Fast Facts
-
Phishing is the most common form of cybercrime, with an estimated 3.4 billion spam emails sent every day.
-
Attackers spent $200-$1000 per day to carry out phishing campaigns.
-
Over the past six months, it is thought that users reported phishing attempts only 11.3% of the time.
-
Google blocks around 100 million phishing emails every day.

Humans are emotional beings and can be easily manipulated through emotions such as greed, fear, and desire. Attackers exploit these vulnerabilities through social engineering attacks, especially in email-based schemes. This kind of email-based attack has proliferated in recent years, making it time-consuming for analysts to investigate these suspicious emails. Our security researchers here at Logpoint have been working tirelessly to create playbooks that can aid organizations in performing investigations and responses. Gone are the days when analysts had to spend tens of hours collecting data, enriching IOC, investigating, and responding. The playbook can significantly reduce the average time between detection and response, bringing it to an all-time low.
Background
Phishing being common among social engineering, attackers often target large enterprises with spear phishing and whaling campaigns. With increased security awareness, such emails are generally reported to the security team. However, threat actors often incorporate new techniques making phishing difficult to detect and comprehend by users. The security team must act promptly to gather all the necessary data to conclude. It's as simple as clicking a button, and all the crucial pieces of evidence appear in the case.
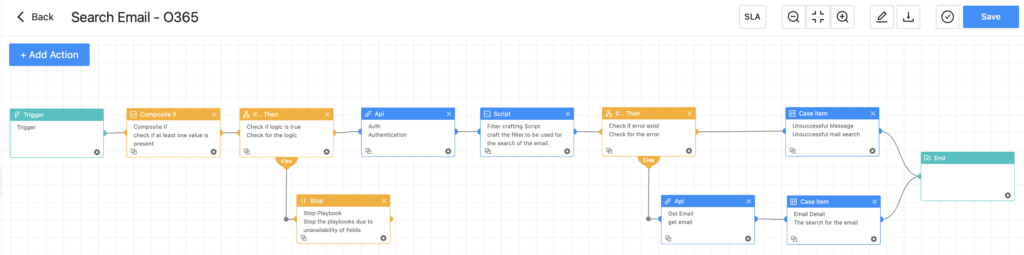
The playbook can be triggered either through incidents or executed manually. Below, we will discuss the manual execution and also showcase the playbook that can be triggered automatically.
Latest Phishing Attack Trend
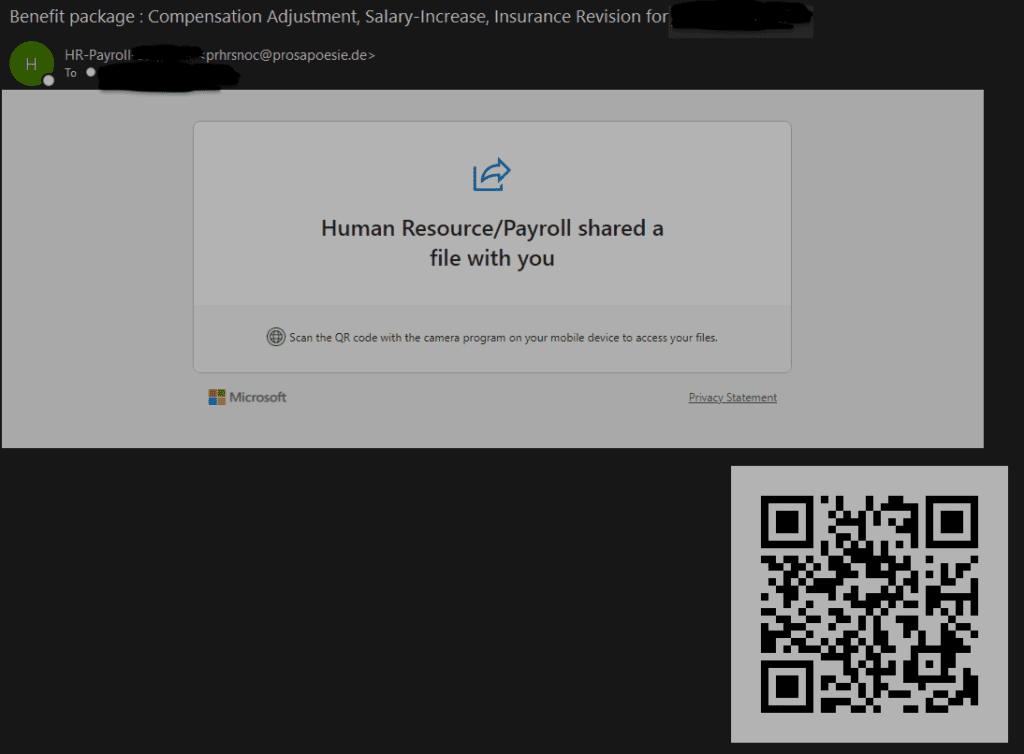
There has been a rise in phishing emails leveraging QR codes as a source of attack. Dubbed Quishing, it's very difficult to detect by the email security gateway and is easily passed to the user. While the phishing email content remains the same; showing some emergency issues or incidents and asking them to follow the link. However, in this case, the link has been replaced by a QR code that has to be scanned by a camera usually via a mobile device. It's a simple yet effective method to bypass the email security.
