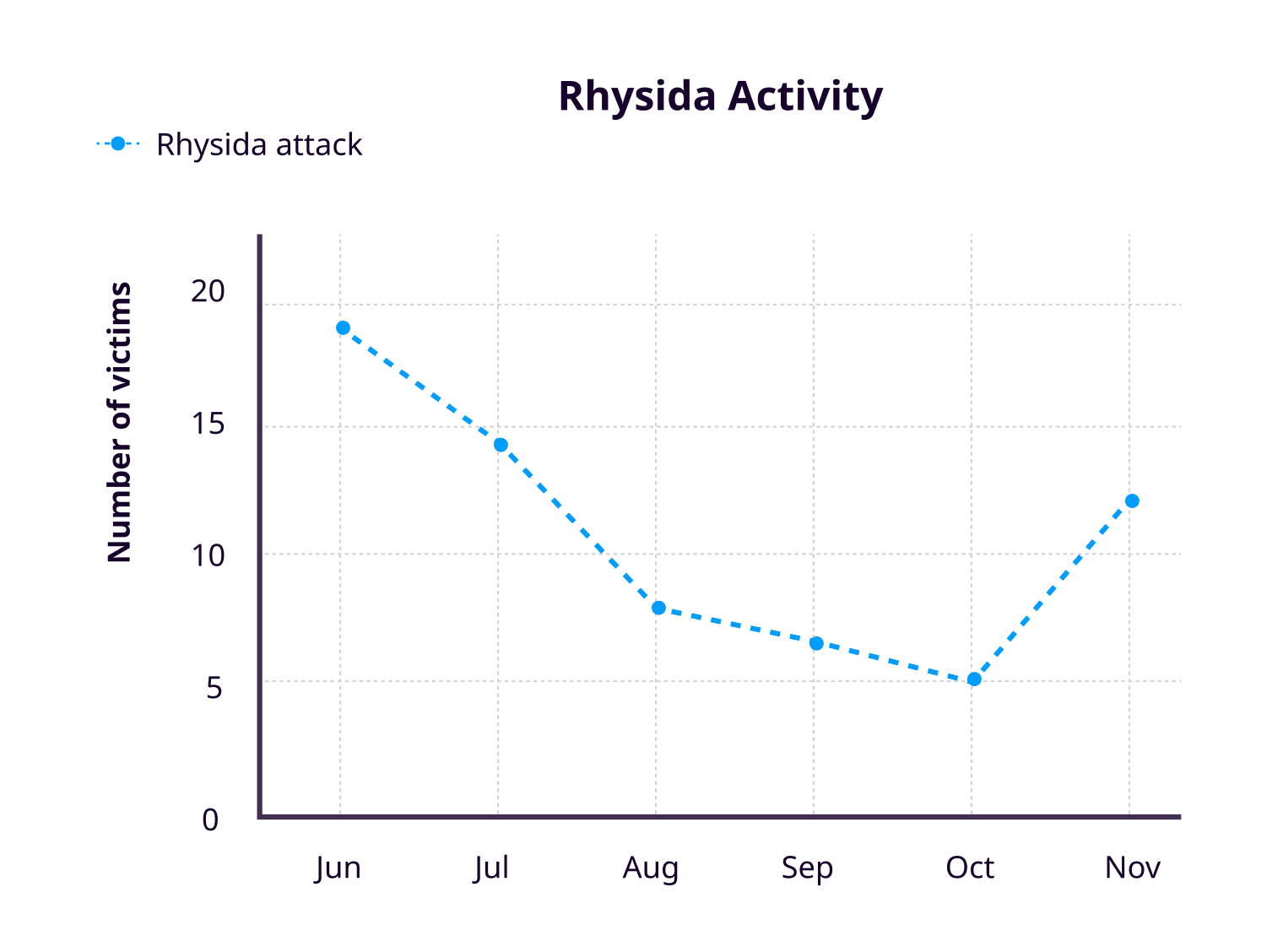
Although the group does not have a long list of victims, its focus on high-profile targets has a severe impact on those who have been affected. In August, the Rhysida ransomware group claimed responsibility for the cyberattack on Prospect Medical Holdings, which impacted 17 hospitals and 166 clinics across the United States. According to the report, the group claims to have exfiltrated 1.3 terabytes of SQL database and one terabyte of documents, including patient records, corporate documents, and 500,000 Social Security numbers. The Rhysida ransomware group has also asserted responsibility for a cyberattack on the British Library, which is one of the largest libraries globally.
