By Christian Have, CPO
Many organizations face challenges of securing and monitoring endpoints beyond antimalware and software/configuration management. As a key point to increase the security posture and capability to act timely to threats and potential breaches, a shift is now taking place where collecting logs from endpoints is the next step.
The challenge with classical deployments is that an agent is required on each endpoint. With the stability issues, ensuring that all endpoints are updated with the correct agent etc. some choose to use agentless WMI to fetch the events. This is moderately better, but requires the SIEM to know which endpoints to query. With the dynamic state of enterprise networks today, that option does not work.
Enter Microsoft Event Subscription (MES). With MES you can configure forwarders and collectors of event data. This means that all endpoints in the network can be configured to forward some or all eventlog contents to a centralized Event Subscription Collector. All functionality is built-in and supported in Windows and has seen a maturing since 2008R2. The overhead of MES on endpoints and collector servers is low and the complexity in configuring MES is very easy. MES can be configured via GPOs or PowerShell and eliminates the need to know which endpoints exists in advance and eliminates the need to query all endpoints via WMI.
Solution
The solution involves a couple of steps:
- Configure an event collector to receive forwarded data
- Configure the GPO on the endpoints
- Configuring the endpoints to forward event data to an event collector
- Install an agent on the event collector to forward data into LogPoint
- Configure LogPoint to receive the data
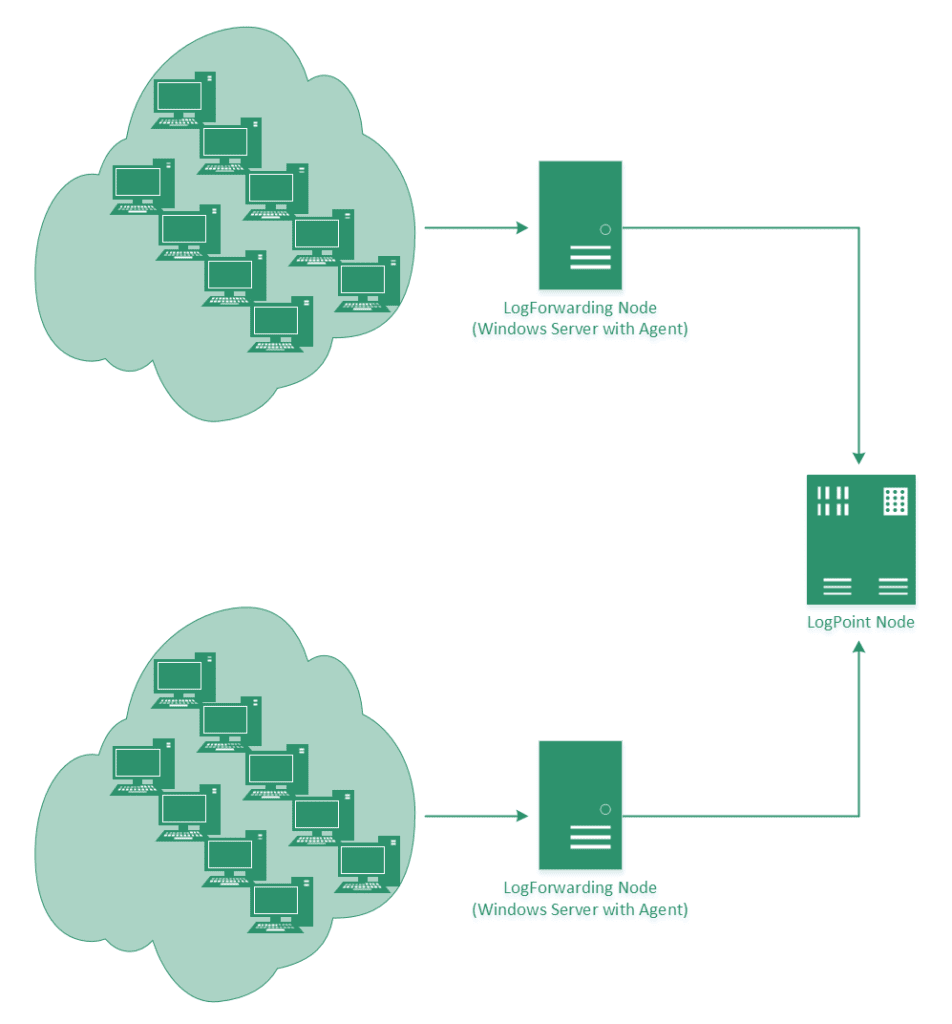
Illustration: Distributed endpoint event collection
Configuring the collector
In the Windows Event Forwarding architecture, the subscription definition is held and maintained on the Collector in order to reduce the number of touch-points in case a subscription needs to be created or modified. Creating the subscription is accomplished through the new Event Viewer user interface by selecting the ‘Create Subscription’ action when the ‘Subscriptions’ branch is highlighted. The Subscription may also be created via the “WECUTIL” command-line utility.
Note: Both Windows Vista and Windows Server 2008 can be event collectors (this feature is not supported for down-level). Although there are no built-in limitations when Vista is a collector, Server 2008 will scale much better in high volume scenarios.
