By Anish Bogati, Logpoint Global Services and Security Research
Contents
TL;DR
Emotet, aka Geodo or Heodo, is a modular malware variant that was initially used as banking malware.
At present Emotet is used as a dropper, which means it downloads other malware like IcedID, QakBOT, and TrickBot.
Emotet was first detected in June 2014 and primarily targeted the banking sector.
Even though the authorities had taken down the Emotet operation, it keeps on coming back with upgraded features and mechanisms to avoid defense.
- Outlook Scraper: The module scrapes names and email addresses from the victim’s Outlook accounts by using the messaging API.
- MailPass View: Software developed by NirSoft to reveal the passwords and other account details from email clients like Outlook, Mozilla Thunderbird, and Gmail.
Report:
** Get in-depth research and analysis, insight, plus hints and tips, on how to detect, manage, and respond to the Emotet threat in the main blog. Playbooks can be created and implemented by the Global Services team, get in touch.
Head to the contents and click each section for quick navigation.
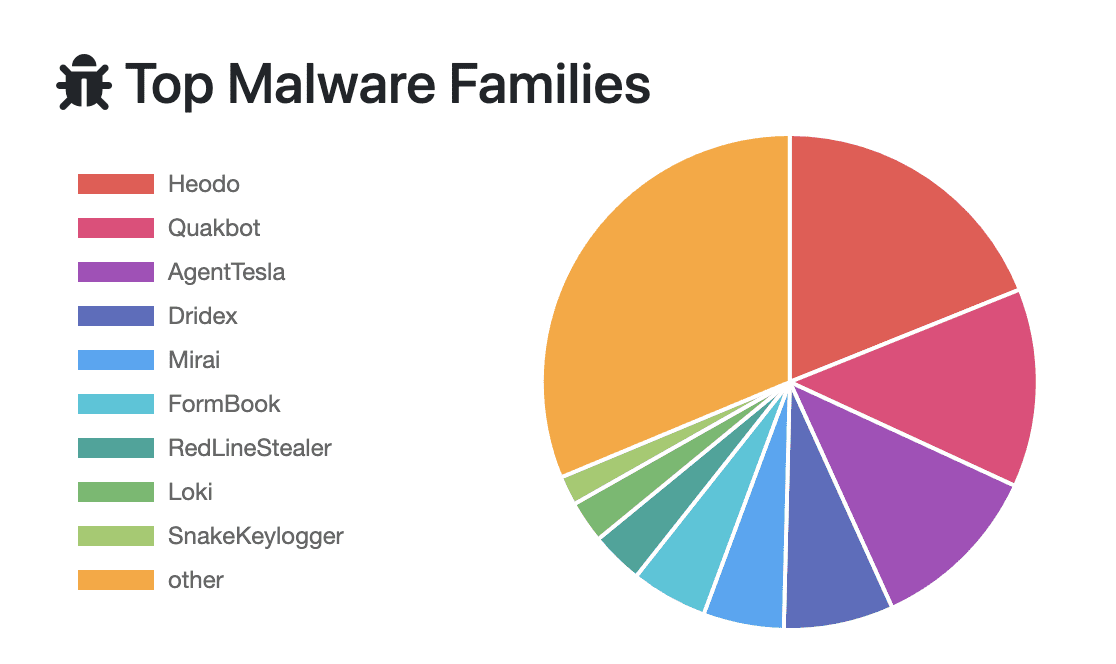
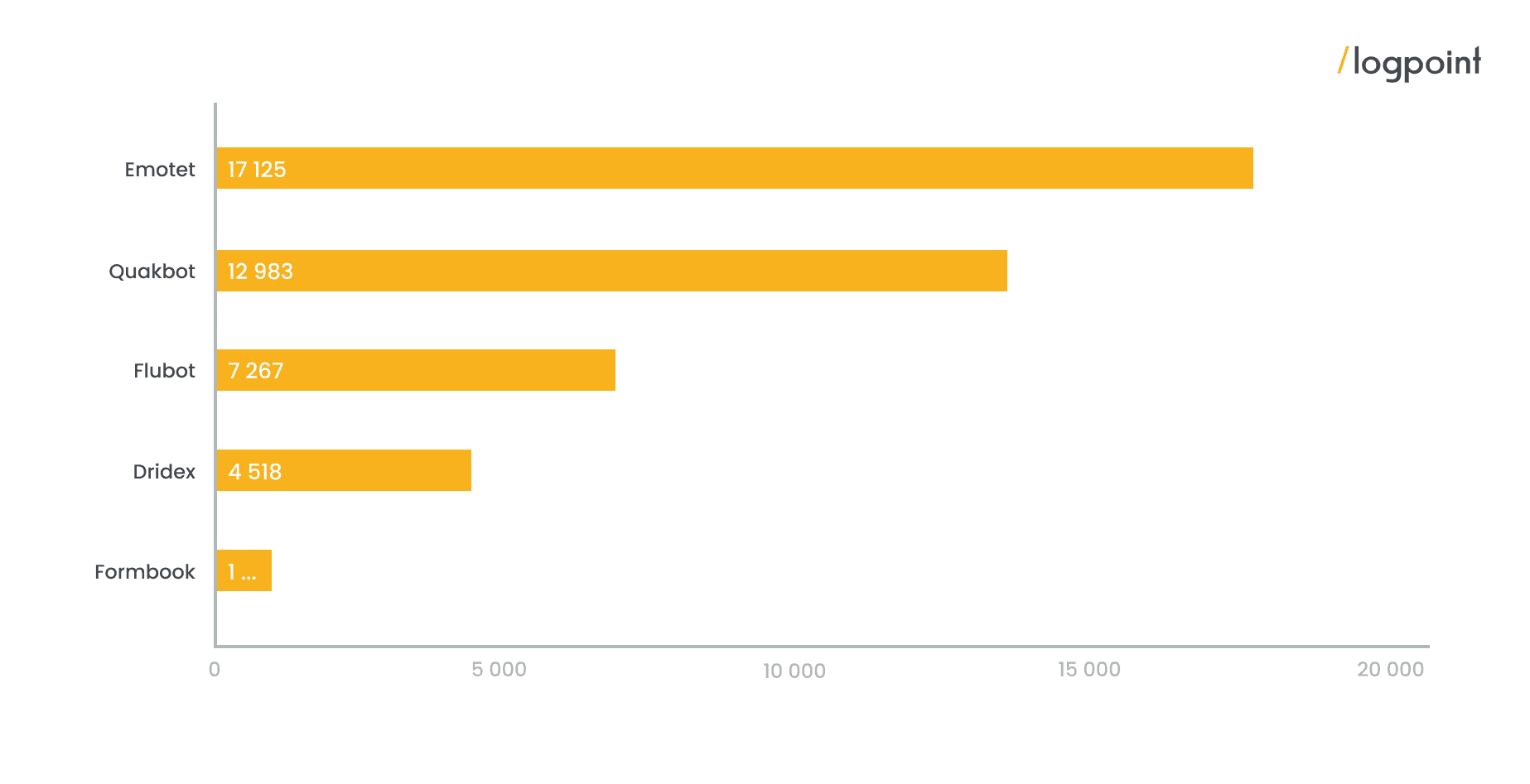
Despite being taken down by authorities, Emotet is a rapidly evolving malware that makes frequent appearances, it’s also one of the detected malware families. By closely monitoring its emergence, attack patterns, and possible detections, Logpoint can help security teams nullify Emotet before it becomes a threat.
What is Emotet?
Emotet, aka Geodo or Heodo, is a modular malware variant that was initially used as banking malware. At present Emotet is used as a dropper, which means it downloads other malware like IcedID, QakBOT, and TrickBot. Emotet was first detected in June 2014. Even though the authorities had initially taken down the Emotet operation, it returned time and time again with upgraded features and mechanisms to avoid methods of defense.
MUMMY SPIDER, aka TA542, MealyBug, and GOLD CABIN, is the threat actor linked to the core development of Emotet malware. The developers have been upgrading its features and now Emotet has evolved into Malware-as-a-Service (MaaS) and various C2 campaigns are run to handle infected systems. Some of the known modules and their use cases are mentioned below:
-
NetPass.exe: NetPass is a software utility developed by NirSoft to recover passwords from network shares under Windows 10/8/7/Vista/XP.