Investigation
To initiate the investigation, we require the message_id. This refers to the id field in the output provided by the O365. Please do not confuse it with internetMessageId. This can be accomplished using the playbook named "Search Email - O365", which accepts input such as sender, receiver, subject, userId, and searchby. This playbook searches within the user's inbox, using the parameters provided in the playbook input and outputs the message_id. This message_id is used to identify the email uniquely in the inbox.
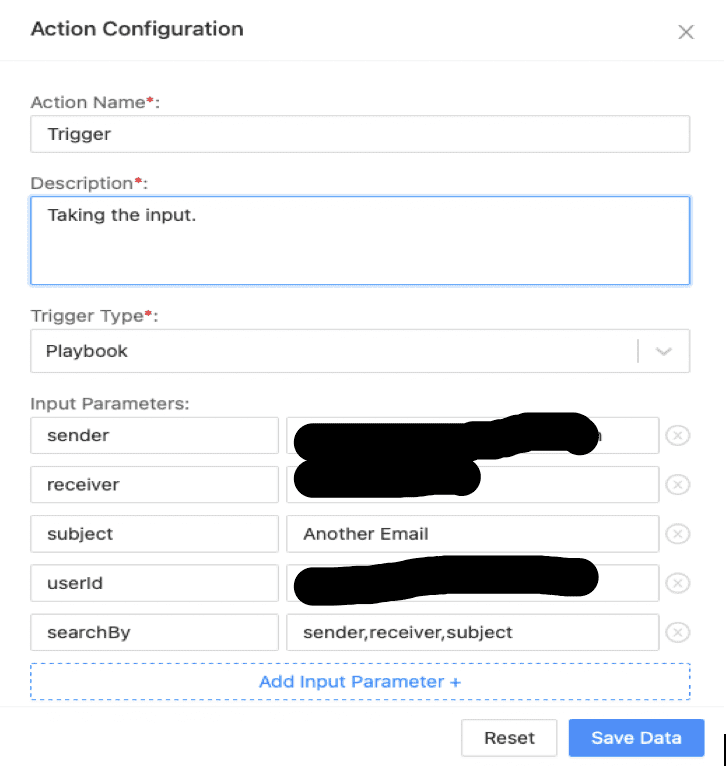
The input parameter sender, receiver, and subject are optional but needs at least one parameter to initiate the search. Providing all three narrows down to the exact email. After executing this playbook, the result can be found in the Cases. Clicking on "Show Json Data" will display all the results returned for the search.
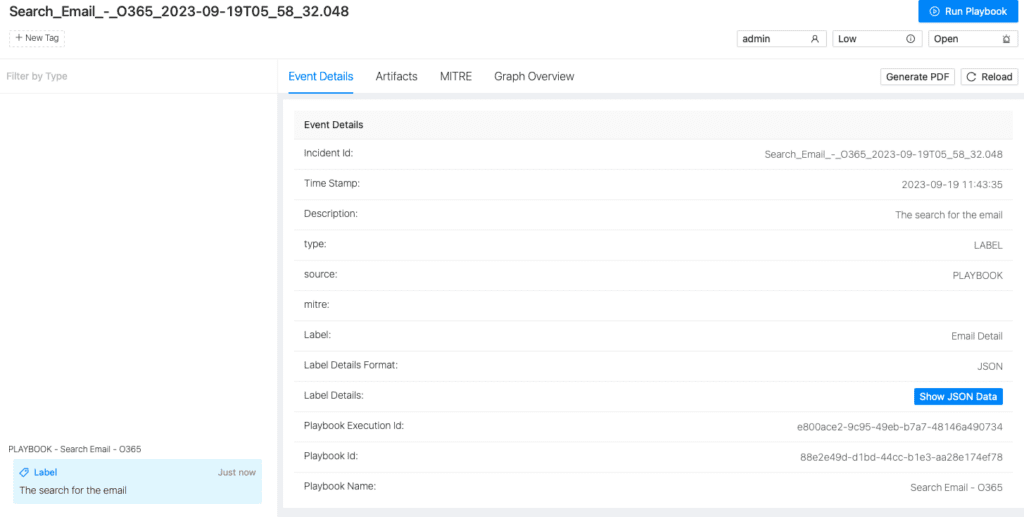
There could be multiple results depending on the input variable. We recommend manually reviewing these results and extracting the specific message ID. Clicking on the "Show JSON Data" instruction will show you details of the email consisting of the maximum information required, including the mail read status, that is needed for the investigation as shown below.