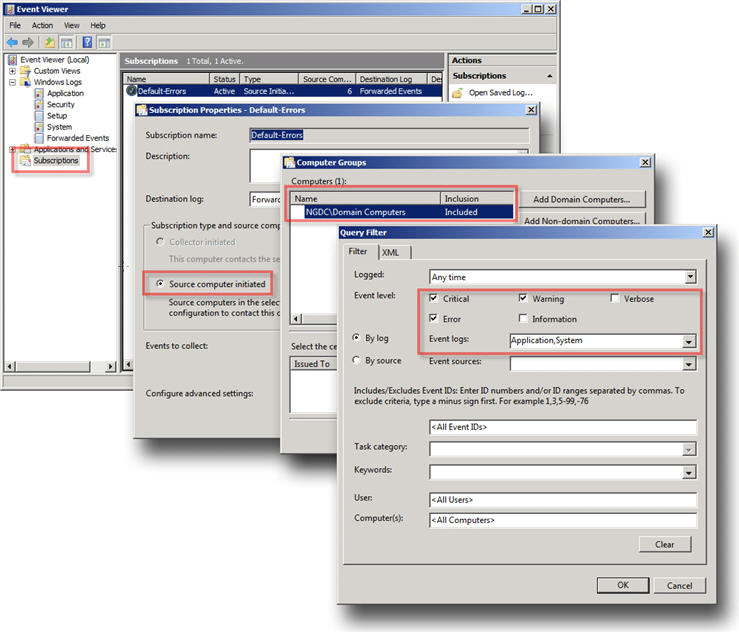
lthough the above subscription is configured to leverage Group Policy, the subscription can be configured in a stand-alone mode (see the “Collector Initiated” option). In addition, this subscription is designed to gather all events from the “Application” and “System” logs that have a level of “Critical”, “Error”, or “Warning”. This event scope can be expanded to gather all events from these logs or even add additional logs (like the “Security” log).
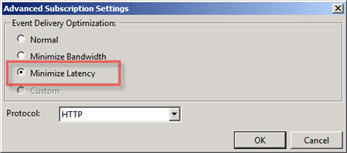
Lastly, the subscription is configured to forward events as quickly as possible with the advanced settings delivery option of “Minimize Latency”. The default setting of “Normal” would only forward events every 15 minutes (which may be more desirable depending the the Collector and Source Computer resources).
If Group Policy is not being used, configure the “Subscription type” to be “Collector Initiated”. In this case Source Computers will need to be manually added to the Subscription either through the Subscription configuration or the “WECUTIL” command-line utility (which can also be scripted using PowerShell, but that’s another topic).
Note: In cases where there Source Computer is generating a large volume of forwarded events (e.g. Security events from a Domain Controller), use WECUTIL on the collector to disable event rendering for the subscription. The task of pre-rendering an event on the source computer can be CPU intensive for a large number of events.
Configure GPO on Endpoints
Group Policy can be used to enable and configure Windows Remote Management (WinRM or WS-Man) on the Source Computers. WinRM is required by Windows Event Forwarding as WS-Man is the protocol used by WS-Eventing. The following shows the Group Policy branch locations for configuring both WinRM and Event Forwarding:
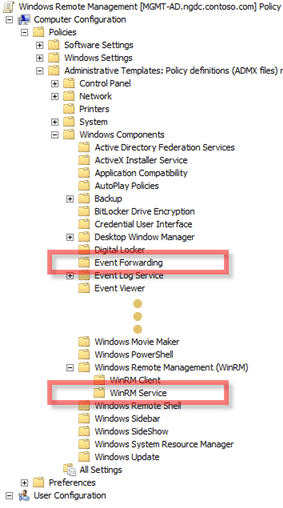
The following GP setting will enable WinRM on the client as well as configure a Listener that will accept packets from ANY source.
Note: This Listener configuration should only be used in a trusted network environment. If the environment is not trusted (like the Internet), then configure only specific IP Addresses or ranges in the IPv4 and IPv6 filters.
Configure Endpoints
As with WinRM, Group Policy can be used to configure Source Computers (Clients) to forward events to a collector (or set of collectors). The policy is very simple. It merely tells the Source Computer to contact a specific FQDN (Fully Qualified Domain Name) or IP Address and request subscription specifics. All of the other subscription details are held on the Collector.
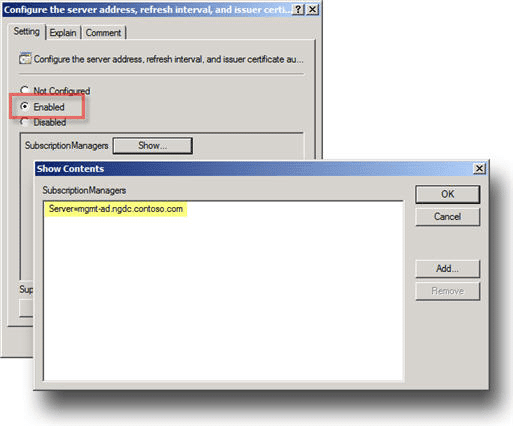
If Group Policy is not being used, then there is nothing to do here as the “Collector Initiated” Subscription will proactively reach out to the Source Computer.






