BCS for SuccessFactors
Meet the compliance regulations – Keep your sensitive data in SAP SuccessFactors safe from misuse.
SAP SuccessFactors is a depository for some of an organization’s most sensitive and regulated data. Safeguarding the confidentiality of employee information by ensuring that only authorized users can access and modify it is essential for avoiding fraud, breaches, costly compliance violations and brand integrity infringements. Get more information below.

Why BCS for SuccessFactors?
To protect the privacy and integrity of critical data, BCS for SuccessFactors continually extracts, monitors, cross-correlates, and analyzes relevant logs to deliver comprehensive, landscape-wide threat visibility, in real-time.
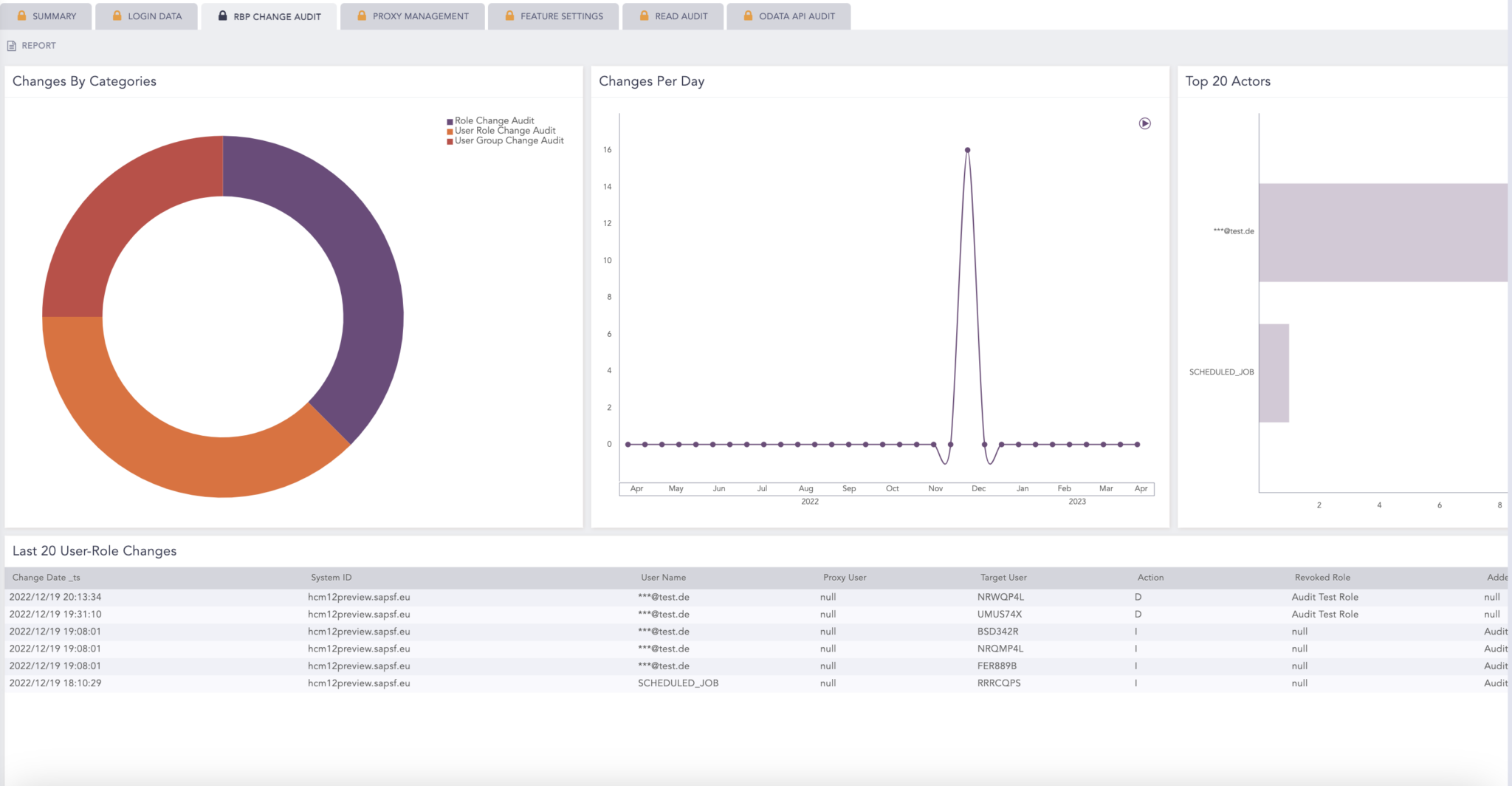
Security parameters covered by BCS for SuccessFactors
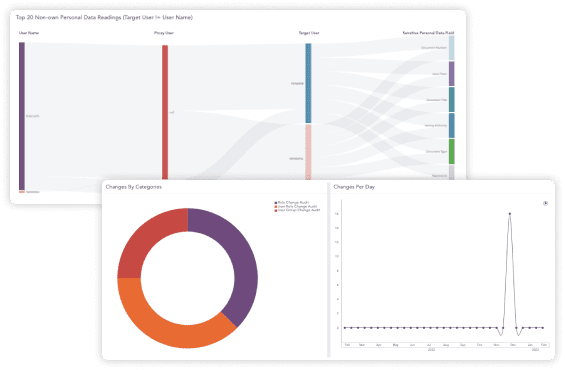
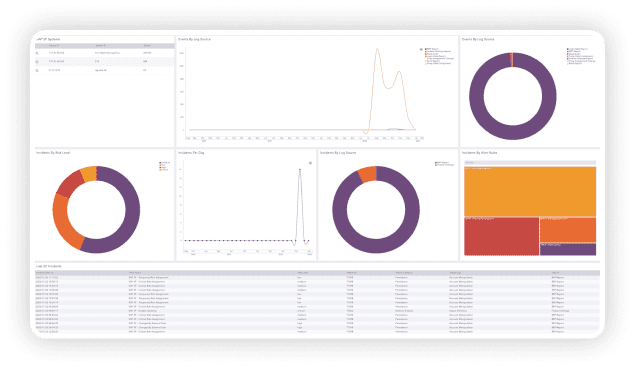
Easy overview with a single pane of glass
Full threat visibility delivered at a glance. With actionable dashboards, you can monitor key metrics, gain contextualized insight and take a deep dive into critical areas that need further investigations. Operating from a single point of truth in a unified overview, we help security teams easily navigate data and effectively distinguish potential risks from critical vulnerabilities that could be exploited.
Time-to-value – Expedited
No need to waste time on complex installations. BCS for SuccessFactors is easily deployed, facilitating a quick roll-out and delivering full monitoring value instantly. On top of that, it works for every industry and integrates with any SIEM.
Use Case:
No overview of admin users
A company accidently assigned ‘admin user’ roles to almost everyone, granting them excessive privileges to access sensitive data, modify and delete HR master data, allocate roles, and permissions to other users, etc. Due to the lacking visibility into SF, this went unnoticed, posing a huge security and compliance risk and threatening the HR operations.
Our solution:
With Change Audit Log, we are monitoring all changes to a business object. This entails any changes to user roles, role-based permissions, or alternations to proxy roles or assignments. Any changes will be flagged, and a comprehensive overview provided, covering the date of the changes, mapping the actions taken, and identifying the user authorizing the changes.