by Bhabesh Raj Rai, Associate Security Analytics Engineer
Detecting attacks that target human error using the Damerau–Levenshtein distance
The longer threat actors remain undetected, the more damage they can do. In an attempt to stay under the radar, malware authors take advantage of user mistakes and try to deceive users by naming their payloads similar to those of critical or common system processes.
In a recent crypto-mining attack, adversaries took advantage of the common service host process svchost. Adversaries named their payload svshost.exe, a slight misspelling of the actual process that enabled the threat actors to stealthily mine Monero (XMRig).
Cyber threat actors often use slightly modified common words to trick users into launching various attacks such as typosquatting and system process impersonation. It’s imperative analysts continually use new, varied ways to detect breaches stemming from human mistakes because human error is consistently increasing year-to-year in frequency.
According to the Verizon 2020 Data Breach Investigations Report, errors are equally as common as social breaches, more common than malware, and are truly ubiquitous across all industries. It is vital for security analysts to regularly hunt for and detect attacks that prey upon human error before attackers can do any harm.
Threat detection with the new Damerau–Levenshtein distance plugin
One way to identify attacks that target human error is to use the newly released Damerau–Levenshtein distance plugin in LogPoint.
The Damerau–Levenshtein distance refers to the distance between two words that is the least number of operations (consisting of insertions, deletions, substitutions or transposition) required to change one word into another. For example, the Damerau-Levenshtein distance between ‘svchost.exe’ and ‘svchast.exe’ is 1 (substitute the “o” with “a”).
We’ll highlight two key use cases where the Damerau–Levenshtein distance plugin can help detect threats that can otherwise easily go undetected.
Detecting critical process impersonation
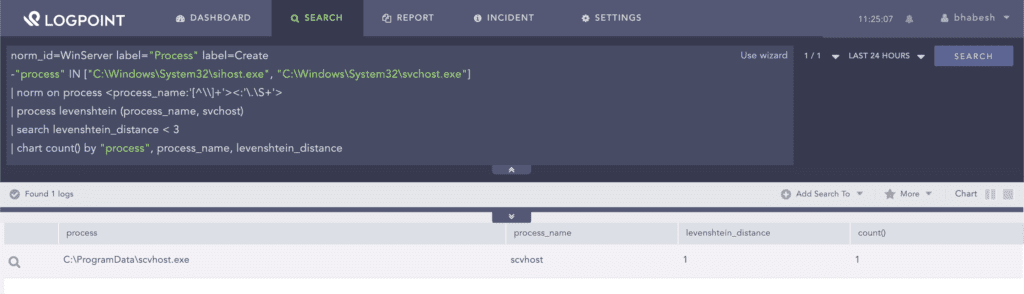
Detecting process impersonation of svchost.exe using the Damerau-Levenshtein plugin
Process impersonation is a way attackers gain access to your system by naming a malicious process similar to a common process. Analysts can easily hunt for processes that are running with confusing names by fetching process creation logs from endpoints. Increasing the threshold value will increase false positives, so we recommend that admins whitelist legitimate system noise for the configuration.
Detecting a typo-squatting attack
Another use of the Damerau–Levenshtein distance plugin is to detect typosquatting attacks against your enterprise. Typosquatting is heavily used in CEO frauds for impersonating senior employees in the organization. For example, if your enterprise’s domain is mycorp.com, adversaries can send phishing emails from typo-squatted domains like myc0rp.com in order to trick the receivers into believing the emails are legitimate.
sender=* receiver=*
| norm on sender @<sender_domain:'\S+'>
| process levenshtein (sender_domain, mycorp.com)
| search levenshtein_distance < 3
You can also search for possible typo-squatted domains from firewall logs.
device_category=Firewall domain=*
| process levenshtein (domain, mycorp.com)
| search levenshtein_distance < 3
The Damerau–Levenshtein distance plugin gives LogPoint users new ways to hunt for threats that target human error. By detecting threats such as process impersonation and typosquatting early on, analysts can reduce the impact and help bolster their defenses.





