Advanced cyber threat detection
What are advanced cyber threats?
Advanced cyber threats are more targeted than other cybersecurity threats. They may focus on a certain industry, sector or geography and sometimes even individual organizations. Anti-malware, other standard controls and endpoint solutions can fail to block or prevent these attacks. More effort is required for detecting cyber threats – but doing so is a must in order to prevent data leakage. Criminals only need to find a single vulnerability to carry out an attack.

Ideally, organizations want to stop attackers during the reconnaissance, exploitation or lateral movement phases of an attack.
- Reconnaissance refers to target selection and research and includes information-gathering from:
- Social networking websites
- Internet search engines
- Other sources that profile the targeted organization
- Data exploitation refers to behavior indicating a successful exploit of a vulnerability
- Lateral movement is a term used to describe penetration activities by intruders as they spread throughout a network.
It’s important to detect attackers with advanced cyber threat detection during these phases because once data has left the network, the threat hunt turns into a forensics case.
Logpoint for advanced cyber threat detection
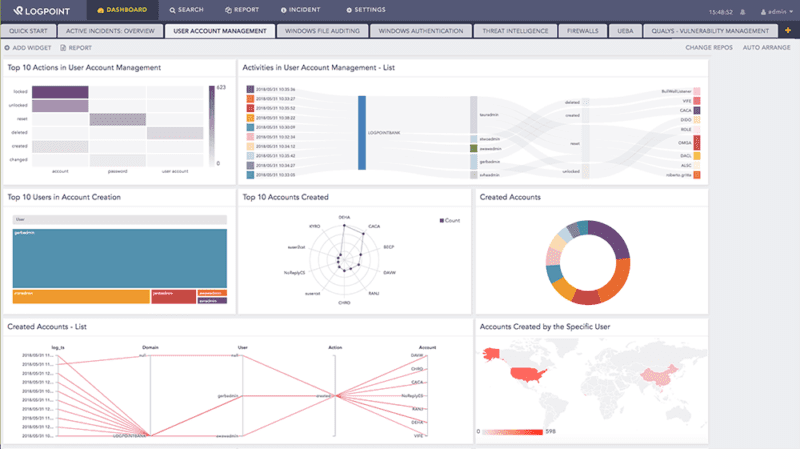
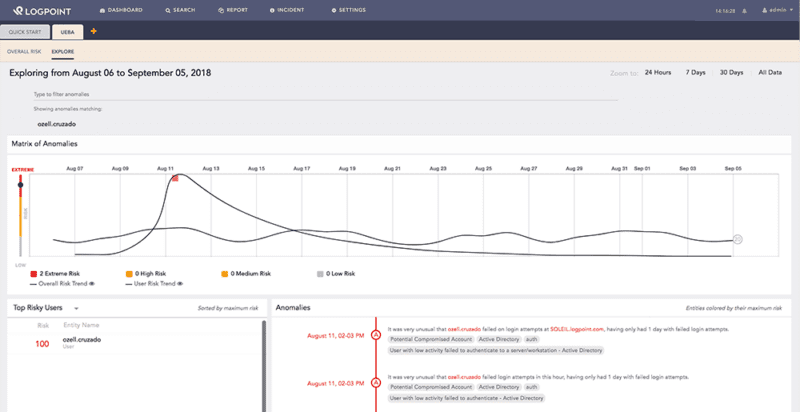
Logpoint makes use of several approaches to combat advanced cyber threats and includes analytics in the form of alert rules, dashboards and data mappings. Using Logpoint’s threat intelligence application, it’s possible for analysts to devise correlation rules and employ machine learning and data exploration to observe unusual patterns of activity across devices for advanced cyber threat detection.
Threat hunting
Logpoint also uses threat intelligence feeds to automate some aspects of threat hunting. Threat intelligence feeds are used at the time of ingest, so that when data comes to us, it’s evaluated against all known configured threat intelligence feeds.
Threat intelligence is also used at the time of analysis, allowing analysts to submit any amount of historical data to be evaluated against most recent threat intelligence feeds, to see if they match any new knowledge about attacks. These correlated and evaluated alerts can then be pushed to a third party incident response tool for orchestration and remediation.
Logpoint cyber threat detection in action
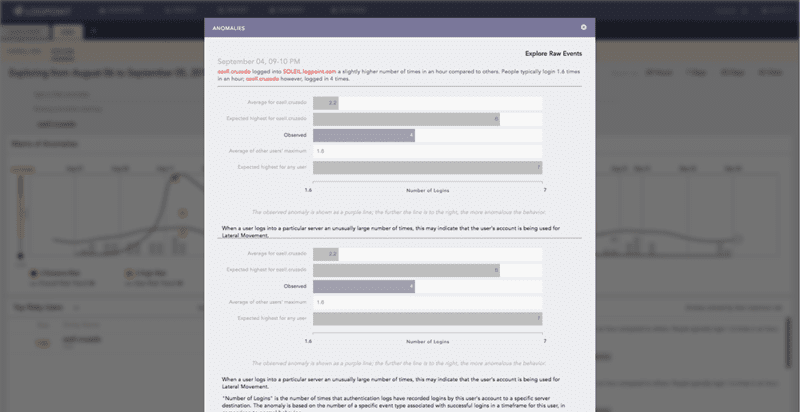
For example, if a machine in engineering starts communicating with workstations and servers in marketing for the first time ever, then starts copying data back to the local machine, you need to know about it. Logpoint will issue an alert, letting you know there’s a case of lateral movement and reconnaissance. With Logpoint’s Modern SIEM & SOAR solution and user entity and behavior analytics (UEBA) functions, your company is able to detect that:
- This activity represents unusual network access patterns
- The user isn’t part of the group that the server was hosted on
- Workstations are never supposed to connect directly to workstations outside their own group
- An unusual file access pattern was observed on the marketing machine
- The amount of data transferred to engineering didn’t fit previous observed models