On February 19, 2024, ConnectWise issued a critical advisory concerning two highly concerning vulnerabilities, namely CVE-2024-1709 (rated at a CVSS score of 10 – Critical) and CVE-2024-1708 (rated at a CVSS score of 8.4 – High) impacting ScreenConnect versions 23.9.7 and earlier. These vulnerabilities have been identified as significantly exploitable and have been observed being actively leveraged in real-world scenarios since the advisory’s release. Additionally, proof of concept exploit code has become widely accessible, exacerbating the risk associated with these vulnerabilities.

The advisory further elaborates on the vulnerabilities as:
Vulnerability
-
CWE-288 Authentication bypass using an alternate path or channel (CVE-2024-1709)
-
CWE-22 Improper limitation of a pathname to a restricted directory (“path traversal”) (CVE-2024-1708)
The severity of these vulnerabilities is underscored by their ease of exploitation, with attackers having readily exploited them in the wild. A tweet by Shadowserver on February 20, 2024, revealed that approximately 3,800 instances of ConnectWise ScreenConnect were identified as vulnerable, emphasizing the widespread risk posed by these vulnerabilities.
Technical Breakdown
CVE-2024-1709 - Authentication Bypass
The first vulnerability, identified as CVE-2024-1709, was discovered due to a critical oversight in the authentication process of ConnectWise ScreenConnect versions 23.9.7 and earlier. This flaw was unearthed after examining a text file. The examination revealed that the authentication mechanism was inadequately secured against all access paths, including the crucial setup wizard ('SetupWizard.aspx').
In the latest update of ConnectWise ScreenConnect, a fundamental improvement was made in a text file called SetupWizard.aspx. This file controls the setup wizard, which is used to set up the initial administrative user and install a license for the system. Previously, there was a potential issue where the setup wizard could be accessed even after the initial setup was completed.
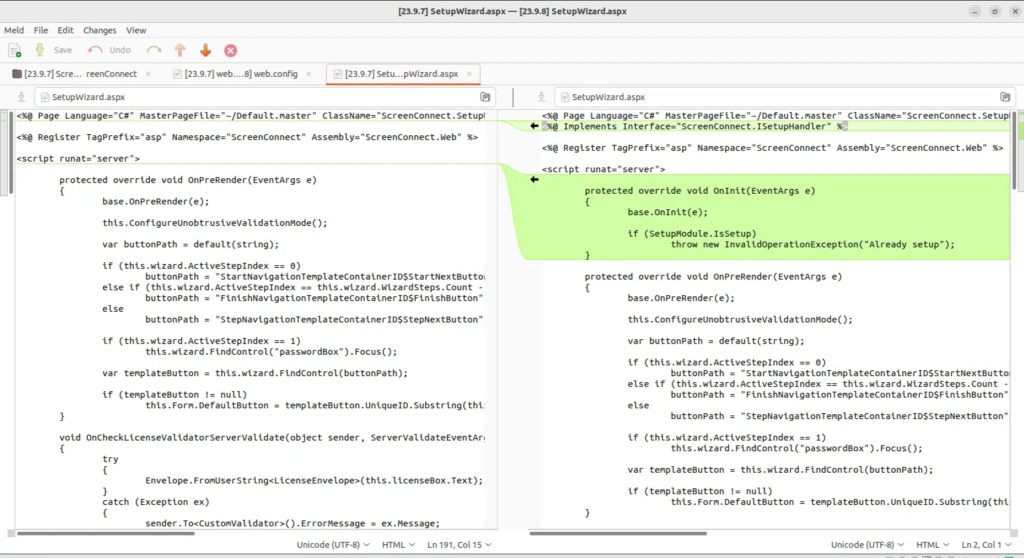
Code difference of SetupWizard.aspx (Source: horizon3.ai )
To address this, a new check was added to ensure that the setup wizard is only accessible, as shown in the above screenshot, if the instance of ScreenConnect has not been set up yet. Initially, this change seemed straightforward, but further investigation revealed a deeper problem. In the older versions of ScreenConnect, a particular part of the code was responsible for checking whether the request path matched "/SetupWizard.aspx" to determine if the setup wizard should be accessible. However, in the latest version, a more comprehensive check was implemented. This check determines whether the resolved HTTP handler (a component that handles incoming requests) implements a specific interface called ISetupHandler.
