by Aida Grollov, Product Marketing Manager, Logpoint
Did you know that SAP customers generate 87% of the total global commerce?
SAP belongs, alongside other software systems, to the category of business-critical applications. By storing and processing critical data, these applications are vital to performing daily operations in almost every step of the value chain. As organizations’ abilities to use data to make decisions are becoming the main differentiating factor, a system that unifies and provides a central repository, such as SAP, is more crucial than ever.
Essential to business continuity, business-critical applications are the digital hearts of organizations. Just as a simple heart failure or a cardiac arrest can have fatal implications for us humans, organizations will suffer the same existential threat, if their digital hearts get compromised. Even a smaller disruption to an application might severely impact the daily operations and lead to significant financial losses, productivity deficiencies and cause unprecedented damage to the brand authority and customer trust.
The role of business-critical applications in business management
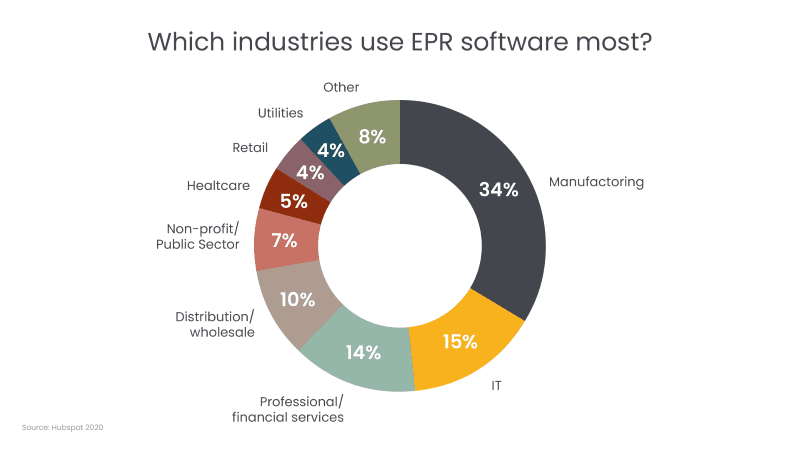
Business criticality is relative. To reflect the differing needs of organizations, a wide array of applications are critical. For example, a material management module is essential for a production plant but completely irrelevant for a software company. One business-critical application that is widely used across different industries, is enterprise planning systems (ERPs). The ERP market is estimated to reach $117.09 billion by 2030 and is widely used by different sectors, including manufacturing, critical infrastructure, and the public sector. Being central to business operations, 27% of an organization’s employees use ERP systems regularly to perform their daily tasks.
Business-critical applications are increasingly under attack
Containing crown jewels of businesses, business-critical applications make an extremely attractive target for organized cybercrime. For hackers looking for big money, breaking into a business-critical application is like hitting a jackpot.
Today, our security measures cannot keep up with the pace of development in businesses. 80% of business leaders acknowledge that digitally fueled innovation is being introduced faster than organizations’ abilities to secure it against cyberattacks.
A rise in frequency and cost
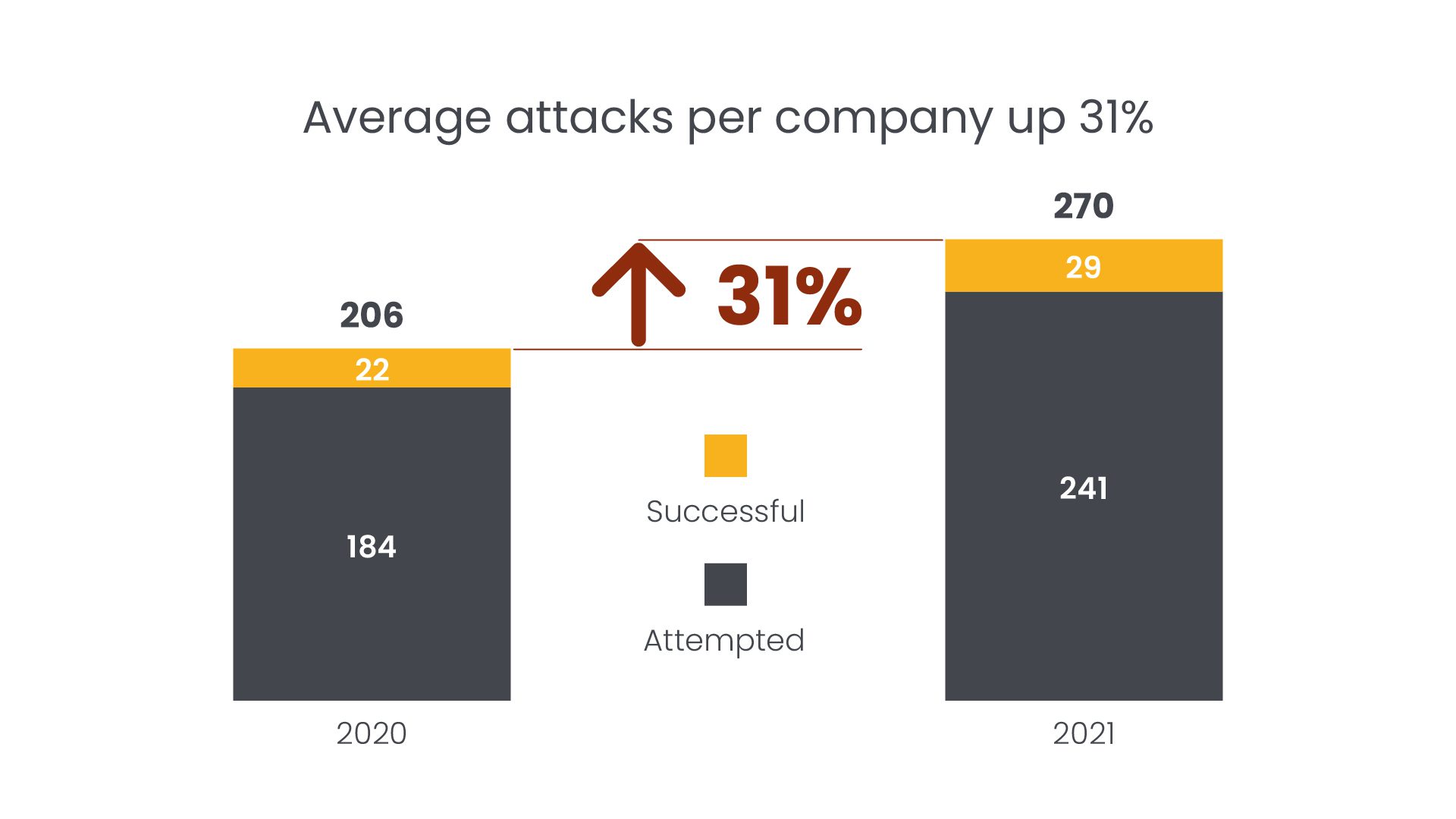