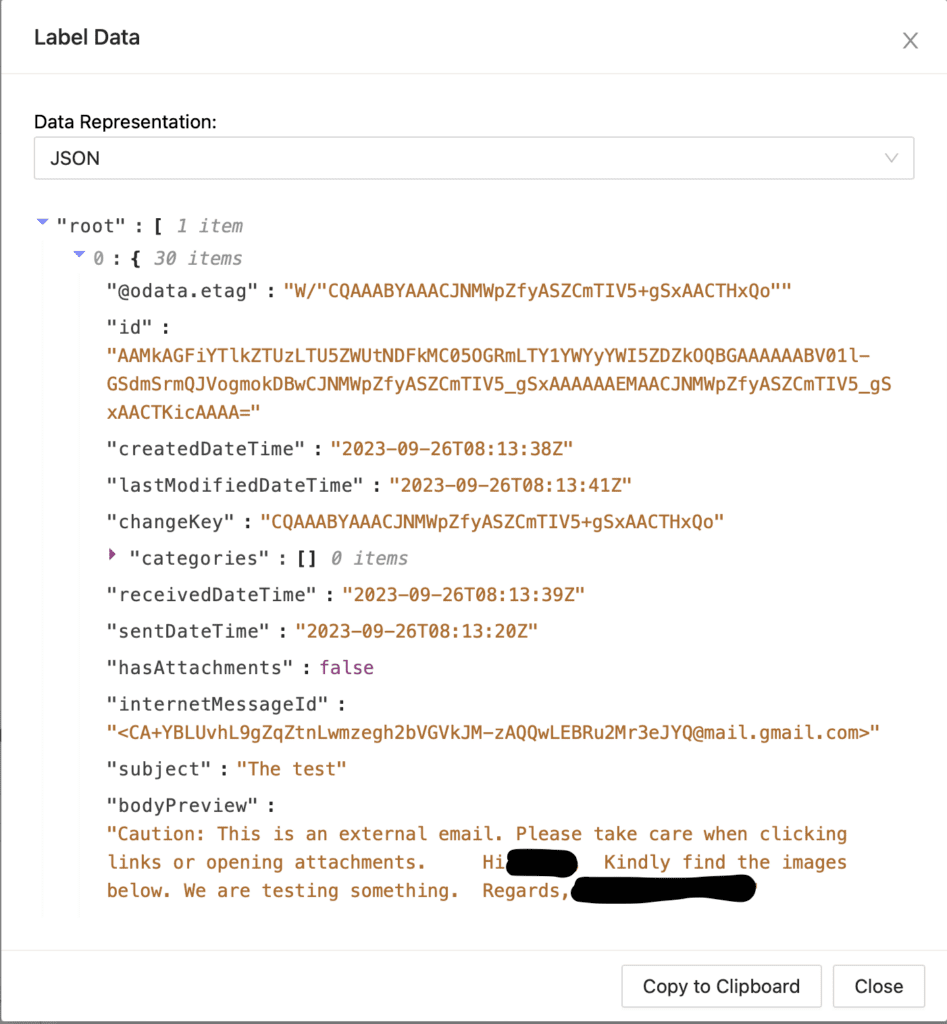
After this step, we can proceed with another playbook called "Email Forensics - Lite". In this playbook, we have two inputs: userId and message_id . This playbook offers a wide range of actions and scripts to extract as much detail as possible.
This playbook collects information such as sender IP details, URL details, and attachment details including QR data. These artifacts are being extracted from the message header, email body, and included attachments. In light of the recent Quishing attacks, we have included the QR decoder too, which would scan for the QR code in the attached image, and decode it. If the data contains a URL, it will be added as an artifact. The extracted IP and URL information is enriched using threat intelligence sources like VirusTotal and RecordedFuture.