-
Outlook Scraper: The module scrapes names and email addresses from the victim’s Outlook accounts by using the messaging API. Phishing emails are sent to those collected accounts from the compromised account.
-
WebBrowserPassView: Another utility developed by NirSoft to recover passwords from browsers like Internet Explorer, Mozilla Firefox, Google Chrome, Safari, and Opera.
-
MailPass View: Software developed by NirSoft to reveal the passwords and other account details from email clients like Outlook, Mozilla Thunderbird, and Gmail.
-
Credential enumerator: The module can perform password brute forcing of user and administrative accounts.
According to data from “any.run” the highest number of running tasks was from Emotet. It is also the most detected malware sample on platforms like CAPE Sandbox, CERT.PL MWDB, ReversingLabs, Triage, UnpacMe and VMRay, according to statistics from MalwareBazaar.
According to data provided by malwarehunters.org, Emotet has the highest number of known command and control servers.
Emotet Fast Facts:
-
Emotet was first detected in 2014 as a banking trojan and now used as a dropper malware.
-
It inspects traffic going to financial sites for extracting bank account information. Five variants of botnet infrastructure are known and out of them epoch 4 and epoch 5 are active.
-
Initial access is gained primarily through phishing attacks, most of the time through Microsoft Office documents such as Excel and Word or through shortcut files (LNK).
-
It has various modules: Netpass, Outlook Scraper, WebBrowserPass View, MailPass View and Credential Enumerator.
-
Emotet has been changing its tactics by using various system binaries for execution, exploiting vulnerabilities, and employing techniques like launching malicious Office applications from trusted paths to bypass protected view, creating file Zone Identifier and obfuscation of payload.
Background and history
Emotet was launched as a banking trojan and its initial version was intended to intercept internet traffic and steal bank account information. Shortly after the initial release they released an updated version that had a number of modules including a feature for transferring money, a malspam module, and a banking module that specifically targeted banks in Germany and Austria. Another version of Emotet entered the market in January 2015 – Version three included a module to specifically evade detection and added Swiss banking as a new target.