Even a pandemic cannot stop cybercriminals. While the world was facing unpreceded uncertainties, cybercriminals exploited these new vulnerabilities to create a breeding ground for new attacks. In 2021, companies have on average suffered from 270 attacks (unauthorized access of data, applications, services, networks, or devices) – a rise of 31% in just one year. This increase is caused by the widespread migration to cloud, outsourcing of development, and the fact that companies did not implement sufficient security measures during the pandemic¹. In 17,5% of the breaches in 2021², remote work was a factor.
The average cost of a data breach has also increased significantly during the pandemic, rising from $3.86 million in 2020 to $4.24 million in 2021³. This is the highest total cost ever recorded in the 17 years IBM has been publishing its report on data breaches. Unfortunately, the world’s leading research institute on the cyber economy, Cybersecurity Ventures, is expecting this trend to continue. According to their estimations, cybercrime costs will grow by 15% over the next three years, reaching $10.5 trillion annually by 2025.
“If it were measured as a country, then cybercrime — which is predicted to inflict damages totaling $6 trillion USD globally in 2021 — would be the world’s third-largest economy after the U.S. and China.”
Fragmentation in cyberthreats
The nature of cyberthreats is becoming more fragmented, extending from individual hacker groups to state-orchestrated attacks. As data is becoming the new natural resource, the face of modern warfare is changing. Instead of conventional weapons, some states are building a new type of arsenal consisting of bits and bytes. Engaging in sabotage and espionage, states are hacking into business-critical applications to obtain data. This information is then used to undermine the market confidence in order to promote the competitiveness of their country’s business.
Another threat vector comes from within and detecting it is even more difficult. An internal threat occurs when an insider within a company maliciously or unintentionally misuses their access to negatively affect or harm the business. Insider threats are among the most common causes of data breaches worldwide. According to the Ponemon Institute, insider threat incidents have risen by 44% over the past two years, costing $15.38 million per incident.
Despite the aggravation of cyber threats both in volume and cost, there is fortunately much you can do to secure your business operations from being hacked.