Additionally, we also provide the email's body content and even the attached image so that analysts can directly view the email's contents and gain a new perspective.
Below we can see the case for each extracted URL/IP with its reputation and enrichment.
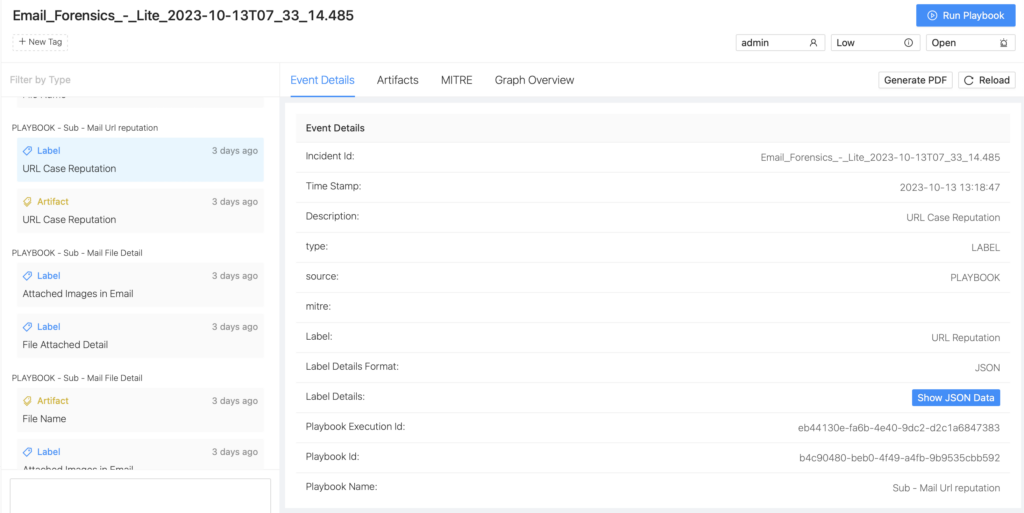
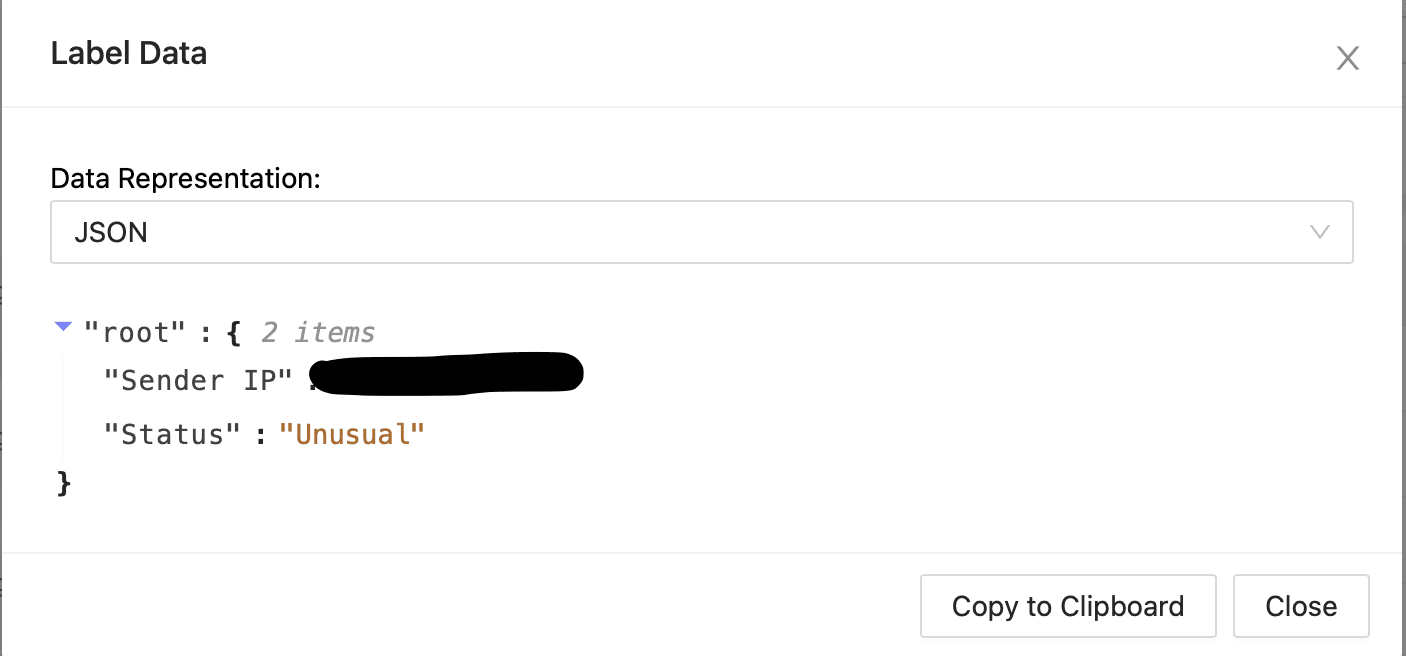
Clicking on the Show JSON data on URL Case Reputation and IP Case Reputation.