In 2018, the Emotet trojan was updated as a “dropper malware” and used in campaigns to deploy TrickBot, Clop, and Ryuk. After the takedown of Emotet infrastructure in January 2021 by the coordinated effort from law enforcement departments of multiple nations, Emotet’s infrastructure came back to life when the TrickBot botnet was found distributing a DLL that emerged as Emotet in November 2021. Before the takedown three infrastructures were known, they are epoch 1, epoch 2, and epoch 3. After the takedown, the Emotet botnet operates with two infrastructures epoch 4 and epoch 5. Each campaign has its own unique delivery mechanism, infrastructure, update schedules, and malspam templates.
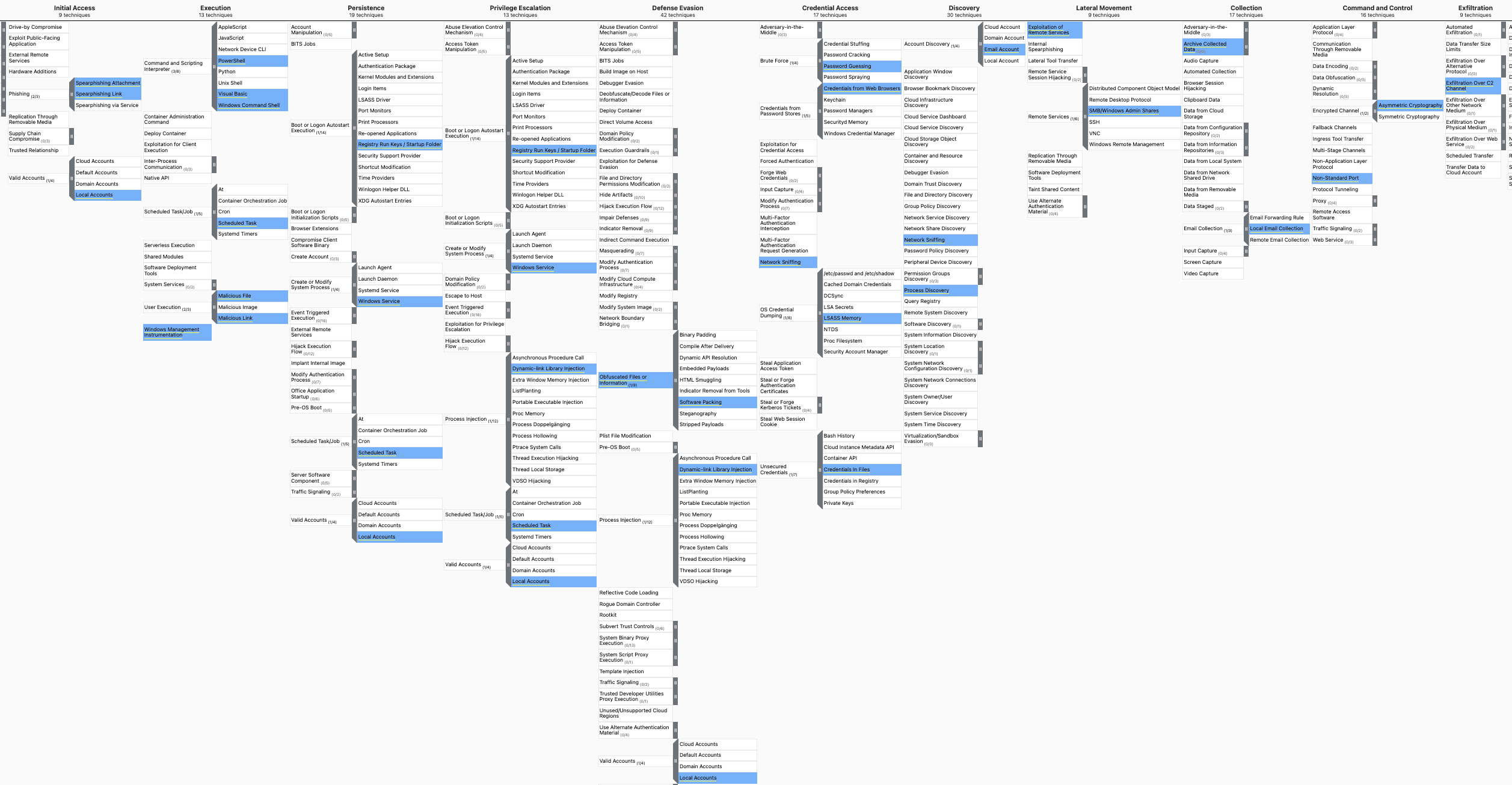
Emotet operations, tactics and techniques
Initial access is carried out mainly through malspam (emails containing malware) or a link to download malware. Emotet is a stager malware, meaning once the victim downloads the malicious file and executes it, Emotet connects to the C2 server and drops the staged payload. A stager is usually a macro-enabled Office document, but the use of the “lnk” file has also been detected.
For persistence, a scheduled task is created for the main payload and a new value is created in the autorun registry. Emotet injects itself into a running process for privilege escalation and defense evasion. It then performs system and network discovery and collects sensitive information like user, host, network, and shares. After collecting the required information, it starts the spam module which sends the phishing mail to collected mail accounts from the victim system. Then it drops the Cobalt Strike beacon which provides control to the adversaries.
For credential access, Emotet uses techniques like LSASS dump and mimikatz. Psexec is uses to transfer payload to other systems and WMIC is used for remote execution. After exfiltrating data to cloud storage servers like Mega, Emotet has been found dropping ransomware like Quantum, MegaCortex, and Conti.
From the static and dynamic analysis linked to our research we uncovered multiple files, domains, and botnet networks that are still active in the wild. All artifacts are provided as lists and the associated alerts are available to download as part of Logpoint’s latest release, as well as through the Logpoint Help Center.
Customized investigation and response playbooks are available to all Logpoint Emerging Threats Protection customers.
The Emotet report below details the analysis, infection chain, detection, and mitigation using Logpoint SIEM+SOAR and you can download it below.