Organizations can mitigate threats quicker by incorporating BCAs with IT security
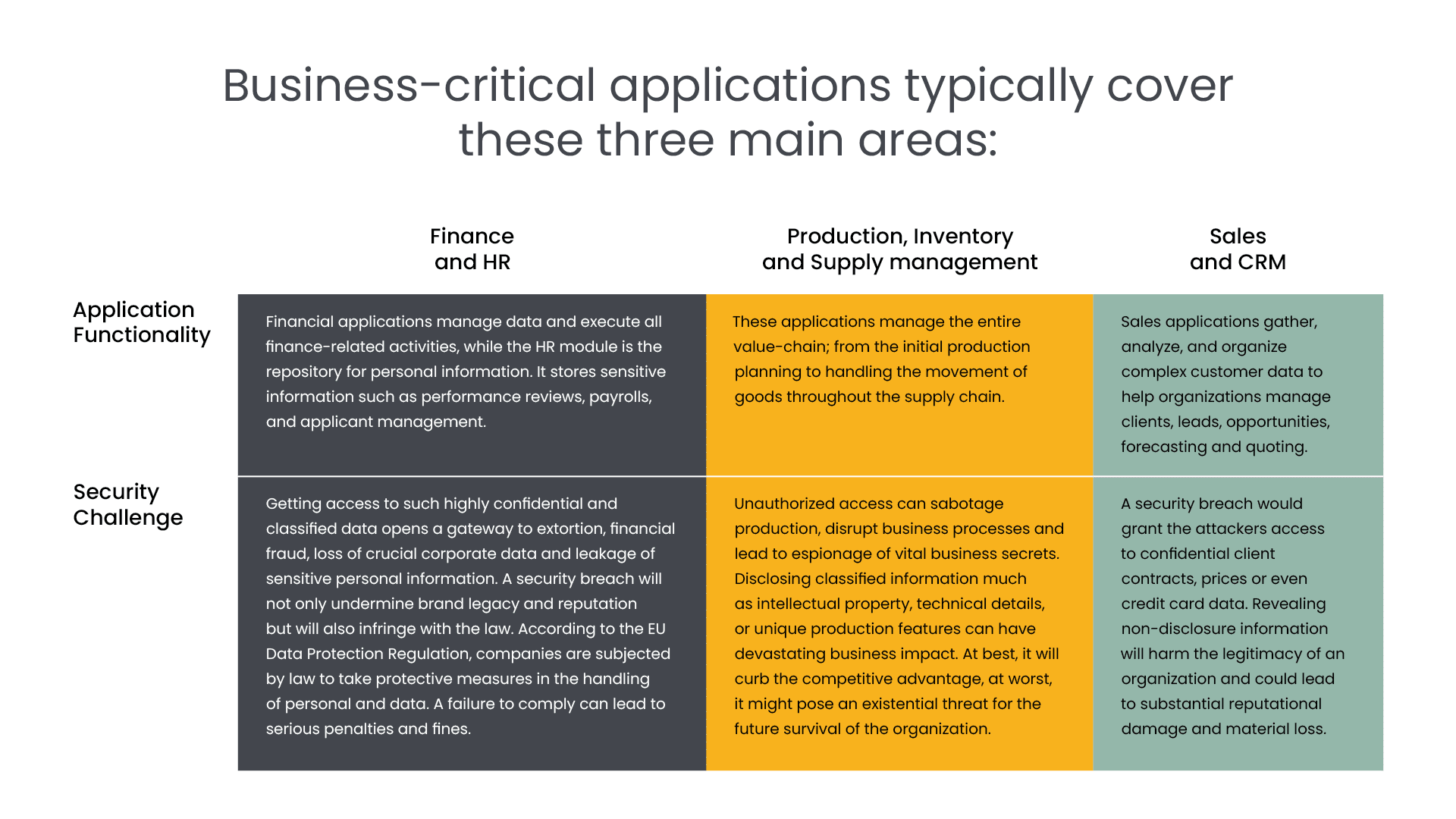
Being tied to almost every aspect of a business, the environment of business-critical applications is intricate and complex. It consists of a wide array of elements, including process and workflow, master data and data warehouses, an underlying computational infrastructure, a large storage network – and dozens, if not hundreds of interfaces and integration points with other IT applications inside and outside of the organization. Understanding the various dependencies between systems is essential because each interconnection may be a vulnerability. Unfortunately, business-critical applications are today monitored separately from the remaining IT infrastructure which prohibits the necessary correlation of data. This leaves a serious security gap, rendering companies vulnerable to attacks.