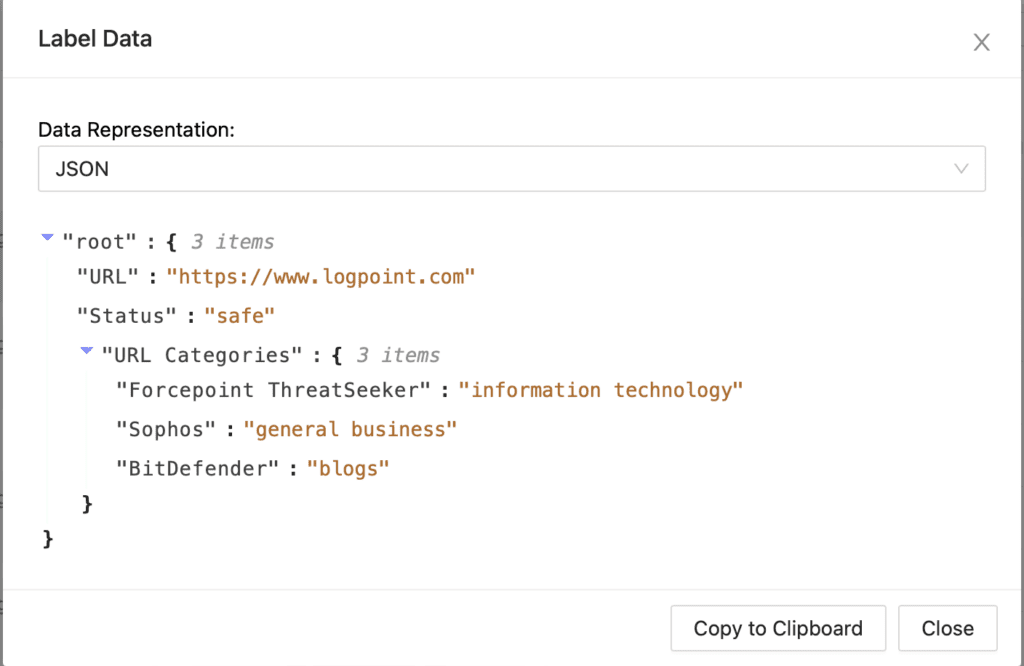
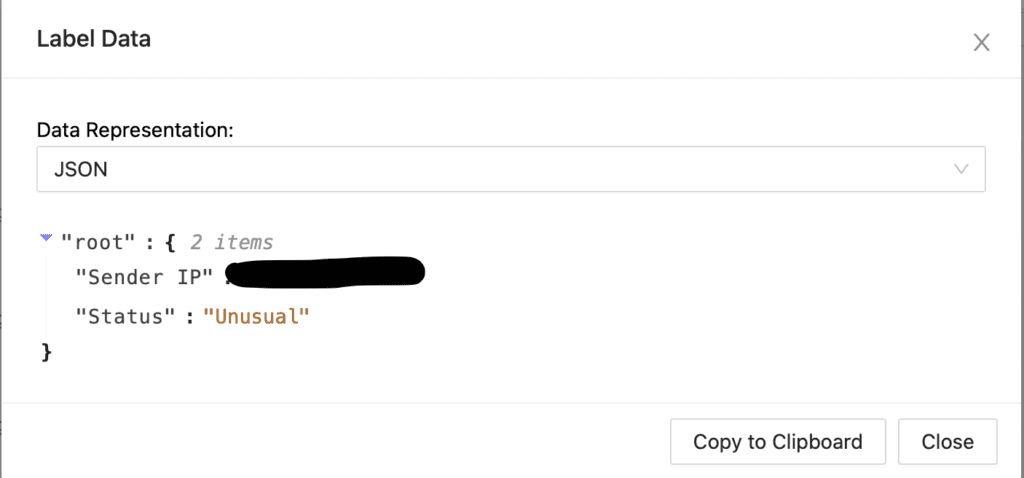
All these IP/URL and any other IOCs are added to the artifacts as shown below.