According to Huntress Labs, this change is crucial because it closes a potential loophole that could allow unauthorized access to the setup wizard. The loophole involves how .Net handles URL paths, where additional components can be added after a legitimate URL. This means that by adding "/literallyanything" to the end of "/SetupWizard.aspx", someone could gain access to the setup wizard even on an already configured system.
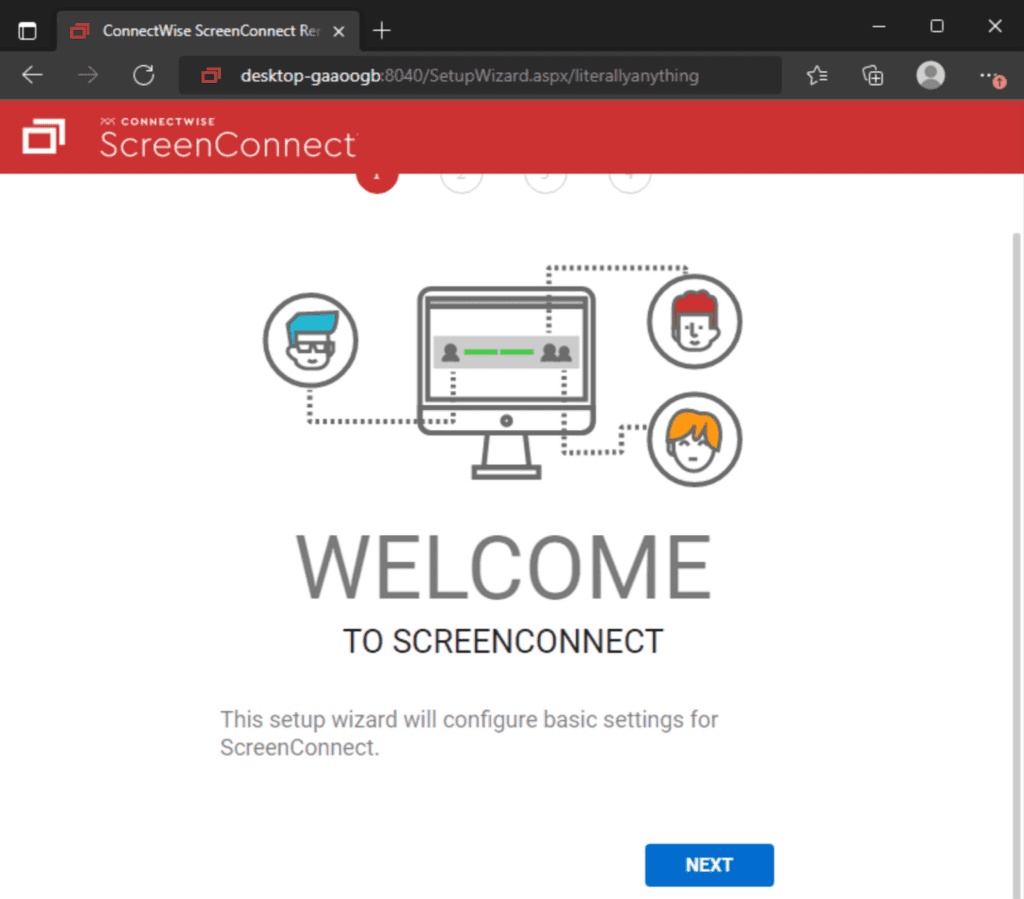
ScreenConnect Setup Wizard (Source: Huntress)
Once access to the setup wizard is gained, it becomes easy for an attacker to compromise the system further. They can overwrite the internal user database, effectively gaining administrative access. From there, they could create and upload a malicious ScreenConnect extension, allowing them to execute code on the system with high privileges.
In simpler terms, the update fixed a problem where the setup wizard could be accessed when it shouldn't be, and it also closed a loophole that could have allowed attackers to gain unauthorized access to the system and potentially take control of it.