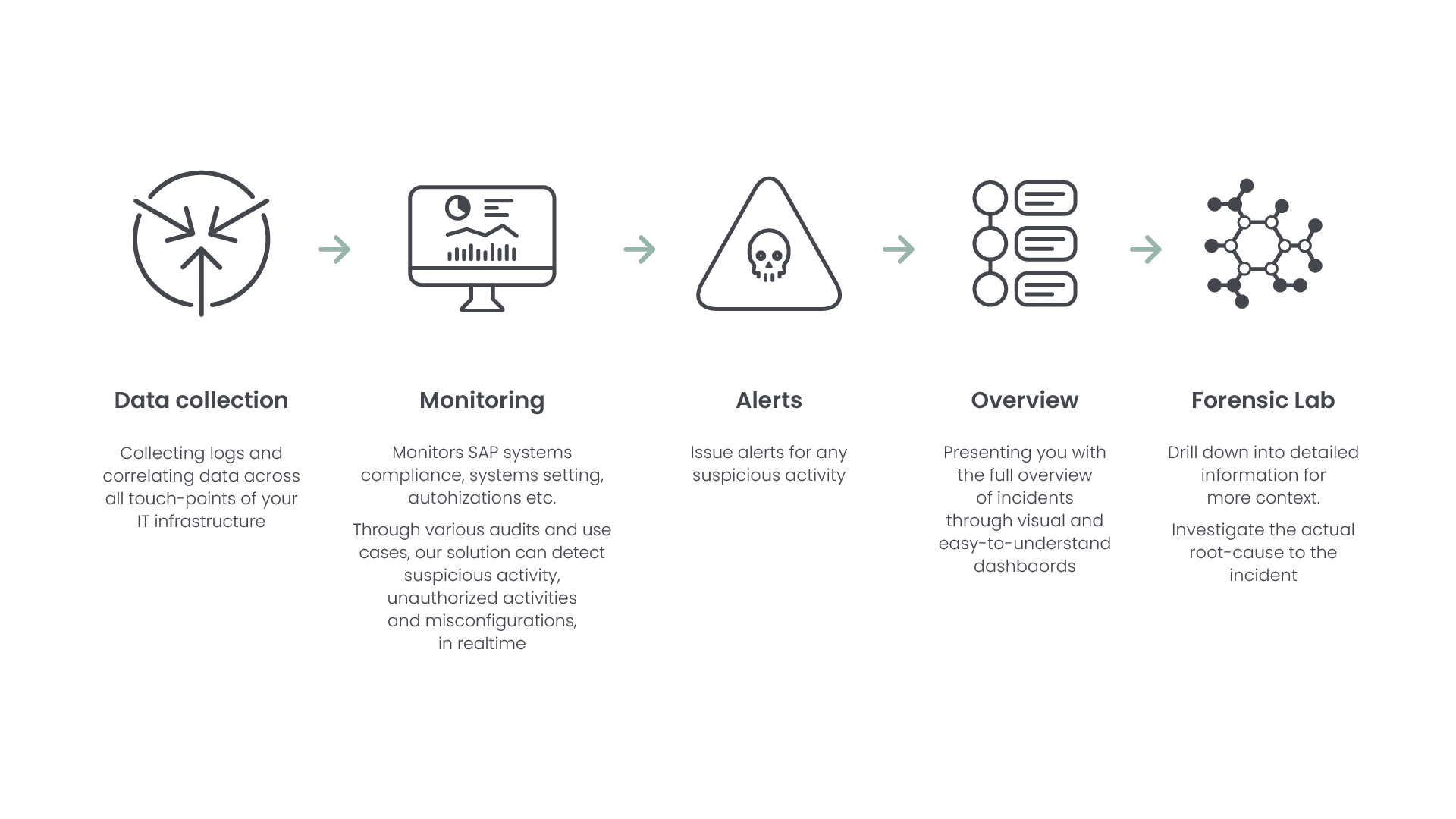
In Logpoint we approach things differently. We break down the siloes and integrate business-critical applications as part of the central monitoring solution. By correlating SAP data with infrastructure data, we monitor events across your entire landscape. This holistic approach strengthens threat detection and enables you to quickly respond to incidents across your various applications. We present you with complete insight, so you effectively can respond to threats and protect your SAP system from unnecessary damage.
So, how do we do it?
Curious to learn more, see how Logpoint helps protect business-critical applications.
Further sources:
¹Hype Cycle for Application Security, 2021, Gartner.
²IBM, “Cost of a Data Breach Report 2021,” July 2021.
³IBM, “Cost of a Data Breach Report 2021,” July 2021.