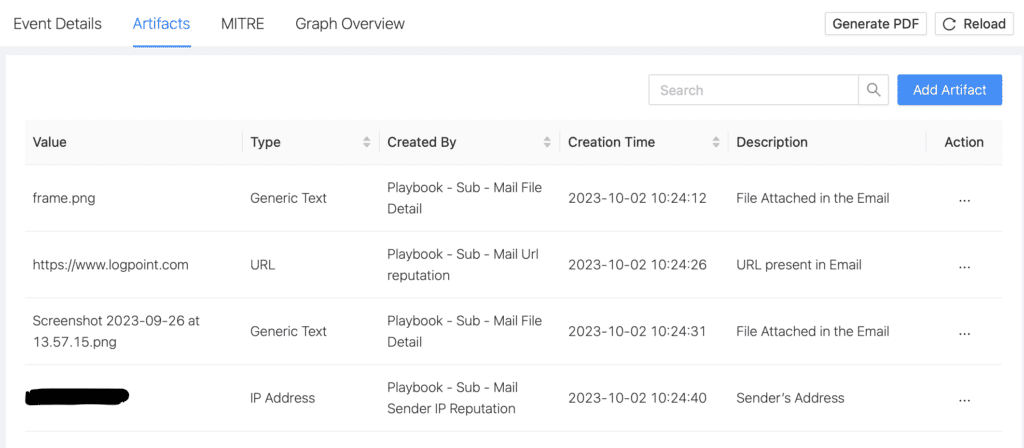
To make the investigation easy for the analyst, we have also included all the extra information that could be relevant.
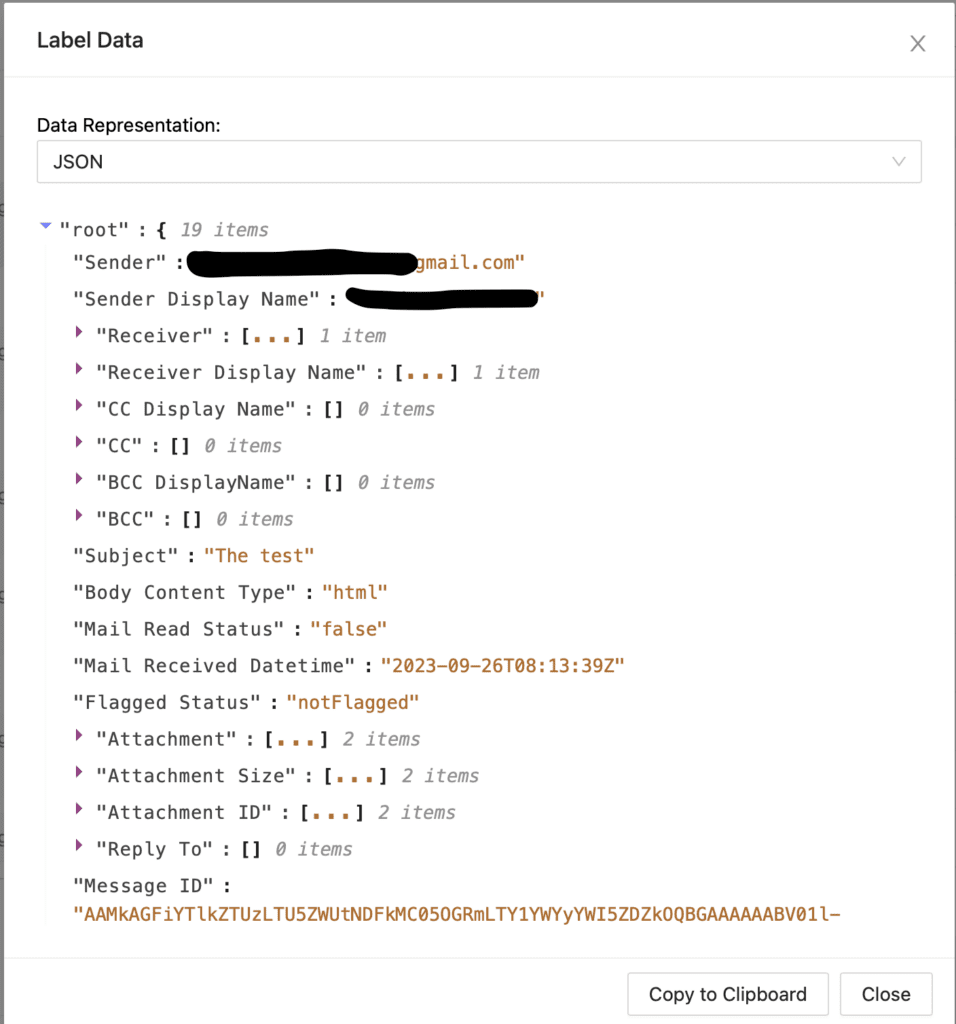
To make the investigation easier, the images that have been sent in the attachment will also be included in our case.
