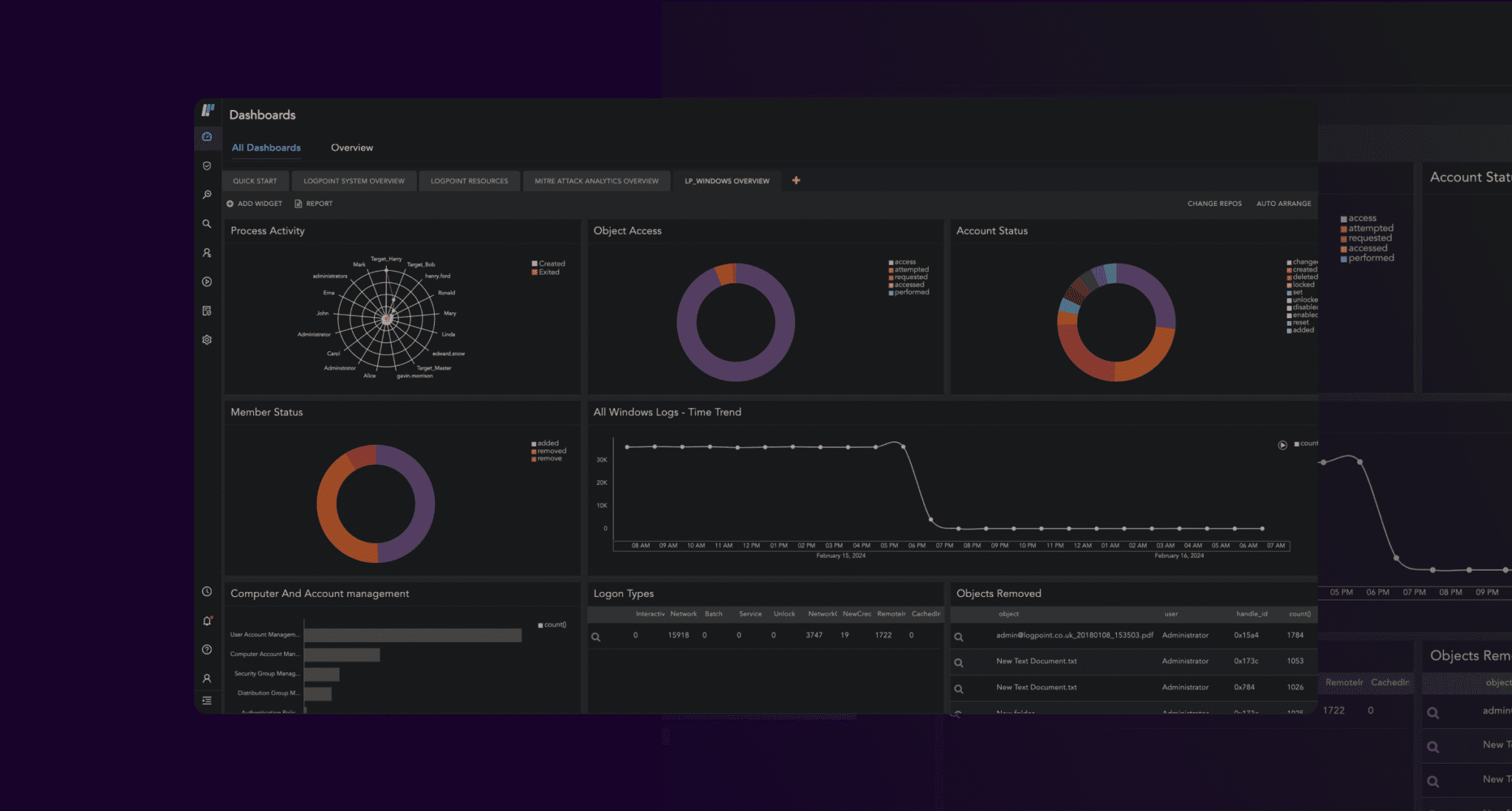
Extensive Fraud Management
With pre-defined use cases and behavioral analytics, we automatically identify
deviations in your SAP business processes. Use our automated process controls to put an end to the likes of employee theft, corruption, and warranty fraud.
Advanced Threat Detection at Business Run Time
A quick response is pivotal to minimizing the impact of cybercrime. With automation, we deliver all the necessary insights at the speed of the business.
Easy Implementation
Get full functionality with minimal configuration efforts. No need to spend time and funds on implementation, when you can have an out-of-the-box solution that works in an instant.
Use case: Reliable and efficient detection and
response to fraud from inside your organization
– to protect your revenue and the integrity of your business
Inability to secure the integrity of a business can severely damage the most robust of businesses. In 61% of all security breaches, valid credentials were involved. Insider attacks can be difficult to identify as established security controls do not apply or can easily be circumvented.
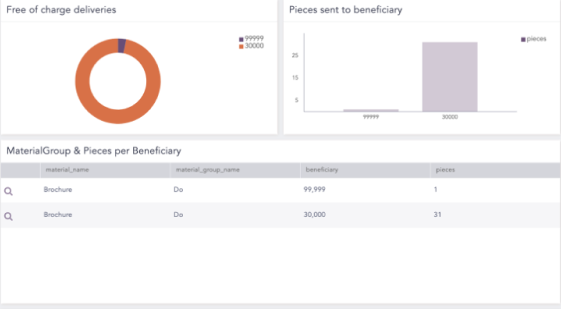
Detecting financial fraud within supply management
An employee in a healthcare organization creates a ‘free of charge delivery’ in the SAP system, releases the order, and sends a large quantity of samples to a beneficiary.
Despite divergence in behavior, traditional security tools fall short of detecting such compromising transactions, due to lacking investigative capabilities.
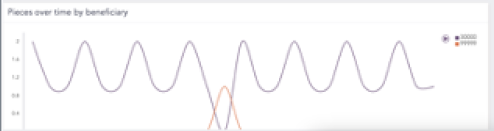
With advanced behavioral analytics, the Business Integrity Monitoring solution can detect deviations from standard business processes, in near real-time. In this case, anomalous transactions would be detected early, so you can intervene and circumvent financial losses.
With the Business Integrity Monitoring solution, you can leverage a wealth of use-cases, predefined rules, and various statistical capabilities, to spot and predict anomalous behavior.