SAP Business Technology Platform
A staggering 98% of businesses have reported cloud breaches in the last 18 months. A fundamental step towards fortifying your security stance in cloud involves securing SAP BTP. A compromise could lead to unparalleled consequences, granting hackers access to your entire infrastructure, applications and integrations, posing a significant threat to business continuity and undermining your organizational legitimacy.
Mehr als 1.000 Organisationen in über 70 Ländern nutzen Logpoint SIEM
Why BCS for SAP BTP?
Embark on a new era of SAP BTP security where uncertainty is a thing of the past. Allow our powerful threat detection and monitoring solution to light the way, providing your teams with comprehensive threat visibility. This ensures they can respond to threats efficiently and take proactive measures to mitigate risks.
- Elevate the security of your SAP BTP – proactively
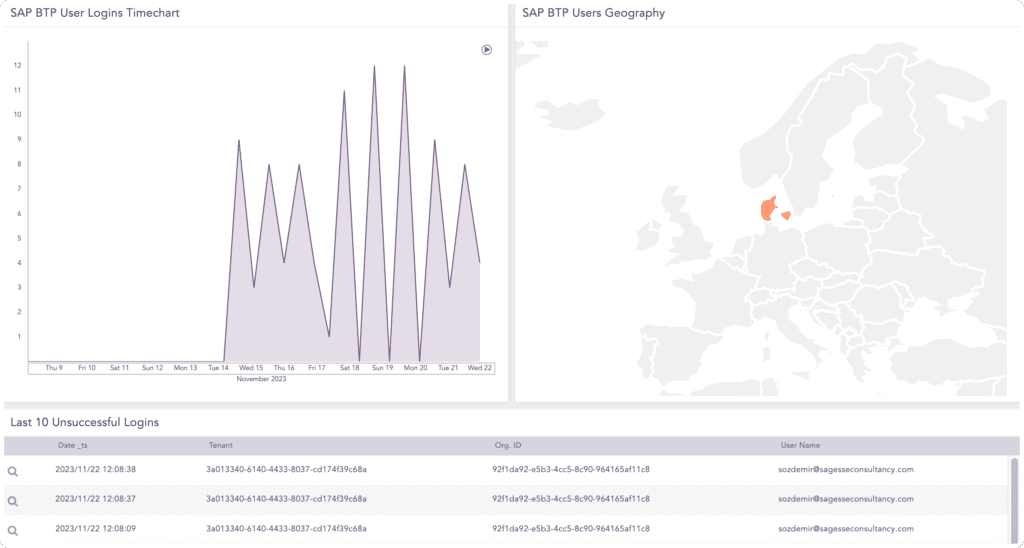
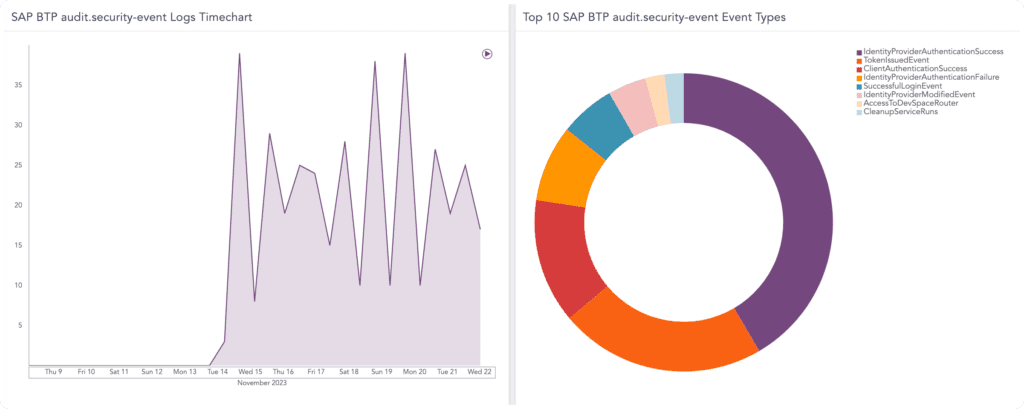
If SAP BTP gets compromised, your entire cloud infrastructure could be at risk. Keeping it safe should be your highest priority. By closely monitoring security–related events in real-time, such as logins, user geography, timeframes, and changes to roles and configurations, we provide you with full threat visibility, empowering you to proactively mitigate threats and keep attacks at bay. - Boost your security posture – effectively
Automate the monitoring of security logs to maximize efficiency. Save time, resources and alleviate alert fatigue by leveraging our intuitive dashboards, which offer a contextualized and prioritized overview of security incidents. This allows you to promptly take action and effectively mitigate threats putting your applications at risk.
Use case
Challenge: A user tries unsuccessfully to login several times within a short time-frame. This could be an indication of brute force attack, where the hacker uses trial and error to crack passwords, login credentials and encryption keys. This is a simple, yet widely used tactic for gaining unauthorized access to individual accounts and organizations’ systems and networks.
Our Solution: We closely monitor a wide range of login metrics; successful logins, unsuccessful logins and internal logins to provide you with a complete overview of who is attempting and succeeding with logging into your system. In addition to this, we also monitor the timeframes of the ‘security relevant events’ to provide you with more context.