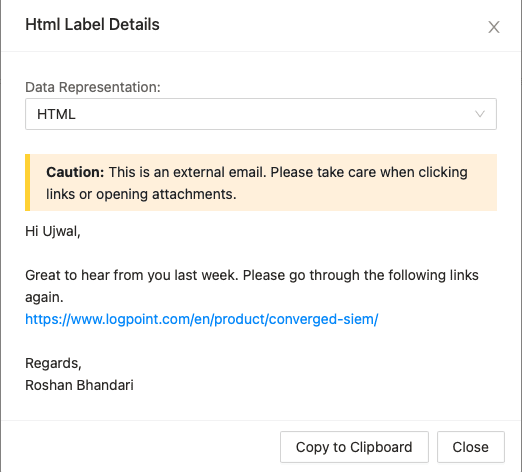
Clicking on the Show HTML Data:
The email body that was received. This would help the analyst to spot any obvious phishing/spam emails.
Response
With all this information, we can conclude the email's classification, whether it's malicious, phishing, or innocuous. If the email is determined to be unsafe, it should be deleted immediately. For this purpose, we have a playbook "Delete Email - O365," which requires the message_id (id) and userPrincipalName/userId as inputs to remove the email from the user's inbox.
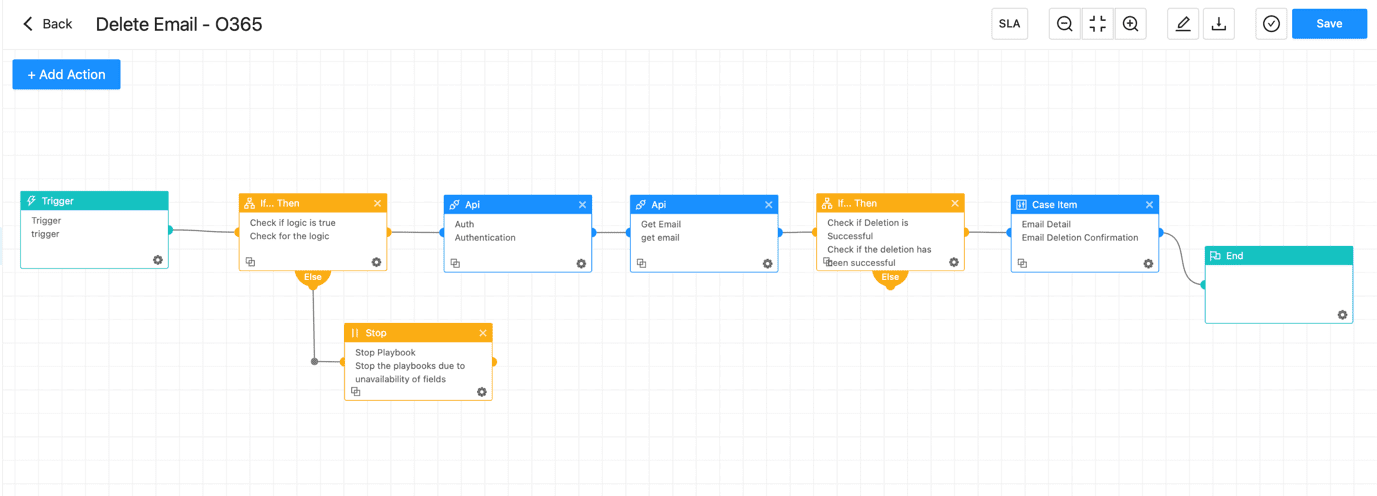
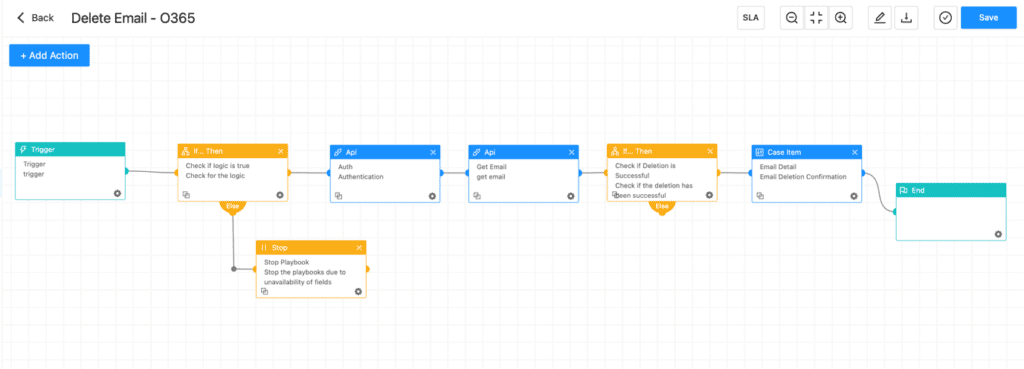
The case would be created when the email is deleted successfully.