Rhysida has primarily relied on leveraging valid credentials and establishing network connections through VPN for initial access. Although how they obtained these credentials is still being determined, it is presumed that they were obtained through an Initial Access Broker(IAB). Upon infiltrating a victim's network, the group employs net commands and leverages tools like Advance IP/Port Scanner to enumerate victim environments and gather critical information about domains. Rhysida leverages Sysinternals tools like PsExec to deploy ransomware on target systems for lateral movement. Before initiating the encryption process, they exfiltrated sensitive data through diverse channels, including MegaSync and PowerShell exfiltration scripts, employing double extortion techniques.
We have created a comprehensive report that details the techniques discovered during our research. In this report, you can read more about this ransomware group, malware analysis, it's mapping to the MITRE ATT&CK framework, and its detection, investigation, and response with Logpoint Converged SIEM.
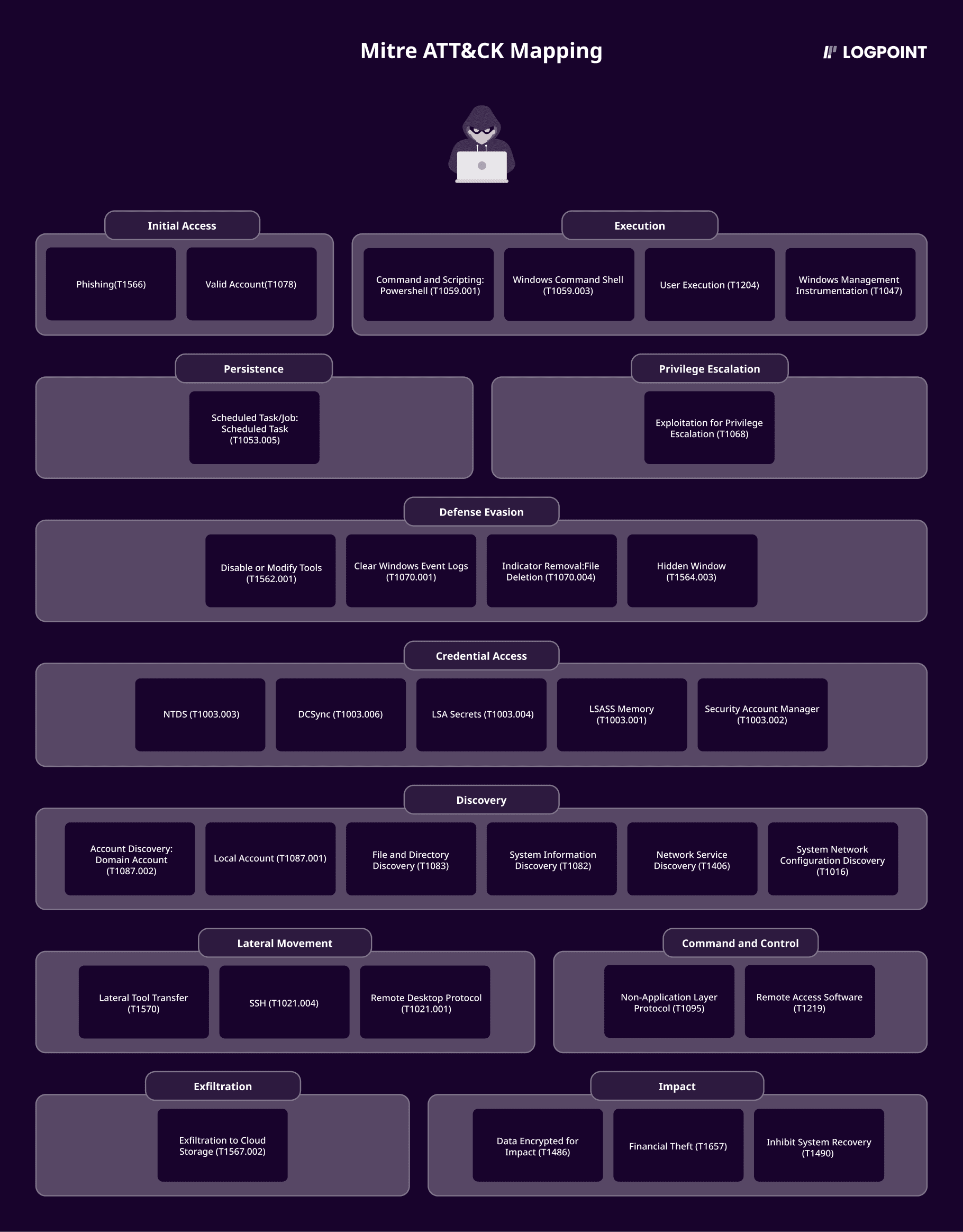
**All new detection rules are available in Logpoint's latest release and through the Logpoint Help Center.
Logpoint Emerging Threats Protection Service provides subscribers with customized investigation and response playbooks tailored to your environment. Contact the Global Services team here.