CVE-2024-1708 - Path Traversal
According to Huntress Labs, The second vulnerability, CVE-2024-1708, mentioned in the ConnectWise ScreenConnect advisory, is related to a type of attack called ZipSlip. This vulnerability involves mishandling ZIP files, and as a consequence, it allows attackers to manipulate the contents of these files to execute malicious code.
This severe vulnerability could allow attackers to execute code on a system remotely. Still, it's important to note that exploiting it requires having administrative credentials and access to a specific feature called "Extensions" within ScreenConnect. However, when used conjugatively with CVE-2024-1709, it can have chaining effects. Any .aspx or .ashx files found in the root directory of C:\Program Files (x86)\ScreenConnect\App_Extensions\ are most likely malicious.
Detection with Logpoint Converged SIEM platform
LogSource Required
-
Windows
-
Windows Sysmon
-
Web Server, Proxy, Firewall
Generating logs of Windows
The detection rules rely on Windows Event ID 4663 for monitoring. This event ID is part of the File System Subcategory of the Object Access Auditing policy and requires specific configurations to be effective. This includes creating an appropriate System Access Control List (SACL) with audit rules specific to the directory of concern. Both successful and failed access attempts that monitor write attempts to the specified directory made by all users and groups may be audited. This proactive setup detects changes to files in the ScreenConnect directory in real-time. Manual configuration of these settings can be done via the graphical user interface (GUI) to ensure thorough auditing of any changes occurring within the ScreenConnect directory.
Alternatively, this PowerShell code by MHaggis can be used.
The detection also uses Windows Sysmon event id 11 (file created) events. To detect file modifications at the root of the App_Extensions directory as well as local user modifications in the ScreenConnect server, we must provide the path to monitor in event id 11. Add these to your Sysmon configuration files.
There are already sigma rules that we can leverage for ourselves to detect potential exploitation of these vulnerabilities. So, let's try to make Logpoint queries out of them.
ScreenConnect User Database Modification (Potential Activities associated with successful exploitation of CVE-2024-1709 )
It identifies changes made to the temporary XML user database file, signaling potential modifications to local users on the ScreenConnect server. These alterations are typically associated with exploiting the ScreenConnect Authentication Bypass vulnerability (CVE-2024-1709) in versions older than 23.9.8. However, such modifications might also occur during legitimate actions like adjusting local users or permissions.
It can also be detected from Windows security event ID 4663.
Potential Exploitation Attempt of ScreenConnect Authentication Bypass CVE-2024-1709
The most notable feature of this CVE is the attacker accessing the /SetupWizard.aspx/literally anything. Such patterns may indicate a Potential Exploitation Attempt of CVE-2024-1709. So, detecting such network connections initiated to this URL is crucial.
CVE-2024-1708 - ScreenConnect Path Traversal Exploitation
One of the notable characteristics of CVE-2024-1708 is the modifications of ASPX and ASHX files within the root of the App_Extensions directory. So, the modifications of such files can indicate exploitation attempts of CVE-2024-1708.
It can also be detected from Windows security event ID 4663.
Recommendations
ConnectWise highlights the essential need to respond quickly to reported vulnerabilities, adding, "On-premise partners are advised to immediately upgrade to the latest version of ScreenConnect to remediate against reported vulnerabilities." Whereas Cloud partners are remediated against both vulnerabilities reported on February 19. This suggestion emphasizes the need to take immediate action to protect the security and integrity of ScreenConnect servers for on-premise partners. Additionally, ConnectWise announces the release of ScreenConnect version 23.9.10.8817, which includes several changes targeted at improving the customer experience and resolving the identified vulnerabilities. ConnectWise has also announced the elimination of licensing restrictions, allowing partners not under maintenance to upgrade to the most recent version of ScreenConnect without restriction, demonstrating their commitment to facilitating access to vital security advancements for all partners.
Conclusion
In short, these vulnerabilities pose a significant danger since they allow attackers to execute malicious code on a machine remotely. However, it is important to emphasize that exploiting this vulnerability requires administrator privileges and access to certain aspects of the vulnerable software. While the vulnerability has been resolved with fixes or patches, it highlights the continual need for awareness and the need to use up-to-date software. This serves as a reminder to enterprises to continue prioritizing security measures and being proactive in mitigating possible risks, even after vulnerabilities have been resolved.