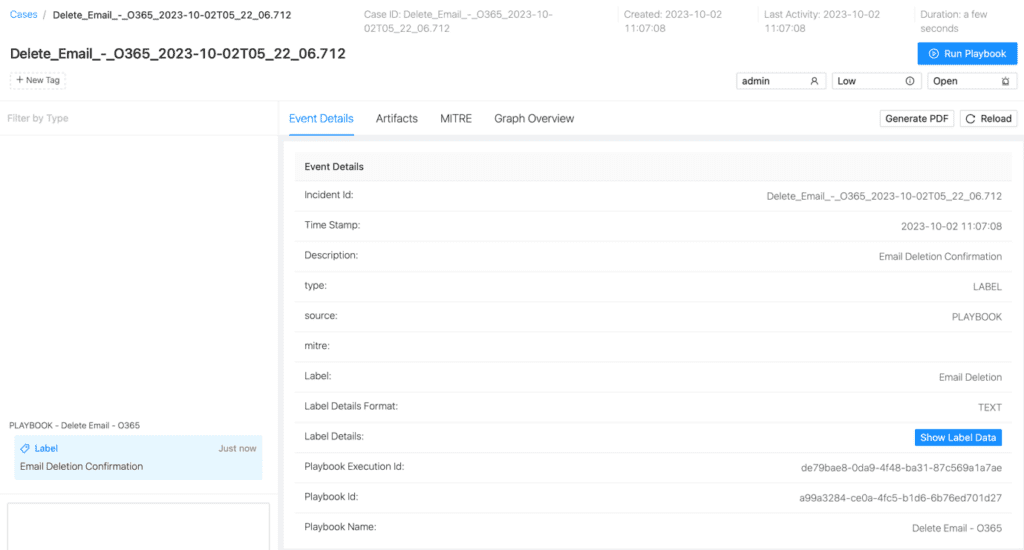
Conclusion
Using the above method, Converged SIEM allows us to efficiently gather email forensic data and take responses when necessary. However, if you believe that this process should be automated and streamlined without the need to move from one playbook to another manually, we have created a playbook "Email Investigation and Response". This playbook is designed to seamlessly collect data and initiate responses, although confirmation from an admin to delete the playbook is required.
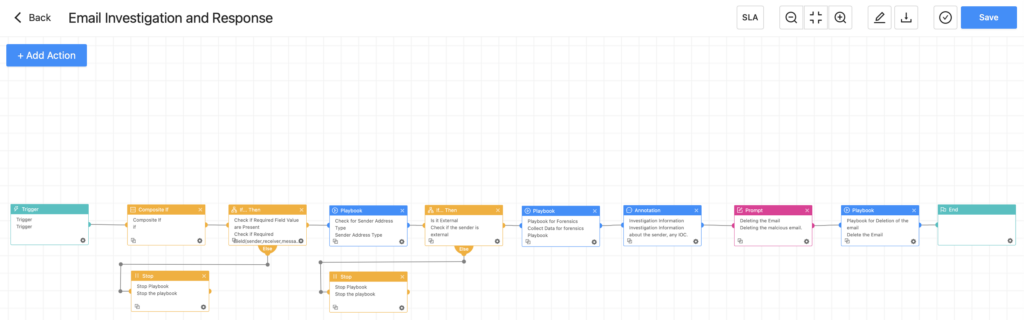
Recommendations
It's very difficult to mitigate these social engineering attacks, but they could be reduced drastically so here are some of the recommendations that could be embraced by organizations:
-
Ensure employees are aware of the latest threats and social engineering attacks.
-
Leverage the ML/AI-based security products.
-
Conduct online/offline training with simulated phishing attacks.
-
Encourage employees to report any security incidents and/or anomalies including suspicious emails.







